In this section, we demonstrate how we can model different aspects of anonymity of a currency scheme, in terms of the proposed framework. First, we formulate a parametric game to capture different attacker scenarios, each of which represents a different aspect of anonymity. Then, we provide a group of definitions for several anonymity properties stemming from the fundamental concept of indistinguishability. The term indistinguishability means that it is not possible to distinguish between two known entities in a given situation, e.g., inability to distinguish the sender of a transaction from two possible sender addresses.
We define these anonymity notions around a set of entities in a typical currency scheme. These entities can be categorized as topological and non-topological where topological entities directly correspond to entities in the transaction graph of the scheme. Senders and recipients form the topological category whereas value and other relevant metadata are categorized as non-topological entities, without having a direct relationship to the transaction graph. We parameterize different scenarios where an attacker can manipulate these entities at various levels.
5.1. Anonymity Game
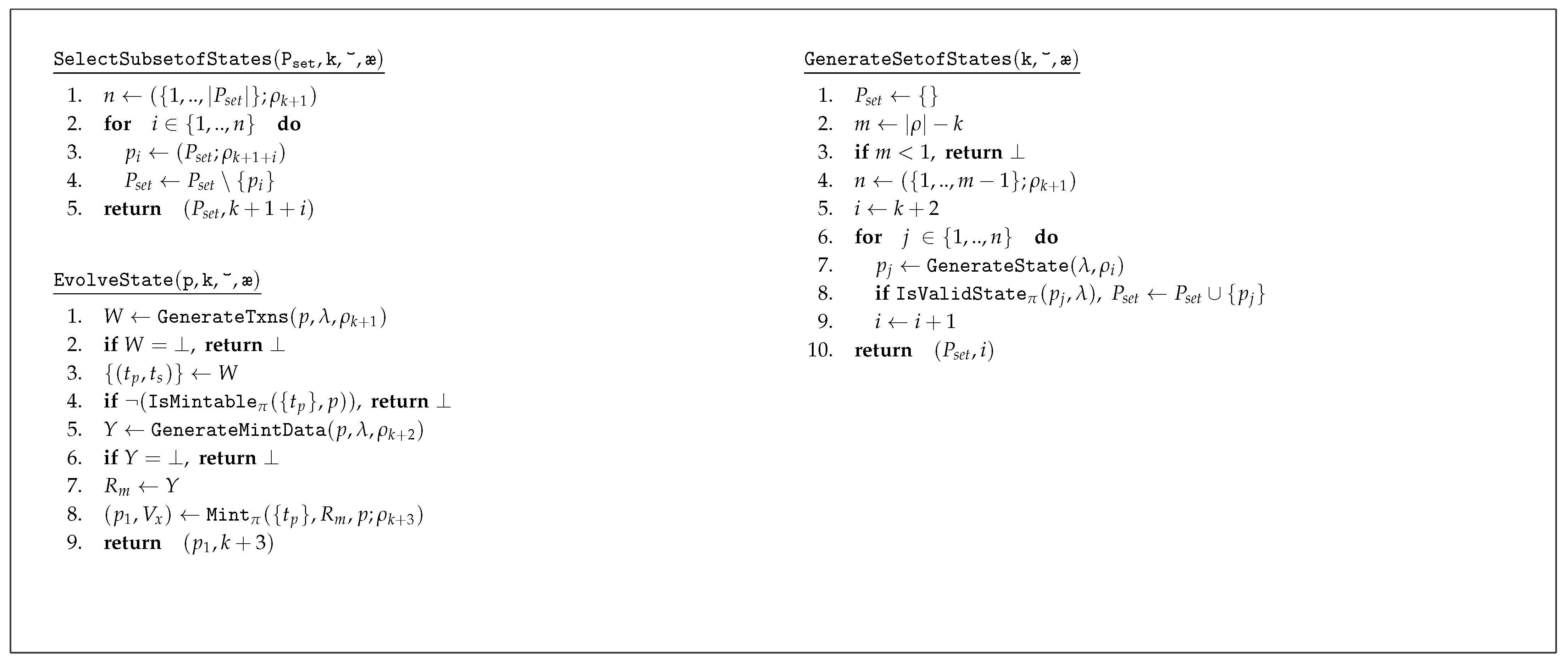
In order to facilitate the execution of the Anonymity game in a more transparent manner, we define a few additional helper functions to check the adversarial conditions of inputs at the start of the game (
) and to reveal data to the adversary at the end (
) based on the parameter
(
Figure 4). Note that for a particular security notion,
is constant. Moreover, we also introduce another variable,
, to represent test variable/s. We define
with each
to indicate which entity (sender/recipient/value/metadata) is being tested in a given instance of the game, based on which the transaction data are varied. The adversarial inputs to the game are crafted based on
. We now define a common game to capture all possible attacker scenarios in this setting.
Figure 5 illustrates the game.
Execution of the Game
The game is executed as follows. The state initialization takes place at the beginning of the execution of the game based on (line 3). The game continues if the returned state is valid. Here, we use ‘’ notation to check this condition. In this notation, if the condition inside the brackets is false, then the game terminates and the adversary loses the game. In this case, if the state is valid, the adversary provides a set of data (to be used in creating transactions, minting, etc.) to the challenger, based on the values of parameters with respect to senders, recipients, values, and metadata. These data include two sets of senders , , recipients , , input/output values , , miners’ addresses , metadata , , a set of transactions T (to be minted), two additional transactions , , two sets of randomness of coins , , together with the current state (line 4). If sender/recipient addresses are hidden, respective outputs should be handles to those hidden addresses created by the oracle, i.e., , , , . The adversary can make corresponding oracle calls to create hidden addresses, and opaque handles to those addresses are given in return. In addition, if transaction values are hidden (i.e., ), then the adversary provides maximum values for respective input and output values (through , ), and the oracle chooses appropriate transaction values accordingly. If , then adversary returns a handle for hidden metadata. The transactions and represent two transactions created by the adversary when . For other values of , these will remain null. The inputs and provide the randomness (of coins) required to create the transactions when , or will be empty, otherwise. According to the values of , the challenger checks whether the values returned by the adversary meet the expected criteria (through the function) and terminates the game if any of the inputs are invalid (line 7). Upon submission of valid inputs, the adversary continues to evolve the current state through appropriate oracle queries.
Next, the challenger checks whether , in which case the adversary produces the required transactions (which will be considered as and ). Otherwise, the challenger creates a transaction , using the input values through the oracle as given in step 13. Based on the entity/entities being tested as defined by , a second transaction is also created as appropriate (line 14). If the transactions are not mintable and the parameter (i.e., failed mint operations are not allowed), then the game is terminated and the adversary loses the game. We use the notation “” to represent this condition. In this case, when , , and the game continues if . When , , and thus always and hence the game proceeds.
Subsequently, the challenger picks a bit b and chooses to mint together with the list of transactions T returned by the adversary (line 15). Next, the challenger calls the function to prepare the information that needs to be revealed to the adversary based on , and this information is then passed to the adversary. At this point, the adversary is not allowed to create any further transactions involving the revealed addresses. Then, he/she makes a guess () for the bit b, based on the revealed data U, minted state , and the adversarial state s. The challenger checks whether the guess is correct, subject to the condition . The adversary wins the game if his/her guess is correct.
Unsurprisingly, there are over 600,000 different combinations of , , , and alone, resulting in different attacker scenarios, which reveal the atomicity of anonymity in a currency system. This game helps one to assess which combinations are satisfied by a given currency scheme, by proving that the attacker has negligible advantage of winning the game. In order to simplify this task, in the next section, we come up with a set of anonymity notions which can be linked to the terminology discussed in the literature.
5.2. Notions of Anonymity
As previously mentioned, different combinations of the parameters in the Anonymity Game yields a large number of unique scenarios with respect to anonymity. While some notions may not result in apprehensible real-world scenarios, others may assist in assessing different levels in achievable anonymity. In this section, we identify a set of some useful anonymity notions with respect to indistinguishability (IND) and unlinkability (ULK) of entities, senders (S), recipients (R), value (V), and metadata (M) in a currency scheme.
We define each notion in terms of a unique adversary, based on the adversary’s goal, knowledge and power as GOAL-KNOWL-POWER, which is also represented as a unique parameter vector
−
−
. The strongest adversary is modeled with the highest power (to manipulate the state initialization and the state, and to make minting to fail) and the maximum knowledge (full knowledge of secret keys of senders/recipients, values, and metadata), which we name as a FULL-FULL adversary. The weakest adversary has no power and no knowledge of transaction data, hence we name as a NIL-NIL adversary. Other intermediate adversaries are named accordingly to emphasize the capabilities in power and knowledge specific to a given setting. Therefore, the highest level of anonymity modeled by the game is the notion ALL-IND-FULL-FULL and the weakest is the notion of NIL-IND-NIL-NIL. Accordingly,
Table 7 lists some useful anonymity notions and their corresponding parameter vectors.
5.2.1. Topological Entities
As already mentioned, the identification of topological entities such as senders and recipients participating in a transaction can directly contribute towards constructing the corresponding relationships among those entities. As a result, one can trace the flow of transactions of a particular entity, affecting the level of anonymity. Several studies have been conducted in this regard, especially in the case of Bitcoin, where a transaction graph could be built using publicly available data related to senders and recipients [
20]. As such, topological entities play a vital role in the achievable level of anonymity of a currency scheme. Therein, we define a set of useful anonymity properties around these entities in this section (
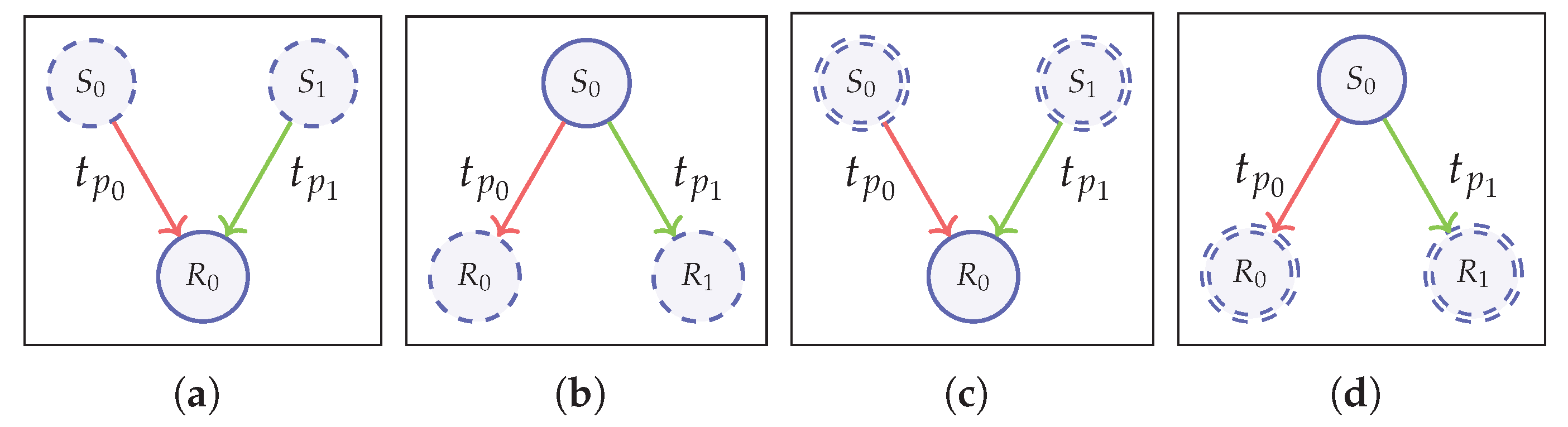
Figure 6).
Sender Indistinguishability (S-IND)
We define this property to represent a case where given two possible senders and a transaction, it is not possible to distinguish the correct sender.
Figure 6a illustrates this scenario. In the anonymity game, only the public keys of the senders will be known to the adversary with
and
(PUBS knowledge) with same transaction values and other metadata, and the challenger will create two transactions
and
with same value and metadata if
(otherwise, the adversary provides the transactions). Based on the chosen bit
b, the challenger mints the transaction
and the adversary gets to see the data related to the minted transaction, based on
, and has to guess the challenger’s choice. The knowledge of recipient addresses can vary based on
and
.
We can see that the game represents the strongest attacker scenario when the recipient addresses are fully controlled by the adversary in a setting with an adversarial hidden state initialization and the ability to manipulate the state, as well as with the highest knowledge of the transaction (i.e., ). However, having = 1 enables the adversary to craft messages in a manner so that failed mint operations can be used to learn about account balances, etc., thus revealing the transaction graph, which will be trivial and thus we consider an adversary with ACTIVE power (i.e., ). Accordingly, the strongest notion of this property is S-IND-PUBS-ACTIVE, which is represented by “ − − ()” in the Anonymity game with the following formal definition.
Definition 4 (S-IND-PUBS-ACTIVE). A currency scheme Π
is said to satisfy the anonymity notion S-IND-PUBS-ACTIVE with respect to Sender Indistinguishability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameter vector − − () is negligible, i.e., Sender Unlinkability (S-ULK)
The notion of sender unlinkability is defined to be the property that it is not possible to link a transaction with its corresponding sender in a given setting. As
Figure 6c illustrates, the adversary has to guess the correct transaction as with S-IND scenario, but without knowing both public/private keys of the senders, i.e., Senders in this case are hidden with
. The strongest notion in this sense is given by S-ULK-NILS-ACTIVE with the parameter vector “
−
− (
)” and the corresponding formal definition is as follows.
Definition 5 (S-ULK-NILS-ACTIVE). A currency scheme Π
is said to satisfy the anonymity notion S-ULK-NILS-ACTIVE with respect to Sender Unlinkability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − , − () is negligible, i.e., Recipient Indistinguishability (R-IND)
This notion is similar to sender indistinguishability, except with recipient addresses. Therefore, it is defined to be one’s inability to distinguish the correct recipient out of two given recipients in a given situation. As shown in the
Figure 6b, public keys of the recipients (
) are known and the senders could be hidden or known as per the parameters
and
. The two transactions
and
both carry the same sender, values, and metadata, yet have two different recipients. The adversary needs to guess which transaction out of
and
was minted. The strongest adversarial scenario in this case is R-IND-PUBR-ACTIVE, denoted as “
−
− (
)”. We define the notion formally as below.
Definition 6 (R-IND-PUBR-ACTIVE). A currency scheme Π
is said to satisfy the anonymity notion R-IND-PUBR-ACTIVE with respect to Recipient Indistinguishability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − − () is negligible, i.e., Recipient Unlinkability (R-ULK)
This property is referred to as the inability to link a transaction to the correct recipient.
Figure 6d shows the basic setup for this game where the adversary needs to guess the correct transaction out of the two options
and
, without any knowledge about the corresponding recipients, i.e.,
,
. The strongest notion in this setting is represented as R-ULK-NILR-ACTIVE given by the vector “
−
− (
)” and the formal definition is given below.
Definition 7 (R-ULK-NILR-ACTIVE). A currency scheme Π
is said to satisfy the anonymity notion R-ULK-NILR-ACTIVE with respect to Recipient Unlinkability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − , − () is negligible. 5.2.2. Non-Topological Entities
As opposed to topological entities, non-topological entities such as value and metadata in a currency scheme do not directly affect the structure of the transaction graph. However, if made public, these entities could also hinder the privacy of users. Therefore, these entities can also be regarded as equally important in determining the level of anonymity in a currency scheme. In this section, we provide formal definitions for major anonymity notions involving non-topological entities: value and metadata (
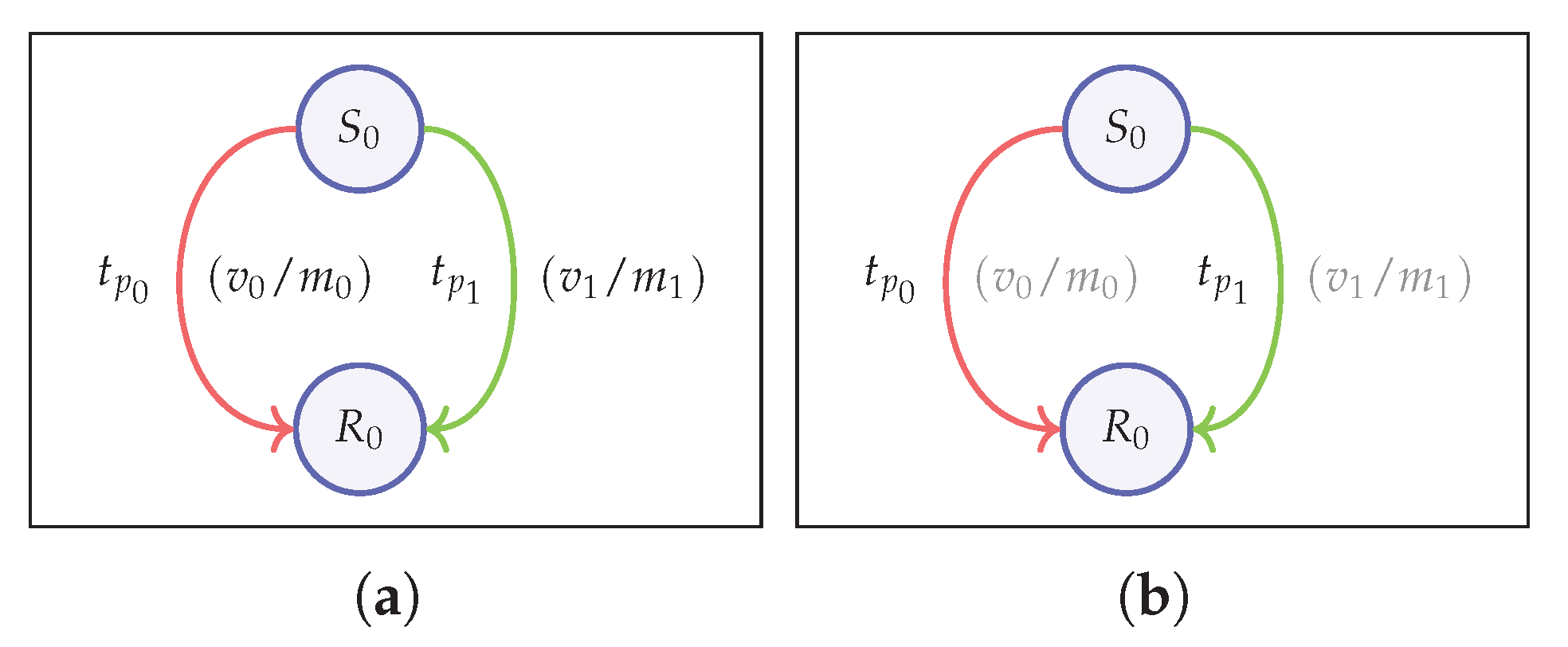
Figure 7).
Value Indistinguishability (V-IND)
The notion of indistinguishability with respect to transaction values refers to the fact that it is impossible to distinguish the correct value from two given values for a given transaction. In the game, the challenger creates two transactions,
and
, with two different values,
and
, while having other entities the same (
Figure 7a). In this case, the adversary knows what the two values are and other entities can vary according to their
values. The challenger then picks a bit
b and mints the transaction
and the adversary has to guess which transaction it is. We represent the strongest adversary as PUBSR-ACTIVE as the knowledge of secret keys would leak information about the value. Therefore, the strongest notion in this scenario is given by V-IND-PUBSR-ACTIVE, which is represented by the vector “
−
− (
)” with the following formal definition.
Definition 8 (V-IND-PUBSR-ACTIVE). A currency scheme Π
is said to satisfy V-IND-PUBSR-ACTIVE with respect to Value Indistinguishability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − , − () is negligible, i.e., Value Unlinkability (V-ULK)
We define the property of unlinkability related to transaction value as the inability to correctly identify value of the minted transaction from two possible hidden values. In order to realize this scenario, failed minting operations have to be allowed in the game with the parameter
set to 1, as it would be impossible for the adversary to win the game otherwise. As
, the adversary gives maximum values for
and
values from which the challenger generates corresponding values required for the transaction using the
helper function (
Figure 3). Further, as in the case of V-IND, we restrict the knowledge of secret keys of senders/recipients as otherwise the transaction is trivial. As shown in
Figure 7b, in this context the challenger creates two transactions
and
with hidden transaction values
and
, respectively. The challenger then picks a bit
b and mints the transaction
and the adversary makes a guess to identify the correct scenario. Accordingly, we have “
−
− (
” as the combination of parameters required to achieve the strongest level of anonymity notion V-ULK-PUBSR-NILV-FULL in this sense and the corresponding definition is as follows.
Definition 9 (V-ULK-PUBSR-NILV-FULL). A currency scheme Π
is said to satisfy the anonymity notion V-ULK-PUBSR-NILV-FULL with respect to Value Unlinkability against an adversary under a hidden adversarial initialisation, if ’s advantage of winning the Anonymity game defined by the parameters − − () is negligible, i.e., 5.2.3. Other Useful Anonymity Notions
Further to above notions, we also formally define the strongest and weakest anonymity notions modeled in this framework as they are useful in benchmarking the anonymity landscape.
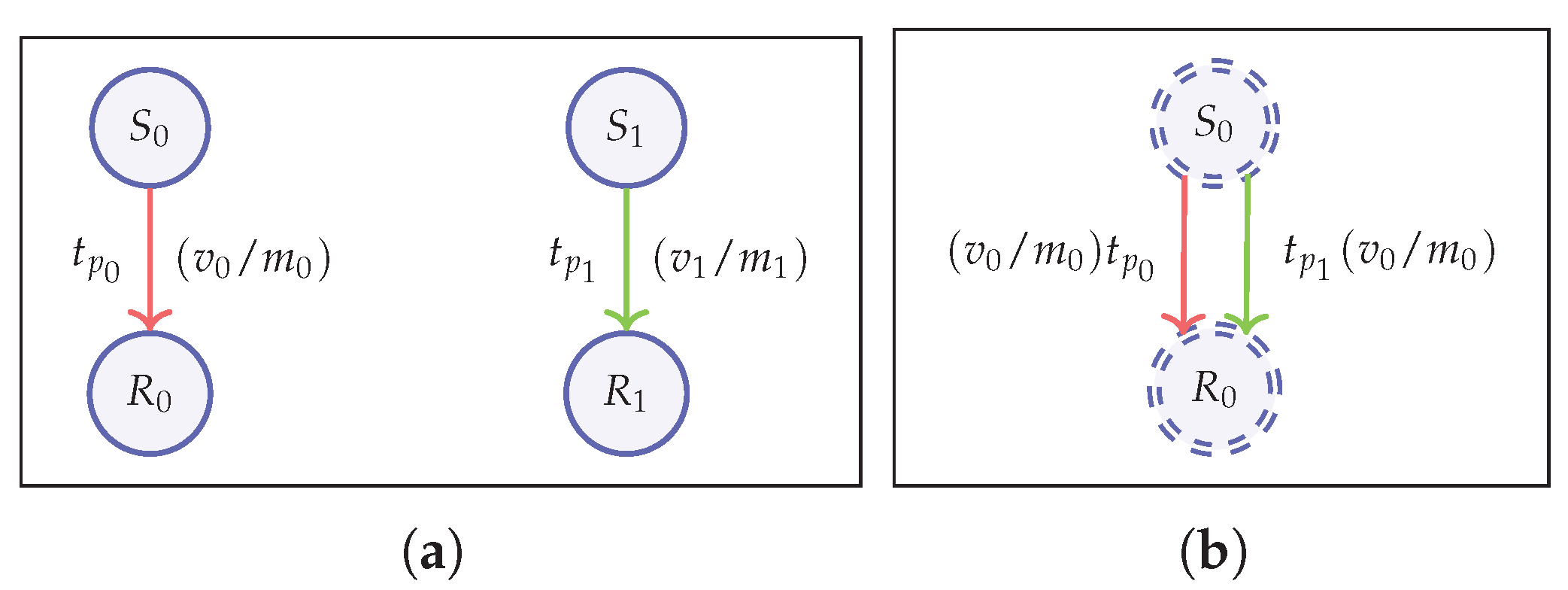
Strongest Anonymity (ALL-IND)
In this setting, the game models two senders and two recipients. The challenger creates two transactions
and
as before, but each transaction is created using distinct set of data, i.e., different sender, recipient, value, and metadata (
Figure 8a). The strongest adversary in this scenario has the FULL knowledge and FULL power given by ALL-IND-FULL-FULL notion and parameterized by the vector
−
,
− (
). This setting models the highest level of anonymity achievable by a currency scheme and can be considered as “absolute fungibility”. We provide the following formal definition in this connection.
Definition 12 (ALL-IND-FULL-FULL). A currency scheme Π
is said to satisfy the anonymity notion ALL-IND-FULL-FULL with respect to indistinguishability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − , − () is negligible, i.e., Weakest Anonymity (NIL-IND)
Here, we consider the weakest adversary that can be modeled in our game. In this case, the game produces two identical transactions as opposed to the strongest scenario above (
Figure 8b). These transactions differ only in their randomness and the adversary has to identify the correct transaction. Therefore, the weakest adversary in this case is a NIL-NIL adversary with no knowledge nor power, which is a passive adversary. This means that even
= 0, meaning that the scheme has a hidden private state, which however may not be the case for most cryptocurrency schemes. Yet, we provide the following formalization for comparison.
Definition 13 (NIL-IND-NIL-NIL). A currency scheme Π
is said to satisfy the anonymity notion NIL-IND-NIL-NIL with respect to indistinguishability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − , − () is negligible, i.e., As many cryptocurrency schemes have public states, we can see that at the very least, the adversary can view the state, meaning that we can set = 1 in our model for most schemes. This will model an adversary with VIEW power with other parameters being zero. Therefore, we define a slightly less weaker notion in this sense, which can be useful to model anonymity in some real world constructions.
Definition 14 (NIL-IND-NIL-VIEW). A currency scheme Π
is said to satisfy the anonymity notion NIL-IND-NIL-VIEW with respect to indistinguishability against an adversary , if ’s advantage of winning the Anonymity game defined by the parameters − , − () is negligible, i.e., 5.2.4. Representation of Anonymity Notions
In order to clearly represent above anonymity notions, we construct graphical illustrations as shown in
Figure 9 and
Figure 10. These diagrams are useful in comparing anonymity landscape across different implementations while illustrating the complex multidimensional diversity of adversarial parameters.
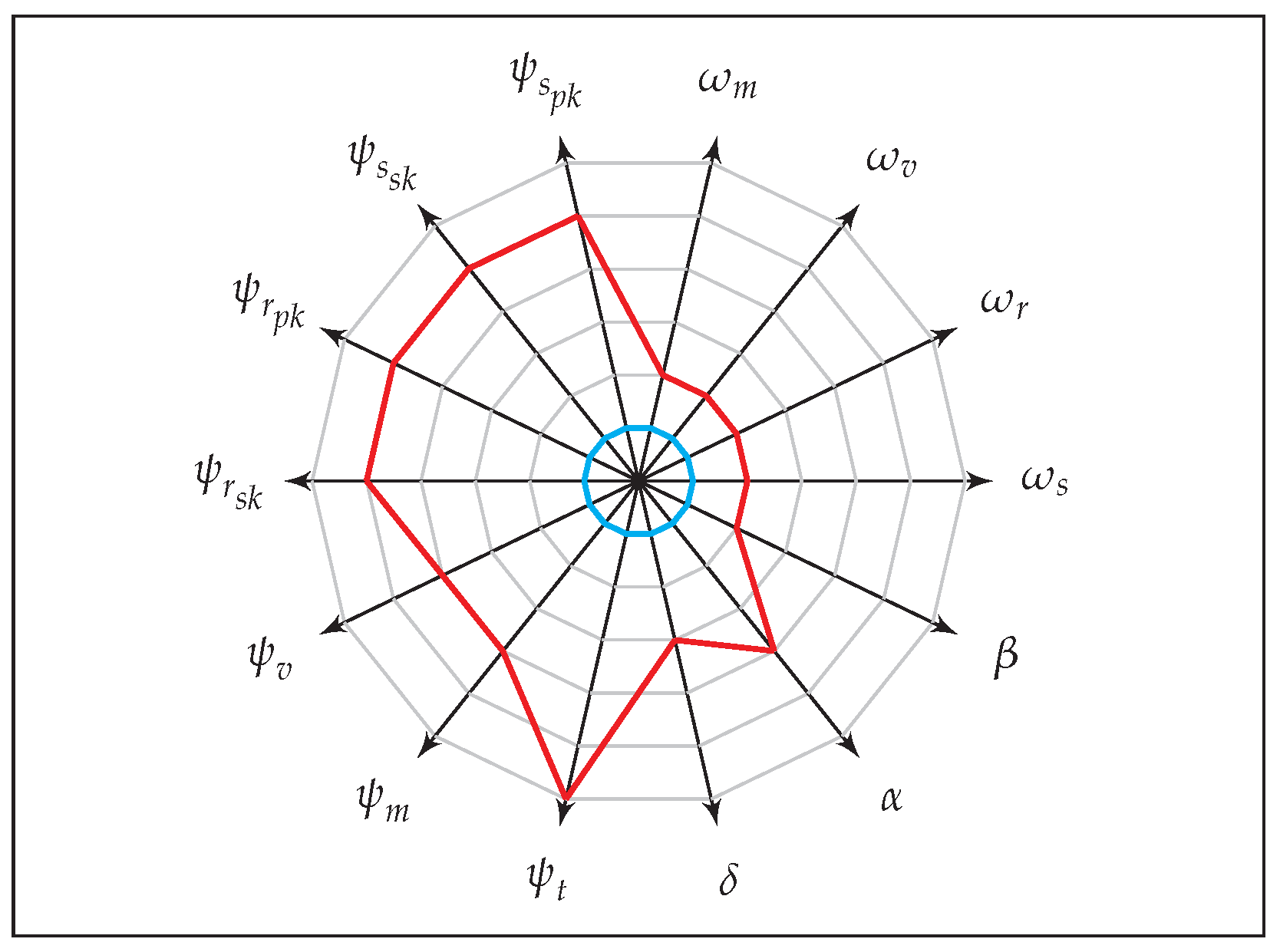
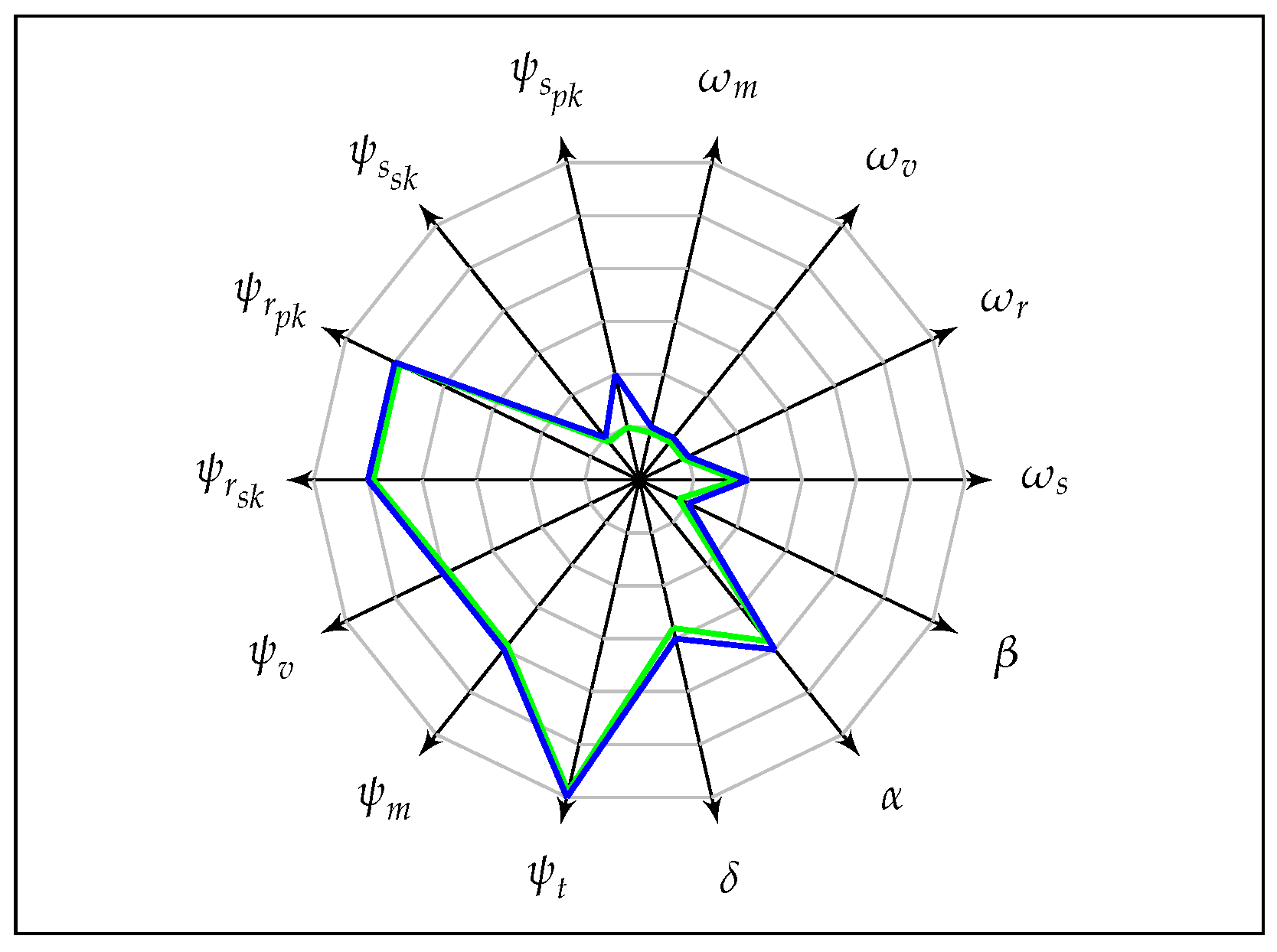
Figure 9 represents a comparison between the strongest anonymity notion ALL-IND-FULL-FULL against the weakest notion NIL-IND-NIL-NIL in our anonymity game. All other notions lay within the area bounded by these two notions. The larger the area covered by the graph of a given notion, the stronger is the level of anonymity. This is evident from the
Figure 10, which represents two more anonymity notions related to S-IND and S-ULK corresponding to Definitions 4 and 5, and shows that S-IND is stronger than S-ULK.
5.3. Theorems
As is apparent from the definitions presented in the previous section, we can utilize the Anonymity game to realize a multitude of potential different attacker scenarios. Identifying the relationships among these is a worthwhile exercise in order to discern the meaningful aspects of anonymity captured by them.
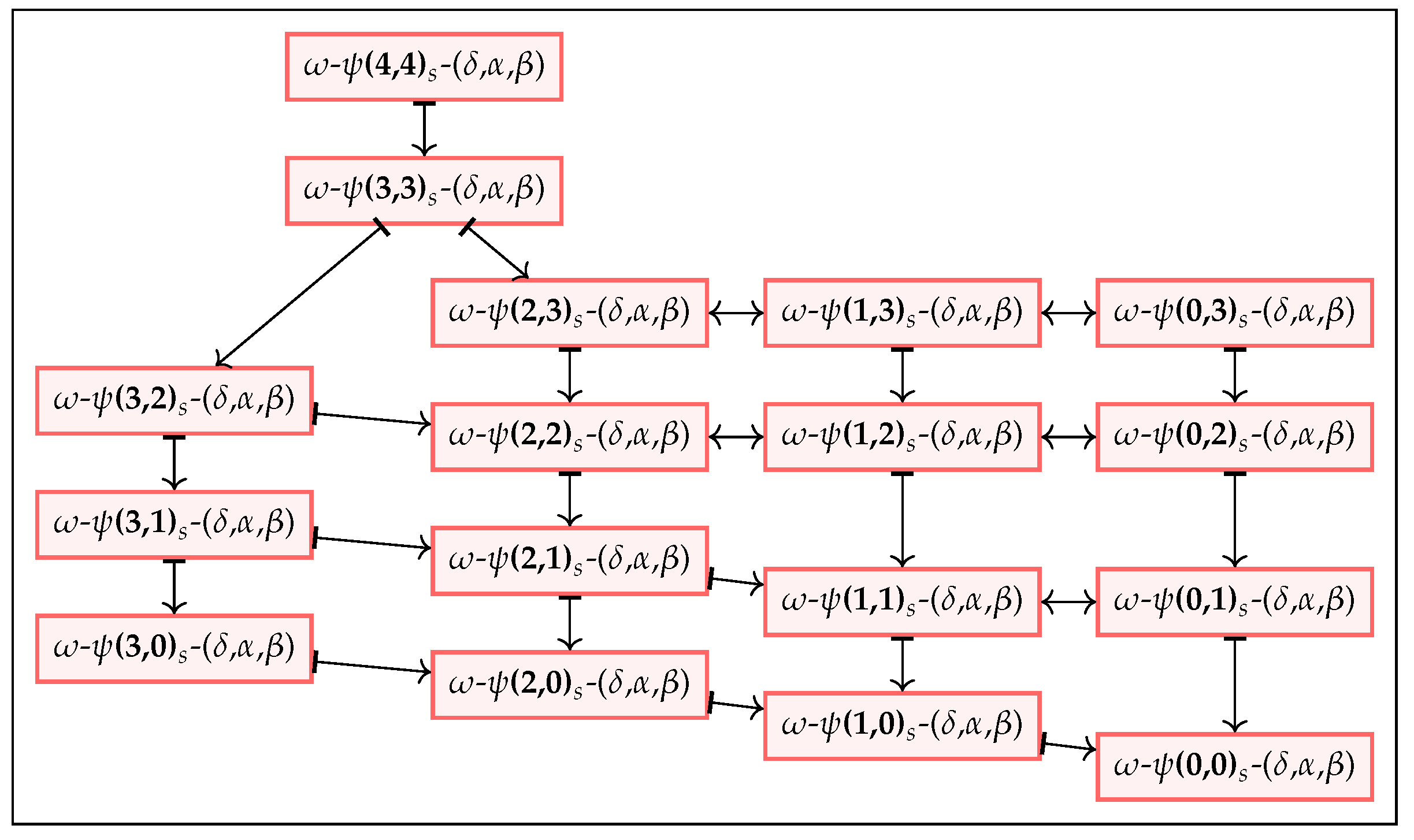
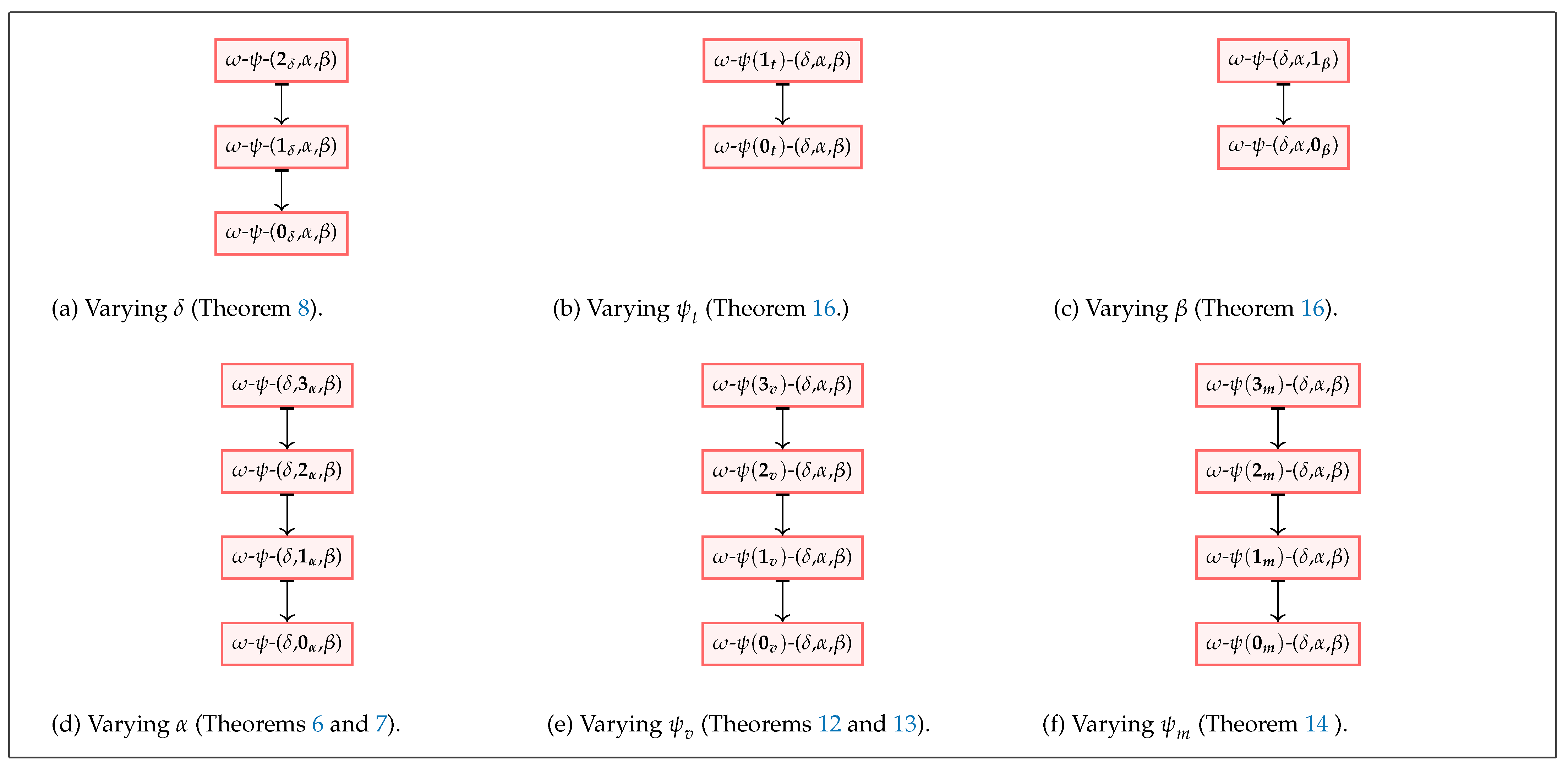
Note that as we vary different security parameters in our model, their correlations result in a non-trivial lattice form as depicted in
Figure 11 and
Figure 12. These relations are interpreted as implications, equivalences, and separations. The arrow “↦” represents an implication in the direction of the arrow and a separation in the opposite direction, whereas the double arrow “↔” shows an equivalence relation. In order to formalize these relationships, we define a set of theorems that will simplify the process of assessing the anonymity of a currency scheme and we present the same below. Relevant proofs of these theorems are available in
Appendix C.
Theorem 1. For a currency scheme Π and for a given combination of ω, δ, α, , , , , , and β, the notion resulting from increasing the value of while holding others is strictly stronger than the former for the following scenarios.
- i.
given that Π is secure in , Π is also secure in , and ,
i.e.,
- ii.
given that Π is secure in , Π is also secure in and ,
i.e.,
- iii.
given that Π is secure in , Π is also secure in ,
i.e.,
- iv.
given that Π is secure in , Π is also secure in ,
i.e.,
- v.
given that Π is secure in , Π is also secure in ,
i.e.,
where , and (Figure 11). Theorem 2. For a currency scheme Π and for a given combination of ω, δ, α, , , , , , and β, the notion resulting from increasing the value of while holding others is strictly stronger than the former for the following scenarios:
- i.
given that Π is secure in , Π is also secure in , and ,
i.e.,
- ii.
given that Π is secure in , Π is also secure in and ,
i.e.,
- iii.
given that Π is secure in , Π is also secure in , and ,
i.e.,
- iv.
given that Π is secure in , Π is also secure in , and ,
i.e.,
where , and (Figure 11). Theorem 3. For a currency scheme Π and for a given combination of ω, δ, α, , , , , and β, the resulting notion from increasing the value of while holding others fixed, is equivalent to the former when under the following scenarios:
- i.
given that Π is secure in , then Π is also secure in , and vice versa.,
i.e.,
- ii.
given that Π is secure in , then Π is also secure in and , and vice versa,
i.e.,
- iii.
given that Π is secure in , then Π is also secure in and , and vice versa,
i.e.,
where , and (Figure 11). Theorem 4. For a currency scheme Π for a given combination of ω, δ, α, , , , , and β (with ), the notion resulting from decreasing the value of while holding others is not necessarily stronger than the former for the following scenarios:
- i.
- ii.
- iii.
- iv.
- v.
where , , and (Figure 11). Theorem 5. For a currency scheme Π for a given combination of ω, δ, α, , , , , and β (with ), the notion resulting from decreasing the value of while holding others is not necessarily stronger than the former for the following scenarios:
- i.
- ii.
- iii.
where , , and (Figure 11). Note that the Theorems 1–4 also hold for recipient addresses in the same manner.
Theorem 6. For a currency scheme Π and for a given combination of ω, δ, ψ, and β, if α is decreased while holding the others, the former notion is strictly stronger than the resulting notion for the following scenarios:
- i.
given Π is secure in , then Π is also secure in ,
i.e.,
- ii.
given Π is secure in , then Π is also secure in ,
i.e.,
- iii.
given Π is secure in , then Π is also secure in ,
i.e.,
where , and (Figure 12d). Theorem 7. For a currency scheme Π and for a given combination of ω, δ, ψ, and β (with ), if α is increased while holding the others, the system is necessarily secure in the resulting notion for the following scenarios:
- i.
Given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- ii.
Given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- iii.
Given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
where , and (Figure 12d). Theorem 8. For a currency scheme Π and for a given combination of ω, α, ψ, and β, if δ is decreased while holding the others, the former notion is strictly stronger than the resulting notion for the following scenarios:
- i.
given Π is secure in then Π is also secure in ,
i.e.,
- ii.
given Π is secure in then Π is also secure in ,
i.e.,
where , and (Figure 12a). Theorem 9. For a currency scheme Π and for a given combination of ω, α, ψ, and β (with ), if δ is increased while holding the others, the resulting notion is not necessarily stronger than the former notion for the following scenarios:
- i.
given that two currency schemes and exists such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- ii.
given that two currency schemes and exists such that is secure in and is not secure in , there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
where , and (Figure 12a). Theorem 10. For a currency scheme Π and for a given combination of ω, α, and ψ, if β is decreased while holding the others, the former notion is strictly stronger than the resulting notion for the following scenarios:
- i.
given Π is secure in then Π is also secure in ,
i.e.,
where , , and (Figure 12a). Theorem 11. For a currency scheme Π and for a given combination of ω, α, and ψ, if β is decreased while holding the others, the former notion is strictly stronger than the resulting notion for the following scenarios:
- i.
given that Π is secure in then Π is not necessarily secure in ,
i.e.,
where , , and (Figure 12a). Theorem 12. For a currency scheme Π and for a given combination of ω, δ, α, , , , and β, when the value of is decreased while holding others fixed, the former notion is strictly stronger than the resulting notion under the following scenarios:
- i.
given Π is secure in , then Π is also secure in ,
i.e., →
- ii.
given Π is secure in , then Π is also secure in ,
i.e., →
- iii.
given Π is secure in , then Π is also secure in ,
i.e., →
where , and (Figure 12e). Theorem 13. For a currency scheme Π and for a given combination of ω, δ, α, , , , and β (with ), the resulting notion from increasing the value of while holding others fixed, the scheme is not necessarily secure in the resulting notion under the following scenarios:
- i.
given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- ii.
given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- iii.
given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
where , , and (Figure 12e). Theorem 14. For a currency scheme Π and for a given combination of ω, δ, α, , , , and β, when the value of is decreased while holding others fixed, the former notion is strictly stronger than the resulting notion under the following scenarios:
- i.
given Π is secure in , then Π is also secure in ,
i.e.,
- ii.
given Π is secure in , then Π is also secure in ,
i.e.,
- iii.
given Π is secure in , then Π is also secure in ,
i.e.,
where , and (Figure 12f). Theorem 15. For a currency scheme Π and for a given combination of ω, δ, α, , , , and β (with ), the resulting notion from increasing the value of while holding others fixed, the scheme is not necessarily secure in the resulting notion under the following scenarios:
- i.
given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- ii.
given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
- iii.
given that two currency schemes and exist such that is secure in and is not secure in , then there exists a currency scheme Π which is secure in but not secure in ,
i.e.,
where , , and (Figure 12f). Theorem 16. For a currency scheme Π and for a given combination of ω, δ, α, , , , and β, when the value of is decreased while holding others fixed, the former notion is strictly stronger than the resulting notion under the following scenarios:
- i.
given Π is secure in , then Π is also secure in ,
i.e.,
- ii.
given Π is secure in , then Π is also secure in ,
i.e.,
- iii.
given Π is secure in , then Π is also secure in ,
i.e.,
- iv.
given Π is secure in , then Π is also secure in ,
i.e.,
- v.
given Π is secure in , then Π is also secure in ,
i.e.,
where , , and (Figure 12b). Theorem 17. For a currency scheme Π and for a given combination of ω, δ, α, , , , and β the resulting notion from increasing the value of while holding others fixed, the scheme is not necessarily secure in the resulting notion under the following scenarios:
- i.
Given that there exists a currency scheme which is secure in , it does not necessarily imply that is secure in ,
i.e., is secure in .
- ii.
Given that there exists a currency scheme which is secure in , it does not necessarily imply that is secure in ,
i.e., is secure in .
- iii.
Given that there exists a currency scheme which is secure in , it does not necessarily imply that is secure in ,
i.e., is secure in .
- iv.
Given that there exists a currency scheme which is secure in , it does not necessarily imply that is secure in ,
i.e., is secure in
- v.
Given that there exists a currency scheme which is secure in , it does not necessarily imply that is secure in ,
i.e., is secure in
where , , , and (Figure 12c). Note that in some cases, the separations are not known to hold for all values of the unspecified parameters. Based on the above theorems, we also define the following corollaries.
Corollary 1 (Absolute Fungibility (ALL-IND-FULL-FULL)).Given that a currency scheme Π
is secure in the strongest anonymity notion (i.e., secure against the strongest possible adversary), then Π
is also secure in any other notion (any other adversary), i.e., where , and (Figure 11). Proof. (sketch) This follows from the above theorems as illustrated in
Figure 11 and
Figure 12 as this notion is the strongest among all. □
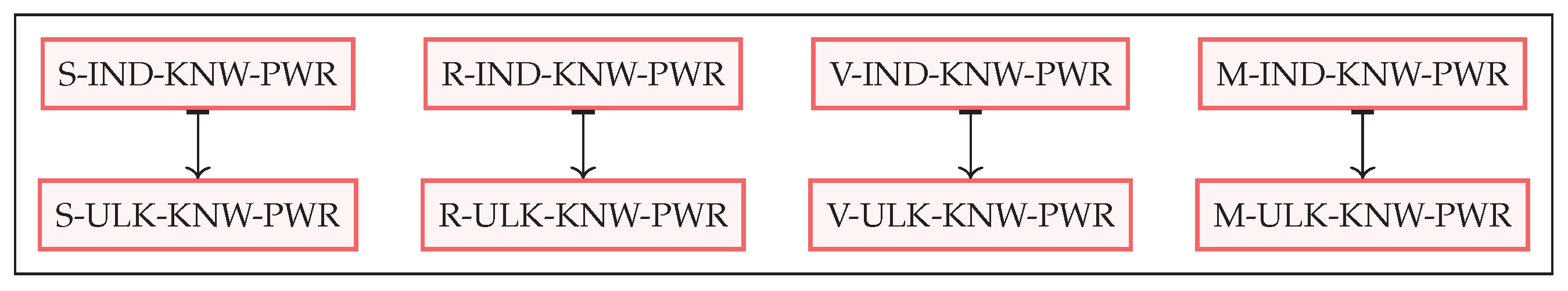
Corollary 2 (IND → ULK).For a currency scheme Π,
- i.
given Π is secure in S-IND-KNW-PWR for a given adversarial knowledge KNW of recipients, value and metadata, and given adversarial power PWR, then Π is also secure in S-ULK-KNW-PWR,
i.e., S-IND-KNW-PWR → S-ULK-KNW-PWR;
- ii.
given Π is secure in R-IND-KNW-PWR for a given adversarial knowledge KNW of senders, value and metadata, and given adversarial power PWR, then Π is also secure in R-ULK-KNW-PWR,
i.e., R-IND-KNW-PWR → R-ULK-KNW-PWR;
- iii.
given Π is secure in V-IND-KNW-PWR for a given adversarial knowledge KNW of senders, recipients and metadata, and given adversarial power PWR, then Π is also secure in V-ULK-KNW-PWR,
i.e., V-IND-KNW-PWR → V-ULK-KNW-PWR; and
- iv.
given Π is secure in M-IND-KNW-PWR for a given adversarial knowledge KNW of senders, recipients and value, and given adversarial power PWR, then Π is also secure in M-ULK-KNW-PWR,
i.e., M-IND-KNW-PWR → M-ULK-KNW-PWR
Proof. (sketch) (Part i) From the definitions of S-IND (Definition 4) and S-ULK (Definition 5), the difference between the two notions is that
in S-IND and it is
in S-ULK. Then, from Theorem 1, it follows that
and hence the implication follows (
Figure 13).
(Part ii) Similarly, it follows from Theorem 1 with respect to recipients.
(Part iii) Follows from Theorem 12.
(Part iv) Follows from Theorem 14. □
Conversely, the weakest adversary is represented by the notion NIL-IND-NIL-NIL represented by the vector − − with all entities hidden (Definition 13). Note that this notion is trivial in that no adversary can ever win the corresponding game as the transactions and are, aside from randomness, identical.