Leveraging Aviation Risk Models to Combat Cybersecurity Threats in Vehicular Networks
Abstract
:1. Introduction
2. Related Works
3. Comparative Review of Aviation Industry Risk Models
4. A Proposed Vehicular Network Risk Management Model and Methodology
- ISO 26262 ASIL Hazard Classification [16]
- ISO 15408 Evaluation criteria for IT security [17]
- ISO 27001 Information Security Management System [18]
- NHTSA-2016-0126 Federal Motor Vehicle Safety Standards: V2V Communications [19]
- SAE J3061 Cybersecurity Guidebook for Cyber-Physical Vehicle Systems [20]
- NIST SP 800-30 Guide for Conducting Risk Assessments [7]
- NIST SP 800-39 Managing Information Security Risk [21]
- NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations [22]
- NIST SP 800-82 Guide to Industrial Control Systems (ICS) Security [23]
- DOT HS 812 073 National Institute of Standards And Technology Cybersecurity Risk Management Framework Applied to Modern Vehicles [24]
- NIST SP 800-37, Risk Management Framework for Information Systems and Organizations [25]
- DODi 8510.01, Risk Management Framework (RMF) for DoD Information Technology (IT) [26]
- NASA SP-2011-3422, NASA Risk Management handbook [27]
- DOD Risk, Issue, and Opportunity Management Guide for Defense Acquisition Programs [28]
- ISO 31000, Risk Management—Guidelines [29]
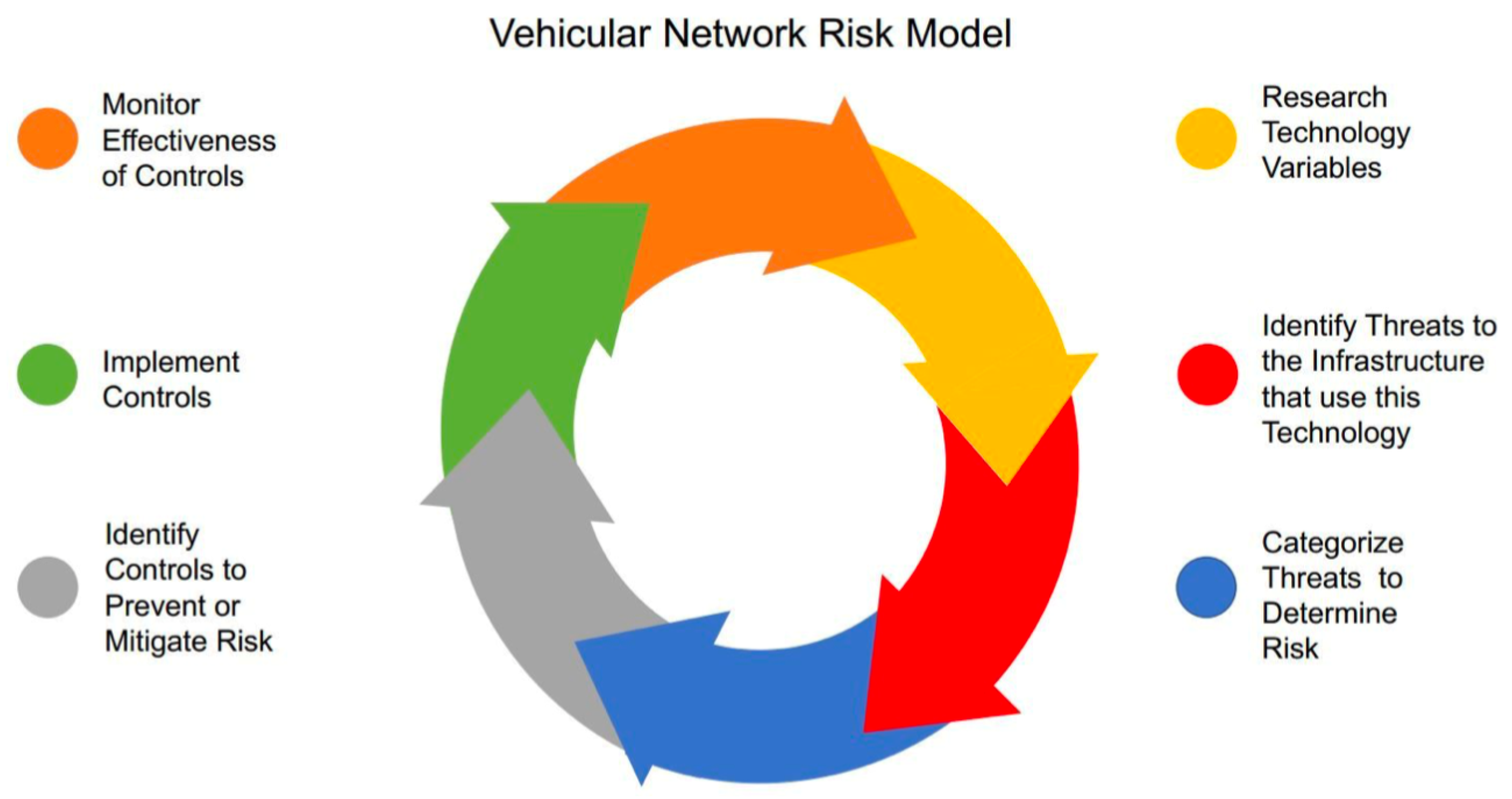
4.1. Vehicular Network Risk Model
- Research Technology Variables;
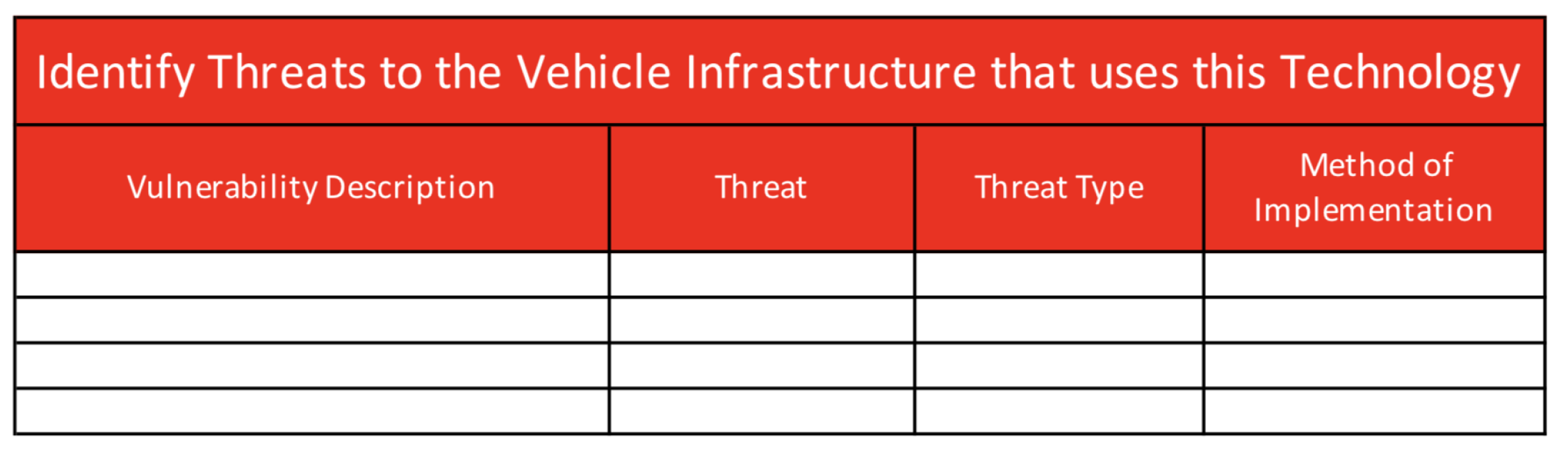
- Identify Threats to the infrastructure that use this Technology;
- Categorize Threats to Determine Risk;
- Identify Controls to Prevent or Mitigate Risk;
- Implement Controls;
- Monitor Effectiveness of Controls.
4.2. Risk Management Process
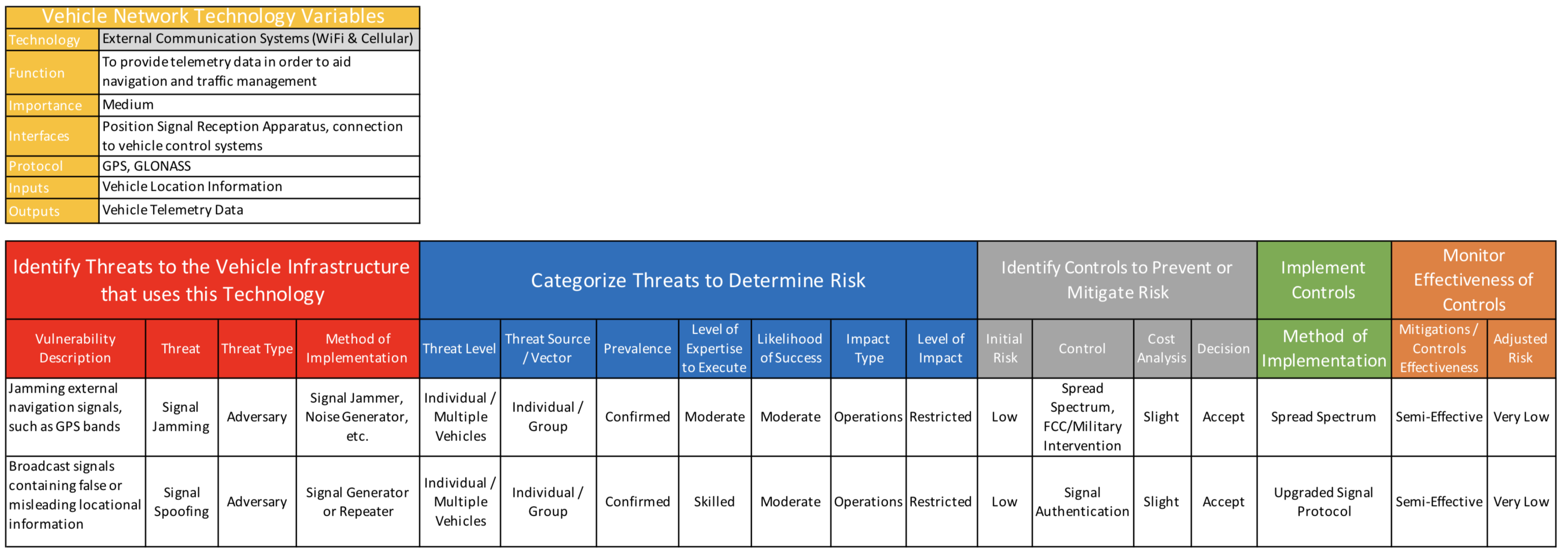
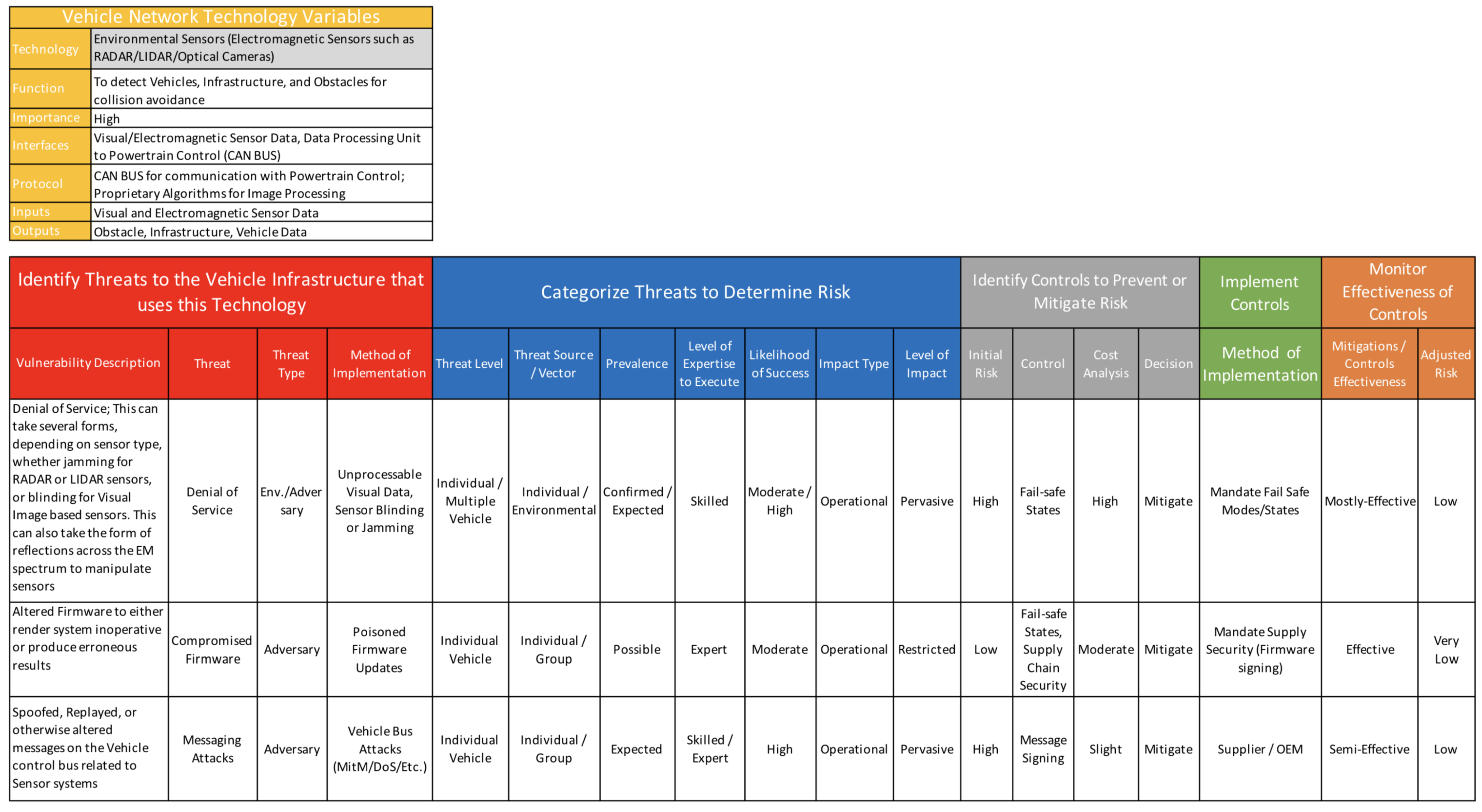
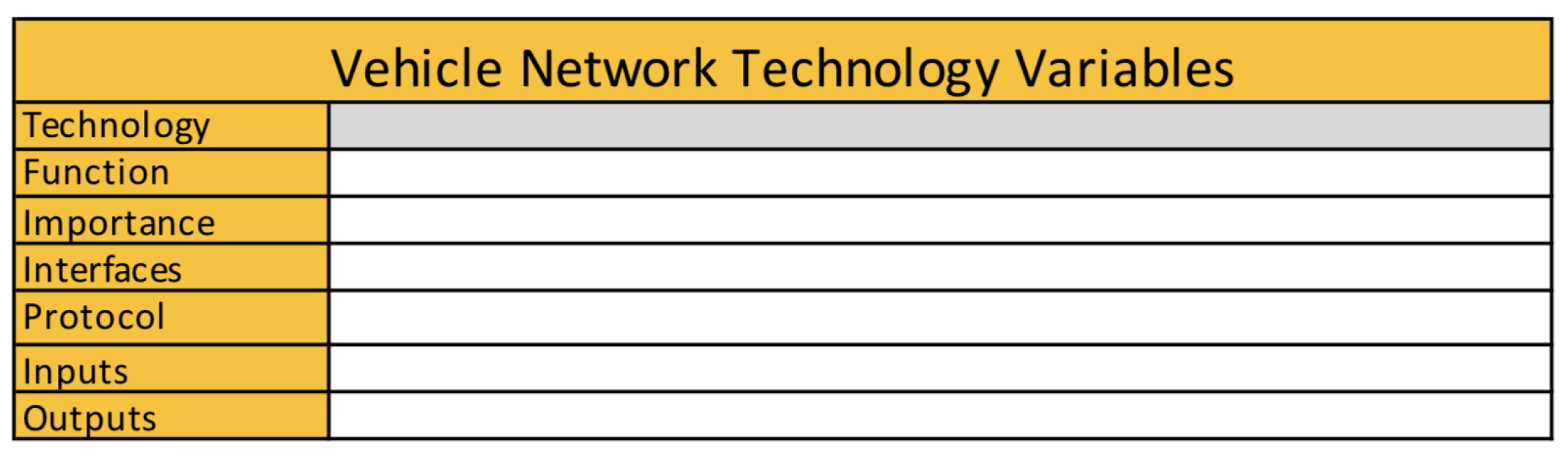
- Technology—The common name for the technology that the threat assessment is being done for;
- Function—The purpose of this technology in the vehicle network;
- Importance—The level of importance to the vehicle network (High, Medium, Low)
- Interfaces—How this technology connects within vehicle network;
- Protocol—Protocol standards used for the technology to communicate within the vehicle network;
- Inputs—Data input into this technology;
- Outputs—Where it sends the information once it is processed.
- Vulnerability Description—Brief description of what the vulnerability is for this vehicle network technology;
- Threat—The name of the threat or scenario that has been identified;
- Threat Type—The type of threat describes what the threat actually is. This is used to develop a scenario to better assess the level of the threat, intent, and where it is coming from. It can also be used to determine whether a threat is malicious, accidental, or environmental. Some threats can consists of one of the following:
- –
- User—Unsuspecting user of the network (non-malicious);
- –
- Adversary—Threat agent with malicious intent against the network;
- –
- Vehicle—Threat is an irregularity coming from one of the vehicles in the network;
- –
- Environmental—Threat is from environmental effects (e.g., Snow, Fog, Rain, Wind, Sand);
- –
- Equipment—Threat is coming from hardware incorporated in the network;
- Method of Implementation—This describes how the threat will be initiated into the network or how it will exploit vulnerabilities. This information can be used to develop controls later on in the process.
- Threat Level—This level describes the scope of the network that can be affected by this type of threat. In a malicious attack this would be the target of the attack. It could also be the amount of the network’s infrastructure that can be affected based on the threat scenario and its capabilities. This information can be used to determine the level of impact from this threat occurring in the network. The description of the level of infrastructure that can be affected by this threat can consists of one of the following:
- –
- Individual Vehicle—Only one vehicle in single location;
- –
- Multiple Vehicles—Capable of affecting more than one vehicle;
- –
- Critical Process—Affects a process that can affect the entire network;
- –
- Critical Infrastructure—Affects a part of the network’s infrastructure.
- Threat Source/Vector—The source/vector describes the size of the entity required to facilitate this threat. This is used to determine the required resources and likelihood of the threat occurring and can be used in control measure development. These can consist of one of the following:
- –
- Individual—Can be performed by one person acting alone;
- –
- Group/Organization—Takes an organized group to execute;
- –
- Nation—Takes the resources of a nation state to implement.
- Prevalence—The prevalence is directly proportional to the likelihood of this threat taking place on the vehicle network. This is based of historical evidence of this particular threat taking place inside a vehicle network;
- –
- Unlikely—Has not been seen in the vehicle network;
- –
- Possible—Has happened before in the network;
- –
- Expected—Happens often in the vehicle network;
- –
- Confirmed—Is happening currently in the network.
- Level of Expertise to Execute—The level of expertise that is required for a perpetrator to execute the attack against the system. The more skill that is required to execute an attack could mean the less prevalent it is and therefore make its occurrence less likely. Levels are categorized as:
- –
- None—This level is for non-adversarial threats, acts of nature, or accidents;
- –
- Novice—Little to no technical knowledge of the attack. Someone that is mimicking a previous attack or following a provided script. This could also include a user that unintentionally introduces the threat to the network;
- –
- Moderate—Attacker with limited skills or resources for attacks; Skilled—Attacker with the necessary experience and skills to execute successful attacks;
- –
- Expert—Attacker with high skills and significant resources at their disposal.
- Likelihood of Success—Based on analysis of the preceding variables and historical information, analysts can estimate the possibility that the attack will have its desired effect on the network. This information is used to determine the initial risk of the threat. The following categories are the success rates for this particular threat once introduced to the network.
- –
- Very Low—0%–4%
- –
- Low—5%–20%
- –
- Medium—21%–79%
- –
- High—80%–95%
- –
- Very High—96%–100%
- Impact Type—The impact type is the affected area of a successful occurrence of this threat. This information can be used to develop control measures. Types of impact can consist of one of the following:
- –
- Operational—The threat will affect how the network runs;
- –
- Assets—The threat will affect components of the network;
- –
- Network—The threat will affect the entire network.
- Level of Impact—This is used to estimate the portion of the vehicle network that will be impacted/affected if this threat is successful. This is used to perform a cost benefit analysis of a control and its effectiveness after it is implemented.
- –
- Small—0%–5%
- –
- Restricted—6%–25%
- –
- Moderate—26%–50%
- –
- Pervasive—51%–85%
- –
- Extreme—86%–100%
- Initial Risk—The initial risk of this threat occurring in the network. This is based on the proposed Risk Guide shown in Figure 6 that uses the likelihood of success of the threat and the impact it has against the network. For example, in Figure 6, if the impact level of a threat is moderate and the likelihood of success of the threat is moderate, the (initial) risk is considered “Moderate”. If both of them are assessed as “high”, then the risk is determined to be “high”.
- Control—After reviewing all the characteristics of the threat from previous analysis, analysts must now choose a viable control that will mitigate this threat by lowering its prevalence and/or impact to the network. More than one control measure can be identified to counteract this threat.
- Cost Analysis—This cost analysis is used to show the amount of resources it will take to implement this control to mitigate this threat. A cost may also be anything negative resulting if a control is not implemented properly or in a timely fashion. This can include network availability, assets, man hours, and publicity. Once again more than one control measure can be evaluated and this information can be used for a cost benefit analysis to help make a decision about what control(s) to implement. The costs can be described as:
- –
- None—The control is already in existence for other threats;
- –
- Slight—The control can be implemented through existing measures with minimal resources;
- –
- Moderate—The control may cause some inconveniences to the network or require expenditure of excess resources;
- –
- Serious—This control will require portions of the network to be shutdown and upgrade or require the expenditure of significant resources;
- –
- Extreme—This control will cause a network wide upgrade that can cause significant problems with network reliability. It will also require the expenditure of resources that are unavailable.
- Decision—After researching the types of controls to mitigate or prevent the risk and performing the cost analysis, a decision must be made about the best method to handle the risk. This decision should be based on available resources or expertise in dealing with this type of threat. The previous attributes in the process, such as, prevalence, likelihood of success, and impact, should also be taken into consideration when making this decision. The decision about the risk can consist of one the following:
- –
- Prevent—Implement a control that will eliminate the risk;
- –
- Accept—If the risk is to be accepted because it is low or implementing the control will have little to no effect, then analysts can make the decision to not do anything about this threat and accept the risk;
- –
- Mitigate—If the decision is made to accept the cost of implementing this control to lower the risk then it will be mitigated;
- –
- Transfer—If there is a third party that can implement the control measures more efficiently, then the control measure can be outsourced to a third party (e.g., insurance).
- Method of Implementation:
- –
- None—No control will be implemented;
- –
- Immediate—The resources are available to immediately implement the control;
- –
- Phased Implementation—A more deliberate approach will be used to integrate the control.
- Mitigation/Controls Effectiveness:
- –
- None—The control measures had no effect against the threat. If this is the case analysts need to make a decision to either give the control more time, alter it, or replace it altogether by reassessing the threat using earlier phases of the process;
- –
- Semi-Effective—This effectiveness level means that the control did prevent the threat, but not entirely or it hampered the system in some other ways that make it inadequate to mitigate the threat. Analysts should reassess the control to make it more effective or reassess the threat earlier in the process to ensure it was evaluated accurately;
- –
- Mostly-Effective—This level means that the control is making a significant impact against the threat with only minimal effect to the existing system;
- –
- Effective—This level of effectiveness means the control has worked against the threat and it no longer affects the system and the control has little or no effect on the system;
- Adjusted Risk—This is where the adjusted risk of the threat is measured after the control is fully implemented. An assessment of the control’s ability to lower the likelihood of success or level of impact can use the previous phases in the process in order to determine adjusted values. This needs to be done on a recurring basis to ensure that the risk level is accurate and has not changed. The same Risk Guide that was used to determine the initial risk would be used to determine the adjusted risk. Figure 7 demonstrates a lowered adjusted risk that is determined based on the lowered impact and/or likelihood of success.
4.3. Control Implementation Milestones Template
5. Use Case and Discussion
5.1. Phase 1
5.2. Phase 2
5.3. Phase 3
5.4. Phase 4
5.5. Phase 5
5.6. Phase 6
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Appendix A

References
- Boyes, H.A.; Luck, A.E.A. A Security-Minded Approach to Vehicle Automation, Road Infrastructure Technology, and Connectivity. In Proceedings of the 10th IET System Safety and Cyber-Security Conference 2015, Bristol, UK, 21–22 October 2015. [Google Scholar]
- Miller, C.; Valasek, C. Remote Exploitation of an Unaltered Passenger Vehicle. In Proceedings of the Black Hat USA 2015, Las Vegas, NV, USA, 1–6 August 2015. [Google Scholar]
- Ward, D.; Wooderson, P. Automotive cyber-security integrity levels. In Proceedings of the 11th International Conference on System Safety and Cyber-Security, London, UK, 11–13 October 2016. [Google Scholar]
- Rockl, M.; Strang, T.; Kranz, M. Demonstrator: V2V Communications in Automotive Multi-Sensor Multi-Target Tracking. In Proceedings of the 2008 IEEE 68th Vehicular Technology Conference, Calgary, AB, Canada, 21–24 September 2008. [Google Scholar]
- Obst, M.; Hobert, L.; Reisdorf, P. Multi-sensor data fusion for checking plausibility of V2V communications by vision-based multiple-object tracking. In Proceedings of the IEEE Vehicular Networking Conference (VNC), Paderborn, Germany, 3–5 December 2014. [Google Scholar]
- Stanganelli, J. Which Threat Risk Model Is Right for Your Organization? September 2016. Available online: https://www.esecurityplanet.com/network-security/which-threat-risk-model-is-right-for-your-organization.html (accessed on 11 September 2021).
- National Institute of Standards and Technology. Special Publication 800-30, Revision 1, Guide for Conducting Risk Assessments; NIST: Gaithersburg, MD, USA, 2012.
- Smith, C. The Car Hacker’s Handbook: A Guide for the Penetration Tester; No Starch Press: San Francisco, CA, USA, 2016. [Google Scholar]
- Sharma, P.; Liu, H.; Wang, H.; Zhang, S. Securing wireless communications of connected vehicles with artificial intelligence. In Proceedings of the 2017 IEEE International Symposium on Technologies for Homeland Security (HST), Waltham, MA, USA, 25–26 April 2017. [Google Scholar]
- Heineke, K.; Kampshoff, P.; Mkrtchyan, A.; Shao, E. Self-Driving Car Technology: When Will the Robots Hit the Road? 2017. Available online: https://www.mckinsey.com/industries/automotive-and-assembly/our-insights/self-driving-car-technology-when-will-the-robots-hit-the-road (accessed on 11 September 2021).
- Stewart, J. Don’t Freak Over Boeing’s Self-Flying Plane-Robots Already Run the Skies. Wired, June 2017. Available online: https://www.wired.com/story/boeing-autonomous-plane-autopilot/ (accessed on 11 September 2021).
- Federal Aviation Administration, Equip ADS-B. April 2018. Available online: https://www.faa.gov/nextgen/equipadsb/ (accessed on 11 September 2021).
- Federal Aviation Administration, ADS-B. January 2018. Available online: https://www.faa.gov/nextgen/programs/adsb/faq/#g1 (accessed on 11 September 2021).
- Federal Aviation Administration, Flight Risk Assessment Tool. 2008. Available online: https://www.faa.gov/news/safety_briefing/2015/media/SE_Topic_15-08.pdf (accessed on 11 September 2021).
- Federal Aviation Administration, Risk Management Handbook. FAA-H-8083-3; 2009. Available online: https://www.faa.gov/regulations_policies/handbooks_manuals/aviation/media/faa-h-8083-2.pdf (accessed on 11 September 2021).
- International Organization for Standardization. ISO 26262: Road Vehicles: Functional Safety; ISO: Geneva, Switzerland, 2012. [Google Scholar]
- International Organization for Standardization. ISO/IEC 15408-1: Informational Technology: Security Techniques: Evaluation Criteria for IT Security; ISO: Geneva, Switzerland, 2009. [Google Scholar]
- International Organization for Standardization. ISO/IEC 27001: Information Technology: Security Techniques: Information Security Management Systems: Requirements; ISO: Geneva, Switzerland, 2013. [Google Scholar]
- NHTSA. Vehicle-to-Vehicle Communication. April 2018. Available online: https://www.nhtsa.gov/technology-innovation/vehicle-vehicle-communication (accessed on 11 September 2021).
- SAE International. Surface Vehicle Recommended Practice: Cybersecurity Guidebook for Cyber-Physical Vehicle Systems; SAE International: Warrendale, PA, USA, 2016. [Google Scholar]
- National Institute of Standards and Technology. Special Publication 800-39, Managing Information Security Risk; NIST: Gaithersburg, MD, USA, 2011.
- National Institute of Standards and Technology. Special Publication 800-53, Security and Privacy Controls for Federal Information Systems and Organizations; NIST: Gaithersburg, MD, USA, 2017.
- National Institute of Standards and Technology. Special Publication 800-82, Guide to Industrial Control Systems (ICS) Security; NIST: Gaithersburg, MD, USA, 2015.
- National Highway Traffic Safety Administration. DOT HS 812 115, Critical Reasons for Crashes Investigated in the National Motor Vehicle Crash Causation Survey; NHTSA: Washington, DC, USA, 2015.
- NIST. Special Publication 800-37, Risk Management Framework for Information Systems and Organizations, REV 2; NIST: Gaithersburg, MD, USA, 2018.
- DODD. DODi 8510.01: Risk Management Framework (RMF) for DoD Information Technology (IT), Change 3; DODD: Washington, DC, USA, 2014.
- NASA/SP-2011-3422. NASA Risk Management Handbook, Version 1; NASA Headquarters: Washington, DC, USA, 2011.
- Department of Defense Risk. Issue, and Opportunity Management Guide for Defense Acquisition Programs; Office of the Deputy Assistant Secretary of Defense for Systems Engineering: Washington, DC, USA, 2017. [Google Scholar]
- International Organization for Standardization. ISO 31000: Risk Management—Guidelines; ISO: Geneva, Switzerland, 2018. [Google Scholar]
- Von Winterfeldt, D.; Fischer, G.W. Multi-attribute utility theory: Models and assessment procedures. In Utility, Probability, and Human Decision Making; PsycEXTRA Dataset; Springer: Dordrecht, The Netherlands, 1975. [Google Scholar]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ebert, J.; Newton, O.; O’Rear, J.; Riley, S.; Park, J.; Gupta, M. Leveraging Aviation Risk Models to Combat Cybersecurity Threats in Vehicular Networks. Information 2021, 12, 390. https://0-doi-org.brum.beds.ac.uk/10.3390/info12100390
Ebert J, Newton O, O’Rear J, Riley S, Park J, Gupta M. Leveraging Aviation Risk Models to Combat Cybersecurity Threats in Vehicular Networks. Information. 2021; 12(10):390. https://0-doi-org.brum.beds.ac.uk/10.3390/info12100390
Chicago/Turabian StyleEbert, Jonathan, Ohad Newton, Jeffery O’Rear, Scott Riley, Jaehong Park, and Maanak Gupta. 2021. "Leveraging Aviation Risk Models to Combat Cybersecurity Threats in Vehicular Networks" Information 12, no. 10: 390. https://0-doi-org.brum.beds.ac.uk/10.3390/info12100390





