Using Blockchain to Ensure Trust between Donor Agencies and NGOs in Under-Developed Countries
Abstract
:1. Introduction
2. Related Work
3. Material and Method
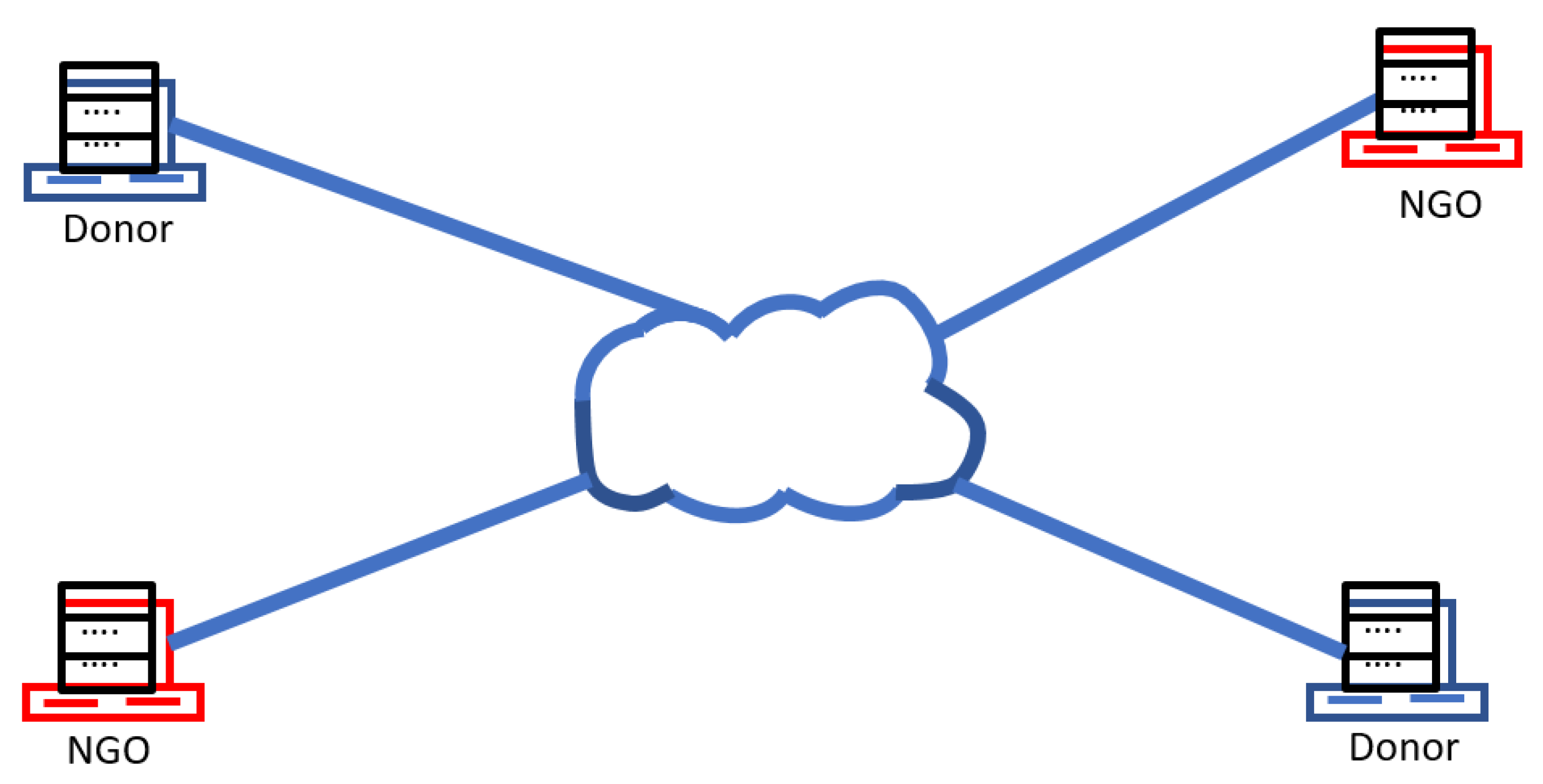
3.1. Overview of the Proposed Solution
3.2. Joining and Leaving the Distributed System
3.3. Restricting Who Can Join the Network
3.4. Algorithm for Joining the Network
| Algorithm 1 To allow a node to join the distributed network |
 |
3.5. Encouraging the Nodes Not to Leave the Network
3.6. A Penalty Mechanism to Encourage Nodes to Stay Connected
4. The Structure and Maintenance of the Ledger
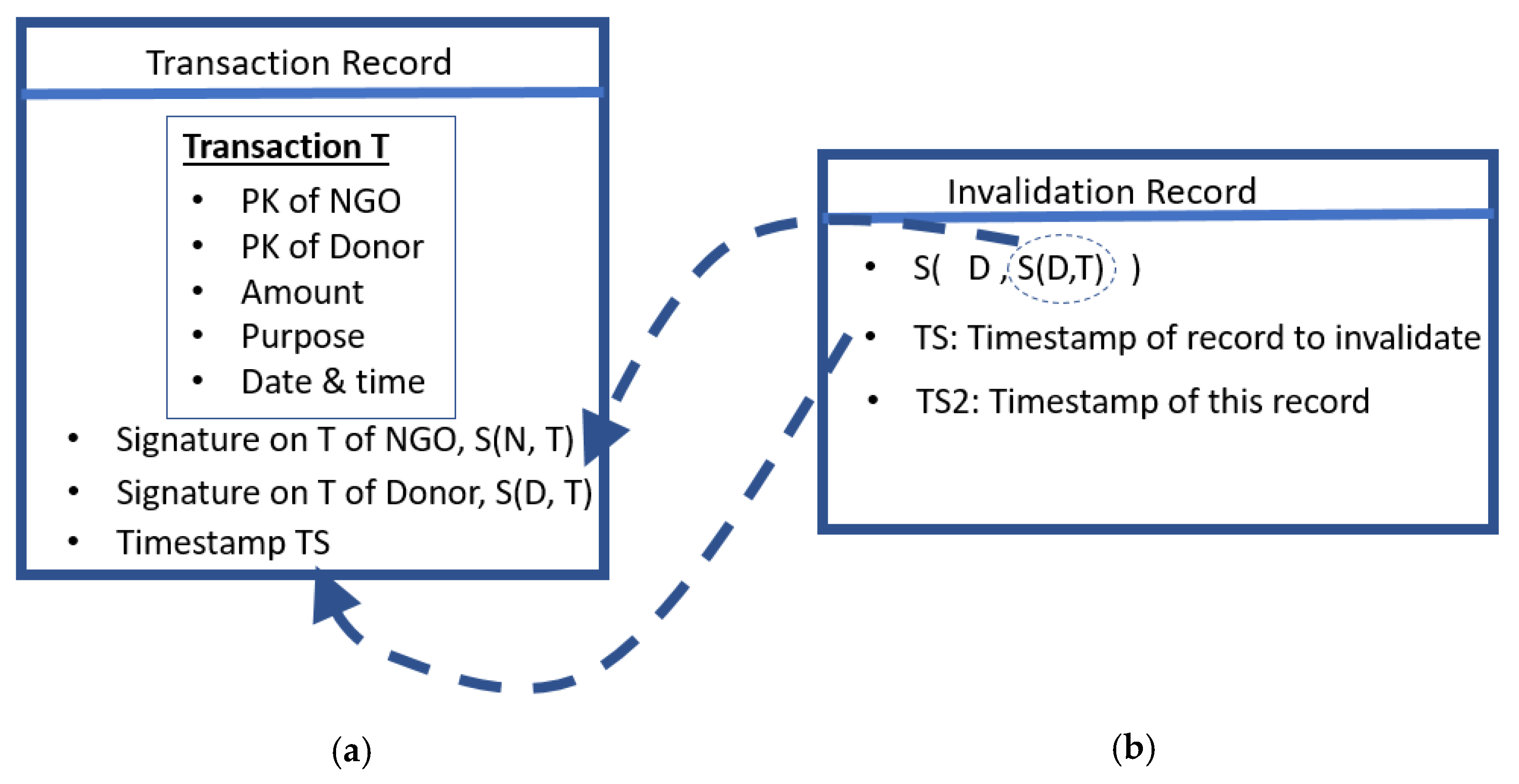
4.1. The Different Kinds of a Record in the Ledger
4.1.1. The Transaction Record
4.1.2. The Invalidation Record
4.2. A Single Block of Transaction in a Ledger
4.2.1. Addition of a Block into the Ledger
4.2.2. Rejection of Invalid Records
- (a)
- Inconsistent or duplicated data: Firstly, the data in the transaction could be inconsistent or duplicated. For instance, maybe there are three parties mentioned in the transaction, but only two of them have signed it. Another possibility is that the amount of money involved in the transaction is not consistent with the purpose mentioned for the transaction.
- (b)
- Unknown signatories: If at least one of the signing parties is not a known NGO or donor agency, then the record cannot be inserted into the ledger. Note that there can be disagreement among the nodes whether a public key belongs to a known NGO/donor agency, or not. One node might know about X, while another might not. Hence, an agreement will be reached among the nodes, by voting.
- (c)
- Insufficient online time: Algorithmically, the most interesting possibility is that although the record is correct, none of the signatories listed in the record have spent enough time and effort in the network to be allowed to insert their transactions. Recall, that to be allowed to insert a record, the entity, which is either an NGO or donor agency, must have spent enough time in the network, verifying the new blocks of data, as well as being part of other consensus algorithms.
- (d)
- Invalid reference to a previous record: In the case of an invalidation record, there should be a reference to a previously inserted record, along with its timestamp. If such a record does not exist, then the invalidation record cannot be inserted into the ledger.
Inconsistent or Duplicate Data
- (a)
- Incorrect signatures: Either there are some parties listed in the transaction that have not signed the transaction, and/or one of the signatures is not from a party listed inside the transaction. In short, the following two sets are not identical: the set of parties mentioned in the transaction details and the set of parties from which the signatures have been received.
- (b)
- Purpose and amount mismatch: Each transaction has to say the purpose that the NGO would use this money for. If the quoted amount is either too small or too large and therefore not in the allowed range of the given purpose, then there is a mismatch in the purpose and amount.
- (c)
- Duplicated purpose: If a transaction that has been added to the ledger, allocated funds for the same purpose, and to the same entity (such as the same student), then it is a duplicate/fake transaction and would be rejected. For instance, two different transactions could not be allocating funds to buy the same books, for the student with the same ID during the same year of his/her education. The details of detecting duplicate transactions are given in Section 4.4.
- (d)
- Purpose unknown: The purpose of an amount can only be one of the allowed purposes. The allowed purposes are listed in the “Table of purposes” that will be covered in Section 4.4 in this article. Each purpose in this table has a unique identifier, as well as a description. A transaction lists its purpose using one of these unique identifiers, and also includes the description of the given purpose. If this pair of (unique identifier, description), does not exist in the table of purposes, then the transaction record cannot be accepted into the ledger.
- (e)
- One of the required fields is missing: Lastly, if one of the above-required fields is missing, then the record should not be inserted into the ledger.
Insufficient Online Time
| Algorithm 2 updating the online time of node c |
 |
| Algorithm 3 Accepting or rejecting a record r from c |
 |
4.2.3. The Frequency of Adding New Blocks
- (1)
- The waiting time for some outstanding transaction or invalidation has crossed the maximum allowed value.
- (2)
- The number of outstanding transactions has crossed the maximum allowed value.
4.3. Table of Purposes and Detecting Duplicates
- (1)
- The unique ID of the purpose: This could just be the row number.
- (2)
- The name of the purpose: This serves the purpose as an English title of the purpose that people can understand.
- (3)
- Unique ID (National ID) of the recipient of this fund: This field is required to detect duplicate/fake transactions as explained in the description later in this subsection.
- (4)
- Time Period of the purpose: This field is also one of the fields that are used to detect duplicate transactions.
- (5)
- The description of the purpose.
- (6)
- The valid range of amount.
- (7)
- Whether this row is currently valid or invalid. If invalid, then signatures of at least N NGOs and M donor agencies that decided to invalidate it.
- (8)
- Signatures of at least N NGOs, and at least M donor agencies.
- (9)
- Other related fields.
4.4. Adapting to the Case When Transaction Data Is Not Public
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kravitz, D. Digital Signature Algorithm. U.S. Patent 5,231,668, 27 July 1993. Available online: https://patentimages.storage.googleapis.com/e6/de/c5/75aceb27607e59/US5231668.pdf (accessed on 11 April 2021).
- Satoshi, N. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 11 April 2021).
- Bhatia, S.; Wright De Hernandez, A.D. Blockchain Is Already Here. What Does That Mean for Records Management and Archives? J. Arch. Organ. 2019, 16, 75–84. [Google Scholar] [CrossRef] [Green Version]
- Irshad, S.; Brohi, M.N.; Soomro, T.R. Block-ED: The Proposed Blockchain Solution for Effectively Utilising Educational Resources. Appl. Comput. Syst. 2020, 25, 1–10. [Google Scholar] [CrossRef]
- Wu, H.; Zhu, X. Developing a Reliable Service System of Charity Donation during the Covid-19 Outbreak. IEEE Access 2020, 8, 154848–154860. [Google Scholar] [CrossRef]
- Sam, D. 30 Blockchain Applications and Real-World Use Cases Disrupting the Status Quo. Available online: https://builtin.com/blockchain/blockchain-applications (accessed on 11 May 2021).
- Akash, T. Top Blockchain Platforms of 2021. Available online: https://www.leewayhertz.com/blockchain-platforms-for-top-blockchain-companies/ (accessed on 11 May 2021).
- Bohme, R.; Christin, N.; Edelman, B.; Moore, T. Bitcoin: Economics, Technology, and Governance. J. Econ. Perspect. 2015, 29, 213–238. [Google Scholar] [CrossRef] [Green Version]
- Abou Jaoude, J.; Saade, R.G. Blockchain Applications-Usage in Different Domains. IEEE Access 2019, 7, 45360–45381. [Google Scholar] [CrossRef]
- Curt, T. Foreign Aid and the Education Sector: Programs and Priorities. Congr. Res. Serv. 2016, 1–23. Available online: https://fas.org/sgp/crs/row/R44676.pdf (accessed on 15 May 2021).
- Zwitter, A.; Boisse-Despiaux, M. Blockchain for Humanitarian Action and Development Aid. J. Int. Humanit. Act. 2018, 3, 1–7. [Google Scholar] [CrossRef] [Green Version]
- Farooq, M.S.; Khan, M.; Abid, A. A Framework to Make Charity Collection Transparent and Auditable Using Blockchain Technology. Comput. Electr. Eng. 2020, 83, 106588. [Google Scholar] [CrossRef]
- Hsu, C.S.; Tu, S.F.; Huang, Z.J. Design of an E-Voucher System for Supporting Social Welfare Using Blockchain Technology. Sustainability 2020, 12, 3362. [Google Scholar] [CrossRef] [Green Version]
- Jia, H.W.; Deng, X.Q. A Preliminary Analysis of the Application of Blockchain in Social Emergency Relief. In Proceedings of the 2018 2nd International Conference on Education Management and Applied Social Science(EMASS), Wuhan, China, 7–8 February 2018. [Google Scholar] [CrossRef] [Green Version]
- Nor, R.M.; Rahman, M.H.; Rahman, T.; Abdullah, A. Blockchain sadaqa mechanism for disaster aid crowdfunding in Zulikha. In Proceedings of the 6th International Conference of Computing & Informatics, Kuala Lumpur, Malaysia, 25–27 April 2017; pp. 400–405. [Google Scholar]
- Rangone, A.; Busolli, L. Managing Charity 4.0 with Blockchain: A Case Study at the Time of Covid-19. Int. Rev. Public Nonprofit Mark. 2021, 1–31. [Google Scholar] [CrossRef]
- Available online: https://www.charitywall.org/ (accessed on 21 May 2021).
- Hu, B.; Li, H. Research on Charity System Based on Blockchain. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2020; Volume 768, p. 072020. [Google Scholar] [CrossRef]
- Nguyen, L.T.; Hoang, T.G.; Do, L.H.; Ngo, X.T.; Nguyen, P.H.; Nguyen, G.D.; Nguyen, G.N. The role of blockchain technology-based social crowdfunding in advancing social value creation. Technol. Forecast. Soc. Chang. 2021, 170, 120898. [Google Scholar] [CrossRef]
- Suciu, G.; Nădrag, C.; Istrate, C.; Vulpe, A.; Ditu, M.C.; Subea, O. Comparative Analysis of Distributed Ledger Technologies. In Proceedings of the 2018 Global Wireless Summit (GWS), Chiang Rai, Thailand, 25–28 November 2018; pp. 370–373. [Google Scholar] [CrossRef]
- Dubey, R.; Gunasekaran, A.; Childe, S.J.; T Hazen, B.E.N.J.A.M.I.N.; Papadopoulos, T. Blockchain for the humanitarian supply chain. Supply Chain. 4.0 Improv. Supply Chain. Anal. Ind. 4.0 Technol. 2021, 61. [Google Scholar]
- Fischer, M.J. The consensus problem in unreliable distributed systems (a brief survey). In International Conference on Fundamentals of Computation Theory; Springer: Berlin/Heidelberg, Germany, 1983. [Google Scholar]
- Gilad, Y.; Hemo, R.; Micali, S.; Vlachos, G.; Zeldovich, N. Algorand: Scaling byzantine agreements for cryptocurrencies. In Proceedings of the 26th Symposium on Operating Systems Principles, Shanghai, China, 28 October 2017; pp. 51–68. [Google Scholar] [CrossRef] [Green Version]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public-key cryptography. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; pp. 452–473. [Google Scholar]
- Lamport, L. Time, clocks, and the ordering of events in a distributed system. In Concurrency: The Works of Leslie Lamport; Association for Computing Machinery: New York, NY, USA, 2019; pp. 179–196. [Google Scholar] [CrossRef] [Green Version]
- Whetten, B.; Todd, M.; Simon, K. A high performance ordered multicast protocol. In Theory and Practice in Distributed Systems; Springer: Berlin/Heidelberg, Germany, 1995; pp. 33–57. [Google Scholar]
- Van Steen, M.; Andrew, S. Tanenbaum. Distributed Systems; Maarten van Steen: Leiden, The Netherlands, 2017. [Google Scholar]
- Nguyen, N.T. Consensus-based Timestamps in Distributed Temporal Databases. Comput. J. 2001, 44, 398–409. [Google Scholar] [CrossRef]
- Awerbuch, B. Optimal Distributed Algorithms for Minimum Weight Spanning Tree, Counting, Leader Election, and Related Problems. In Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 25–27 May 1987; pp. 230–240. [Google Scholar] [CrossRef]
- Abraham, I.; Dolev, D.; Halpern, J.Y. Distributed Protocols for Leader Election. ACM Trans. Econ. Comput. 2019, 7, 1–26. [Google Scholar] [CrossRef]




| Public Key | Hour 1 | Hour 2 | Hour 3 | Hour 24 × d |
|---|---|---|---|---|
| ABA14S | 0 | 1 | 0 | 1 |
| FF2G | 1 | 0 | 1 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, E.; Khan, M.A.; Soomro, T.R.; Taleb, N.; Afifi, M.A.; Ghazal, T.M. Using Blockchain to Ensure Trust between Donor Agencies and NGOs in Under-Developed Countries. Computers 2021, 10, 98. https://0-doi-org.brum.beds.ac.uk/10.3390/computers10080098
Rehman E, Khan MA, Soomro TR, Taleb N, Afifi MA, Ghazal TM. Using Blockchain to Ensure Trust between Donor Agencies and NGOs in Under-Developed Countries. Computers. 2021; 10(8):98. https://0-doi-org.brum.beds.ac.uk/10.3390/computers10080098
Chicago/Turabian StyleRehman, Ehsan, Muhammad Asghar Khan, Tariq Rahim Soomro, Nasser Taleb, Mohammad A. Afifi, and Taher M. Ghazal. 2021. "Using Blockchain to Ensure Trust between Donor Agencies and NGOs in Under-Developed Countries" Computers 10, no. 8: 98. https://0-doi-org.brum.beds.ac.uk/10.3390/computers10080098







