1. Introduction
The fifth generation of mobile networks (5G) was designed to support three main types of services with widely different requirements: enhanced mobile broadband (eMBB), ultra-reliable low-latency communications (URLLC), and massive machine-type communications (mMTC) [
1]. The eMBB category focuses on human-oriented services that transmit large amounts of data and offer higher data rates and increased spectral efficiency when compared to the previous generation. On the other hand, Internet of Things (IoT)-like services, which transmit small amounts of data intermittently (and hence are termed intermittent services throughout the rest of the paper), may fall within either URLLC or mMTC categories, depending on their latency and reliability requirements, and processing/computational capabilities. The intermittent services where low latency (in the order of a few milliseconds) must be guaranteed with extremely high reliability (in the order of 1–
) belong to URLLC service type. Conversely, intermittent services with relaxed latency and reliability requirements while incorporating exceedingly large numbers of devices belong to mMTC service type.
However, such a categorization of IoT services is too simplistic and cannot model a finer gradation of timely data delivery requirements. In particular, there are novel, timeliness-related metrics that may better capture the requirements of some categories of IoT applications. In this respect, AoI has recently attracted attention due its ability to measure the freshness of information by combining the communication and data generation processes [
2]. AoI is measured at the point of reception, as the time elapsed since the moment of generation (at the transmitter) of the last successfully received message. A related metric is Peak Age of Information (PAoI), which represents the AoI measured immediately before a new message is successfully received [
3].
AoI and PAoI are particularly relevant in control systems and similar setups with (quasi) periodic message exchanges [
4]. The underlying assumption is that users send updates of an ongoing process, such that the most recent update provides all the necessary information about the state of the process. In such scenario, the reliability and latency of individual packets are of secondary importance [
2]. We refer the interested reader to a recent survey [
5] for a thorough review of AoI and its properties, and to our previous work for a discussion on the differences between AoI and latency and reliability as timeliness metrics [
6,
7].
The concept of network slicing has been widely investigated in recent years, mainly motivated by the need for accommodation of heterogeneous services in the network. The idea is to allocate (i.e., slice) the network’s resources among the different coexisting services, such that each service has the experience of meeting the performance requirements while being isolated from the other service types [
8,
9]. In our previous work [
7], we introduced the concept of spectrum slicing to refer to the allocation of shared wireless resources among coexisting heterogeneous services in the Radio Access Network (RAN). Those resources can be defined, for example, in time, frequency, or spatial domains. So far, spectrum allocation, rather than slicing, has been widely studied in the form of diverse OMA and NOMA techniques in the presence of multiple users with the same type of service [
10,
11,
12]. OMA techniques assign dedicated resources to individual users and/or services: Orthogonal Frequency-Division Multiple Access (OFDMA), Code Division Multiple Access (CDMA), and multi-user multiple-input multiple-output (MU-MIMO) are examples of OMA that achieved widespread implementation in 3GPP cellular systems, including 5G [
13,
14,
15]. On the other hand, the NOMA concept refers to the allocation of shared (i.e., non-orthogonal) resources in the time and/or frequency domains to multiple services or users. Such allocation intrinsically implies collisions of users’ transmissions in the shared domain(s), and NOMA techniques generally rely on more complex receivers, capable of Multi-Packet Reception (MPR) to resolve collisions. The benefit of this techniques is potentially a higher resource efficiency than OMA, and less need for strict coordination among users. On the downside, implementation of MPR techniques is usually complex; a typical example is Successive Interference Cancellation (SIC) [
11,
16].
In scenarios with broadband services only, resource efficiency is easily defined and the trade-offs are clearly characterized by the achievable data rates and/or throughput [
11,
12]. However, further research is needed on novel slicing mechanisms in scenarios with heterogeneous services, for example, broadband and intermittent, since the efficiency cannot be simply measured in terms of throughput or data rates [
9,
17]. We illustrate this through a toy example presented in
Figure 1, where there are (i) 3 intermittent users following an ALOHA-based protocol, and (ii) a broadband user. With OMA, orthogonal resources are defined for each service type. This limits the frequency of resources for the intermittent users, which increases the probability of collision among them, as shown by the cross-mark in
Figure 1; these collided packets cannot be recovered. In contrast, with NOMA all resources are available for the intermittent and broadband users, and SIC is used to recover the packets lost due to collision between the broadband and intermittent users. In this example, NOMA obtains greater throughout for the broadband user and a lower latency and greater reliability for the intermittent users than OMA. This insight motivates the work presented in this paper.
In particular, in this paper we investigate orthogonal and non-orthogonal slicing mechanisms in the case where a broadband user shares a wireless channel with multiple intermittent users share. Specifically, we explore the performance of slicing implemented via multiple access schemes standardly used in the cellular access, which are TDMA and slotted ALOHA, and a scheme representing their combination. The broadband user implements a K-out-of-N erasure code, which allows the user to counteract the packet losses due to channel and potential collisions with the intermittent users transmission in the case of non-orthogonal slicing. In the later case, once the block of N broadband users’ packets becomes decoded, the receiver uses SIC to attempt recovery of the intermittent users’ packets. The performance parameters of interests are throughput of the broadband user and two timeliness metrics for the intermittent users: latency-reliability of individual packets and PAoI.
In our previous works [
6,
7], we investigated the performance trade-offs of OMA and NOMA in a simple uplink scenario with one broadband user and one intermittent user. The general conclusion was that OMA usually outperforms NOMA when transmissions takes place in a collision channel with packet erasures and without capture, which is a rather conservative channel model. However, NOMA schemes achieved a similar performance as OMA in extreme cases when the single objective is to maximize the throughput of the broadband user or to minimize the latency of the intermittent user [
6]. We also evaluated how the capture effect and immediate (i.e., intra-collision) SIC at the receiver enhance the performance of NOMA. Under this scenario we observed that important gains can be achieved with NOMA when the intermittent user aims to minimize latency, but the gains are limited when the objective is to minimize AoI [
7]. This paper extends that analysis to the case with multiple intermittent users, showing quite different trade-offs. We derive closed-form expressions for the performance parameters and show that, when the intermittent users aim to minimize the PAoI, OMA with TDMA is the best choice, albeit by a small margin. In contrast, when the intermittent users aim to optimize the packet latency, the slicing mechanism must be carefully selected based on the access load and the number of users, as there is no single slicing method that provides the best trade-offs.
In summary, the main contributions of this paper are the following:
We analyze the trade-offs and regions of operation of OMA and NOMA schemes with a broadband and multiple intermittent users in a collision channel with erasures.
We investigate the impact of the metrics of interest on the overall system design and on the achievable gains with OMA and NOMA.
We investigate the impact of the activation probability of intermittent users on the performance of the slicing mechanism.
We derive Pareto frontiers, which define the best possible trade-offs between throughput of the broadband user and latency/AoI of the intermittent users with the considered schemes.
The rest of the paper is organized as follows.
Section 2 presents the literature review. The system model is described in
Section 3. The analyses for OMA and NOMA schemes are presented in
Section 4 and
Section 5, respectively. The results are presented in
Section 6.
Section 7 concludes the paper.
2. Related Work
Orthogonal slicing has been widely explored and used in commercial systems [
9]. It is a straightforward approach where independent resources are allocated to the different services, which allows one to treat them in an isolated manner. Popovski et al. [
17] provided one of the first studies that compared orthogonal to non-orthogonal slicing. In particular, it investigated the benefits of OMA and NOMA schemes for the different combinations of 5G services in an uplink scenario: eMBB with URLLC and eMBB with mMTC. In the latter, orthogonal resources were allocated to each eMBB user, mMTC traffic was assumed to be Poisson distributed, and one URLLC user was considered. It was observed that NOMA may offer benefits with respect to OMA depending on the rate of the eMBB users and on the coexisting type of the intermittent traffic: with high URLLC, high data rates at the eMBB user were beneficial for NOMA, whereas the opposite is true with mMTC traffic.
The work presented in [
17] was extended to a multi-cell scenario with strict latency guarantees for URLLC traffic [
18]. A single URLLC user per cell was considered, and it was observed that NOMA leads to a greater spectral efficiency with respect to OMA. A similar conclusion was drawn by Maatouk et al. [
10] in an uplink scenario with two users with the same service type that aimed to minimize the average AoI. It was also observed that a greater spectral efficiency does not directly translate into a lower average AoI. Another scenario that includes power control to simplify the reception of the intermittent packets was studied in [
19], which derived analytical formulas for throughput and AoI with those settings.
The selection of the multiple access scheme is essential when considering spectrum slicing with multiple intermittent users [
9], and particularly so in MU-MIMO systems which can make MPR easier [
20]. Slotted ALOHA and TDMA are two basic multiple access schemes that offer widely different benefits. Slotted ALOHA is simple, flexible, and effective for relatively low traffic loads. It is one of the most widely used random access protocols, implemented in a number of variants, e.g., multichannel slotted ALOHA in 5G [
21,
22]. There is a vast literature on the performance evaluation of ALOHA-based schemes in terms of latency and reliability. For instance, grant-free ALOHA-based access has been studied for URLLC services [
23,
24]. Besides, latency and reliability can be combined into a single performance indicator termed latency-reliability [
25]. On the other hand, it is difficult to derive closed-form expressions of the probability distribution of the AoI. Hence, most papers in the literature examined it in terms of its mean value and in the context of queuing theory and often in ideal systems with Markovian service [
26]. Only a few studies investigated the tail or the full distribution of AoI, event though these provide a clear measure for the reliability and stability of control systems. In particular, these are directly connected to control systems by the survival time, defined as the time that an application may continue to operate without receiving an anticipated message [
27]. The distribution of AoI with packet preemption and memoryless servers was investigated in [
28]. In [
29], the Chernoff bound was used to derive an upper bound of the quantile function of the AoI for two queues in tandem with deterministic arrivals. The peak-age violation probability, defined as the probability of exceeding a pre-defined PAoI threshold, was derived for a single-hop link with fading and retransmissions, in the form of variable-length-stop-feedback [
3].
So far, only a few studies considered the impact of physical layer and medium access control on the AoI. Among these, recent works compute the average AoI in Carrier Sense Multiple Access (CSMA) [
30], ALOHA [
31], and slotted ALOHA [
32] networks, considering the impact of the different medium access policies on the age. Of special interest for our study, the AoI with a TDMA-like scheme with perfect feedback and immediate retransmissions was compared to that of ALOHA [
33]. It was observed that TDMA with retransmissions greatly reduced the AoI when compared to ALOHA. However, the former scheme assumes that the transmissions from all users after a transmission failure are delayed to allow for a retransmission to occur in the next time slot, which is inefficient, as a separate channel is needed for feedback.
There are only a few studies on heterogeneity in AoI systems. We mention the work presented in [
34], which considered different service classes, and modeled the system as an M/G/1/1 queue with hyperexponential service time. However, only the service rate was different among classes. Then, the classes could adapt the arrival rate to minimize the AoI.
3. System Model
In the following, we denote random variables with capital letters (e.g.,
X) and their values with the corresponding lowercase letters (e.g.,
x). Sets are denoted in calligraphic font (e.g.,
), and the corresponding standard capital letters denote their cardinality (e.g.,
U). Vectors are denoted with bold lowercase letters (e.g.,
), and matrices with bold capital letters (e.g.,
). probability mass functions (pmfs) are denoted with a lowercase
p and Cumulative Distribution Functions (CDFs) with a capital
P.
Table 1 provides a quick reference for the most important notation used in the rest of the paper.
We define the outcome of the user’s activity in a slot as an event, which happens with probability
p and is mutually exclusive with other outcomes. The outcome vector
then corresponds to the composite event in which the
i-th outcome is observed
times, and the probability vector
contains the probability of each outcome (which does not necessarily sum to 1 as we consider that none of the outcomes might occur). We can then define the multinomial function
, which corresponds to the probability of outcome vector
being observed over
n slots.
where
is the length of vector
. The binomial function
is the special case in which
.
We also define the modulo function, which behaves as expected from integer arithmetic.
for
.
is the set of non-negative integers.
3.1. Access Model
We consider an uplink scenario with a set of users transmitting data to a Base Station (BS) over a single time-slotted multiple access channel. This single channel may consist of a single or of multiple subcarriers in an OFDMA system, whose number remains constant throughout the operation of the system. Users can transmit up to one packet per time slot, denoted by the index , by occupying the available bandwidth and the entire duration of the slot. This can achieved by selecting a proper modulation and coding scheme based on the size of the payload to transmit. The study of multi-channel settings is considerably more complex, and left to future work, as having multiple concurrent resources in frequency domain changes the timing considerations significantly.
There is as set of users
in the system, composed of a single broadband user and multiple intermittent users. Specifically, user
is the broadband user following the eMBB model: it is a full-buffer user that always has data to transmit and maintains an infinite transmission queue. To counteract potential packet losses due to the noise, the broadband user implements a packet-level coding scheme, where blocks of
K source packets are encoded to generate a frame of
N coded packets of length
ℓ bits each. The basic operation of the broadband user is shown in
Figure 1. The coded packets are linearly independent, which can be achieved, for example, with Maximum Distance Separable (MDS) codes or with Random Linear Network Coding (RLNC) with Galois-field size equal to
∞. In effect, decoding any subset of
K coded packets is sufficient for recovering the original block.
The intermittent users belong to the subset , where . They generate packets in each slot with a probability (i.e., they experience Bernoulli arrivals with parameter ) and maintain a queue of up to Q generated packets. If a new packet is generated when the instantaneous length of the queue is Q, these users discard the oldest buffered packet and add the newly generated one at the end of the queue. The choice of discarding the oldest packet in the queue follows a simple rationale: discarding any of the packets has the same effect on the overall reliability, choosing the oldest minimizes the latency for the ones that are delivered, as they will spend less time waiting for a slot in which they can be transmitted. In most practical cases, the queue will be set up so as to minimize the probability of discarding packets, but the case with short queues is relevant for low-power IoT devices with limited memory and computational resources. Packets are transmitted from the queue using First-In First-Out (FIFO) discipline, and the transmissions take place in the allocated slots.
We consider a static allocation scheme, in which users are synchronized at the slot level. The set of users that are allocated slot t is denoted by , where s.t. . We define the following three types of slot allocations.
Broadband: The slot is reserved for the broadband user. Hence, .
Intermittent: The intermittent users are allocated the slot and may use it if there are packets in their queues. Hence, .
Mixed: Both types of users are allowed to access the slot. Hence, s.t. and .
Next, we define the OMA and NOMA slicing based on the resource allocation as follows.
Finally, based on the allocation in the intermittent and mixed slots, we define the following three subdivisions of OMA and NOMA slicing. We take a slot t in which the intermittent users can transmit, i.e., any slot in NOMA or one of the intermittent slots in OMA.
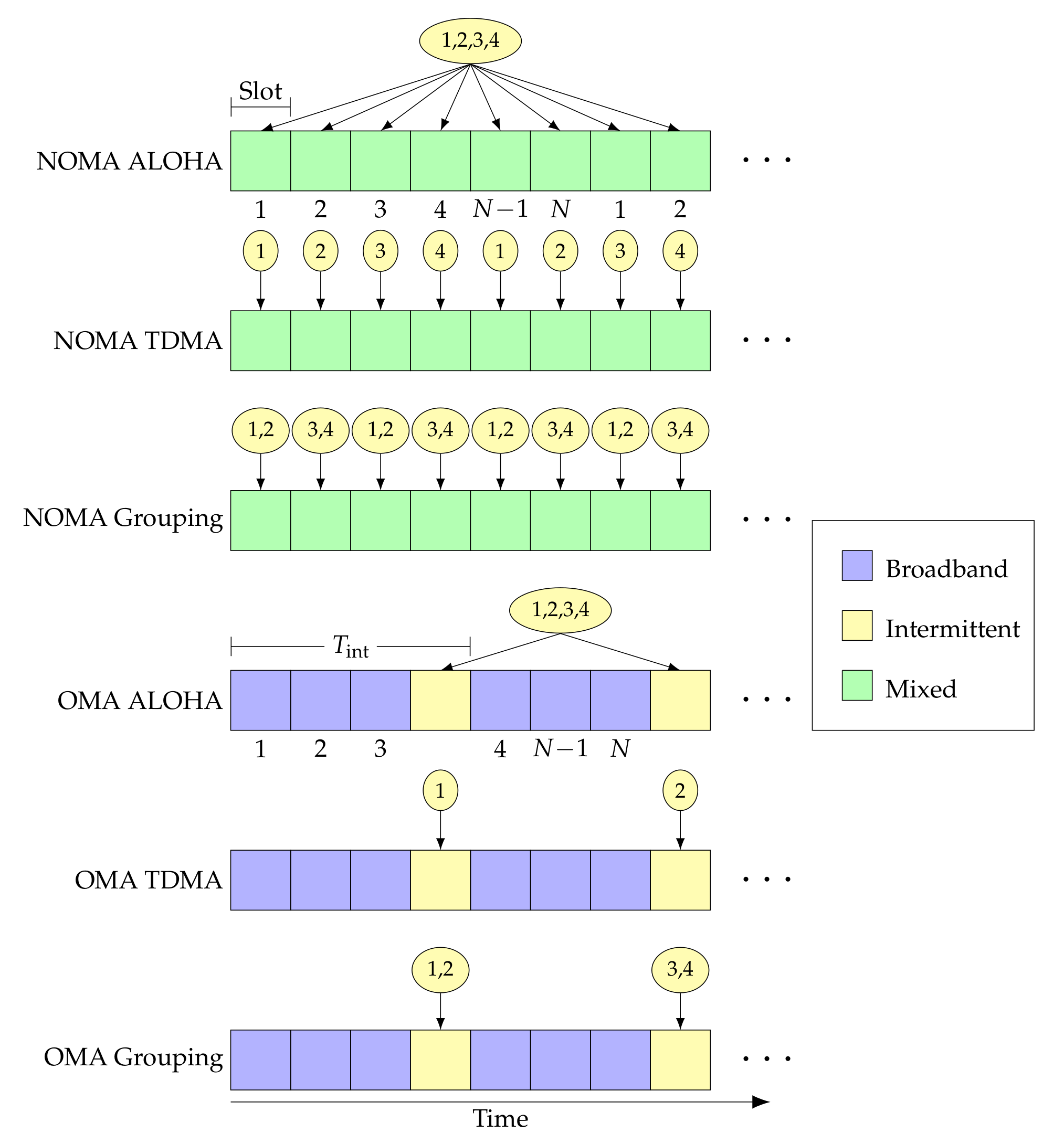
TDMA: The slot is allocated to a single intermittent user, such that .
Grouping: The slot is allocated to intermittent users s.t. for all t. We consider the case where , i.e., we can divide the intermittent users into groups of equal size.
ALOHA: All the intermittent users are allowed to transmit in the slot. Hence, for all slots, excluding the broadband slots in OMA.
The frame structures for the six access schemes resulting from the combining of the slicing and allocation methods described above are illustrated in
Figure 2: the circles represent the intermittent users that have access in any given slot, and the color of the square represents the type of access in that slot. We also not that the grouping scheme can be easily extended to cover the two extreme cases in which (i) there is only one group comprising all intermittent users (which is equivalent to ALOHA) and (ii) there is one user per group (which is equivalent to TDMA). Thus, it represents a general scheme which we can apply within OMA or NOMA.
3.2. Channel Model
We consider a quasi-static block fading channel, where the received signal by the BS at any slot
t is given as
where
is the random fading coefficient for user
u at slot
t and
is an Additive White Gaussian Noise (AWGN) noise with variance
. The random variable
models user’s activity, being equal to 1 if the user is active in that slot and 0 otherwise. A user is active only if it is allowed to transmit; i.e., if
, and if its packet queue
is not empty:
where
is the indicator function, equal to 1 if the condition is true and 0 otherwise. Let
be the fixed transmission power of user
u, which can be different for each user. The Signal to Noise Ratio (SNR) of user
u at time slot
t is given by:
whereas the Signal to Interference plus Noise Ratio (SINR) of user
u at time slot
t is given by
where
is the set of users except user
u. We can also simply divide the SINR by the noise power
, giving
Hence, the SINR is equal to the SNR in the absence of interference. Next, we define
as the threshold in the SNR to decode a packet. That is,
defines the erasure probability of a binary erasure channel (BEC) as
Further, we consider a simple collision model, so that packets cannot be decoded in the presence of interference (i.e., collisions). Hence, a packet from user
u can be decoded, with probability
if and only if
. This model neither allows for capture, nor for potential subsequent application SIC within slots containing more than one transmission (i.e., intra-collision SIC), representing the worst-case scenario for schemes that rely on MPR, such as power-domain NOMA. Instead, SIC can be only performed after decoding the broadband user, regeneration of all its
N coded packets, and removing them from the slots that also contain transmissions from the intermittent users (i.e., extra-collision SIC). In slots without a collision, we assume a constant erasure probability for each user, denoted as
for the broadband user and
for the intermittent user. Our assumption is that the erasure probability after the interference is canceled is the same as for a free channel, which is a simplification. However, the use of parity checks on all the packets in a frame means that the probability of erroneous packet decodings is very low, and modeling the precise performance of SIC schemes is beyond the scope of this paper, and this is a common assumption in the coded slotted ALOHA literature, which assumes a similar setting [
35]. The model provides a general view on the lower bound on performance of the OMA and NOMA schemes that is independent of the underlying channel model.
3.3. Key Performance Indicators
The KPIs of interest are described in the following.
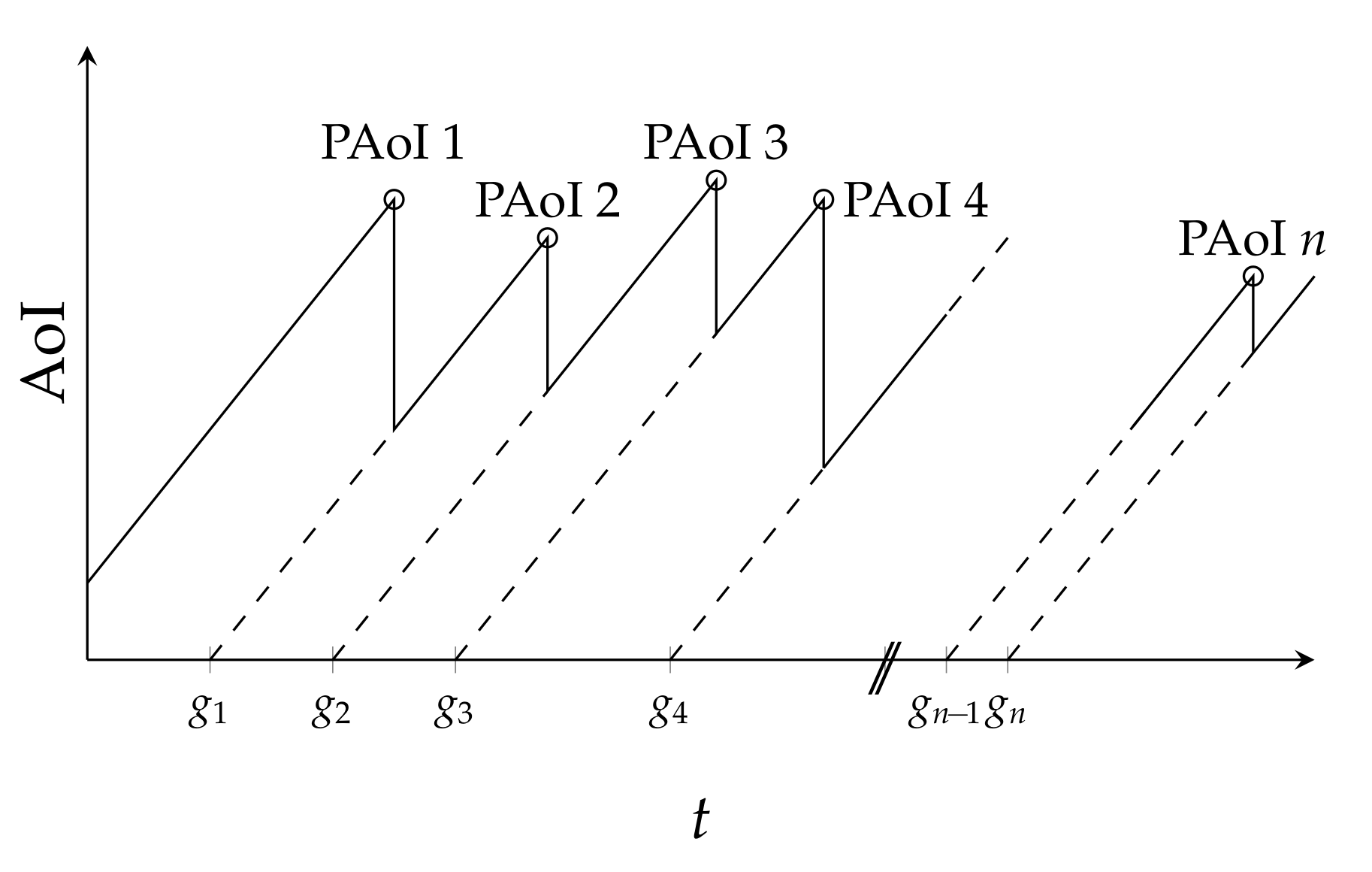
We first define the AoI
, which in our case is the number of slots that have passed since the generation of the last correctly received packet. If packet
i is generated in slot
and decoded by the receiver in slot
, while packet
is generated in slot
and decoded by the receiver in slot
, we have:
The PAoI
is then simply defined as the AoI, measured at the instant of arrival of a new packet:
The PAoI is the maximum value of the AoI across a cycle, as depicted in
Figure 3.
The relevant KPI for PAoI-oriented systems is the 90th percentile of the PAoI, denoted by
.
Latency and age are expressed in slots.
allows us to assess the tail distribution of the PAoI in a general scenario, and can be used to compare performance with different values of the slot arrival rate
. In contrast, a widely employed metric called
PAoI violation probability [
3] requires the definition of a specific threshold, either expressed as an absolute time or as a maximum number of slots. Furthermore, it cannot be used to compare the performance under different arrival rates
since the AoI is greatly determined by the latter.
For latency-oriented systems, we introduce a similar KPI, which is the 90th percentile of the latency-reliability for intermittent users. The distribution of latency-reliability is computed by multiplying the distribution of the latency of successfully received packets by their success probability
:
on all packets, not just the successfully delivered ones,
We can now define the Pareto frontier, which is commonly used in multi-objective optimization:
Definition 1. Let and be the set of feasible configurations. Next, letwhere is the throughput of the broadband user and τ is the timeliness of the intermittent user, i.e., or . The Pareto frontier is the set 6. Results
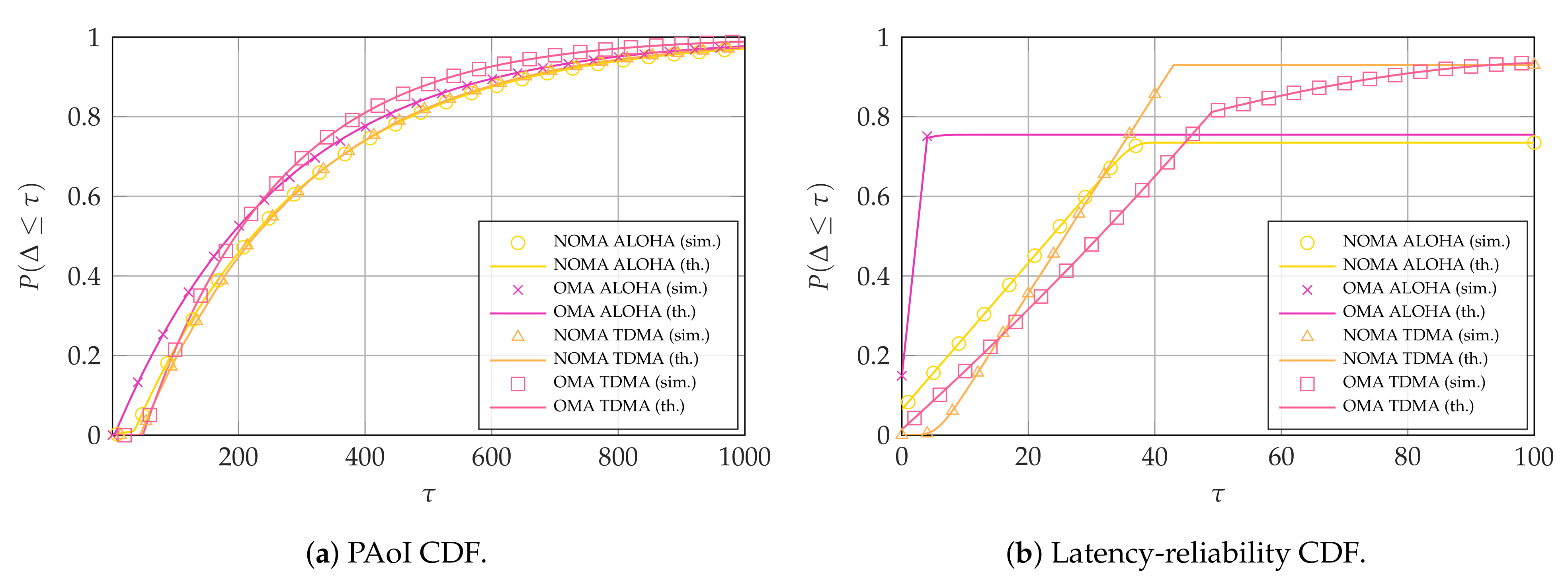
In this section, we show some illustrative analytical results for the PAoI-oriented and latency-oriented case. We first confirm that our theoretical calculations are correct by considering a given scenario and performing a Monte Carlo simulation. We simulate the erasure channel and destructive interference simply by dropping packets from the list, and consider
frames. In the scenario we simulate, the broadband user protects its transmission with a
K over
N erasure code, i.e.,
and
, and the arrival rate for each of the
intermittent users is
(i.e.,
). The OMA systems use
. As
Figure 4 shows, the theoretical results for both PAoI and latency-reliability, shown here as CDFs, match the simulations perfectly in all cases. Monte Carlo results are not shown for the rest of the section to improve the understandability of the plots, but the results still match tightly with the theoretical analysis.
The results are presented in the form of Pareto frontiers, that capture the best trade-offs between the throughput of the broadband user
and the 90th percentile of the timeliness metric for the intermittent users. The parameter settings are shown in
Table 2. With the selected parameters and if only the broadband user is considered, the optimal source and coded block sizes are
and
, where
K is limited to 64 to make the solution practical), respectively, which results a throughput of
packets per slot. The latter corresponds to the upper bound in throughput for both OMA and NOMA systems evaluated in the following.
We first consider PAoI-oriented systems, whose performance has a strong dependence on the aggregate arrival rate
. We assume that
, which allows us to explore a wide range of values for
. In this case, the grouping scheme used
, whereas the ALOHA and TDMA cases had the expected
and
, respectively. When
is very low, the inter-arrival time dominates the PAoI and the impact of the choice of access schemes is negligible. As
Figure 5 shows, this is true even for a total arrival rate of
, which corresponds to an average of one packet every 400 slots from each source: as the arrival process is exponentially distributed, the 90th percentile of the inter-arrival time is 920 slots, and it is impossible to achieve a lower
. In cases with a higher arrival rate, OMA TDMA seems to be the best system, although NOMA ALOHA can achieve a similar performance when PAoI is more important than the broadband user throughput.
Besides the achievable performance trade-offs, it is also important to observe the parameter settings that achieve Pareto efficiency, as shown in
Figure 6. The difference between the optimal values of
in OMA for the three considered schemes is stark, as shown in
Figure 6a. This is because collisions are the main factor driving up the age in OMA, making the age for TDMA far lower. The other factor in the age is the waiting time due to the grouping: while TDMA compensates for this by avoiding collisions entirely, the grouping scheme with
is the worst of both worlds, getting extremely poor performance due to having both a longer interval between allocated slots and the risk of collisions. Therefore, in age-oriented systems where the arrival rate
for each intermittent user needs to be relatively high to achieve the desired AoI, orthogonal slicing among all users (broadband and intermittent) is a good choice, as the alternative will result in a high collision probability.
Collisions are not so common in TDMA, as the transmissions for the intermittent users can be spread out over all slots, and are not concentrated in some reserved ones. In this case, the specific method used is not very important, as
Figure 6b shows: the three schemes have a similar age with very similar coding rates. However, NOMA cannot significantly outperform OMA TDMA, as allowing collisions with the broadband user limits the achievable throughput.
Next, we consider the latency-oriented systems where the 90th percentile of latency-reliability
is the main KPI for intermittent users. For these, we focus on illustrating the impact of the arrival rate
and the number of intermittent users
.
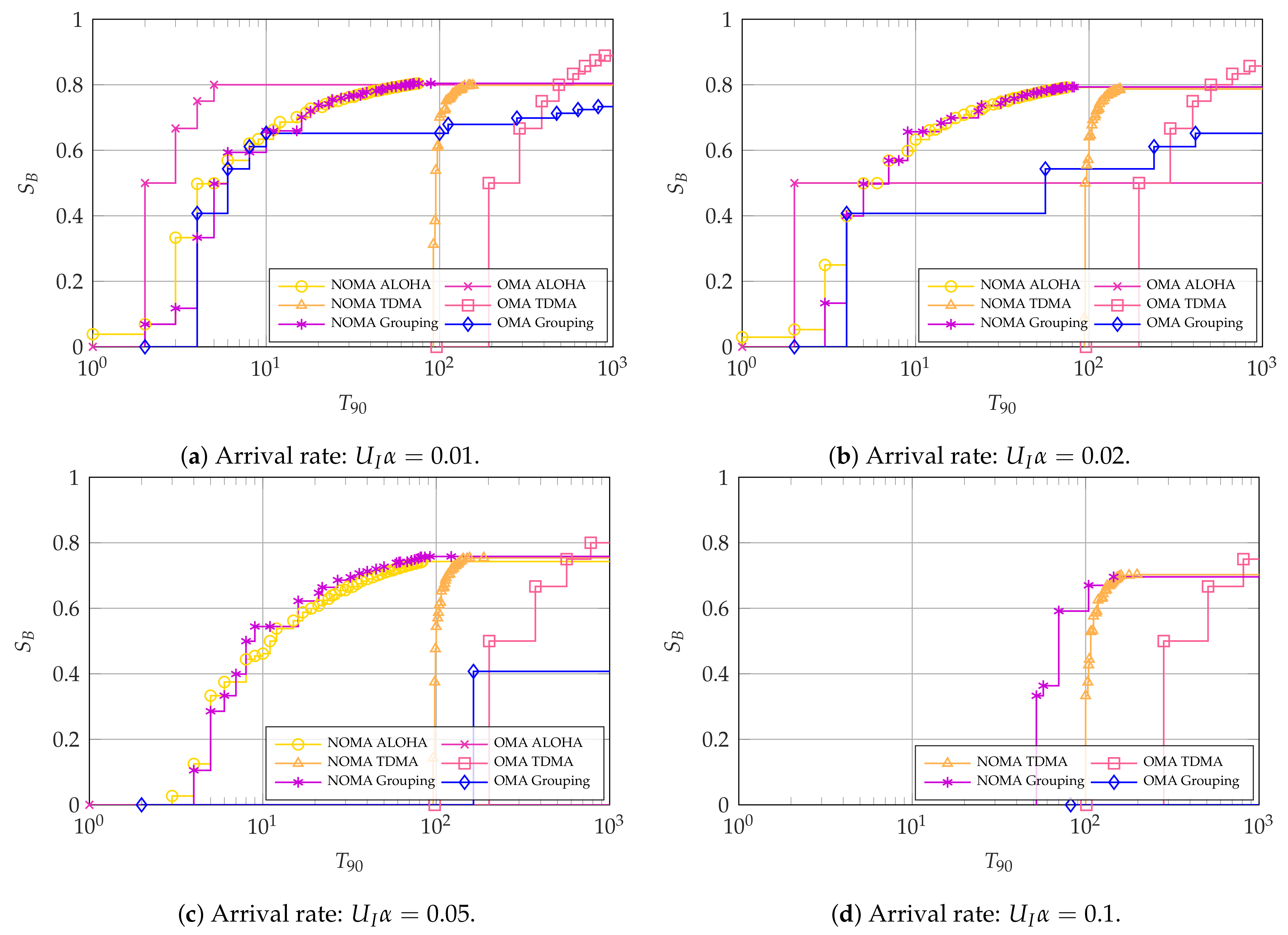
Figure 7,
Figure 8 and
Figure 9 show the Pareto frontiers for the cases with
,
, and
, respectively. Each of the figures includes the latency and throughput trade-offs for
.
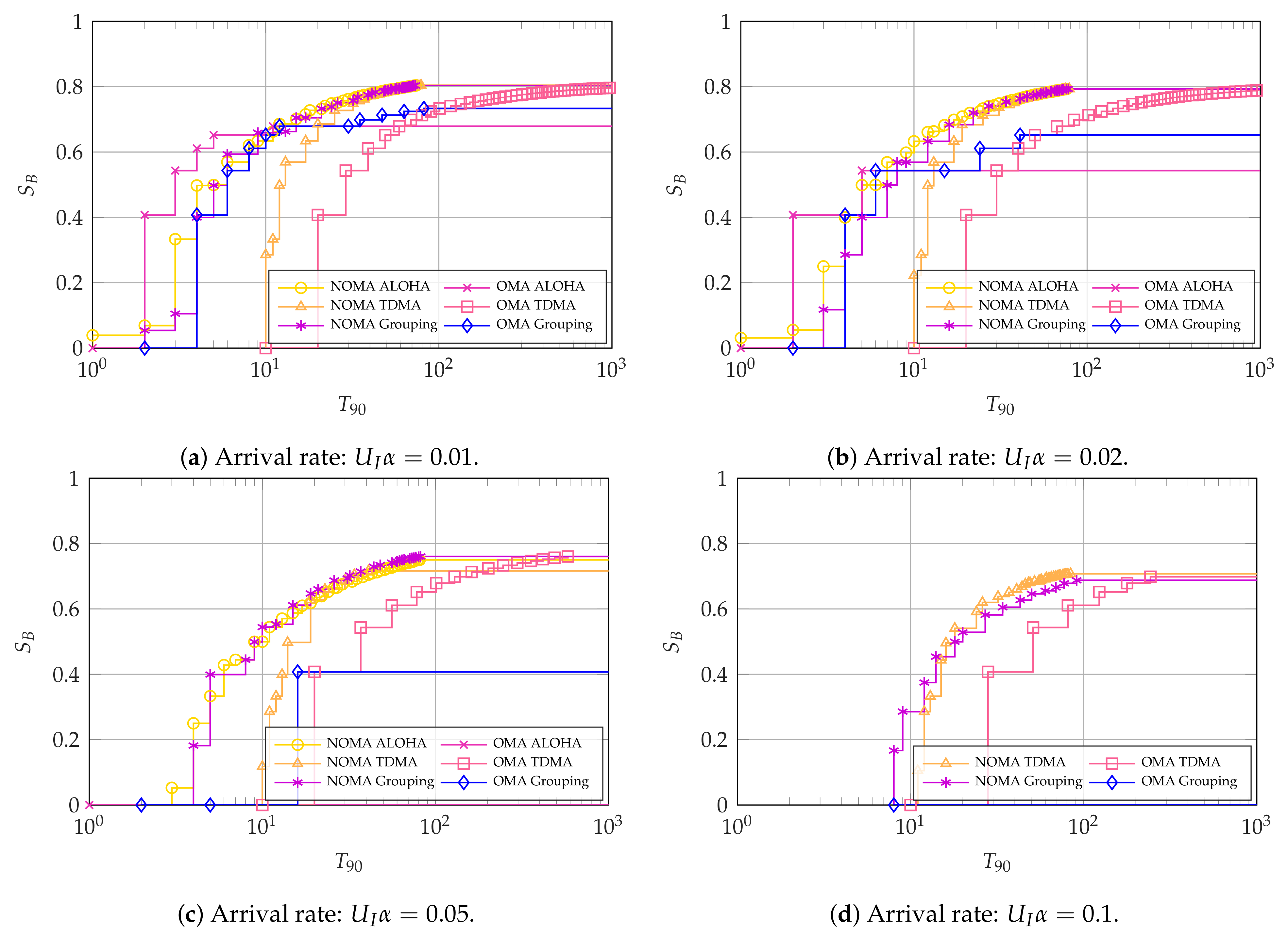
For the case with
, we see an interesting phenomenon in
Figure 7a,b: if the arrival rate is low, OMA ALOHA is the optimal choice if the main KPI is the latency-reliability. However, it is not able to achieve a high broadband user throughput
. Conversely, NOMA, either with ALOHA or grouped access among the intermittent users, can achieve the greatest throughput
. In addition, NOMA ALOHA achieves the lowest latency-reliability with
.
As the arrival rate increases with
, NOMA becomes the Pareto efficient choice for all points in the latency-throughput trade-off, albeit with a small margin. This is observed in
Figure 7c,d, where the Pareto efficient methods are NOMA ALOHA and NOMA TDMA, respectively, with NOMA grouping achieving a close performance. The reason for the better performance of NOMA with high arrival rates is that it allows the intermittent users to access considerably more resources than OMA, which minimizes collisions between them. These collisions are considerably harmful for the system as they cannot be resolved. Therefore, OMA ALOHA becomes infeasible with high arrival rates, whereas OMA TDMA may suffer from queue overflows since intermittent slots are spaced by
slots.
Next,
Figure 8 shows a similar pattern to
Figure 7, but with a much better performance of NOMA with respect to OMA. Specifically, NOMA ALOHA and grouping achieve much better trade-offs when compared to OMA TDMA for the considered arrival rates, with the only exception being that NOMA grouping is not viable for
. This is also the case with all the ALOHA methods, which fail for the cases with
because of the excessive collisions among the intermittent users. Finally, OMA grouping can only achieve the required 90% reliability for the intermittent users with
by making
.
The case with
, displayed in
Figure 9, features a more pronounced differences among the access schemes, indicating that the selection of the access scheme and/or its parameters will be even more critical in massive access scenarios with larger number of users. As in the previous cases, using NOMA becomes more convenient as the total arrival rate increases. OMA ALOHA performs particularly well for low total activation rates, as collisions between intermittent users are rare in this scenario, and in settings that are oriented more towards latency-reliability than broadband user throughput, as increasing the transmission opportunities for the intermittent users can further reduce the probability of collisions between them.
In general, it can be concluded that ALOHA schemes perform better under low arrival rates , whereas TDMA schemes perform better when the aggregate arrival rate increases. This may be expected, in particular as the assumed timeliness parameters of interest are rather stringent. The performance of OMA grouping oftentimes lies between that of OMA ALOHA and TDMA for all values of . This showcases its robustness to the arrival rate , but also that it is not an ideal option to optimize performance. Instead, NOMA grouping achieves a remarkable performance, oftentimes matching or even surpassing the performance of NOMA ALOHA and NOMA TDMA, even with very high rates. Depending on the scenario, the number of groups is highly variable: if , the grouping scheme uses the largest possible number of groups (i.e., with ), making the scheme closer to TDMA than pure ALOHA. On the other hand, ALOHA is more convenient for lower activation rates, so the best grouping performance will be obtained with .
Most interestingly, NOMA schemes outperform OMA under most conditions, with the exception of OMA ALOHA for low arrival rates. This behavior is extremely encouraging for the performance of NOMA in realistic systems, as the collision channel we considered is a worst-case scenario for non-orthogonal access.
As observed in our previous work [
7], by including the probability of channel capture and intra-collision SIC, the performance of non-orthogonal schemes can only improve. Nevertheless, OMA may can also benefit from capture and intra-collision SIC by mitigating collisions between intermittent users.
7. Conclusions
In this work, we investigated the performance trade-offs with orthogonal and non-orthogonal spectrum slicing in a multiple access system with broadband and intermittent users. We derived closed-form expressions for both PAoI and latency-reliability for the intermittent users, along with throughput for the broadband user, in a time-slotted system in which the users share a single frequency channel.
The results illustrate that, by implementing an erasure code at the broadband user, the choice between OMA and NOMA depends on the specific features of the considered scenario and on the objectives of the system designer. In particular, the number of intermittent users and their aggregate arrival rate have major impacts on the preferred slicing and access method for latency-oriented systems. In these cases, TDMA was clearly preferable for the higher arrival rates, whereas ALOHA performed remarkably well with low to medium arrival rates. Interestingly, the opposite effect can be seen for the choice of the access scheme, as NOMA outperformed OMA with higher arrival rates, and orthogonal allocation worked better for lower arrival rates. The NOMA ALOHA scheme presents a case of particular interest, as by correctly tuning the coding parameters for the broadband user, it could oftentimes achieve the best performance trade-offs with low to medium arrival rates in the extreme cases—that is, when the intermittent users required the lowest latency and when the broadband users required the highest throughput. On the other hand, NOMA TDMA is clearly the best access method for latency-reliability with high arrival rates. The PAoI results show that the two access methods are almost equivalent, as long as they are configured properly, and the main driver of performance is the packet generation process. However, OMA TDMA does show significant advantages with respect to the other OMA schemes, as it avoids collisions entirely, whereas the other OMA schemes may still have collisions between intermittent users. These results, obtained in the simple collision channel without capture, showcase the potential of NOMA schemes in scenarios with heterogeneous service types as channel capture and intra-collision SIC greatly improve its performance.
Future work on the subject can be oriented in multiple directions: First, analyzing the system with MPR is definitely a priority, as the worst-case analysis has already shown the advantages of NOMA. Secondly, more realistic systems could be investigated, with time-dependent arrival patterns or with multiple frequency channels, which would add an interesting dimension to the problem by providing parallel resources. The possibility of using packet repetition to increase the intermittent users’ reliability is another interesting facet that can be examined, although the complexity of the system may grow beyond the possibility of analytical tools, requiring a simulation-based approach.