Edge Computing Resource Allocation for Dynamic Networks: The DRUID-NET Vision and Perspective
Abstract
:1. Introduction
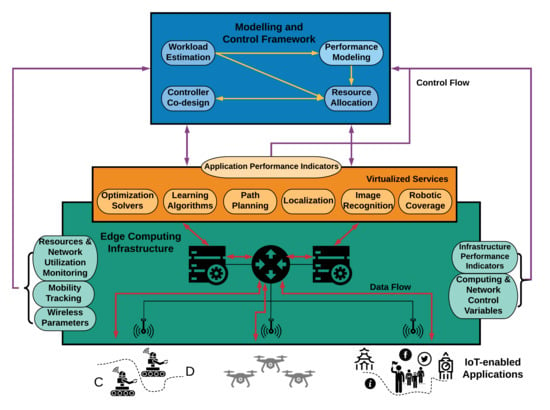
The DRUID-NET Perspective and Contributions
- -
- Workload Profile: The IoT applications generate time-varying traffic in terms of request size and number of flows. Additionally, the involved wireless communication between the mobile devices and the back-end software components introduces additional uncertainties that considerably affect the offloading decision and the resource scheduling at the edge computing infrastructure. Contrarily to existing average traffic characteristics, building dynamic traffic profiles and prediction mechanisms will enable more accurate, adaptive, and successful data offloading and resource allocation mechanisms.
- -
- Performance Modelling: Most of the existing models for describing the performance of IoT-enabled applications are empirical and usually focus on a specific performance metric, e.g., response time, throughput, energy consumption, etc. These models cannot adequately capture the dynamic nature of the emerging applications, which in turn leads to either performance degradation or resource over-provisioning. On the other hand, the DRUID-NET framework proposes formal dynamic multi-input multi-output performance models applicable to various IoT applications. These types of models enable the design of novel controllers for finer regulation of Quality of Service (QoS) metrics.
- -
- Resource Allocation: Usually, most studies in the literature combine a static performance model with solving an optimization problem. However, this approach assumes that the workload does not vary significantly, which limits their validity, applicability, and exploitability. In contrast to these approaches, we envisage to design stabilizing controllers in order to guarantee the feasibility of the resource scheduling and the performance requirements.
- -
- Control co-design The DRUID-NET framework examines specifically the case where the application is the controller design and its implementation for dynamic processes. In this setting, the performance of the closed-loop system is considered in the overall application performance. The control co-design approach aims to design feedback mechanisms achieving closed-loop system properties such as reachability, stabilization, and other complex specifications, and simultaneously design and implement resource allocation algorithms for the dynamic network.
2. Related Work and Motivation
2.1. IoT Workload Profile
2.2. Performance Modeling and Resource Allocation in Cloud and Edge Computing
2.3. Control-Theoretic Resource Allocation and Control Co-Design
3. DRUID-NET Conceptual Architecture
3.1. IoT Workload Profiling
3.1.1. IoT Applications Classification
3.1.2. IoT Applications Workload Prediction
3.2. Performance Modeling
3.3. Resource Allocation
3.3.1. Static Resource Allocation
3.3.2. Dynamic Resource Allocation
3.4. Co-Design of Controllers
4. IoT-Enabled Applications
4.1. Collaborative Robotics
4.2. Rapid Resource Deployment for Physical Disaster Scenarios
4.3. Mobility-Aware Edge Computing
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| MDPI | Multidisciplinary Digital Publishing Institute |
| DOAJ | Directory of Open Access Journals |
| IoT | Internet of Things |
| UAV | Unmanned Aerial Vehicle |
| UGV | Unmanned Ground Vehicle |
| MEC | Multi-Access Edge Computing |
| DRUID-NET | eDge computing ResoUrce allocatIon for Dynamic NETworks |
| QoS | Quality of Service |
| QoE | Quality of Experience |
| NFV | Network Functions Virtualization |
| SDN | Software Defined Networks |
| 5G | Fifth Generation |
| SC | Service Chain |
| VNF | Virtualized Network Function |
| VM | Virtual Machine |
| NCS | Networked Control Systems |
References
- Cisco. White Paper. Internet of Things at a Glance. Available online: https://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/iot-aag.pdf (accessed on 12 April 2020).
- Ericsson. Mobility Report—q4, 2018. Available online: https://www.ericsson.com/4932c2/assets/local/mobility-report/documents/2019/emr-q4-update-2018.pdf (accessed on 12 April 2020).
- Hayat, S.; Yanmaz, E.; Muzaffar, R. Survey on unmanned aerial vehicle networks for civil applications: A communications viewpoint. IEEE Commun. Surv. Tutor. 2016, 18, 2624–2661. [Google Scholar] [CrossRef]
- ETSI. Multi-access Edge Computing (MEC) Group. Available online: https://www.etsi.org/technologies/multi-access-edge-computing (accessed on 12 April 2020).
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Jeong, S.; Simeone, O.; Kang, J. Mobile edge computing via a UAV-mounted cloudlet: Optimization of bit allocation and path planning. IEEE Trans. Vehic. Techn. 2017, 67, 2049–2063. [Google Scholar] [CrossRef] [Green Version]
- He, D.; Qiao, Y.; Chan, S.; Guizani, N. Flight security and safety of drones in airborne fog computing systems. IEEE Commun. Mag. 2018, 56, 66–71. [Google Scholar] [CrossRef]
- Valentino, R.; Jung, W.S.; Ko, Y.B. Opportunistic computational offloading system for clusters of drones. In Proceedings of the 20th International IEEE Conference on Advanced Communication Technology, Korea, South, 11–14 February 2018; pp. 303–306. [Google Scholar]
- Abdelzaher, T.; Hao, Y.; Jayarajah, K.; Misra, A.; Skarin, P.; Yao, S.; Weerakoon, D.; Undefinedrzén, K. Five Challenges in Cloud-Enabled Intelligence and Control. ACM Trans. Internet Technol. 2020, 20. [Google Scholar] [CrossRef] [Green Version]
- Kiani, A.; Ansari, N.; Khreishah, A. Hierarchical Capacity Provisioning for Fog Computing. IEEE/ACM Trans. Net. 2019, 27, 962–971. [Google Scholar] [CrossRef]
- Villari, M.; Fazio, M.; Dustdar, S.; Rana, O.; Ranjan, R. Osmotic Computing: A New Paradigm for Edge/Cloud Integration. IEEE Cloud Comp. 2016, 3, 76–83. [Google Scholar] [CrossRef] [Green Version]
- Li, Y.; Chen, Y.; Lan, T.; Venkataramani, G. MobiQoR: Pushing the Envelope of Mobile Edge Computing Via Quality-of-Result Optimization. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 1261–1270. [Google Scholar]
- Leivadeas, A.; Falkner, M.; Lambadaris, I.; Ibnkahla, M.; Kesidis, G. Balancing Delay and Cost in Virtual Network Function Placement and Chaining. In Proceedings of the 2018 IEEE 4th International Conference on Network Softwarization and Workshops (NetSoft), Montreal, QC, Canada, 25–29 June 2018; pp. 1–9. [Google Scholar]
- Leivadeas, A.; Kesidis, G.; Ibnkahla, M.; Lambadaris, I. VNF Placement Optimization at the Edge and Cloud. Future Internet 2019, 11, 69. [Google Scholar] [CrossRef] [Green Version]
- Nwanganga, F.; Chawla, N. Using Structural Similarity to Predict Future Workload Behavior in the Cloud. In Proceedings of the 2019 IEEE 12th International Conference on Cloud Computing (CLOUD), Milan, Italy, 8–13 July 2019; pp. 132–136. [Google Scholar]
- Ra, M.; Lee, H. Fighting with Unknowns: Estimating the Performance of Scalable Distributed Storage Systems with Minimal Measurement Data. In Proceedings of the 2019 35th Symposium on Mass Storage Systems and Technologies (MSST), Santa Clara, CA, USA, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Yao, S.; Zhao, Y.; Hu, S.; Abdelzaher, T. QualityDeepSense: Quality-Aware Deep Learning Framework for Internet of Things Applications with Sensor-Temporal Attention. In Proceedings of the 2nd International Workshop on Embedded and Mobile Deep Learning, Munich, Germany, 15 June 2018. [Google Scholar]
- Prakah-Asante, K.O.; Tonshal, B.; Yang, H.; Strumolo, G.; Chen, Y.; Rankin, J.S. Workload estimation for mobile device feature integration. U.S. Patent 9,889,862, 13 February 2018. [Google Scholar]
- Sanchez-Alvarez, D.; Linaje, M.; Rodriguez-Pérez, F. A Framework to Design the Computational Load Distribution of Wireless Sensor Networks in Power Consumption Constrained Environments. Sensors 2018, 18, 954. [Google Scholar] [CrossRef] [Green Version]
- Pinto Neto, J.B.; Gomes, L.; Ortiz, F.; Almeida, T.; Campista, M.; Kosmalski, M.; Costa, L.; Mitton, N. An Accurate Cooperative Positioning System for Vehicular Safety Applications. Comp. Electr. Engin. 2019, 83, 1–13. [Google Scholar] [CrossRef] [Green Version]
- Laftchiev, E.; Lagoa, C.M.; Brennan, S. Vehicle localization using in-vehicle pitch data and dynamical models. IEEE Trans. Intellig. Transp. Syst. 2015, 16, 206–220. [Google Scholar] [CrossRef]
- Belhajem, I.; Ben Maissa, Y.; Tamtaoui, A. A robust low cost approach for real time car positioning in a smart city using Extended Kalman Filter and evolutionary machine learning. In Proceedings of the 4th IEEE International Colloquium on Information Science and Technology (CiSt), Tangier, Morocco, 24–26 October 2016. [Google Scholar]
- Toldov, V.; Clavier, L.; Loscrí, V.; Mitton, N. A Thompson Sampling Approach to Channel Exploration- Exploitation Problem in Multihop Cognitive Radio Networks. In Proceedings of the 27th annual IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–8 September 2016; pp. 1–6. [Google Scholar]
- Razafimandimby, C.; Loscrí, V.; Maria Vegni, A.; Aourir, D.; Neri, A. A Bayesian approach for an efficient data reduction in IoT. In Proceedings of the InterIoT 2017—3rd EAI International Conference on Interoperability in IoT, Valencia, Spain, 7 November 2017; pp. 1–7. [Google Scholar]
- Li, X.; Mitton, N.; Simplot-Ryl, I.; Simplot-Ryl, D. Dynamic Beacon Mobility Scheduling for Sensor Localization. IEEE Trans. Parl. Distrib Syst. 2012, 23, 1439–1452. [Google Scholar] [CrossRef]
- Ardagna, D.; Panicucci, B.; Trubian, M.; Zhang, L. Energy-aware autonomic resource allocation in multitier virtualized environments. IEEE Trans. Serv. Comp. 2010, 5, 2–19. [Google Scholar] [CrossRef] [Green Version]
- Chen, C.-T. Linear System Theory and Design; Oxford University Press, Inc.: New York, NY, USA, 1998. [Google Scholar]
- Ullah, A.; Li, J.; Shen, Y.; Hussain, A. A control theoretical view of cloud elasticity: taxonomy, survey and challenges. Clust. Comp. 2018, 21, 1735–1764. [Google Scholar] [CrossRef] [Green Version]
- Dechouniotis, D.; Leontiou, N.; Athanasopoulos, N.; Christakidis, A.; Denazis, S. A control-theoretic approach towards joint admission control and resource allocation of cloud computing services. Intern. J. Netw. Manag. 2015, 25, 159–180. [Google Scholar] [CrossRef] [Green Version]
- Leontiou, N.; Dechouniotis, D.; Denazis, S.; Papavassiliou, S. A hierarchical control framework of load balancing and resource allocation of cloud computing services. Comp. Elect. Eng. 2018, 67, 235–251. [Google Scholar] [CrossRef]
- Zhang, W.; Han, B.; Hui, P. On the networking challenges of mobile augmented reality. In Proceedings of the Workshop on Virtual Reality and Augmented Reality Network, Los Angeles, CA, USA, 11 August 2017; pp. 24–29. [Google Scholar]
- Kalatzis, N.; Avgeris, M.; Dechouniotis, D.; Papadakis-Vlachopapadopoulos, K.; Roussaki, I.; Papavassiliou, S. Edge computing in IoT ecosystems for UAV-enabled early fire detection. In Proceedings of the 2018 IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Italy, 18–20 June 2018; pp. 106–114. [Google Scholar]
- Sonmez, C.; Ozgovde, A.; Ersoy, C. Fuzzy workload orchestration for edge computing. IEEE Trans. Net. Serv. Manag. 2019, 16, 769–782. [Google Scholar] [CrossRef]
- Guan, G.; Dong, W.; Zhang, J.; Gao, Y.; Gu, T.; Bu, J. Queec: QoE-aware Edge Computing for Complex IoT Event Processing Under Dynamic Workloads. In Proceedings of the ACM Turing Celebration Conference, Chengdu, China, 17–19 May 2019. [Google Scholar]
- Jalali, F.; Hinton, K.; Ayre, R.; Alpcan, T.; Tucker, R.S. Fog computing may help to save energy in cloud computing. IEEE J. Sel. Areas Comm. 2016, 34, 1728–1739. [Google Scholar] [CrossRef]
- Lyu, X.; Tian, H.; Jiang, L.; Vinel, A.; Maharjan, S.; Gjessing, S.; Zhang, Y. Selective offloading in mobile edge computing for the green internet of things. IEEE Netw. 2018, 32, 54–60. [Google Scholar] [CrossRef]
- Gao, B.; Zhou, Z.; Liu, F.; Xu, F. Winning at the starting line: Joint network selection and service placement for mobile edge computing. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 1459–1467. [Google Scholar]
- Leivadeas, A.; Kesidis, G.; Falkner, M.; Lambadaris, I. A graph partitioning game theoretical approach for the VNF service chaining problem. IEEE Trans. Netw. Serv. Manag. 2017, 14, 890–903. [Google Scholar] [CrossRef]
- Hegyi, A.; Flinck, H.; Ketyko, I.; Kuure, P.; Nemes, C.; Pinter, L. Application Orchestration in Mobile Edge Cloud Placing of IoT Applications to the Edge. In Proceedings of the IEEE Int. Workshop on Foundations and Applications of Self* Systems, Augsburg, Germany, 12–16 September 2016. [Google Scholar]
- Nam, Y.; Song, S.; Chung, J.M. Clustered NFV Service Chaining Optimization in Mobile Edge Clouds. IEEE Commun. Lett. 2017, 21, 350–353. [Google Scholar] [CrossRef]
- Barcelo, M.; Correa, A.; Tulino, A.; Vicario, J.L.; Morell, A. IoT-Cloud Service Optimization in Next, Generation Smart Environments. IEEE J. Sel. Areas Commun. 2016, 34, 4077–4090. [Google Scholar] [CrossRef]
- Zanzi, L.; Giust, F.; Sciancalepore, V. M2EC: A Multi-tenant Resource Orchestration in Multi-Access Edge Computing Systems. In Proceedings of the IEEE International Conference on Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Wang, J.; Qi, H.; Li, K.; Zhou, X. PRSFC-IoT: A Performance and Resource Aware Orchestration System of Service Function Chaining for Internet of Things. IEEE J. Inter. Things 2018, 5, 1400–1410. [Google Scholar] [CrossRef]
- Cao, J.; Zhang, Y.; An, W.; Chen, X.; Sun, J.; Han, Y. VNF-FG Design and VNF Placement for 5G Mobile Networks. Springer J. Inform. Sci. 2017, 60, 040302. [Google Scholar] [CrossRef]
- Jemaa, F.; Pujolle, G.; Pariente, M. QoS-aware VNF placement Optimization in Edge-Central Carrier Cloud Architecture. In Proceedings of the IEEE International Conference on Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016. [Google Scholar]
- Avgeris, M.; Dechouniotis, D.; Athanasopoulos, N.; Papavassiliou, S. Adaptive resource allocation for computation offloading: A control-theoretic approach. ACM Trans Inter. Techn. 2019, 19, 1–20. [Google Scholar] [CrossRef] [Green Version]
- Gupta, R.; Chow, M. Networked control system: Overview and research trends. IEEE Trans. Indust. Electron. 2010, 57, 2527–2535. [Google Scholar] [CrossRef]
- Zhang, W.; Branicky, M.; Phillips, S. Stability of networked control systems. IEEE Cont. Syst. 2001, 21, 84–99. [Google Scholar]
- Wen, S.; Guo, G. A survey of recent results in networked control systems. Proc. IEEE 2007, 95, 138–162. [Google Scholar]
- Elia, N.; Mitter, S. Stabilization of linear systems with limited information. IEEE Trans. Autom. Cont. 2001, 46, 1384–1400. [Google Scholar] [CrossRef] [Green Version]
- Simon, D.; Robert, D.; Sename, O. Robust control/scheduling co-design: application to robot control. In Proceedings of the 11th IEEE Real Time and Embedded Technology and Applications Symposium, San Francisco, CA, USA, 7–10 March 2005. [Google Scholar]
- Xia, F.; Sun, Y. Control-Scheduling Codesign: A Perspective on Integrating Control and Computing. Dyn. Contin. Discr. Impuls. Syst. Ser. B 2005, 13, 1352–1358. [Google Scholar]
- Branicky, M.; Phillips, S.; Zhang, W. Scheduling and feedback co-design for networked control systems. In Proceedings of the 41st IEEE Conference on Decision and Control, Las Vegas, NV, USA, 10–13 December 2002. [Google Scholar]
- Bertsekas, D.; Tsitsiklis, J. Parallel and Distributed Computation: Numerical Methods; Prentice Hall Englewood: Cliffs, NJ, USA, 1989. [Google Scholar]
- Kashyap, A.; Başar, T.; Srikant, R. Quantized consensus. Automatica 2007, 43, 1192–1203. [Google Scholar] [CrossRef]
- Schenato, L.; Sinopoli, B.; Franceschetti, M.; Poolla, K.; Sastry, S. Foundations of control and estimation over lossy networks. Proc. IEEE 2007, 95, 163–187. [Google Scholar] [CrossRef] [Green Version]
- Jungers, R.; Kundu, A.; Heemels, W. Observability and controllability analysis of linear systems subject to data losses. IEEE Trans. Autom. Cont. 2018, 63, 3361–3376. [Google Scholar] [CrossRef] [Green Version]
- Athanasopoulos, N.; Jungers, R. Combinatorial methods for invariance and safety of hybrid systems. Automatica 2018, 98, 130–140. [Google Scholar] [CrossRef] [Green Version]
- Dilip, A.; Athanasopoulos, N.; Jungers, R. The impact of packet dropouts on the reachability energy. In Proceedings of the International Conference on Cyber-Physical Systems (ICCPS), Porto, Portugal, 11–13 April 2018. [Google Scholar]
- Zhang, L.; Hristu-Varsakelis, D. Communication and control co-design for networked control systems. Automatica 2006, 42, 953–958. [Google Scholar] [CrossRef]
- Guo, G. A switching system approach to sensor and actuator assignment for stabilisation via limited multi-packet transmitting channels. Intern. J. Cont. 2011, 84, 78–93. [Google Scholar] [CrossRef]
- Wen, S.; Guo, G. Control and resource allocation of cyber-physical systems. IET Cont. Theory Applic. 2016, 10, 2038–2048. [Google Scholar] [CrossRef]
- Martí, P.; Camacho, A.; Velasco, M.; Gaid, M. Runtime allocation of optional control jobs to a set of CAN-based networked control systems. IEEE Trans. Indust. Inform. 2010, 6, 503–520. [Google Scholar] [CrossRef]
- Tabuada, P. Event-triggered real-time scheduling of stabilizing control tasks. IEEE Trans. Autom. Cont. 2007, 52, 1680–1685. [Google Scholar] [CrossRef] [Green Version]
- Abdelrahim, M.; Postoyan, R.; Daafouz, J.; Nei, D.; Heemels, M. Co-design of output feedback laws and event-triggering conditions for the L2-stabilization of linear systems. Automatica 2018, 87, 337–344. [Google Scholar] [CrossRef] [Green Version]
- Donkers, M.; Heemels, W. Co-design of output feedback laws and event-triggering conditions for the L2-stabilization of linear systems. IEEE Trans. Autom. Cont. 2012, 57, 1362–1376. [Google Scholar] [CrossRef]
- Goebel, R.; Sanfelice, R.; Teel, A. Hybrid dynamical systems. IEEE Cont. Syst. Magaz. 2009, 29, 28–93. [Google Scholar] [CrossRef]
- Matveev, A.; Savkin, A. Estimation and Control over Communication Networks; Springer Science & Business Media: Boston, MA, USA, 2009. [Google Scholar]
- Garoche, P. Formal Verification of Control System Software; Princeton University Press: Princeton, NJ, USA, 2019. [Google Scholar]




© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dechouniotis, D.; Athanasopoulos, N.; Leivadeas, A.; Mitton, N.; Jungers, R.; Papavassiliou, S. Edge Computing Resource Allocation for Dynamic Networks: The DRUID-NET Vision and Perspective. Sensors 2020, 20, 2191. https://0-doi-org.brum.beds.ac.uk/10.3390/s20082191
Dechouniotis D, Athanasopoulos N, Leivadeas A, Mitton N, Jungers R, Papavassiliou S. Edge Computing Resource Allocation for Dynamic Networks: The DRUID-NET Vision and Perspective. Sensors. 2020; 20(8):2191. https://0-doi-org.brum.beds.ac.uk/10.3390/s20082191
Chicago/Turabian StyleDechouniotis, Dimitrios, Nikolaos Athanasopoulos, Aris Leivadeas, Nathalie Mitton, Raphael Jungers, and Symeon Papavassiliou. 2020. "Edge Computing Resource Allocation for Dynamic Networks: The DRUID-NET Vision and Perspective" Sensors 20, no. 8: 2191. https://0-doi-org.brum.beds.ac.uk/10.3390/s20082191