On General Data Protection Regulation Vulnerabilities and Privacy Issues, for Wearable Devices and Fitness Tracking Applications
Abstract
:1. Introduction
- Purpose limitation;
- Data minimization;
- Accuracy;
- Storage limitation;
- Integrity and confidentiality;
- Accountability.
- Is data privacy and security established for the popular wearable devices in the new, GDPR, era?
- What are the privacy risks that users may encounter using fitness tracking applications, smart devices, and wearable technology?
2. Personal Data and Privacy in the GDPR Era
- The concept of processing;
- The concept of storing; and
- The concept of purpose.
3. The New Era of Wearable Internet of Things
3.1. Sensors
3.2. Cloud Based IoΤ, Data Privacy and Encryption
4. Security and Privacy Vulnerability Issues in Fitness Tracking Devices
5. Proposed Work: Experimental Environment and Analysis
5.1. Experimental Environment
5.2. Experimental Results and Analysis
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| Abbreviation | Full Form | Definition |
| 9DoF | 9 Degrees of Freedom | The process of capturing nine different types of orientation or motion related data. |
| GDPR | General Data Protection Regulation | The European legal framework setting guidelines for the collection and processing of personal information from individuals. |
| IoT | Internet of Things | A system of interrelated, internet-connected objects, able to collect and transfer data over a wireless network. |
| MEMS | Micro Electrical and Mechanical System | Miniaturized devices and structures that are made using the techniques of microfabrication. |
| MITM attack | Man-in-the-Middle Attack | Active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them. |
| OS | Operating System | System software managing hardware and software resources, and providing common services for applications. |
| TLS | Transport Layer Security | A security protocol providing privacy and data integrity for Internet communications. |
| UUID | Universally Unique Identifier | A 128-bit label used for information in computer systems. |
| WIoT | Wearable Internet of Things | A sub-category of IoT electronic devices that can be embedded in clothing worn as accessories. |
References
- Hadzovic, S.; Mrdovic, S.; Radonjic, M. Identification of IoT Actors. Sensors 2021, 21, 2093. [Google Scholar] [CrossRef]
- Lee, J.; Kim, D.; Ryoo, H.-Y.; Shin, B.-S. Sustainable Wearables: Wearable Technology for Enhancing the Quality of Human Life. Sustainability 2016, 8, 466. [Google Scholar] [CrossRef] [Green Version]
- Yang, H.; Kumara, S.; Bukkapatnam, S.T.; Tsung, F. The internet of things for smart manufacturing: A review. IISE Trans. 2019, 51, 1190–1216. [Google Scholar] [CrossRef]
- Hayward, J.; Chansin, J.; Zervos, H. Wearable Technology 2018–2028: Markets, Players, Forecasts. Available online: http://www.idtechex.com/research/reports/wearabletechnology-2017-2027-markets-players-forecasts-000536.asp (accessed on 26 June 2021).
- Kaewkannate, K.; Kim, S. A comparison of wearable fitness devices. BMC Public Health 2016, 16, 433. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Muñiz, R.; Díaz, J.; Martínez, J.; Nuño, F.; Bobes, J.; García-Portilla, M.; Sáiz, P. A Smart Band for Automatic Supervision of Restrained Patients in a Hospital Environment. Sensors 2020, 20, 5211. [Google Scholar] [CrossRef] [PubMed]
- Fereidooni, H.; Frassetto, T.; Miettinen, M.; Sadeghi, A.-R.; Conti, M. Fitness Trackers: Fit for Health but Unfit for Security and Privacy. In Proceedings of the 2017 IEEE/ACM International Conference on Connected Health: Applications, Systems and Engineering Technologies (CHASE), Philadelphia, PA, USA, 17–19 July 2017; pp. 19–24. [Google Scholar] [CrossRef]
- Clausing, E.; Schiefer, M. Internet of Things Security Evaluation of 7 Fitness Trackers on Android and the Apple Watch; AV-TEST—The Independent IT-Security Institute: Magdeburg, Germany, 2016. [Google Scholar]
- Zhang, Q.; Liang, Z. Security analysis of bluetooth low energy based smart wristbands. In Proceedings of the 2017 2nd International Conference on Frontiers of Sensors Technologies (ICFST), Shenzhen, China, 14–16 April 2017. [Google Scholar] [CrossRef]
- Cusack, B.; Bryce, A.; Ward, G.; Mod, S. Assessment of security vulnerabilities in wearable devices. In Proceedings of the 15th Australian Information Security Management Conference, Perth, WA, Australia, 5–6 December 2017. [Google Scholar]
- Langone, M.; Setola, R.; Lopez, J. Cybersecurity of Wearable Devices: An Experimental Analysis and a Vulnerability Assessment Method. In Proceedings of the 2017 IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), Turin, Italy, 4–8 July 2017. [Google Scholar]
- Shiaeles, S.; Kolokotronis, N.; Bellini, E. IoT Vulnerability Data Crawling and Analysis. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019. [Google Scholar]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and Security: Challenges and Solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Warren, S.; Brandeis, L. The Right to Privacy. Available online: https://groups.csail.mit.edu/mac/classes/6.805/articles/privacy/Privacy_brand_warr2.html (accessed on 26 June 2021).
- Li, H.; Sun, G.; Li, Y.; Yang, R. Wearable Wireless Physiological Monitoring System Based on Multi-Sensor. Electronics 2021, 10, 986. [Google Scholar] [CrossRef]
- Kalapodi, A.; Sklavos, N. The Concerns of Personal Data Privacy, on Calling and Messaging, Networking Applications. In Communications in Computer and Information Science; Springer: Singapore, 2021; pp. 275–289. [Google Scholar] [CrossRef]
- Gadaleta, M.; Rossi, M. IDNet: Smartphone-based gait recognition with convolutional neural networks. Pattern Recognit. 2018, 74, 25–37. [Google Scholar] [CrossRef] [Green Version]
- Hasan, O.; Habegger, B.; Brunie, L.; Bennani, N.; Damiani, E. A Discussion of Privacy Challenges in User Profiling with Big Data Techniques: The EEXCESS Use Case. In Proceedings of the IEEE International Congress on Big Data 2013, Santa Clara, CA, USA, 27 June–2 July 2013; pp. 25–30. [Google Scholar] [CrossRef] [Green Version]
- Starner, T. The challenges of wearable computing: Part 1. IEEE Micro 2001, 21, 44–52. [Google Scholar] [CrossRef] [Green Version]
- Mnjama, J.; Foster, G.; Irwin, B. A privacy and security threat assessment framework for consumer health wearables. In Proceedings of the 2017 Information Security for South Africa (ISSA), Johannesburg, South Africa, 16–17 August 2017; pp. 66–73. [Google Scholar] [CrossRef]
- Goyal, R.; Dragoni, N.; Spognardi, A. Mind the tracker you wear. In Proceedings of the 31st Annual ACM Symposium on Applied Computing, Pisa, Italy, 4–8 April 2016. [Google Scholar] [CrossRef]
- Braghin, C.; Cimato, S.; Della Libera, A. Are mHealth Apps Secure? A Case Study. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018. [Google Scholar] [CrossRef]
- Barcena, M.; Wueest, C.; Lay, H. How Safe Is Your Quantified Self? 2014. Available online: https://www.symantec.com/content/dam/symantec/docs/white-papers/how-safe-is-your-quantified-self-en.pdf (accessed on 27 August 2021).
- Viel, F.; Silva, L.A.; Valderi Leithardt, R.Q.; Zeferino, C.A. Internet of Things: Concepts, Architectures and Technologies. In Proceedings of the 2018 13th IEEE International Conference on Industry Applications (INDUSCON), Sao Paulo, Brazil, 12–14 November 2018. [Google Scholar] [CrossRef]
- Garrity, J. Harnessing the Internet of Things for Global Development. SSRN Electron. J. 2015. [Google Scholar] [CrossRef]
- Huh, J.-H. Implementation of lightweight intrusion detection model for security of smart green house and vertical farm. Int. J. Distrib. Sens. Netw. 2018, 14, 155014771876763. [Google Scholar] [CrossRef] [Green Version]
- Ioannidou, I. Revolutionizing Sports Science through Information Technology: IoT, Augmented and Virtual Reality Applications. In Proceedings of the 1st International Interdisciplinary Conference on the Theme of “Sports and Art”: Scientific and Artistic Dialogue, Ioannina, Greece, 5–7 April 2019. [Google Scholar] [CrossRef]
- Ullah, F.; Haq, H.U.; Khan, J.; Safeer, A.A.; Asif, U.; Lee, S. Wearable IoTs and Geo-Fencing Based Framework for COVID-19 Remote Patient Health Monitoring and Quarantine Management to Control the Pandemic. Electronics 2021, 10, 2035. [Google Scholar] [CrossRef]
- Rahman, A.; Asyhari, A.T. The Emergence of Internet of Things (IoT): Connecting Anything, Anywhere. Computers 2019, 8, 40. [Google Scholar] [CrossRef] [Green Version]
- Rybarczyk, D. Application of the MEMS Accelerometer as the Position Sensor in Linear Electrohydraulic Drive. Sensors 2021, 21, 1479. [Google Scholar] [CrossRef]
- Asimakopoulos, S.; Asimakopoulos, G.; Spillers, F. Motivation and User Engagement in Fitness Tracking: Heuristics for Mobile Healthcare Wearables. Informatics 2017, 4, 5. [Google Scholar] [CrossRef] [Green Version]
- Becerra, V.; Perales, F.J.; Roca, M.; Buades, J.M.; Miró-Julià, M. A Wireless Hand Grip Device for Motion and Force Analysis. Appl. Sci. 2021, 11, 6036. [Google Scholar] [CrossRef]
- Lima, W.S.; Souto, E.; El-Khatib, K.; Jalali, R.; Gama, J. Human Activity Recognition Using Inertial Sensors in a Smartphone: An Overview. Sensors 2019, 19, 3213. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kumar, S.; Buckley, J.L.; Barton, J.; Pigeon, M.; Newberry, R.; Rodencal, M.; Hajzeraj, A.; Hannon, T.; Rogers, K.; Casey, D.; et al. A Wristwatch-Based Wireless Sensor Platform for IoT Health Monitoring Applications. Sensors 2020, 20, 1675. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Saraiva, D.A.F.; Leithardt, V.R.Q.; De Paula, D.; Mendes, A.S.; González, G.V.; Crocker, P. PRISEC: Comparison of Symmetric Key Algorithms for IoT Devices. Sensors 2019, 19, 4312. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sklavos, N.; Zaharakis, I.D. Cryptography and Security in Internet of Things (IoTs): Models, Schemes, and Implementations. In Proceedings of the 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Larnaca, Cyprus, 21–23 November 2016. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. IMSC-EIoTD: Identity Management and Secure Communication for Edge IoT Devices. Sensors 2020, 20, 6546. [Google Scholar] [CrossRef]
- Kumar, N.; Madhuri, J.; ChanneGowda, M. Review on security and privacy concerns in Internet of Things. In Proceedings of the 2017 International Conference on IoT and Application (ICIOT), Nagapattinam, India, 19–20 May 2017. [Google Scholar] [CrossRef]
- Cilliers, L. Wearable devices in healthcare: Privacy and information security issues. Health Inf. Manag. J. 2020, 49, 150–156. [Google Scholar] [CrossRef]
- Ching, K.W.; Singh, M.M. Wearable Technology Devices Security and Privacy Vulnerability Analysis. Int. J. Netw. Secur. Its Appl. 2016, 8, 19–30. [Google Scholar] [CrossRef]
- Yan, T.; Lu, Y.; Zhang, N. Privacy Disclosure from Wearable Devices. In Proceedings of the 2015 Workshop on Privacy-Aware Mobile Computing, Hangzhou, China, 22 June 2015. [Google Scholar] [CrossRef]
- Sklavos, N.; Zaharakis, I.D.; Kameas, A.; Kalapodi, A. Security & Trusted Devices in the Context of Internet of Things (IoT). In Proceedings of the 2017 Euromicro Conference on Digital System Design (DSD), Vienna, Austria, 30 August–1 September 2017; pp. 502–509. [Google Scholar] [CrossRef]
- Mendoza, F.A.; Alonso, L.; López, A.M.; Cabarcos, D.D.S.A.P.A. Assessment of Fitness Tracker Security: A Case of Study. Proceedings 2018, 2, 1235. [Google Scholar] [CrossRef] [Green Version]
- Rieck, J. Attacks on fitness trackers revisited: A case-study of unfit firmware security. arXiv 2016, arXiv:1604.03313. [Google Scholar]
- Saha, R.; Sarkar, S.; Datta, S.K. Balancing security & sharing of fitness trackers’ data. In Proceedings of the 2017 1st International Conference on Electronics, Materials Engineering and Nano-Technology (IEMENTech), Kolkata, India, 28–29 April 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Torre, I.; Koceva, F.; Sanchez, O.R.; Adorni, G. A framework for personal data protection in the IoT. In Proceedings of the 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST), Barcelona, Spain, 5–7 December 2016. [Google Scholar] [CrossRef]
- Adat, V.; Gupta, B.B. Security in Internet of Things: Issues, challenges, taxonomy, and architecture. Telecommun. Syst. 2018, 67, 423–441. [Google Scholar] [CrossRef]
- Hale, M.L.; Lotfy, K.; Gamble, R.F.; Walter, C.; Lin, J. Developing a platform to evaluate and assess the security of wearable devices. Digit. Commun. Netw. 2019, 5, 147–159. [Google Scholar] [CrossRef]
- Meteriz, U.; Yildiran, N.F.; Kim, J.; Mohaisen, D. Understanding the Potential Risks of Sharing Elevation Information on Fitness Applications. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020. [Google Scholar] [CrossRef]
- Aktypi, A.; Nurse, J.; Goldsmith, M. Unwinding Ariadne’s Identity Thread. In Proceedings of the 2017 on Multimedia Privacy and Security, Dallas, TX, USA, 30 October 2017. [Google Scholar] [CrossRef] [Green Version]
- Alrayes, F.; Abdelmoty, A. Towards Location Privacy Awareness on Geo-Social Networks. In Proceedings of the 2016 10th International Conference on Next Generation Mobile Applications, Security and Technologies (NGMAST), Cardiff, UK, 24–26 August 2016. [Google Scholar] [CrossRef] [Green Version]
- Singhal, S.; Neustaedter, C.; Schiphorst, T.; Tang, A.; Patra, A.; Pan, R. You are Being Watched. In Proceedings of the CHI Conference Extended Abstracts on Human Factors in Computing Systems, San Jose, CA, USA, 7–12 May 2016. [Google Scholar] [CrossRef]
- Rowan, M.; Dehlinger, J. A Privacy Policy Comparison of Health and Fitness Related Mobile Applications. Procedia Comput. Sci. 2014, 37, 348–355. [Google Scholar] [CrossRef] [Green Version]
- Ho, J.J.; Novick, S.; Yeung, C. A snapshot of data sharing by select health and fitness apps. In Proceedings of the Seminar on Privacy Implications of Consumer Generated and Controlled Health Data, Washington, DC, USA, 7 May 2014. [Google Scholar]
- Bikos, A.N.; Sklavos, N. The Future of Privacy and Trust on the Internet of Things (IoT) for Healthcare: Concepts, Challenges, and Security Threat Mitigations. In Book Recent Advances in Security, Privacy, and Trust for Internet of Things (IoT) and Cyber-Physical Systems (CPS); Li, K.-C., Brij, B., Gupta, B.B., Agrawal, D.P., Eds.; CRC-Press: Boca Raton, FL, USA, 2020; pp. 63–90. [Google Scholar]
- Lumen Privacy Monitor|ICSI. Available online: https://www.icsi.berkeley.edu/icsi/projects/networking/haystack (accessed on 26 June 2021).
- Razaghpanah, A.; Nithyanand, R.; Vallina-Rodriguez, N.; Sundaresan, S.; Allman, M.; Kreibich, C.; Gill, P. Apps, Trackers, Privacy, and Regulators: A Global Study of the Mobile Tracking Ecosystem. In Proceedings of the 2018 Network and Distributed System Security Symposium, San Diego, CA, USA, 18–21 February 2018. [Google Scholar] [CrossRef]
- Michalevsky, Y.; Boneh, D. Gyrophone: Recognizing Speech from Gyroscope Signals. In Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 1053–1067. [Google Scholar]
- Raij, A.; Ghosh, A.; Kumar, S.; Srivastava, M. Privacy risks emerging from the adoption of innocuous wearable sensors in the mobile environment. In Proceedings of the 2011 Annual Conference on Human Factors in Computing Systems—CHI’11, Vancouver, BC, Canada, 7–12 May 2011. [Google Scholar] [CrossRef]
- Lopes, H.; Pires, I.M.; Blas, H.S.S.; García-Ovejero, R.; Leithardt, V. PriADA: Management and Adaptation of Information Based on Data Privacy in Public Environments. Computers 2020, 9, 77. [Google Scholar] [CrossRef]
- Prevezanos, I.; Tselios, C.; Angelou, A.; McGrath, M.; Mekuria, R.; Tsogkas, V.; Tsolis, G. Evaluating Hammer Network Traffic Simulator: System Benchmarking and Testbed Integration. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar] [CrossRef]
- González-Zapata, A.M.; Tlelo-Cuautle, E.; Cruz-Vega, I.; León-Salas, W.D. Synchronization of chaotic artificial neurons and its application to secure image transmission under MQTT for IoT protocol. Nonlinear Dyn. 2021, 104, 4581–4600. [Google Scholar] [CrossRef]
- De la Fraga, L.G.; Mancillas-López, C.; Tlelo-Cuautle, E. Designing an authenticated Hash function with a 2D chaotic map. Nonlinear Dyn. 2021, 104, 4569–4580. [Google Scholar] [CrossRef]
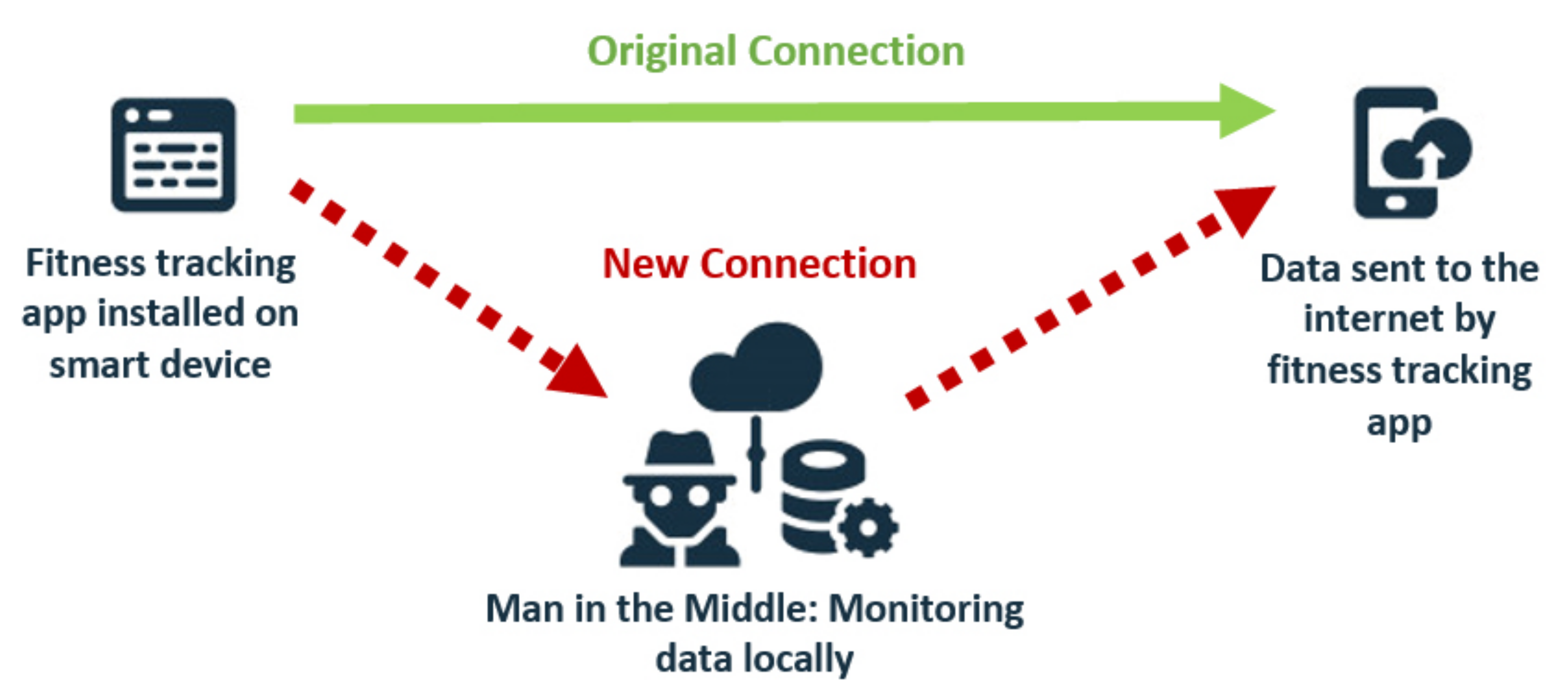
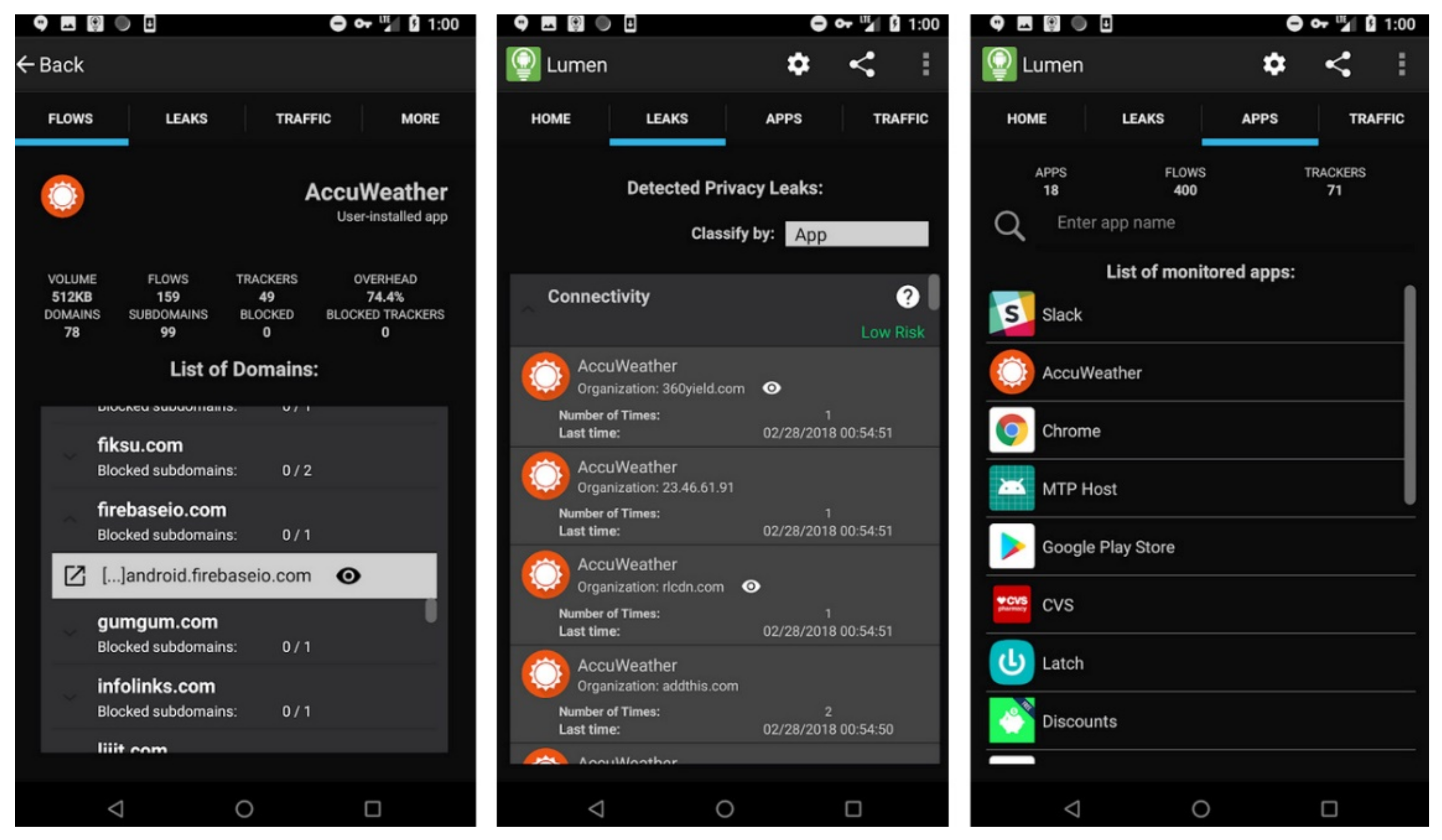
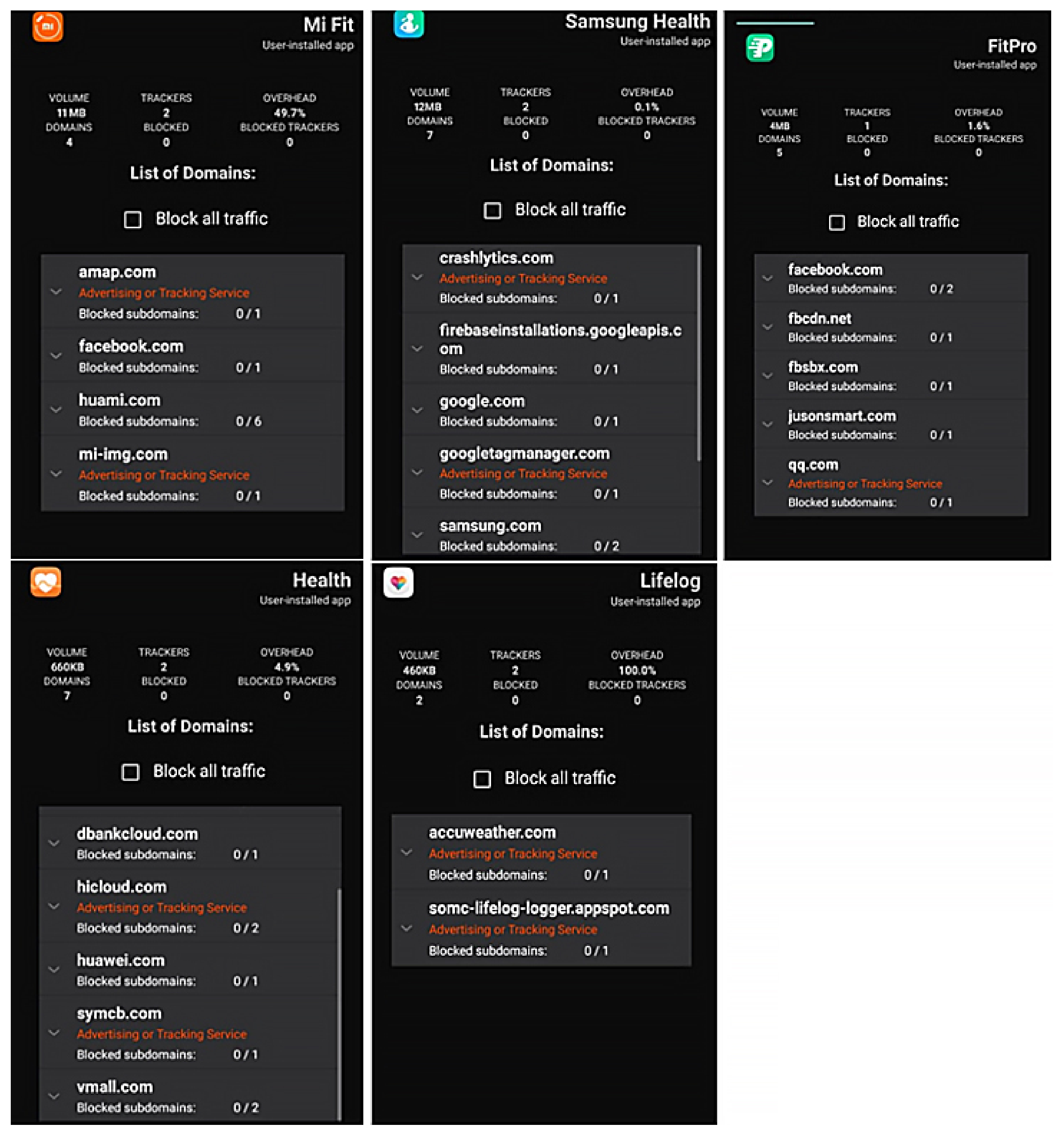
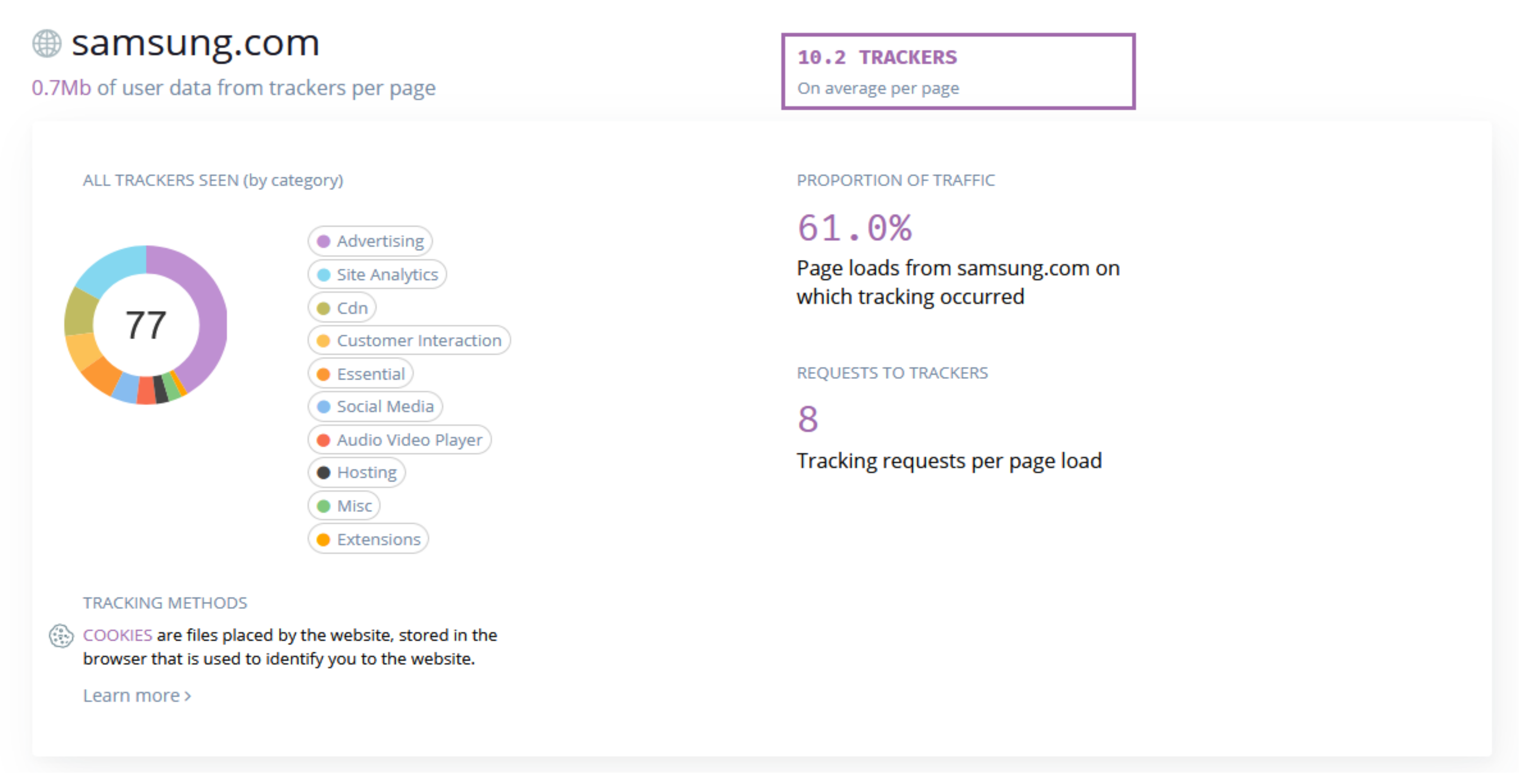
| Study | Method | Findings |
|---|---|---|
| Fereidooni et al. | MITM attack targeting 17 different fitness trackers’ associated applications | Only 5 out of 17 devices take minor measures to protect data integrity. |
| Clausing and Schiefer | MITM attack targeting 7 fitness trackers on Android and Apple Watch | User can be identified by accelerometer and gyroscope signals of walking data. |
| Zhang and Liang | MITM attack targeting 4 different smart wristbands and a smart watch | Identified Replay, MITM, brute-force and DoS attack vulnerabilities on Bluetooth Low Energy based smart wristbands. |
| Goyal, Dragoni, and Spognardi | MITM attack targeting Jawbone UP Move and Fitbit Charge fitness trackers | Vulnerabilities through Bluetooth and Wi-Fi networks in Fitbit and Jabone wristbands. |
| Ho, Novick, and Yeung | MITM in 43 different fitness tracking applications | 12 out of 43 were found to be sharing a huge amount of information to 76 different third parties |
| Wearable Device | Application | Version |
|---|---|---|
| Xiaomi Mi Smart Band 4 | Mi Fit | 4.6.5 |
| Samsung Galaxy Watch Active 2 | Samsung Health | 6.12.3.001 |
| OEM M4-LH716 | FitPro | 1.5.2 |
| Huawei Honor Band 5 | Huawei Health | 10.1.1.312 |
| Sony SWR10 | Lifelog | 4.0.A.0.34 |
| Application | Volume | Flows | Trackers | Overhead |
|---|---|---|---|---|
| Xiaomi Mi Fit | 11 Mb | 235 | 2 | 49.7% |
| Samsung Health | 12 Mb | 54 | 2 | 0.1% |
| FitPro | 4 Mb | 29 | 1 | 1.6% |
| Huawei Health | 660 Kb | 25 | 2 | 4.9% |
| Lifelog | 460 Kb | 10 | 2 | 100% |
| Wearable Device | Number of Trackers | Number of Domains (of Which Advertising or Tracking Services) | Overhead (%) | Leaks |
|---|---|---|---|---|
| Xiaomi Mi Fit | 2 | 4 (2) | 49.7 | 0 |
| Samsung Health | 2 | 7 (2) | 0.1 | 0 |
| FitPro | 1 | 5 (1) | 1.6 | 0 |
| Huawei Health | 2 | 7 (2) | 4.9 | 2 (Low Risk) |
| Lifelog | 2 | 2 (2) | 100 | 0 |
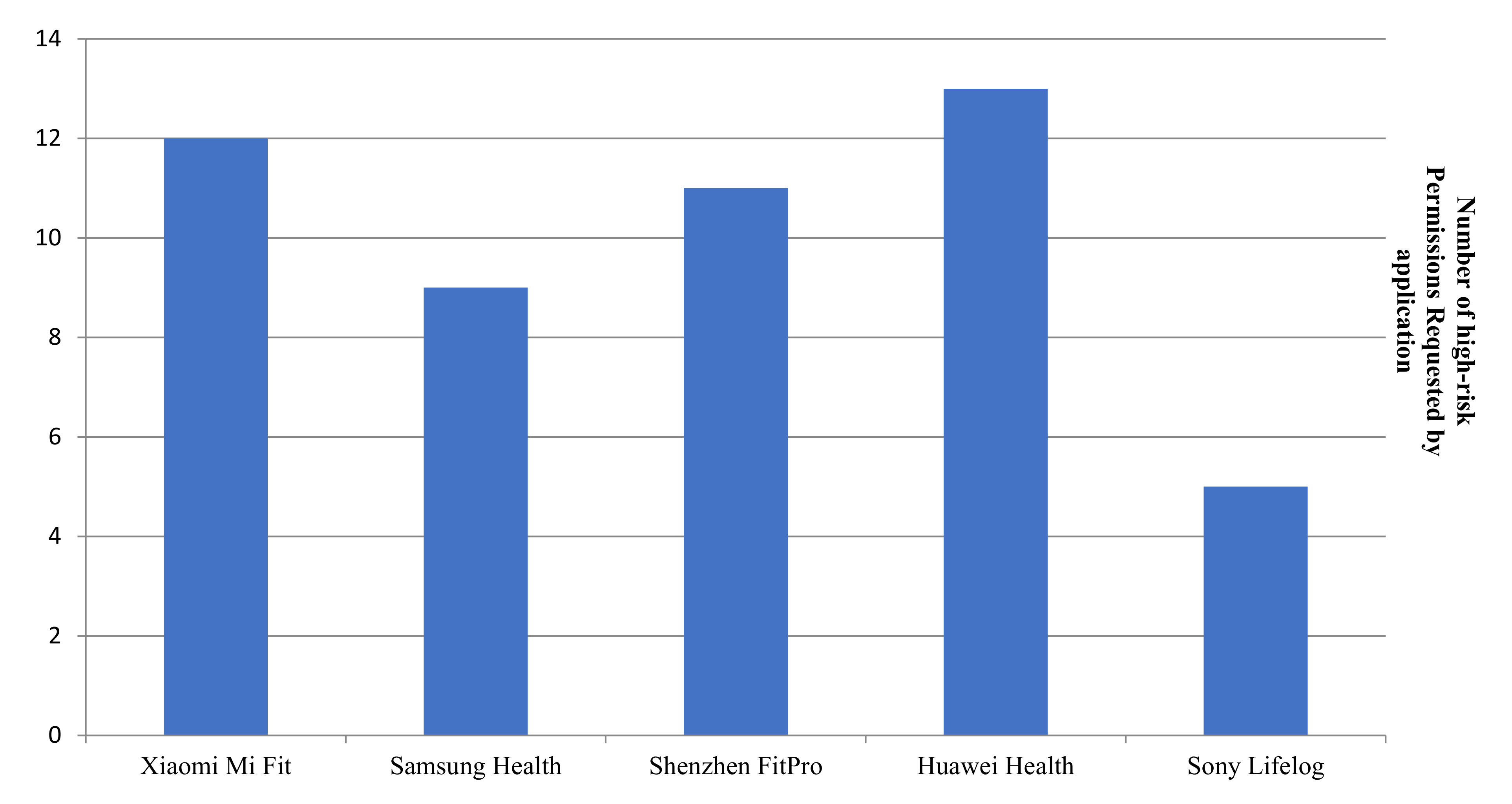
| Requested Permission | Xiaomi Mi Fit | Samsung Health | Shenzhen FitPro | Huawei Health | Sony Lifelog |
|---|---|---|---|---|---|
| Approximate Location | ✓ | ✓ | ✓ | ✓ | ✓ |
| Precise Location | ✓ | ✓ | ✓ | ✓ | ✓ |
| Body Sensors (e.g., heart-rate) | ✓ | ||||
| Camera | ✓ | ✓ | ✓ | ✓ | ✓ |
| Record Audio (by phone’s microphone) | ✓ | ✓ | |||
| External Storage Read | ✓ | ✓ | ✓ | ✓ | ✓ |
| External Storage Write | ✓ | ✓ | ✓ | ✓ | |
| Phone State Read (phone number, cellular network, status of ongoing calls and list of phone accounts) | ✓ | ✓ | ✓ | ✓ | |
| Phone Calls Dial | ✓ | ✓ | |||
| Phone Call Answer | ✓ | ✓ | |||
| Outgoing Calls Process (allows call redirect and call abortion) | ✓ | ✓ | |||
| List of accounts (device’s accounts service) | ✓ | ✓ | ✓ | ||
| Phone Contacts Read | ✓ | ✓ | ✓ | ✓ | |
| Call Log Read | ✓ | ✓ | ✓ | ||
| SMS Read | ✓ | ||||
| SMS Receive | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ioannidou, I.; Sklavos, N. On General Data Protection Regulation Vulnerabilities and Privacy Issues, for Wearable Devices and Fitness Tracking Applications. Cryptography 2021, 5, 29. https://0-doi-org.brum.beds.ac.uk/10.3390/cryptography5040029
Ioannidou I, Sklavos N. On General Data Protection Regulation Vulnerabilities and Privacy Issues, for Wearable Devices and Fitness Tracking Applications. Cryptography. 2021; 5(4):29. https://0-doi-org.brum.beds.ac.uk/10.3390/cryptography5040029
Chicago/Turabian StyleIoannidou, Irene, and Nicolas Sklavos. 2021. "On General Data Protection Regulation Vulnerabilities and Privacy Issues, for Wearable Devices and Fitness Tracking Applications" Cryptography 5, no. 4: 29. https://0-doi-org.brum.beds.ac.uk/10.3390/cryptography5040029






