Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles
Abstract
:1. Introduction
- Strengthen interest in automated vehicles, demonstrating that security risks have been mitigated, the concept of cyber security has been validated and verified, and systems have been systematically tested.
- Protect motorists and manufacturers by ensuring that cybersecurity threats are handled following state-of-the-art standards and best practices.
- Develop safe and state-of-the-art AV technologies by ensuring that the automated guidance systems adopted are developed with security-by-design and defense-in-depth in mind.
- Gain a competitive advantage by collaborating with international experts who have up-to-date knowledge on information security, vulnerabilities, and applicable standards.
- Continuous vulnerability management: defining authorized channels for firmware and application updates that restrict the perimeter of attack.
- Security maintainability: if we want to refer, for example, to the cryptographic protection of data, it is unlikely that the keys and algorithms adopted in the initial phase will guarantee the same level of protection over time. For this reason, Security-by-design must be associated with a modular development approach that allows the creation of products capable of adapting to emerging threats.
- Cybersecurity evolution: from this point of view, it is useful to refer to the experience gained by the aeronautical industry, where the use of partitioned embedded systems and domain segregation have made it possible to achieve particularly high security standards.
- The definition of a chain-of-trust, from the prototyping of the individual components of a vehicle, and the system that drives it, to the cloud infrastructure used for data exchange and communications. Solutions based on distributed technologies and blockchain can provide a fundamental contribution in the certification of the phases that participate in the production chain and in the dynamics of the supply chain.
- The implementation of interfaces dedicated to the sector that refer to specialized security policies. The need to develop such countermeasures is accentuated by the frequent use of technologies borrowed from other sectors, such as OTA and bluetooth connections.
2. Related Works
3. Backgrounds on Cybersecurity in IoT, Bayesian Networks and Information Security in Automotive
3.1. Cybersecurity in IoT
- Theft or damage of device: (perception layer) physical damage to the device.
- Side-channel attacks: (perception layer) collect information on the running time, power consumption, electromagnetic radiation, or sounds produced by a device during the execution of a particular task to deduce information contained in the device memory;
- Fake Node attacks: (perception layer) inserting into the network nodes created by the attacker in order to transmit bogus information or consume the resources, in terms of energy, of the legitimate nodes;
- Replay attacks: (perception layer) after having intercepted authentic credentials of a node; an attacker then sends them back to the recipient simulating the identity of the issuer;
- Node Tampering attacks: (perception layer) replace part of the node hardware or firmware with components created by the attacker and equipped with malicious functions;
- Jamming attacks: (perception layer) consists, if the nodes communicate via wireless protocols, of disturbing the frequencies used by the protocol;
- Denial-of-Service (DoS): (network layer) its purpose is to prevent reaching the nodes via the network. To achieve this goal, it is possible to use many techniques, such as sending a large number of bogus packets on the network to make sure that the various nodes have more information in input than they can process (flooding), compromising a node in the network in order to modify its topology and degrade its performance (sinkhole attack);
- Man-in-the-middle: (network layer) consists of intercepting the data transmitted by the various nodes before they arrive at the recipient to steal them or retransmit a modified version;
- Storage attacks: (network layer) consist of modifying user information in the device memory or in the cloud;
- Routing attacks: (network layer) a class of attacks (the sinkhole attack is an example) in which an attacker tries to alter the information that the devices use to route packets to create loops, to send error messages, or to lose packets;
- Cross-Site-Scripting (XSS): (application layer), which uses client-side scripting languages (for example, JavaScript) to execute malicious code through a browser that shows a specific web page. This type of attack is also exploited in the IoT field because embedded devices often use web interfaces for configuration, more particularly in this case, we speak of Cross-Channel-Scripting (XCS);
- Malicious Code: (application layer) inject malicious code (malware) into the application for it to execute it;
- Credential theft: (application layer) in order to impersonate legitimate users. This layer can be accomplished through eavesdropping, man-in-the-middle attacks, brute force or dictionary attacks (to try to guess credentials), etc.
3.2. Bayesian Network
3.3. Information Security in Automotive
- Physical access points: allow direct or indirect physical access to the car’s internal network (USB, OBD, etc.).
- Short range access points: allow communication with the vehicle at a distance that generally varies from 5 to 300 m. Interfaces such as Wi-Fi, bluetooth, remote keyless entry (RKE), tire pressure monitoring system (TPMS), etc., are part of this class.
- Long range access points: allow communication with the vehicle at a distance greater than 1 km. Its groups interfaces include cellular networks (4G, 5G), global positioning system (GPS), etc.
3.3.1. Encryption, Access Control and Authentication Systems
3.3.2. Intrusion Detection System
- Signature detection based in which the collected data are compared with traces of already known attacks looking for a correspondence that confirms the fact that there is an attack in progress;
- Anomaly detection based, by which the system’s behavior is monitored by checking that its methods of use do not deviate from the regular use.
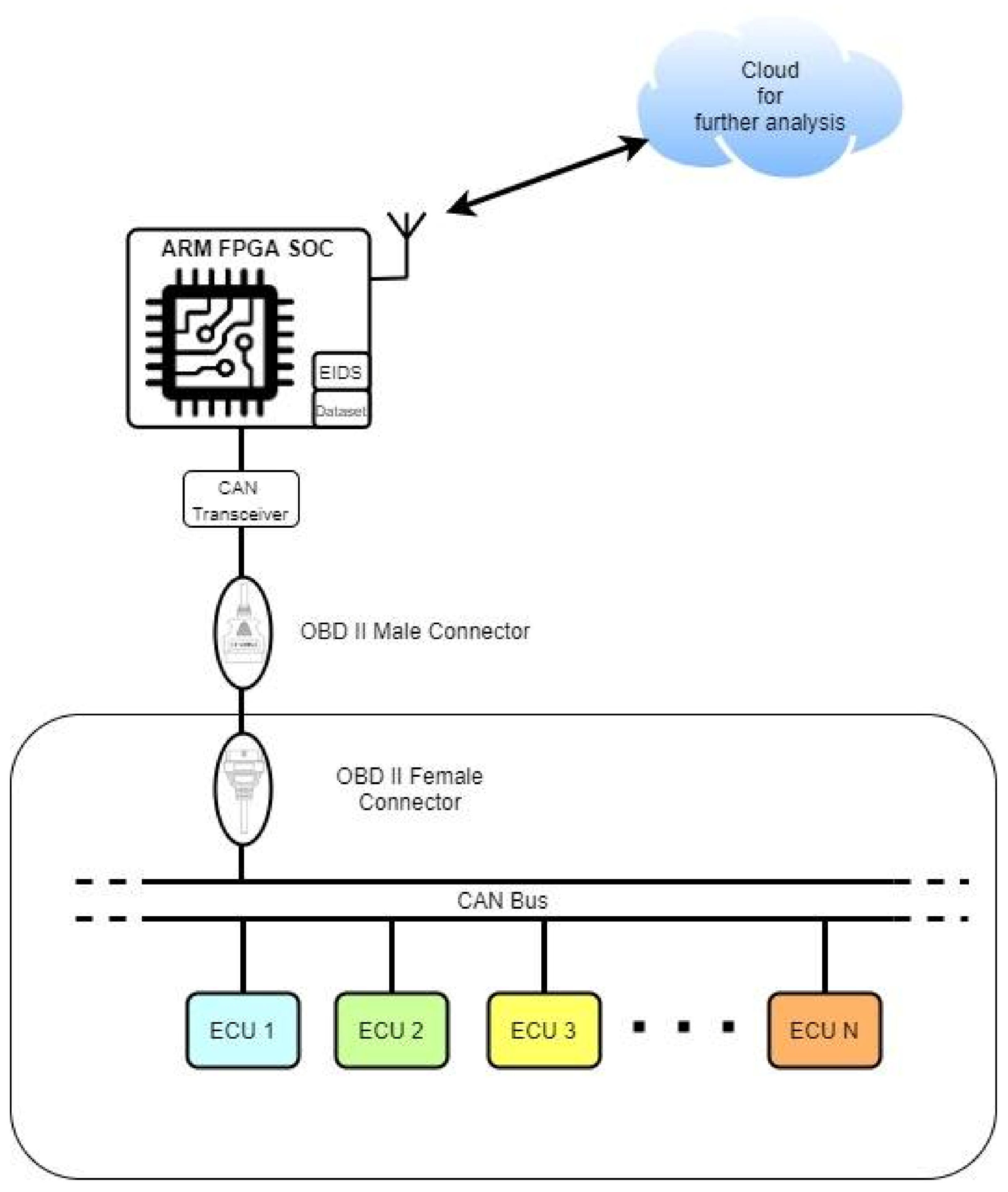
4. The Proposed Approach and Methodology
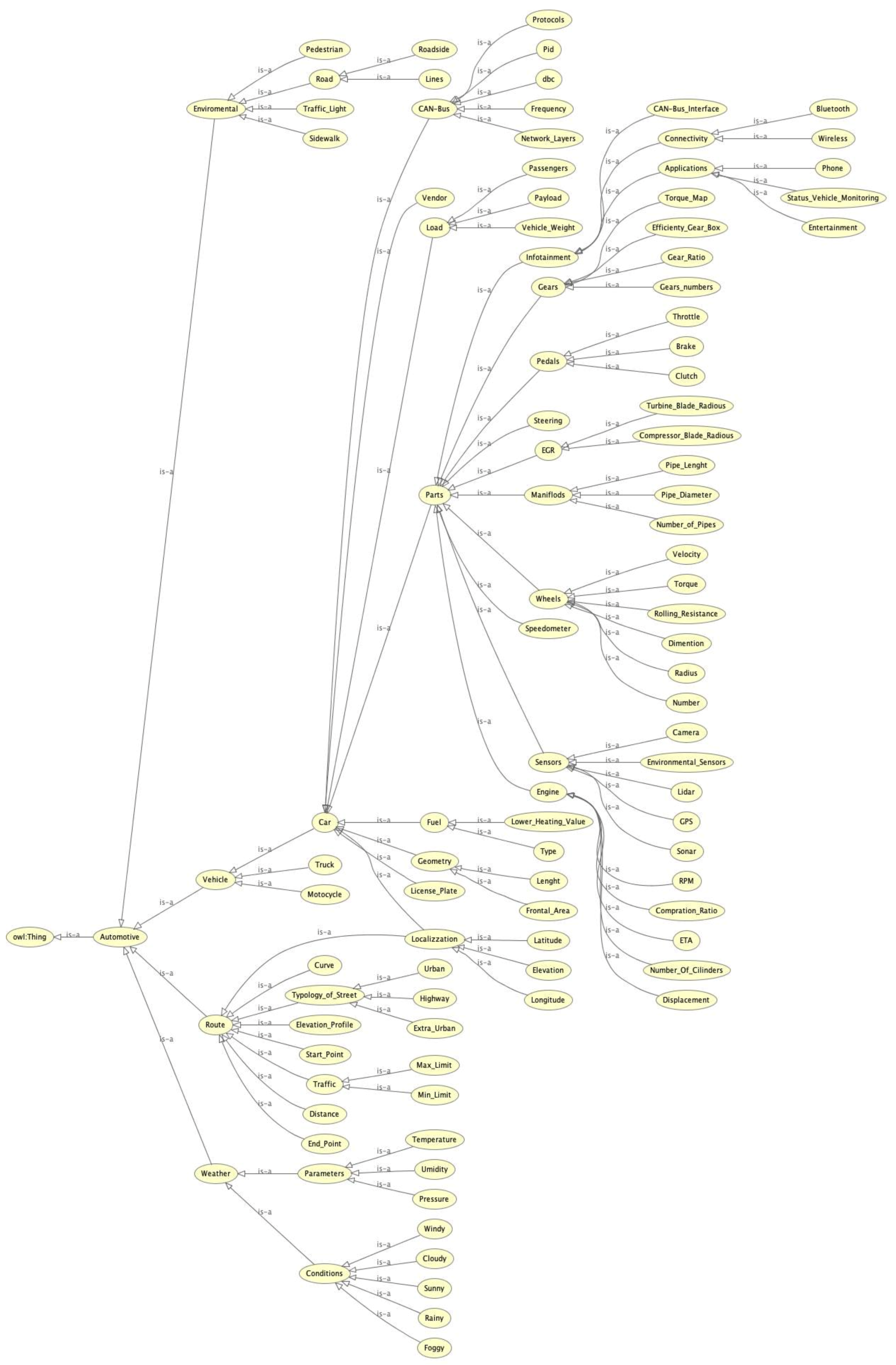
4.1. Case of Study
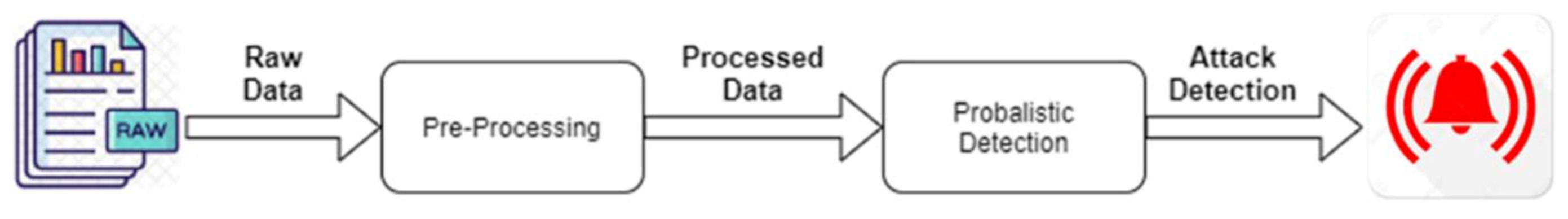
4.2. Two-Steps Algorithm
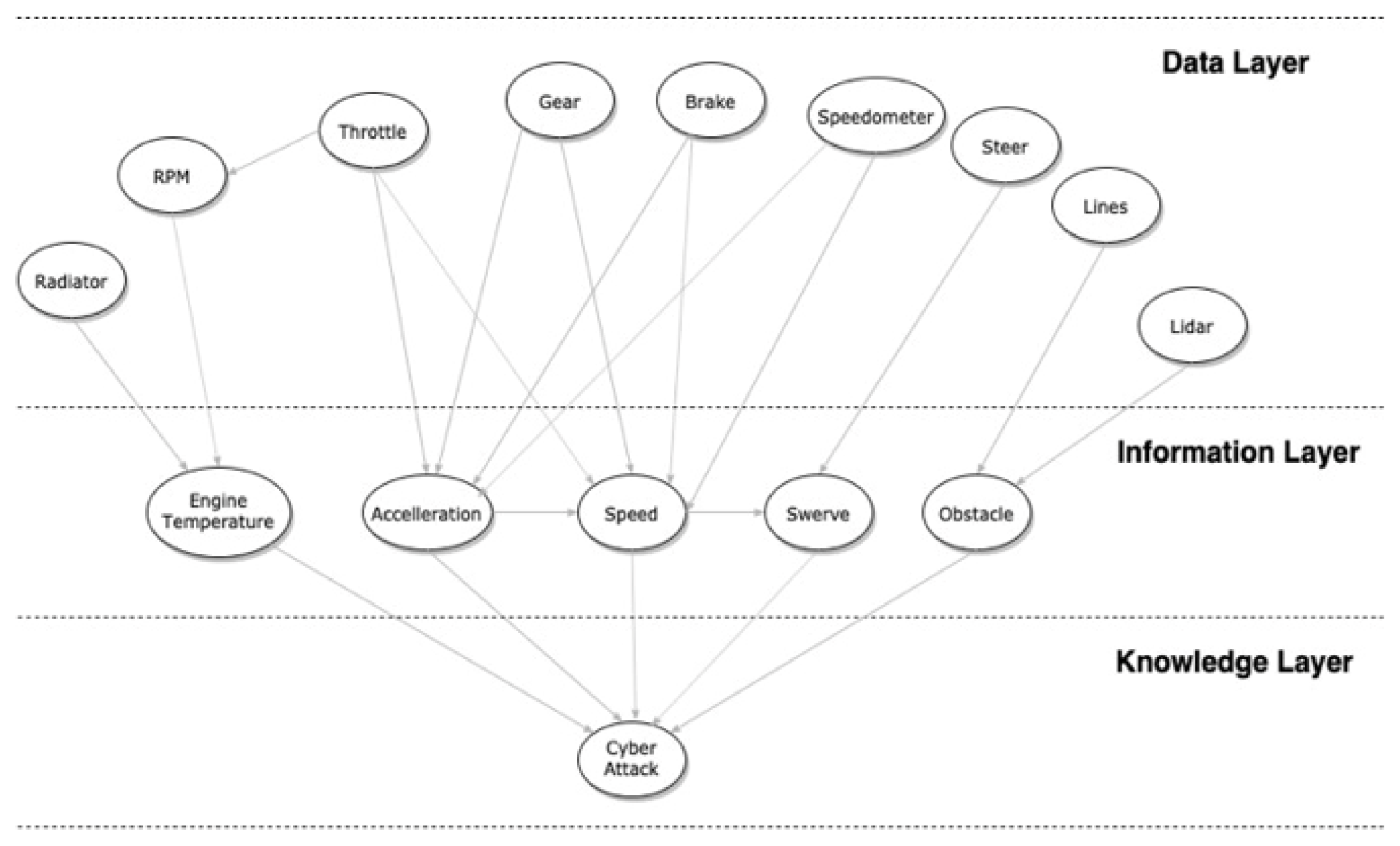
- The first step, called pre-processing, analyzes ten state frames (containing each frame the exact values of each car parameter considered for our case study, tab). Moreover, it verifies through spatial and temporal analysis obtained from an analysis of the problem whether it may or may not be a possible attack in that sequence of values. Each status frame is recorded with a unique timestamp, and its recording takes place every 4 ms.
- In the second step, through the use of a Bayesian network, previously trained through a pre-established data set during the simulation phase, it can decide whether we are in the presence or not of an attack, keeping in mind both the parameters that make up the frame values status, and the parameters obtained as information from these parameters.
- Steer: CAN message related to steering, 7 classes (−1:1 norm., step variable, very left, middle left, left, center, right, middle right, very right);
- Throttle: CAN message related to acceleration, 4 classes (0:1 norm., step variable, pedal not pressed, low, medium, high);
- Brake: CAN message related to braking, 4 classes (0:1 norm., pedal not pressed-low, medium, high);
- RPM: CAN message related to rotations per minute, 5 classes (0:1, step variable, stop, slow, normal, medium, high);
- Gear: CAN message related to gear of car, 5 classes (0, 1, 2, 3, 4, 5);
- Radiator: State of ignition of the cooling system, 2 classes (on, off);
- Lidar: Presence or absence of obstacles, 2 classes (0, 1);
- Lines: Crossing a road line or not, 2 classes (0, 1);
- Speedometer: Speed in absolute value, 6 classes (0:1 norm., stop, very slowly, slowly, medium, fast, very fast);
- Acceleration: Car acceleration, 5 classes (−1:1 norm., step variable, deceleration high, deceleration low, no acceleration, acceleration low, acceleration high);
- Speed: Car current speed, 6 classes (0:1 norm., step variable, stop [0 km/h], very slowly [0–30 km/h], slowly [30–50 km/h], medium [50–90 km/h], fast [90–130 km/h], very fast [130–150 km/h]);
- Engine Temperature: Car engine temperature, 4 classes (0:150, step variable, normal operation, low overheating, medium overheating, high overheating);
- Swerve: Car swerve, 7 classes (−1:1 norm., step 0.285, very left [−60° to −45°], middle left [−45° to −30°], left [−30° to −5°], center [−5° to 5°], right [5° to 30°], middle right [30° to 45°], very right [45° to 60°]);
- Obstacle: Presence or absence of generic obstacle within a radius of 20 m, 2 classes (true, false);
- Attack: Presence or absence of attack, 2 classes (true, false).
5. Experimental Results
- DoS attack: injecting messages of ‘0 × 000’ CAN ID in a short cycle.
- Fuzzy attack: injecting messages of spoofed random CAN ID and DATA values.
- Impersonation attack: injecting messages of Impersonating node, arbitration ID = ‘0 × 164’.
- Attack Free State: normal CAN messages.
- True Positives (TP): attack present and correct classification;
- True Negatives (TN): attack not present and correct classification;
- False Positives (FP): attack not present and incorrect classification;
- False Negatives (FN): attack present and incorrect classification.
6. Conclusions
7. Patents
Author Contributions
Funding
Conflicts of Interest
References
- Lombardi, M.; Pascale, F.; Santaniello, D. Internet of Things: A General Overview between Architectures, Protocols and Applications. Information 2021, 12, 87. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, L.D. Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics. IEEE Internet Things J. 2019, 6, 2103–2115. [Google Scholar] [CrossRef]
- Botte, M.; Pariota, L.; D’Acierno, L.; Bifulco, G.N. C-ITS communication: An insight on the current research activities in the European Union. Int. J. Transp. Syst. 2018, 3, 52–63. [Google Scholar]
- Nzabahimana, J.P. Analysis of security and privacy challenges in Internet of Things. In Proceedings of the 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, Ukraine, 24–27 May 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 175–178. [Google Scholar]
- Whitman, M.E.; Mattord, H.J. Principles of Information Security, 4th ed.; Course Technology: Boston, MA, USA, 2011. [Google Scholar]
- Chhawri, S.; Tarnutzer, S.; Tasky, T.; Lane, G.R. Smart Vehicles, Automotive Cyber Security & Software safety applied to Leader-Follower (LF) and Autonomous Convoy Operations. In Proceedings of the 2017 Ground Vehicle Systems Engineering and Technology Symposium (GVSETS), Novi, MI, USA, 8–10 August 2017. [Google Scholar]
- Haus, M.; Waqas, M.; Ding, A.Y.; Li, Y.; Tarkoma, S.; Ott, J. Security and Privacy in Device-to-Device (D 2 D) Communication: A Review. IEEE Commun. Surv. Tutor. 2017, 19, 1054–1079. [Google Scholar] [CrossRef]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2016, 18, 1153–1176. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Azwar, H.; Murtaz, M.; Siddique, M.; Rehman, S. Intrusion Detection in secure network for Cybersecurity systems using Machine Learning and Data Mining. In Proceedings of the 2018 IEEE 5th International Conference on Engineering Technologies and Applied Sciences (ICETAS), Bangkok, Thailand, 22–23 November 2018; pp. 1–9. [Google Scholar]
- Lokman, S.-F.; Othman, A.T.; Abu Bakar, M.H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 184. [Google Scholar] [CrossRef] [Green Version]
- Kulandaivel, S.; Goyal, T.; Agrawal, A.K.; Sekar, V. Canvas: Fast and inexpensive automotive network mapping. In Proceedings of the 28th USENIX Security Symposium, Santa Clara, CA, USA, 14–16 August 2019; pp. 389–405. [Google Scholar]
- Lin, C.-W.; Sangiovanni-Vincentelli, A. Cyber-Security for the Controller Area Network (CAN) Communication Protocol. In Proceedings of the 2012 International Conference on Cyber Security, Alexandria, VI, USA, 14–16 December 2012; pp. 1–7. [Google Scholar]
- Fowler, D.S.; Cheah, M.; Shaikh, S.A.; Bryans, J. Towards a Testbed for Automotive Cybersecurity. In Proceedings of the 2017 IEEE International Conference on Software Testing, Verification and Validation, Tokyo, Japan, 13–17 March 2017; pp. 540–541. [Google Scholar]
- Hoppe, T.; Kiltz, S.; Dittmann, J. Security threats to automotive can networks—Practical examples and selected short-term countermeasures. Reliab. Eng. Syst. Saf. 2011, 96, 11–25. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental Security Analysis of a Modern Automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Barkeley, CA, USA, 22–25 May 2010; pp. 447–462. [Google Scholar]
- Onishi, H. Paradigm change of vehicle cyber security. In Proceedings of the 2012 4th International Conference on Cyber Conflict (CYCON 2012), Tallinn, Estonia, 5–8 June 2012; pp. 1–11. [Google Scholar]
- Reilly, J.; Martin, S.; Payer, M.; Bayen, A. On cybersecurity of freeway control systems: Analysis of coordinated ramp metering attacks. Transp. Res. 2014, 1–20. [Google Scholar]
- Li, R.; Liu, C.; Luo, F. A design for automotive CAN bus monitoring system. In Proceedings of the 2008 IEEE Vehicle Power and Propulsion Conference, Harbin, China, 3–5 September 2008; pp. 1–5. [Google Scholar]
- Zalman, R.; Mayer, A. A secure but still safe and low cost auto- motive communication technique. In Proceedings of the 51st Annual Design Automation Conference, San Francisco, CA, USA, 1–5 June 2014; pp. 1–5. [Google Scholar]
- Olufowobi, H.; Young, C.; Zambreno, J.; Bloom, G. SAIDuCANT: Specification-Based Automotive Intrusion Detection Using Controller Area Network (CAN) Timing. IEEE Trans. Veh. Technol. 2019, 69, 1484–1494. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Walton, R.; Van Kleek, M.; Montalvo, R.M.; Maddox, L.; Santos, O.; Burnap, P.; Anthi, E. Artificial intelligence and machine learning in dynamic cyber risk analytics at the edge. SN Appl. Sci. 2020, 2, 1–8. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.C.; Nurse, J.R.C.; Montalvo, R.M.; Cannady, S.; Santos, O.; Maddox, L.; Burnap, P.; Maple, C. Future developments in standardisation of cyber risk in the Internet of Things (IoT). SN Appl. Sci. 2020, 2, 1–16. [Google Scholar] [CrossRef] [Green Version]
- Waqas, M.; Niu, Y.; Li, Y.; Ahmed, M.; Jin, D.; Chen, S.; Han, Z. A Comprehensive Survey on Mobility-Aware D2D Communications: Principles, Practice and Challenges. IEEE Commun. Surv. Tutor. 2019, 22, 1863–1886. [Google Scholar] [CrossRef] [Green Version]
- Ullah, S.; Abbas, G.; Waqas, M.; Abbas, Z.; Tu, S.; Hameed, I. EEMDS: An Effective Emergency Message Dissemination Scheme for Urban VANETs. Sensors 2021, 21, 1588. [Google Scholar] [CrossRef]
- Vijayalakshmi, A.V.; Arockiam, L. A Study on Security Issues and Challenges in IoT. Int. J. Eng. Sci. Manag. Res. 2016, 3, 34–43. [Google Scholar]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the IoT world: Present and future challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Wang, H.; Te Lai, T.T.; Choudhury, R.R. MoLe: Motion leaks through smartwatch sensors. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking, Paris, France, 7–11 September 2015; pp. 155–166. [Google Scholar]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.-S. IoT Elements, Layered Architectures and Security Issues: A Comprehensive Survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [Green Version]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the Internet of Things (IoT): A Security Taxonomy for IoT. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 163–168. [Google Scholar]
- Ali, I.; Sabir, S.; Ullah, Z. Internet of Things Security, Device Authentication and Access Control: A Review. arXiv 2019, arXiv:1901.07309. [Google Scholar]
- Zhang, T.; Antunes, H.; Aggarwal, S. Defending Connected Vehicles against Malware: Challenges and a Solution Framework. IEEE Internet Things J. 2014, 1, 10–21. [Google Scholar] [CrossRef]
- Lea, P. Internet of Things for Architects: Architecting IoT Solutions by Implementing Sensors, Communication Infrastructure, Edge Computing, Analytics, and Security, 1st ed.; Packt Publishing: Birmingham, UK, 2018. [Google Scholar]
- Sidhu, S.; Mohd, B.J.; Hayajneh, T. Hardware Security in IoT Devices with Emphasis on Hardware Trojans. J. Sens. Actuator Netw. 2019, 8, 42. [Google Scholar] [CrossRef] [Green Version]
- Levi, M.; Allouche, Y.; Kontorovich, A. Advanced Analytics for Connected Car Cybersecurity. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018. [Google Scholar]
- Huang, J.; Zhao, M.; Zhou, Y.; Xing, C.-C. In-Vehicle Networking: Protocols, Challenges, and Solutions. IEEE Netw. 2018, 33, 92–98. [Google Scholar] [CrossRef]
- Macher, G.; Armengaud, E.; Brenner, E.; Kreiner, C. Threat and Risk Assessment Methodologies in the Automotive Domain. Procedia Comput. Sci. 2016, 83, 1288–1294. [Google Scholar] [CrossRef] [Green Version]
- Smith, C. The Car Hacker’s Handbook: A Guide for the Penetration Tester; No Starch Press: San Francisco, CA, USA, 2016. [Google Scholar]
- Carsten, P.; Andel, T.R.; Yampolskiy, M.; McDonald, J.T. In-vehicle networks: Attacks, vulnerabilities, and proposed solutions. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 6–8 April 2015; pp. 1–8. [Google Scholar]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive Experimental Analyses of Automotive Attack Surfaces. In Proceedings of the USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011; p. 2021. [Google Scholar]
- Li, S. Securing the Internet of Things; Syngress: Maryland Heights, MO, USA, 2017; pp. 69–95. [Google Scholar]
- Tu, S.; Waqas, M.; Huang, F.; Abbas, G.; Abbas, Z.H. A revocable and outsourced multi-authority attribute-based encryption scheme in fog computing. Comput. Netw. 2021, 195, 108196. [Google Scholar] [CrossRef]
- Tu, S.; Waqas, M.; Rehman, S.U.; Mir, T.; Abbas, G.; Abbas, Z.H.; Halim, Z.; Ahmad, I. Reinforcement Learning Assisted Impersonation Attack Detection in Device-to-Device Communications. IEEE Trans. Veh. Technol. 2021, 70, 1474–1479. [Google Scholar] [CrossRef]
- Tu, S.; Waqas, M.; Meng, Y.; Rehman, S.U.; Ahmad, I.; Koubaa, A.; Halim, Z.; Hanif, M.; Chang, C.-C.; Shi, C. Mobile fog computing security: A user-oriented smart attack defense strategy based on DQL. Comput. Commun. 2020, 160, 790–798. [Google Scholar] [CrossRef]
- Tanveer, M.; Abbas, G.; Abbas, Z.H.; Waqas, M.; Muhammad, F.; Kim, S. S6AE: Securing 6LoWPAN Using Authenticated Encryption Scheme. Sensors 2020, 20, 2707. [Google Scholar] [CrossRef] [PubMed]
- Waqas, M.; Tu, S.; Rehman, S.U.; Halim, Z.; Anwar, S.; Abbas, G.; Abbas, Z.H.; Rehman, O.U. Authentication of Vehicles and Road Side Units in Intelligent Transportation System. Comput. Mater. Contin. 2020, 64, 359–371. [Google Scholar] [CrossRef]
- Di Mauro, M.; Galatro, G.; Liotta, A. Experimental Review of Neural-Based Approaches for Network Intrusion Management. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2480–2495. [Google Scholar] [CrossRef]
- Syzdykbayev, M.; Hajari, H.; Karimi, H.A. An Ontology for Collaborative Navigation Among Autonomous Cars, Drivers, and Pedestrians in Smart Cities. In Proceedings of the 2019 4th International Conference on Smart and Sustainable Technologies (SpliTech), Split, Croatia, 18–21 June 2019; pp. 1–6. [Google Scholar]
- Klotz, B.; Datta, S.K.; Wilms, D.; Troncy, R.; Bonnet, C. A Car as a Semantic Web Thing: Motivation and Demonstration. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; pp. 1–6. [Google Scholar]
- Klotz, B.; Troncy, R.; Wilms, D.; Bonnet, C. VSSo: A Vehicle Signal and Attribute Ontology. In Proceedings of the 9th International Semantic Sensor Networks Workshop, Monterey, CA, USA, 9 October 2018. [Google Scholar]
- Colace, F.; De Santo, M. Ontology for E-Learning: A Bayesian Approach. IEEE Trans. Educ. 2009, 53, 223–233. [Google Scholar] [CrossRef]
- Colace, F.; De Santo, M.; Vento, M. A MultiExpert Approach for Bayesian Network Structural Learning. In Proceedings of the 2010 43rd Hawaii International Conference on System Sciences, Honolulu, HI, USA, 5–8 January 2010; pp. 1–11. [Google Scholar]
- Colace, F.; De Santo, M.; Lombardi, M.; Pascale, F.; Santaniello, D.; Tucker, A. A Multilevel Graph Approach for Predicting Bicycle Usage in London Area. In Proceedings of the 4th International Congress on Information and Communication Technology. Advances in Intelligent Systems and Computing, London, UK, 25–26 February 2019; Volume 1027. [Google Scholar] [CrossRef]
- Casillo, M.; Coppola, S.; De Santo, M.; Pascale, F.; Santonicola, E. Embedded Intrusion Detection System for Detecting Attacks over CAN-BUS. In Proceedings of the 2019 4th International Conference on System Reliability and Safety (ICSRS), Rome, Italy, 20–22 November 2019; pp. 136–141. [Google Scholar]
- Lombardi, M.; Pascale, F.; Santaniello, D. EIDS: Embedded Intrusion Detection System using Machine Learning to Detect Attack over the CAN-BUS. In Proceedings of the 30th European Safety and Reliability Conference and the 15th Probabilistic Safety Assessment and Management Conference, Venice, Italy, 21–26 June 2020. [Google Scholar] [CrossRef]
- Colace, F.; Khan, M.; Lombardi, M.; Santaniello, D. A Multigraph Approach for Supporting Computer Network Monitoring Systems. In Proceedings of the 5th International Congress on Information and Communication Technology, London, UK, 20–21 February 2021; pp. 470–477. [Google Scholar]
- Castiglione, A.; Palmieri, F.; Colace, F.; Lombardi, M.; Santaniello, D.; D’Aniello, G. Securing the internet of vehicles through lightweight block ciphers. Pattern Recognit. Lett. 2020, 135, 264–270. [Google Scholar] [CrossRef]
- Dosovitskiy, A.; Ros, G.; Codevilla, F.; Lopez, A.; Koltun, V. CARLA: An open urban driving simulator. arXiv 2017, arXiv:1711.03938, preprint. [Google Scholar]
- Mhetre, V.; Nagar, M. Classification based data mining algorithms to predict slow, average and fast learners in educational system using WEKA. In Proceedings of the 2017 International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 18–19 July 2017; pp. 475–479. [Google Scholar]
- Ertam, F.; Aydin, G. Data classification with deep learning using Tensorflow. In Proceedings of the 2017 International Conference on Computer Science and Engineering (UBMK), Antalya, Turkey, 5–7 October 2017; pp. 755–758. [Google Scholar]
- Lee, H.; Jeong, S.H.; Kim, H.K. OTIDS: A Novel Intrusion Detection System for In-vehicle Network by Using Remote Frame. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 57–5709. [Google Scholar] [CrossRef]
- Di Mauro, M.; Galatro, G.; Fortino, G.; Liotta, A. Supervised feature selection techniques in network intrusion detection: A critical review. Eng. Appl. Artif. Intell. 2021, 101, 104216. [Google Scholar] [CrossRef]
- Erhan, L.; Ndubuaku, M.; Di Mauro, M.; Song, W.; Chen, M.; Fortino, G.; Bagdasar, O.; Liotta, A. Smart anomaly detection in sensor systems: A multi-perspective review. Inf. Fusion 2021, 67, 64–79. [Google Scholar] [CrossRef]
- Pascale, F.; Adinolfi, E.A.; Avagliano, M.; Giannella, V.; Salas, A. A Low Energy IoT Application Using Beacon for Indoor Localization. Appl. Sci. 2021, 11, 4902. [Google Scholar] [CrossRef]

| Detected Attack | YES | NOT |
|---|---|---|
| YES | True Positives (TP) | False Negatives (FN) |
| NOT | False Positives (FP) | True Negatives (TN) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pascale, F.; Adinolfi, E.A.; Coppola, S.; Santonicola, E. Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles. Electronics 2021, 10, 1765. https://0-doi-org.brum.beds.ac.uk/10.3390/electronics10151765
Pascale F, Adinolfi EA, Coppola S, Santonicola E. Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles. Electronics. 2021; 10(15):1765. https://0-doi-org.brum.beds.ac.uk/10.3390/electronics10151765
Chicago/Turabian StylePascale, Francesco, Ennio Andrea Adinolfi, Simone Coppola, and Emanuele Santonicola. 2021. "Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles" Electronics 10, no. 15: 1765. https://0-doi-org.brum.beds.ac.uk/10.3390/electronics10151765






