Securing SDN-Based IoT Group Communication
Abstract
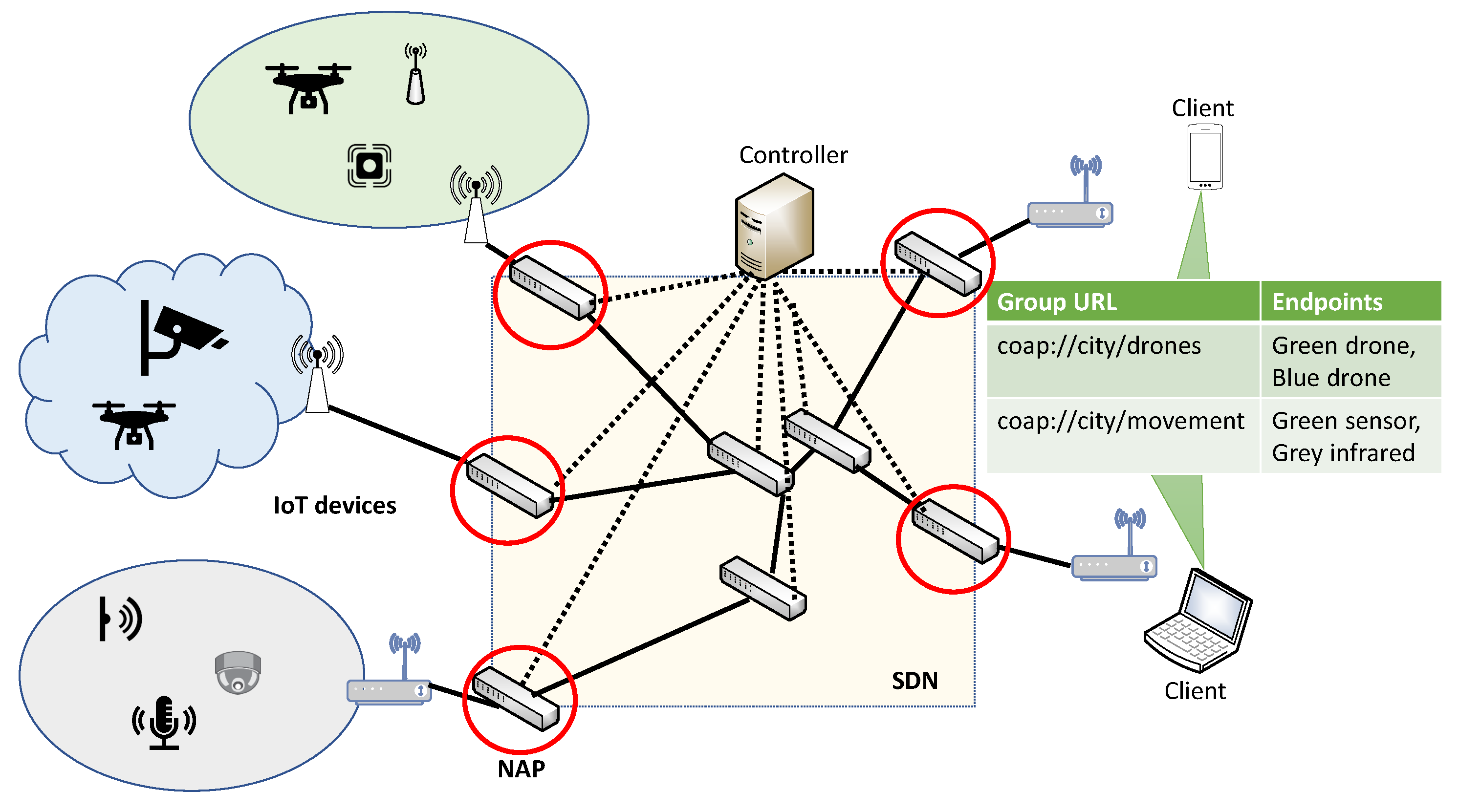
:1. Introduction
- We design an IoT onboarding process that ensures that only authorized IoT devices participate in a group;
- We leverage linked-data signatures to provide advertisement validity and proof of ownership;
- We extend our solution to support selective advertisement of resources using zero-knowledge proofs.
2. Background
2.1. SDN and Bloom Filter-Based Forwarding
2.2. CoAP and CoAP Group Communication
2.3. Web of Things
3. Overview
3.1. System Entities and Security Assumptions
3.2. IoT Device Onboarding
| 1 | { |
| 2 | “context”: “https://www.w3.org/.../v1”, |
| 3 | ... |
| 4 | “id”: EndpointID, |
| 5 | } |
| 6 | “properties”: {…}, |
| 7 | “actions”: { |
| 8 | “turnoff_sensor”: { |
| 9 | “forms”: |
| 10 | [{ |
| 11 | “href”: “coap://gate7.stadium/sensor1/turnoff”, |
| 12 | “cov:methodName”: “POST” |
| 13 | }, |
| 14 | { |
| 15 | “href”: “coap://stadium/sensors/turnoff”, |
| 16 | “cov:methodName”: “POST” |
| 17 | “subprotocol”: “cov:group” |
| 18 | }, |
| 19 | { |
| 20 | “href”: “coap://city1/sensors/turnoff”, |
| 21 | “cov:methodName”: “POST” |
| 22 | “subprotocol”: “cov:group” |
| 23 | }] |
| 24 | } |
| 25 | }, |
| 26 | “events”: {...} |
| 27 | } |
| 1 | { |
| 2 | “type”: “Ed25519Signature2020”, |
| 3 | “created”: “2021-17-06T11:01:24Z”, |
| 4 | “verificationMethod”: NetworkID, |
| 5 | “proofPurpose”: “assertionMethod”, |
| 6 | “proofValue”: "VqpLMweBrSxMY2x…aqA3Q1geV6” |
| 7 | } |
3.3. SDN-Based IoT Group Communication
3.3.1. Resource Advertisement
3.3.2. CoAP Group Request
- From the lookup table, it retrieves the identifiers of the CoAP servers that are members of the group;
- If it knows a for all retrieved identifiers, it proceeds to step 4;
- It constructs a message that includes all identifiers for which it does not know a and sends it to a “special” MAC address used for forcing SDN switches to forward a packet to the controller. The controller responds with a list of that is eventually returned back to the client;
- It creates a new by ORing the identifiers of the retrieved identifiers and forwards the CoAP request using the created . Due to the properties of Bloom filter-based forwarding (see [7] for more details), the CoAP request will be forwarded to the appropriate IoT devices.
4. Implementation and Evaluation
4.1. Implementation
4.2. Security Evaluation
4.3. Private Advertisements Using ZKPs
5. Related Research
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Jiang, Y.; Miao, Y.; Alzahrani, B.; Barnawi, A.; Alotaibi, R.; Hu, L. Ultra Large-Scale Crowd Monitoring System Architecture and Design Issues. IEEE Internet Things J. 2021, 8, 10356–10366. [Google Scholar] [CrossRef]
- Rahman, A.; Dijk, E. Group Communication for the Constrained Application Protocol (CoAP). 2014. Available online: https://www.hjp.at/doc/rfc/rfc7390.html (accessed on 5 August 2021).
- Kaebish, S.; Kamiya, T.; McCool, M.; Charpenay, V.; Kovatsch, M. Web of Things Thing Description. 2020. Available online: https://www.w3.org/TR/wot-binding-templates/ (accessed on 5 August 2021).
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A Survey on Software-Defined Networking. IEEE Commun. Surv. Tutor. 2015, 17, 27–51. [Google Scholar] [CrossRef]
- Lara, A.; Kolasani, A.; Ramamurthy, B. Network Innovation using OpenFlow: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 493–512. [Google Scholar] [CrossRef] [Green Version]
- Bloom, B.H. Space/time trade-offs in hash coding with allowable errors. Commun. ACM 1970, 13, 422–426. [Google Scholar] [CrossRef]
- Reed, M.J.; Al-Naday, M.; Thomos, N.; Trossen, D.; Petropoulos, G.; Spirou, S. Stateless multicast switching in software defined networks. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–7. [Google Scholar] [CrossRef] [Green Version]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP). 2014. Available online: https://iottestware.readthedocs.io/en/master/coap_rfc.html (accessed on 5 August 2021).
- Kovatsch, M.; Matsukura, R.; Lagally, M.; Kawaguchi, T.; Toumura, K.; Kajimoto, K. Web of Things Architecture. 2020. Available online: https://www.w3.org/TR/wot-architecture/ (accessed on 5 August 2021).
- Kellogg, G.; Champin, P.; Longley, D. JSON-LD 1.1. 2020. Available online: https://www.w3.org/TR/json-ld11/ (accessed on 5 August 2021).
- Bernstein, D.J.; Duif, N.; Lange, T.; Schwabe, P.; Yang, B.Y. High-speed high-security signatures. J. Cryptogr. Eng. 2012, 2, 77–89. [Google Scholar] [CrossRef] [Green Version]
- Josefsson, S. The Base16, Base32, and Base64 Data Encodings. 2006. Available online: https://www.hjp.at/doc/rfc/rfc4648.html (accessed on 5 August 2021).
- Longley, D.; Sporny, M. Linked Data Proofs 1.0. 2021. Available online: https://w3c-ccg.github.io/ld-proofs/ (accessed on 5 August 2021).
- Fotiou, N.; Mendrinos, D.; Polyzos, G.C. Edge-assisted traffic engineering and applications in the IoT. In Proceedings of the 2018 Workshop on Mobile Edge Communications (MECOMM’18), Budapest, Hungary, 20–25 August 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 37–42. [Google Scholar]
- Alzahrani, B.; Fotiou, N. Enhancing Internet of Things Security using Software-Defined Networking. J. Syst. Archit. 2020, 110, 101779. [Google Scholar] [CrossRef]
- Pfaff, B.; Pettit, J.; Koponen, T.; Jackson, E.; Zhou, A.; Rajahalme, J.; Gross, J.; Wang, A.; Stringer, J.; Shelar, P.; et al. The design and implementation of open vSwitch. In Proceedings of the 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI 15), Oakland, CA, USA, 4–6 May 2015; USENIX Association: Oakland, CA, USA, 2015; pp. 117–130. [Google Scholar]
- Gude, N.; Koponen, T.; Pettit, J.; Pfaff, B.; Casado, M.; McKeown, N.; Shenker, S. NOX: Towards an Operating System for Networks. SIGCOMM Comput. Commun. Rev. 2008, 38, 105–110. [Google Scholar] [CrossRef]
- Lantz, B.; Heller, B.; McKeown, N. A network in a laptop: Rapid prototyping for software-defined networks. In Proceedings of the 9th ACM SIGCOMM Workshop on Hot Topics in Networks, Monterey, CA, USA, 20–21 October 2010; ACM: New York, NY, USA, 2010; pp. 19:1–19:6. [Google Scholar]
- Goldreich, O.; Oren, Y. Definitions and properties of zero-knowledge proof systems. J. Cryptol. 1994, 7, 1–32. [Google Scholar] [CrossRef]
- Quisquater, J.J.; Quisquater, M.; Quisquater, M.; Quisquater, M.; Guillou, L.; Guillou, M.A.; Guillou, G.; Guillou, A.; Guillou, G.; Guillou, S. How to explain zero-knowledge protocols to your children. In Proceedings of the Conference on the Theory and Application of Cryptology, Santa Barbara, CA, USA, 20–24 August 1989; pp. 628–631. [Google Scholar]
- Looker, T.; Steele, O. BBS+ Signatures 2020. 2020. Available online: https://w3c-ccg.github.io/ldp-bbs2020/ (accessed on 5 August 2021).
- Sakemi, Y. (Ed.) Pairing-Friendly Curves v09. 2020. Available online: https://datatracker.ietf.org/doc/html/draft-irtf-cfrg-pairing-friendly-curves-09 (accessed on 5 August 2021).
- W3C. JSON-LD 1.1 Framing. 2020. Available online: https://www.w3.org/TR/json-ld11/ (accessed on 16 July 2020).
- Tiloca, M.; Selander, G.; Palombini, F.; Park, J. Group OSCORE—Secure Group Communication for CoAP. 2021. Available online: https://www.ietf.org/id/draft-ietf-core-oscore-groupcomm-12.html (accessed on 5 August 2021).
- Tiloca, M.; Nikitin, K.; Raza, S. Axiom: DTLS-Based Secure IoT Group Communication. ACM Trans. Embed. Comput. Syst. 2017, 16, 1–29. [Google Scholar] [CrossRef] [Green Version]
- Park, C.S. Security Architecture for Secure Multicast CoAP Applications. IEEE Internet Things J. 2020, 7, 3441–3452. [Google Scholar] [CrossRef]
- Basu, S.S.; Tripathy, S. Securing Multicast Group Communication in IoT-Enabled Systems. IETE Tech. Rev. 2019, 36, 83–93. [Google Scholar] [CrossRef]
- Gündoğan, C.; Amsüss, C.; Schmidt, T.C.; Wählisch, M. IoT content object security with OSCORE and NDN: A first experimental comparison. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–26 June 2020; pp. 19–27. [Google Scholar]
- Wijnands, I.; Rosen, E.C.; Aldrin, S.; Przygienda, T.; Dolganow, A. Multicast Using Bit Index Explicit Replication (BIER). 2017. Available online: https://www.hjp.at/doc/rfc/rfc8279.html (accessed on 5 August 2021).
- Hui, J.; Kelsey, R. M Multicast Protocol for Low-Power and Lossy Networks (MPL). 2016. Available online: https://tex2e.github.io/rfc-translater/html/rfc7731.html (accessed on 5 August 2021).
- Gündoğan, C.; Amsüss, C.; Schmidt, T.C.; Wählisch, M. Toward a restful information-centric web of things: A deeper look at data orientation in CoAP. In Proceedings of the 7th ACM Conference on Information-Centric Networking (ICN’20), Virtual, 29 September–1 October 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 77–88. [Google Scholar]
- Felde, N.; Grundner-Culemann, S.; Guggemos, T. Authentication in dynamic groups using identity-based signatures. In Proceedings of the 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Limassol, Cyprus, 15–17 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- W3C Credentials Community Group. A Primer for Decentralized Identifiers. 2019. Available online: https://w3c-ccg.github.io/did-primer/ (accessed on 5 August 2021).
- Kortesniemi, Y.; Lagutin, D.; Elo, T.; Fotiou, N. Improving the Privacy of IoT with Decentralised Identifiers (DIDs). J. Comp. Netw. Commun. 2019, 2019, 8706760:1–8706760:10. [Google Scholar] [CrossRef]
| Operation | Desktop | Raspberry Pi |
|---|---|---|
| LDP generation | 0.93 ms | 5.2 ms |
| LDP verification | 0.83 ms | 6.0 ms |
| Operation | Desktop | Raspberry Pi |
|---|---|---|
| LDP | 174.6 ms | 999.2 ms |
| LDP verification | 74.3 ms | 1004.0 ms |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alzahrani, B.; Fotiou, N. Securing SDN-Based IoT Group Communication. Future Internet 2021, 13, 207. https://0-doi-org.brum.beds.ac.uk/10.3390/fi13080207
Alzahrani B, Fotiou N. Securing SDN-Based IoT Group Communication. Future Internet. 2021; 13(8):207. https://0-doi-org.brum.beds.ac.uk/10.3390/fi13080207
Chicago/Turabian StyleAlzahrani, Bander, and Nikos Fotiou. 2021. "Securing SDN-Based IoT Group Communication" Future Internet 13, no. 8: 207. https://0-doi-org.brum.beds.ac.uk/10.3390/fi13080207






