Separable Reversible Data Hiding in Encryption Image with Two-Tuples Coding
Abstract
:1. Introduction
- A new two-tuples coding compression method is proposed, which can be utilized in the field of data hiding, yet it serves as an alternative method of lossless image compression. The proposed two-tuples coding effectively compresses the high-order bits of carrier image and produces large independent redundant space, resulting in a higher compression ratio.
- Our RDH-EI scheme eliminates (i) the conventional process of integrating additional image encryption algorithms by directly generating an encrypting image during image coding, and (ii) the pre-requisite for the content owner to prepare the embeddable space in advance. Consequently, the proposed RDH-EI scheme significantly lessens the complexity of recent RDH-EI schemes and minimizes the risk of destroying image in data hider side when embedding additional data.
- In our RDH-EI scheme, the additional data are embedded independently of the carrier image in the redundancy filling bits, and this ensures that image restoration and additional data extraction are separable and reversible.
- Our RDH-EI scheme has a high generality property, which can accommodate any form and feasible size of the carrier image.
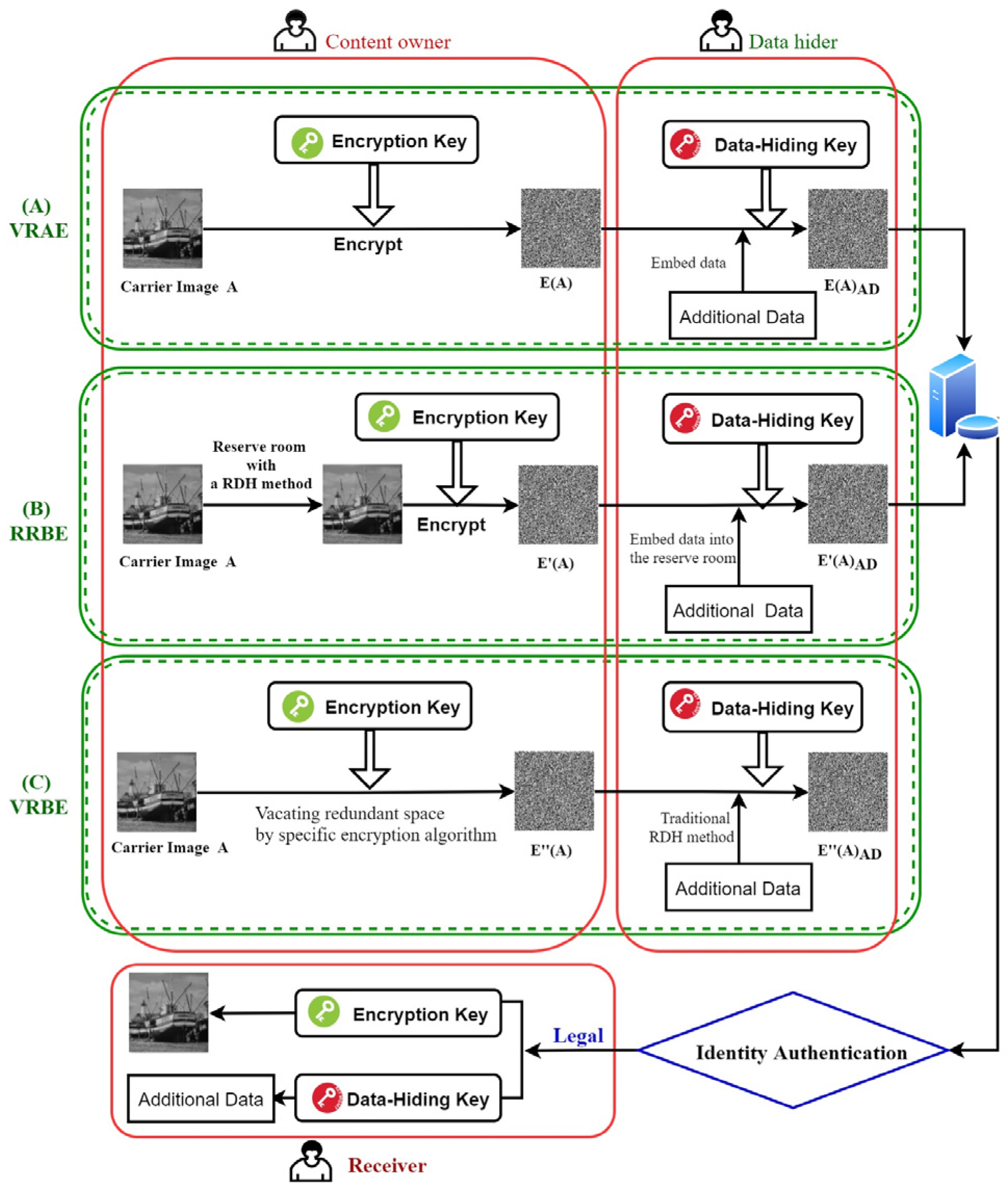
- The proposed RDH-EI scheme is constructed based on Vacating Room by Encryption (VRBE). Therefore, it enjoys a higher security level compared to the conventional Vacating Room after Encryption (VRAE) and Reserving Room before Encryption (RRBE).
2. RDH-EI and Related Works
- Vacating Room After Encryption (VRAE) Method
- Reserving Room Before Encryption (RRBE) Method
- Vacating Room By Encryption (VRBE) Method
- Limitations of Recent RDH-EI Methods
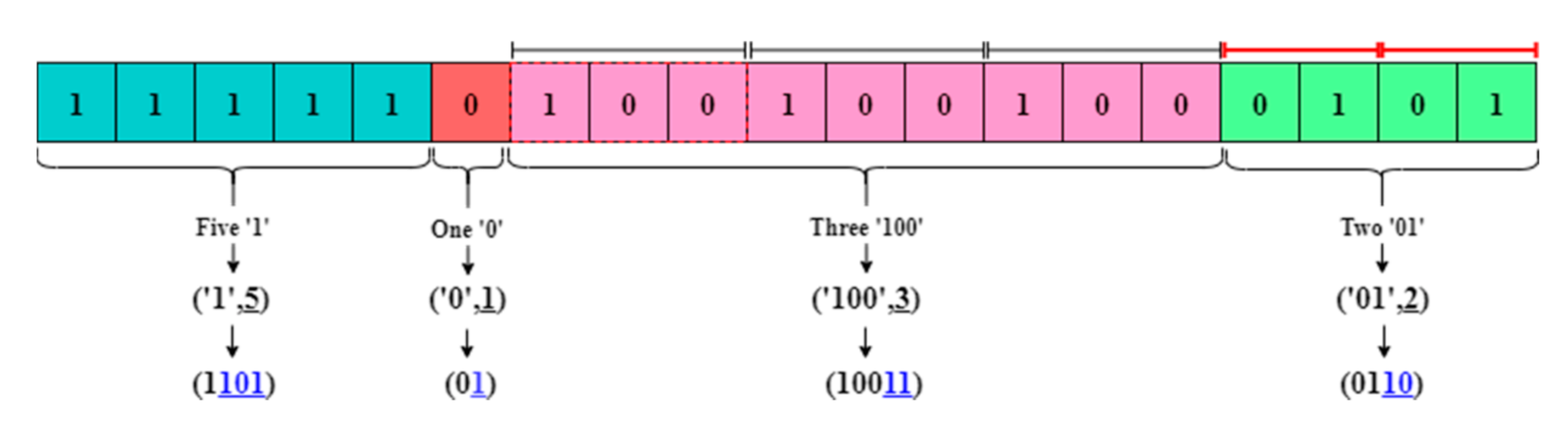
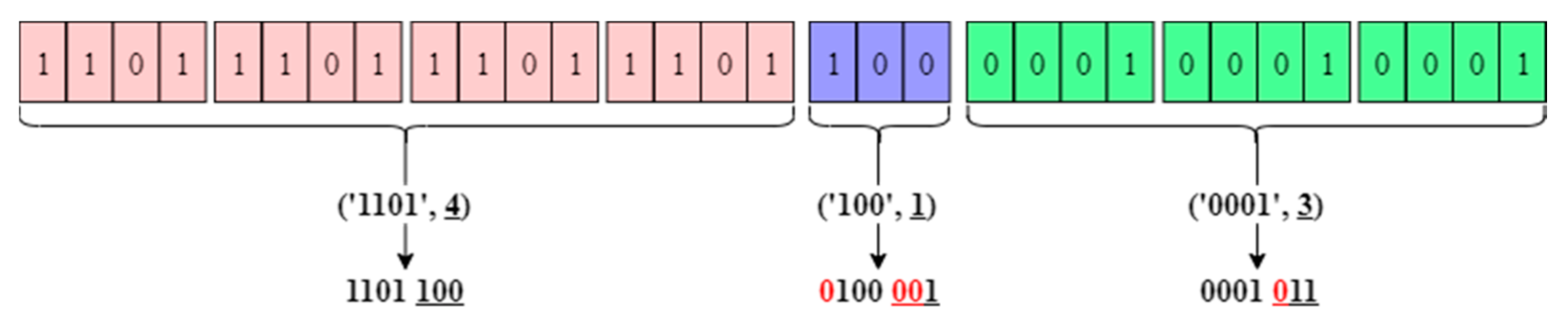
3. Two-Tuples Coding Method
3.1. Two-Tuples Coding
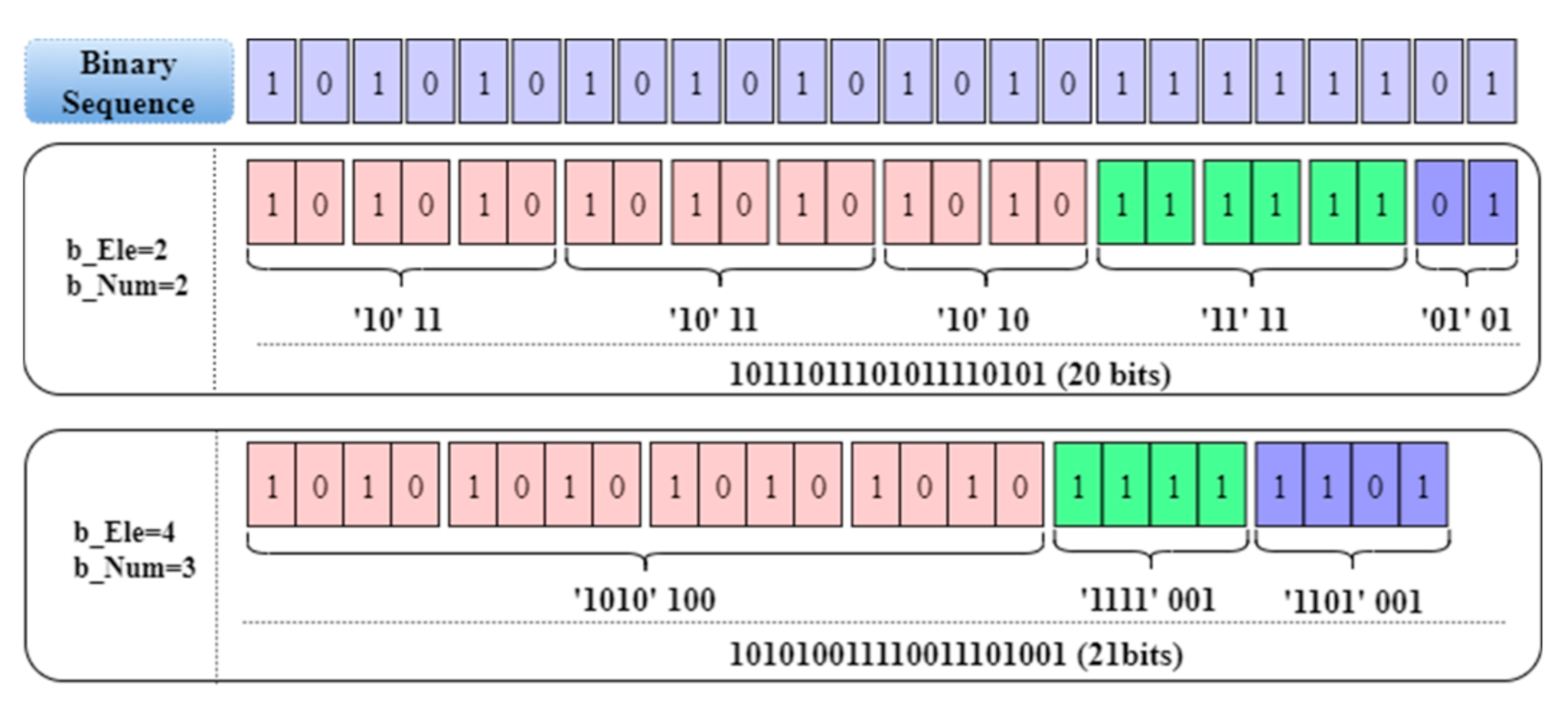
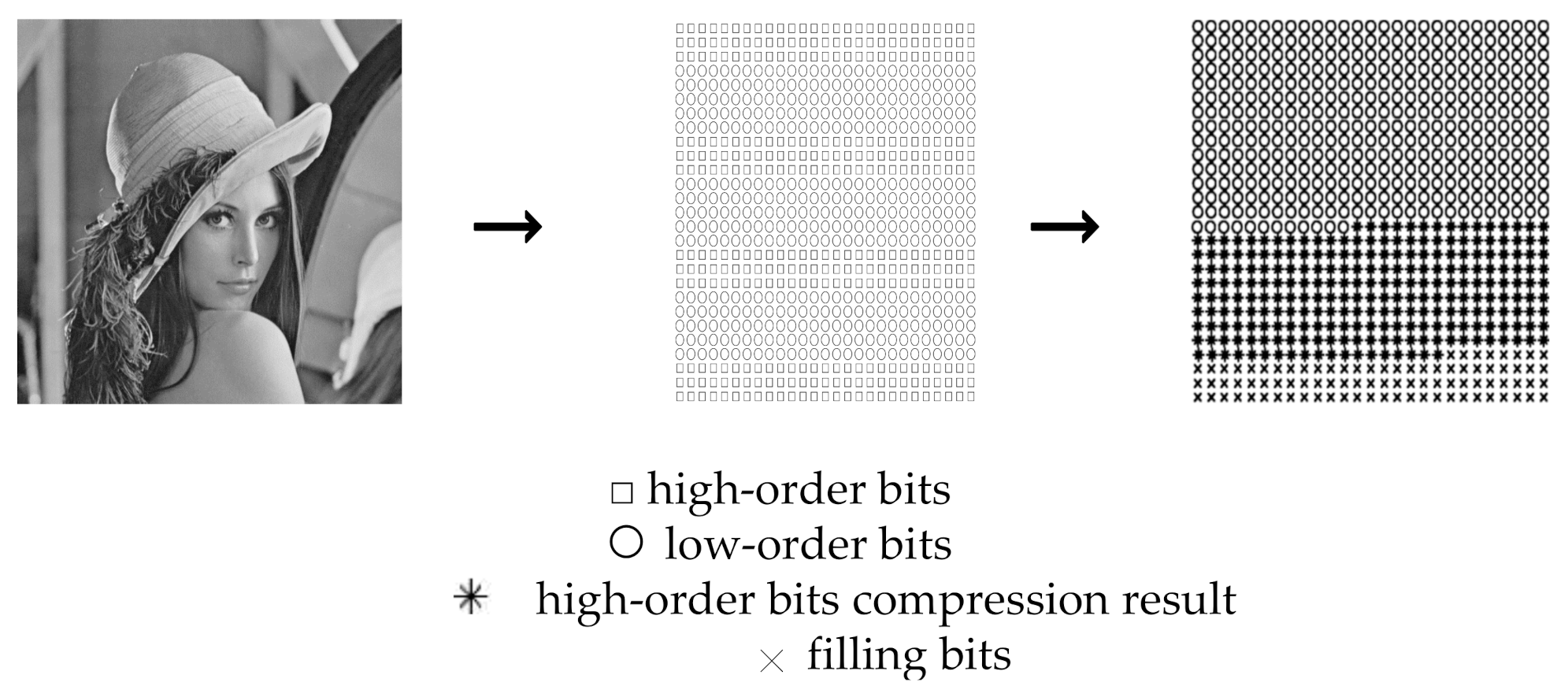
3.2. Enhanced Two-Tuples for Image Compression
3.3. Evaluation of Compression Efficiency
4. Separable Reversible Data Hiding in Encryption Image (RDH-EI) with Two-Tuples Coding
4.1. Coding Structure of the Encrypted Image
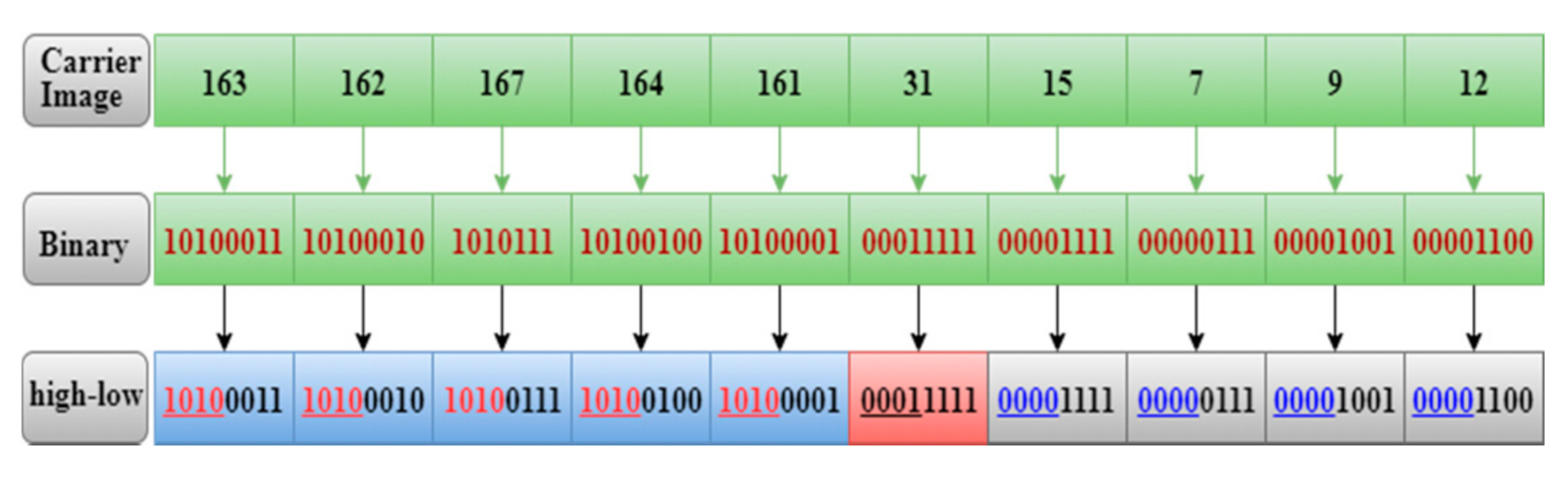
4.2. Calculate the High-Order Bits and Low-Order Bits of the Image
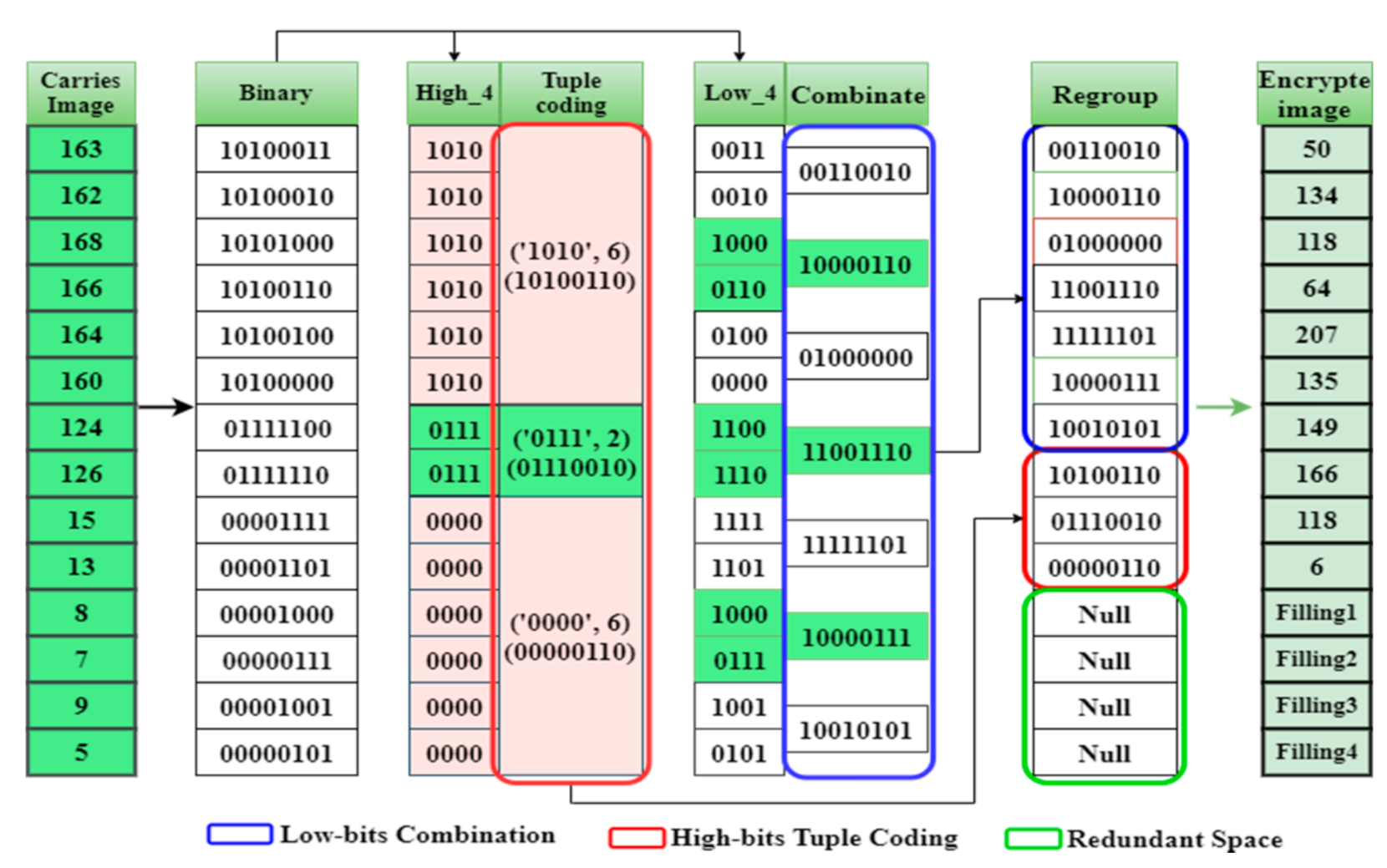
4.3. High-Order Bits Compression with Two-Tuples Coding Method
4.4. High-Order Bits Compression with Two-Tuples Coding Method
4.5. Compressed Redundancy Space-Filling Bits
4.6. Pixel Diffusion
4.7. Embedding Additional Data
4.8. Recovery of Carrier Image and Extraction of Additional Data
- Recovery of the Carrier Image
- Extracting Additional Data
5. Experimental Results and Analysis
5.1. Embedded Capacity
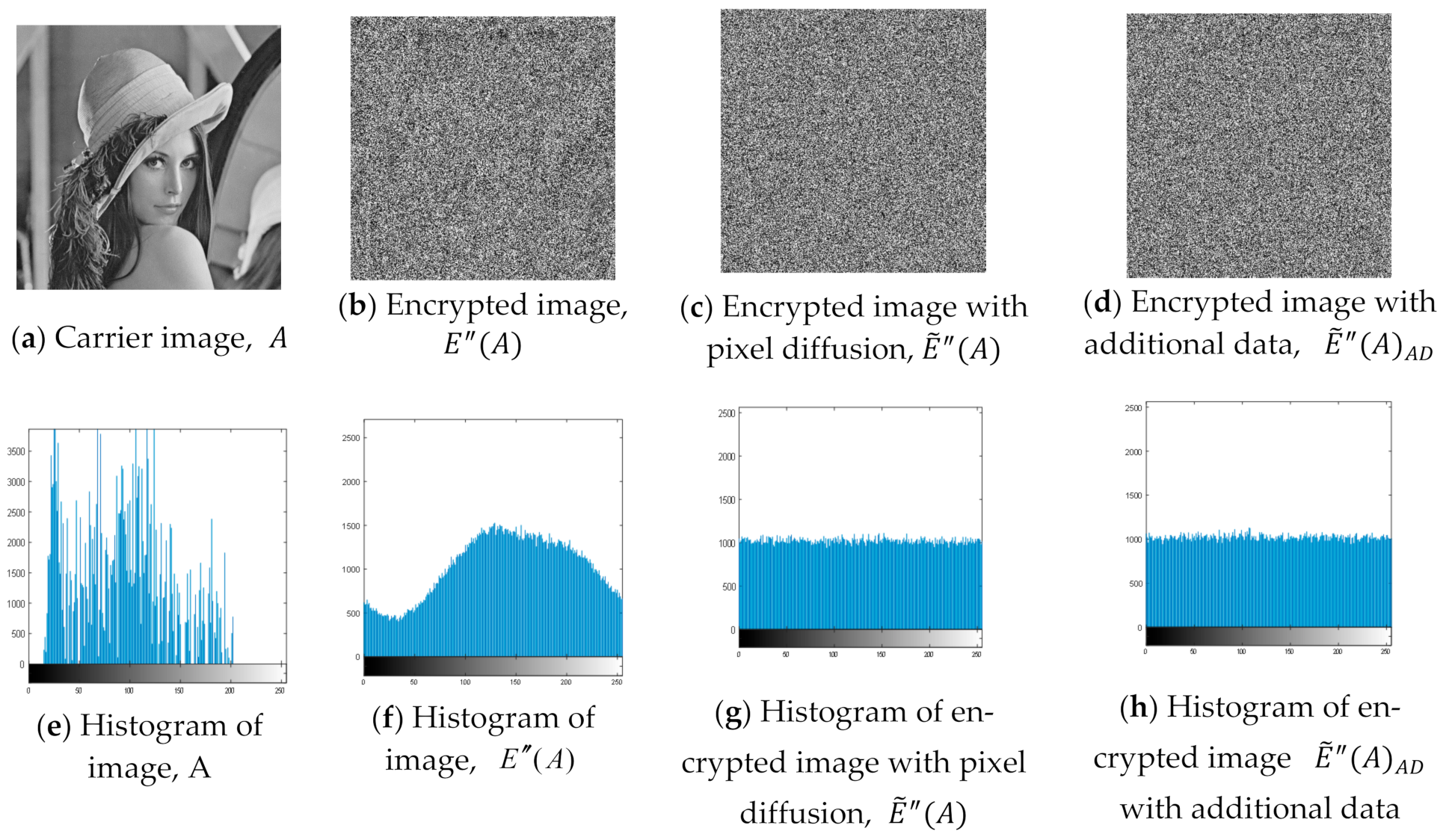
5.2. Experimental Results
5.3. Correlation Analysis
5.4. Comparison of the Proposed RDH-EI with Related Works
5.5. Complexity Analysis
5.6. Security Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Acronyms | Full Names |
|---|---|
| RDH | Reversible Data Hiding |
| RDH-EI | Reversible Data Hiding in Encryption Image |
| SRDH-EI | Separable Reversible Data Hiding in Encryption Image |
| VRAE | Vacating Room After Encryption |
| RRBE | Reserving Room Before Encryption |
| VRBE | Vacating Room By Encryptio |
| AD | Additional Data |
| ER | Embedding Rate |
| PD | Pixel Diffusion |
| LSB | Least Significant Bits of image |
| PSNR | Peak Signal to Noise Ratio |
| Symbols | Meaning | Symbols | Meaning |
|---|---|---|---|
| Carrier image | High-order -bits value of pixel | ||
| Encrypted image with the method of VRAE | Double data type of | ||
| Encrypted image with the method of RRBE | Continuous occurrence times of | ||
| Encrypted image with the method of VRBE | Low-bits sequential 8-bit binary | ||
| Output of embedding data into the encrypted image of | High-bits sequential 8-bit binary | ||
| Output of embedding data into Encrypted image of | Second part of the encrypted image | ||
| output of embedding data into Encrypted image of | First part of the encrypted image | ||
| Encrypted Image after pixel diffusion of | Third part of the Encrypted image | ||
| A combination of one or more selected bits in a binary sequence | Total bits of space | ||
| Consecutive count of the in a sequence | Length of | ||
| Bit-length of | Additional data | ||
| Bit-length of | A random sequence | ||
| High-order -bits of binary pixel coding | Matrix of sequence | ||
| Low-order -bits of binary pixel coding | A random sequence | ||
| Result of embedding AD in the complement |
References
- Kumar, R.; Chand, S.; Singh, S. A Reversible High Capacity Data Hiding Scheme Using Combinatorial Strategy. Int. J. Multimed. Intell. Secur. 2018, 3, 146–161. [Google Scholar] [CrossRef]
- Kumar, R.; Chand, S.; Singh, S. An Improved Histogram-Shifting-Imitated Reversible Data Hiding Based on HVS Characteristics. Multimed. Tools Appl. 2018, 77, 13445–13457. [Google Scholar] [CrossRef]
- Malik, A.; Sikka, G.; Verma, H.K. A Reversible Data Hiding Scheme for Interpolated Images Based on Pixel Intensity Range. Multimed. Tools Appl. 2020, 2, 1–27. [Google Scholar] [CrossRef]
- Tang, Z.; Nie, H.; Pun, C.; Yao, H.; Yu, C.; Zhang, X. Color Image Reversible Data Hiding with Double-Layer Embedding. IEEE Access 2020, 8, 6915–6926. [Google Scholar] [CrossRef]
- Liu, Y.L.; Qu, X.X.; Xin, G.J. A ROI-based Reversible Data Hiding Scheme in Encrypted Medical Images. J. Vis. Commun. Image Represent. 2016, 39, 51–57. [Google Scholar] [CrossRef]
- Wu, H.T.; Huang, J.W.; Shi, Y.Q. A Reversible Data Hiding Method with Contrast Enhancement for Medical Images. J. Vis. Commun. Image Represent. 2015, 31, 146–153. [Google Scholar] [CrossRef]
- Chen, Y.; Hung, T.; Hsieh, S.; Shiu, C. A New Reversible Data Hiding In Encrypted Image Based on Multi-Secret Sharing and Lightweight Cryptographic Algorithm. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3332–3343. [Google Scholar] [CrossRef]
- Khan, A.N.; Fan, M.Y.; Nazeer, M.I.; Memon, R.A.; Malik, A.; Husain, M.A. An Efficient Separable Reversible Data Hiding Using Paillier Cryptosystem for Preserving Privacy in Cloud Domain. Electronics 2019, 8, 682. [Google Scholar] [CrossRef] [Green Version]
- Zhang, X. Reversible Data Hiding in Encrypted Image. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Parah, S.A.; Ahad, F.; Sheikh, J.A.; Bhat, G.M. Hiding Clinical Information in Medical Images: A New High Capacity and Reversible Data Hiding Technique. J. Biomed. Inform. 2017, 66, 214–230. [Google Scholar] [CrossRef]
- Wu, D.; Xu, R.X. Reversible Data Hiding in the Encrypted Domain for Medical Image Security. Basic Clin. Pharmacol. Toxicol. 2019, 125, 225–226. [Google Scholar]
- Ke, G.; Wang, H.; Zhou, S.; Zhang, H. Encryption of Medical Image with Most Significant Bit and High Capacity in Piecewise Linear Chaos Graphics. Measurement 2019, 135, 385–391. [Google Scholar] [CrossRef]
- Shen, W.T.; Qin, J.; Yu, J.; Hao, R.; Hu, J. Enabling Identity-Based Integrity Auditing and Data Sharing with Sensitive Information Hiding for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 2019, 12, 331–346. [Google Scholar] [CrossRef]
- Xiong, L.Z.; Shi, Y.Q. On the Privacy-Preserving Outsourcing Scheme of Reversible Data Hiding over Encrypted Image Data in Cloud Computing. Comput. Mater. Continua 2018, 55, 523–539. [Google Scholar] [CrossRef]
- Yang, Y.; Xiao, X.; Cai, X.; Zhang, W. A Secure and Privacy-Preserving Technique Based on Contrast-Enhancement Reversible Data Hiding and Plaintext Encryption for Medical Images. IEEE Signal. Process. Lett. 2020, 27, 256–260. [Google Scholar] [CrossRef]
- Yuan, G.; Hao, Q. Digital Watermarking Secure Scheme for Remote Sensing Image Protection. China Commun. 2020, 17, 88–98. [Google Scholar] [CrossRef]
- Wu, G.; Lee, C. Framework for cloud database protection by using reversible data hiding methods. In Proceedings of the IEEE International Conference on Consumer Electronics, Ilan, Taiwan, 20–22 May 2019; pp. 1–2. [Google Scholar] [CrossRef]
- Iqbal, M.M.; Khadam, U.; Han, K.J.; Han, J.; Jabbar, S. A Robust Digital Watermarking Algorithm for Text Document Copyright Protection Based on Feature Coding. In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 1940–1945. [Google Scholar] [CrossRef]
- Liao, X.; Shu, C.W. Reversible Data Hiding in Encrypted Images Based on Absolute Mean Difference of Multiple Neighboring Pixels. J. Vis. Commun. Image Represent. 2015, 28, 21–27. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.S.; Wu, H.Y. An Improved Reversible Data Hiding in Encrypted Images Using Side Match. IEEE Signal. Process. Lett. 2012, 199–202. [Google Scholar] [CrossRef]
- Qin, C.; Zhang, X.P. Effective Reversible Data Hiding in Encrypted Image with Privacy Protection for Image Conten. J. Vis. Commun. Image Represent. 2015, 31, 154–164. [Google Scholar] [CrossRef]
- Wang, Y.M.; Cai, Z.C.; He, W.G. A New High Capacity Separable Reversible Data Hiding in Encrypted Images Based on Block Selection And Block-Level Encryption. IEEE Access 2019, 7, 175671–175680. [Google Scholar] [CrossRef]
- Zhang, X.P. Separable Reversible Data Hiding in Encrypted Imag. IEEE Trans. Inf. Forensics Secur. 2012, 7, 826–832. [Google Scholar] [CrossRef]
- Xu, D.W.; Wang, R.D. Separable and Error-Free Reversible Data Hiding in Encrypted Images. Signal. Process. 2016, 123, 9–21. [Google Scholar] [CrossRef]
- Agrawal, S.; Kumar, M. Mean Value Based Reversible Data Hiding in Encrypted Images. Optik 2017, 130, 922–934. [Google Scholar] [CrossRef]
- Singh, P.; Raman, B. Reversible Data Hiding for Rightful Ownership Assertion of Images In Encrypted Domain Over Cloud. Aeu-Int. J. Electron. Commun. 2017, 76, 18–35. [Google Scholar] [CrossRef]
- Qin, C.; Zhang, W.; Cao, F.; Zhang, X.; Chang, C.C. Separable Reversible Data Hiding in Encrypted Images Via Adaptive Embedding Strategy with Block Selection. Signal. Process. 2017, 153, 109–122. [Google Scholar] [CrossRef]
- Zhang, W.; Kong, P.; Yao, H.; Hu, Y.C.; Cao, F. Real-Time Reversible Data Hiding in Encrypted Images Based on Hybrid Embedding Mechanism. J. Real-Time Image Process. 2019, 16, 697–708. [Google Scholar] [CrossRef]
- Yi, S.; Zhou, Y.C.; Hua, Z.Y. Reversible Data Hiding in Encrypted Images using Adaptive Block-Level Prediction-Error Expansion. Signal. Process. Image Commun. 2018, 64, 78–88. [Google Scholar] [CrossRef]
- Di, F.Q.; Huang, F.J.; Zhang, M.Q. Reversible Data Hiding in Encrypted Images with High Capacity by Bitplane Operations and Adaptive Embedding. Multimed. Tools Appl. 2018, 7, 20917–20935. [Google Scholar] [CrossRef]
- Yu, C.; Zhang, X.; Tang, Z.; Xie, X. Separable and Error-Free Reversible Data Hiding in Encrypted Image Based on Two-Layer Pixel Errors. IEEE Access 2018, 6, 76956–76969. [Google Scholar] [CrossRef]
- Xu, D.W.; Su, S.B. Separable Reversible Data Hiding in Encrypted Images Based on Difference Histogram Modification. Secur. Commun. Netw. 2019, 6, 1–14. [Google Scholar] [CrossRef]
- Cao, X.; Du, L.; Wei, M.D.; Guo, X. High Capacity Reversible Data Hiding in Encrypted Images by Patch-Level Sparse Representation. IEEE Trans. Cybern. 2016, 46, 1132–1143. [Google Scholar] [CrossRef]
- Han, X.; Qian, Z.X.; Feng, G.R.; Zhang, X.P. Reversible Data Hiding in Encrypted Images Based on Image Interpolation. Int. J. Digit. Crime Forensics 2014, 6, 16–29. [Google Scholar] [CrossRef]
- Qian, Z.X.; Zhang, X.P.; Feng, G.R. Reversible Data Hiding in Encrypted Images Based on Progressive Recovery. IEEE Signal. Process. Lett. 2016, 23, 1672–1676. [Google Scholar] [CrossRef]
- Li, Q.; Yan, B.; Li, H. Separable Reversible Data Hiding in Encrypted Images with Improved Security and Capacity. Multimed. Tools Appl. 2018, 77, 30749–30768. [Google Scholar] [CrossRef]
- Wu, H.B.; Li, F.Y.; Qin, C.; Wei, W.M. Separable Reversible Data Hiding in Encrypted Images Based on Scalable Blocks. Multimed. Tools Appl. 2019, 78, 25349–25372. [Google Scholar] [CrossRef]
- Nasrullah, N.; Sang, J.; Mateen, M.; Akbar, M.A.; Xiang, H.; Xia, X.F. Reversible Data Hiding in Compressed and Encrypted Images by using Kd-tree. Multimed. Tools Appl. 2019, 78, 17535–17554. [Google Scholar] [CrossRef]
- Yu, M.J.; Liu, Y.C.; Sun, H.; Yao, H.; Qiao, T. Adaptive and Separable Multiary Reversible Data Hiding in Encryption Domain. Eurasip J. Image Video Process. 2020, 1–15. [Google Scholar] [CrossRef]
- Liu, Z.L.; Pun, C.M. Reversible Data-Hiding in Encrypted Images by Redundant Space Transfer. Inf. Sci. 2018, 433, 188–203. [Google Scholar] [CrossRef]
- Yi, S.; Zhou, Y.C. Separable and Reversible Data Hiding in Encrypted Images Using Parametric Binary Tree Labeling. IEEE Trans. Multimed. 2019, 21, 51–64. [Google Scholar] [CrossRef]
- Tang, Z.J.; Xu, S.J.; Yao, H.; Qin, C.; Zhang, X.Q. Reversible Data Hiding with Differential Compression in Encrypted Image. Multimed. Tools Appl. 2019, 78, 9691–9715. [Google Scholar] [CrossRef]
- Qin, C.; Qian, X.K.; Hong, W.; Zhang, X.P. An Efficient Coding Scheme for Reversible Data Hiding In Encrypted Image With Redundancy Transfer. Inf. Sci. 2019, 487, 176–192. [Google Scholar] [CrossRef]




| 1 | 2 | 3 | 4 | 5 | 6 | |
| 1 | ─ | ─ | ─ | ─ | ─ | ─ |
| 2 | ─ | 139,552 (6.65%) | 265,377 (12.65%) | 318,316 (15.18%) | 284,121 (13.55%) | 126,856 (6.05%) |
| 3 | 87,092 (4.15%) | 273,113 (13.02%) | 415,146 (19.80%) | 439,051 (20.94%) | 328,544 (15.67%) | 43,008 (2.05%) |
| 4 | 136,639 (6.52%) | 326,636 (15.58%) | 459,462 (21.91%) | 436,696 (20.82%) | 253,544 (12.09%) | ─ |
| 5 | 160,366 (7.65%) | 341,826 (16.30%) | 458,072 (21.84%) | 388,444 (18.52%) | 145,080 (6.92%) | ─ |
| 6 | 168,505 (8.03%) | 338,328 (16.13%) | 435,315 (20.76%) | 323,026 (15.40%) | 29,275 (1.40%) | ─ |
| 7 | 168,176 (8.02%) | 324,695 (15.48%) | 402,642 (19.20%) | 251,934 (12.01%) | ─ | ─ |
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 1 | ─ | ─ | ─ | ─ | ─ | ─ |
| 2 | ─ | 140,500 (6.70%) | 252,092 (12.02%) | 304,282 (14.51%) | 243,178 (11.60%) | 70,016 (3.34%) |
| 3 | 87,584 (4.18%) | 277,093 (13.21%) | 395,694 (18.87%) | 420,704 (20.06%) | 264,672 (12.62%) | ─ |
| 4 | 138,919 (6.62%) | 334,664 (15.96%) | 434,857 (20.74%) | 413,984 (19.74%) | 175,910 (8.39%) | ─ |
| 5 | 164,278 (7.83%) | 355,805 (16.97%) | 427,880 (20.40%) | 362,605 (17.29%) | 59,650 (2.84%) | ─ |
| 6 | 174,581 (8.32%) | 356,520 (17.00%) | 400,449 (19.09%) | 294,806 (14.06%) | ─ | ─ |
| 7 | 174,800 (8.34%) | 346,232 (16.51%) | 362,622 (17.29%) | 221,068 (10.54%) | ─ | ─ |
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 1 | ─ | ─ | ─ | ─ | ─ | ─ |
| 2 | ─ | 158,592 (7.56%) | 300,232 (14.32%) | 394,474 (18.81%) | 395,974 (18.88%) | 253,264 (12.08%) |
| 3 | 106,816 (5.09%) | 309,153 (14.74%) | 478,344 (22.81%) | 569,111 (27.14%) | 505,184 (24.09%) | 219,084 (10.45%) |
| 4 | 166,594 (7.94%) | 380,102 (18.12%) | 546,885 (26.08%) | 606,008 (28.90%) | 464,819 (22.16%) | 84,974 (4.05%) |
| 5 | 200,248 (9.55%) | 413,639 (19.72%) | 566,248 (27.00%) | 585,454 (27.92%) | 382,480 (18.24%) | ─ |
| 6 | 219,367 (10.46%) | 427,688 (20.39%) | 559,452 (26.68%) | 543,086 (25.90%) | 290,976 (13.87%) | ─ |
| 7 | 229,792 (10.96%) | 428,546 (20.43%) | 540,782 (25.79%) | 494,330 (23.57%) | 198,548 (9.47%) | ─ |
| 1 | 1 | 11,000 | 262,144 | ─ | ─ |
| 2 | 2 | 21,740 | 96,184 | 139,552 | 6.65% |
| 3 | 3 | 38,239 | 61,881 | 415,146 | 19.89% |
| 4 | 4 | 72,415 | 76,485 | 436,696 | 20.82% |
| 5 | 5 | 116,494 | 116,564 | 145,080 | 6.92% |
| 6 | 6 | 169,042 | 169,067 | ─ | ─ |
| Correlation | Carrier Image, (a) | Encrypted Image, (b) | Encrypted Image with Pixel Diffusion, (c) | Encrypted Image with Additional Data, (d) |
| Horizontal direction | 0.9848 | −0.0369 | 0.0032 | 0.0028 |
| Horizontal direction | 0.9726 | 0.0037 | −0.00068 | −0.00024 |
| Diagonal direction | 0.9592 | 0.0018 | −0.00067 | −0.0003 |
| Correlation | Carrier Image, (a) | Encrypted Image, (b) | Encrypted Image with Pixel Diffusion, (c) | Encrypted Image with Additional Data, (d) |
| Horizontal direction | 0.9848 | −0.0029 | −0.0046 | −0.0041 |
| Horizontal direction | 0.9726 | −0.0008 | −0.0014 | −0.0011 |
| Diagonal direction | 0.9592 | −0.0006 | −0.0135 | −0.0146 |
| Scheme | Perfect Recovery | Separable | Maximum ER (bpp) | PSNR (dB) | Main Means | Category | Published Year |
| Qin [27] | Yes | Yes | 0.032 | 41.50 | Compressing LSBs | VRAE | 2018 |
| Yi [29] | Yes | Yes | 0.500 | 39.86 | Prediction-error expansion | VRAE | 2018 |
| Di [30] | Yes | Yes | 0.720 | 26.50 | Bit plane decomposition | VRAE | 2018 |
| Yu [31] | Yes | Yes | 0.500 | 36.50 | Modification Histogram | VRAE | 2018 |
| Zhang [28] | Yes | Yes | 0.186 | 44.50 | Divides blocks, stream cipher and permutation | VRAE | 2019 |
| Xu [32] | Yes | Yes | 0.541 | 40.94 | Prediction error, Modification Histogram | VRAE | 2019 |
| Wang [22] | No | Yes | 0.120 | - | Flipping LSBs | VRAE | 2019 |
| Li [36] | Yes | Yes | 0.858 | 35.73 | Prediction errors, Stream cipher | RRBE | 2018 |
| Wu [37] | Yes | Yes | 1.192 | 47.93 | Divides blocks, Stream cipher | RRBE | 2019 |
| Nasrullah [38] | Yes | Yes | 0.180 | 39.85 | Wavelet transform, High dimensional Kd-tree | RRBE | 2019 |
| Yu [39] | Yes | Yes | 0.352 | 50.24 | Prediction errors | RRBE | 2020 |
| Liu [40] | Yes | Yes | 1.600 | 41.49 | Arnold transform-based encryption method | VRBE | 2018 |
| Yi [41] | Yes | Yes | 1.722 | - | Parametric binary tree labeling | VRBE | 2019 |
| Qin [43] | Yes | Yes | 1.580 | 46.53 | Sparse block coding | VRBE | 2019 |
| Proposed Scheme | Yes | Yes | 1.753 | 45.76 | Two-tuples coding | VRBE |
| Test Image (Seconds) | Liu [40] | Yi [41] | Qin [43] | Proposed |
| Lena | 0.2854 | 0.3265 | 0.1255 | 0.1385 |
| Peppers | 0.2257 | 0.3133 | 0.1377 | 0.1433 |
| Zelda | 0.2344 | 0.3658 | 0.1164 | 0.1066 |
| Bridge | 0.2758 | 0.3142 | 0.1287 | 0.1249 |
| Airfield | 0.2691 | 0.3296 | 0.1238 | 0.1372 |
| Average | 0.2581 | 0.3298 | 0.1264 | 0.1301 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, J.; Tan, S.F. Separable Reversible Data Hiding in Encryption Image with Two-Tuples Coding. Computers 2021, 10, 86. https://0-doi-org.brum.beds.ac.uk/10.3390/computers10070086
Wang J, Tan SF. Separable Reversible Data Hiding in Encryption Image with Two-Tuples Coding. Computers. 2021; 10(7):86. https://0-doi-org.brum.beds.ac.uk/10.3390/computers10070086
Chicago/Turabian StyleWang, Jijun, and Soo Fun Tan. 2021. "Separable Reversible Data Hiding in Encryption Image with Two-Tuples Coding" Computers 10, no. 7: 86. https://0-doi-org.brum.beds.ac.uk/10.3390/computers10070086






