An IoT-Based Participatory Antitheft System for Public Safety Enhancement in Smart Cities
Abstract
:1. Introduction
2. Related Work
3. Methods and Materials
- City.Risks operation center.
- BLE/Wi-Fi Gateway bridge.
- BLE sensors as antitheft devices.
- Smartphone application.
3.1. Object Tracking Service
- The sensor (with a unique ID) is attached to the object to be tracked.
- The owner registers the sensor to his/her mobile application.
- The sensor supports two operational modes: an active beacon mode and a receiving mode. It switches between them depending on the owner’s decision.
- If the object is lost, the owner informs the authorities via a mobile application developed.
- The authorities dispatch a request to the intermediate entities (gateways or mobile apps of the community network, depending on the scenario).
- The intermediate entities send a signal to activate the sensor.
- The sensor starts broadcasting a beacon.
- The sensor is detected by a nearby community member smartphone through the participatory sensing approach and the location is reported to the authorities.
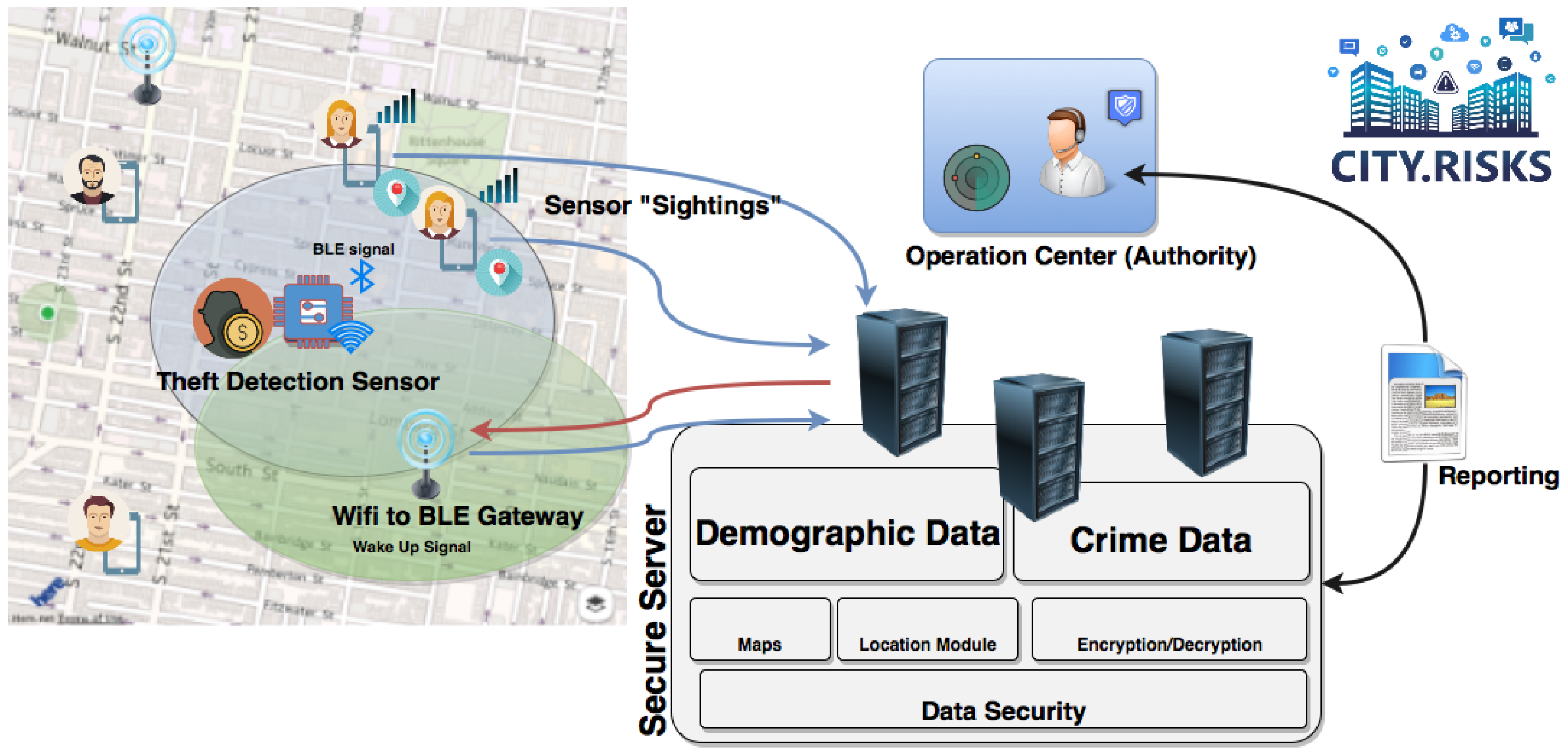
3.2. System Architecture
- The communication between the mobile application/gateways and the Operation Center is via HTTP and is secured with hash authentication. Only City.Risks application users/gateways can communicate with this endpoint and receive information from it.
- There are only two procedures that can be initiated by the Operation Center, which are activation and discovery. These two procedures can only be initiated after a request from the owner of the device (the one that has registered the device). The request is accompanied by the unique ID of the stolen device and does not contain any personal information about its possessor. Therefore, the tracking procedure focuses on the object and not the owner.
- No mobile application/gateway can initiate a tracking procedure without a corresponding command of the Operation Center (secured with hash authentication).
- No user can report a stolen device that he/she does not own (confirmed with local registration). Therefore, a tracking procedure cannot be initiated by other than the owner.
- The reports received from participatory users during the tracking procedure are not associated with them but with the stolen device. Therefore, the location that accompanies the sighting reports is associated with the ID of the stolen device.
3.3. Sensor Operational Modes and Events Sequence
- Stealth mode: In this state the device does not transmit at all. Only the authorized user will be able to connect to the tag by using a passphrase. The passphrase is provided to the Authority by the user that reports the theft. The Authority in turn provides the selected app-users and beacons with it, so they can wake up the device. The purpose of this is to prevent non-authorized personnel from accessing the device.
- Beacon mode: In this mode, the device is awake and notifies every mobile app user or gateway of its existence. In this mode, the sensor operates under the optimum current consumption scheme.
- State 1: Tag is in beacon mode—No theft report → no interaction from the mobile app.
- State 2: Tag is in stealth mode—No theft report → no interaction from the mobile app, except if user wants to switch it back to beacon mode.
- State 3: Tag is in beacon mode—Theft report → Authorities send signal to the mobile app to search for the beacon signals (track the tag).
- State 4: Tag is in stealth mode—Theft report → Authorities send signal to the mobile app to activate the tag (switch to beacon mode) → Activation Confirmed → Authorities signal the tracking procedure.
- Contain Antitheft Sensor with the coin cell battery case attached;
- Protect the sensor and the battery from environment factors that could harm the device;
- Make the device compact and easy to install on multiple items of interest (bicycles, bags, etc.);
- Allow the developer to make changes to the software without removing the sensor from the case.
3.4. Mobile Phone Application Features
- Tag register;
- Tag deregister;
- Theft report;
- Stealth mode on;
- Activate my device.
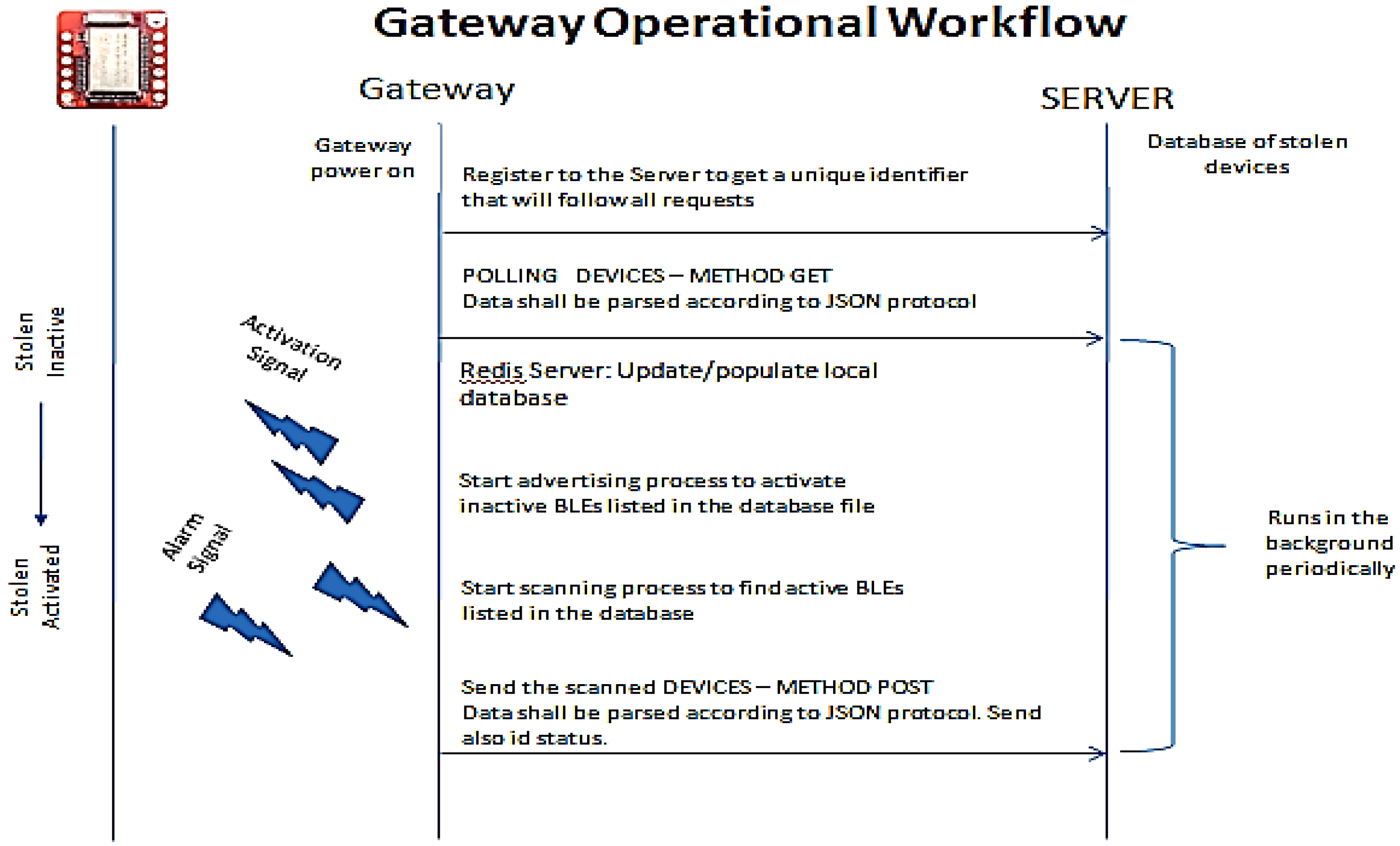
3.5. Gateway Operational Workflow
- REG: Registered device. The device is considered as being in normal status as there has been no user report concerning their status modification.
- ACT: Active device. The device is considered as being a stolen device; therefore, associated sensors must be beacon-enabled by the Gateway.
- INA: Inactive device. The device is considered as being activated (not necessarily found or traced), and beacon broadcast will be terminated by the platform.
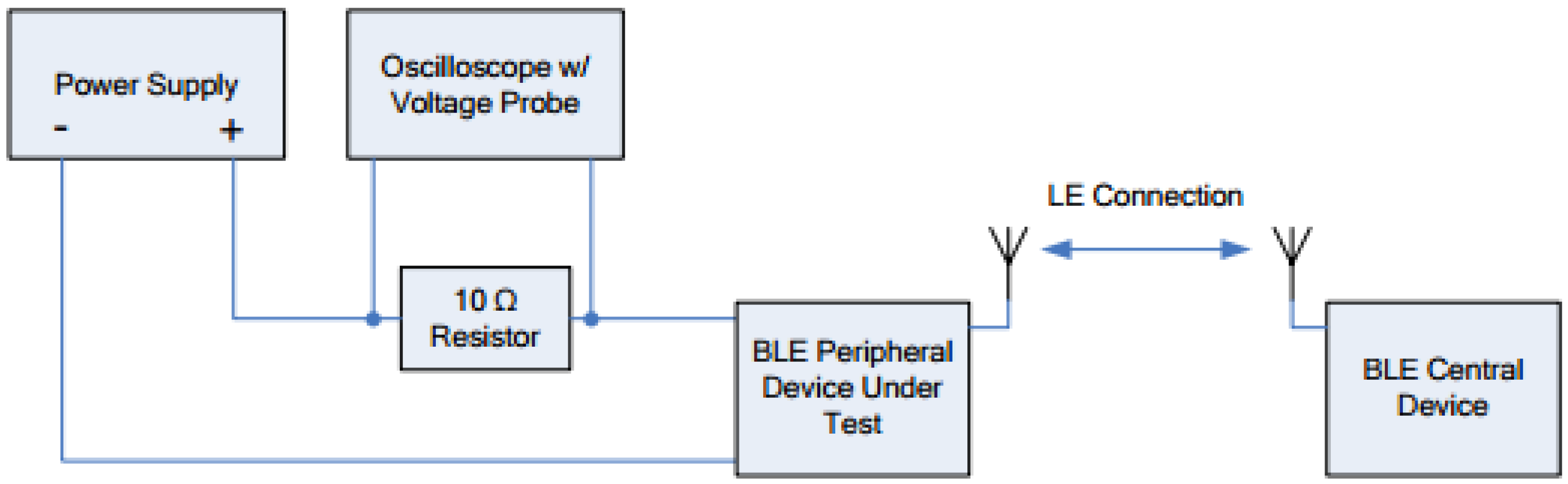
3.6. Current Consumption
- Advertising interval;
- Amount of advertising payload data in bytes for each advertising packet;
- Continuous advertising or periodical advertising;
- Transmitter power.
- Connection interval;
- Slave latency;
- Receive (RX) payload in each packet;
- Transmit (TX) payload in each packet.
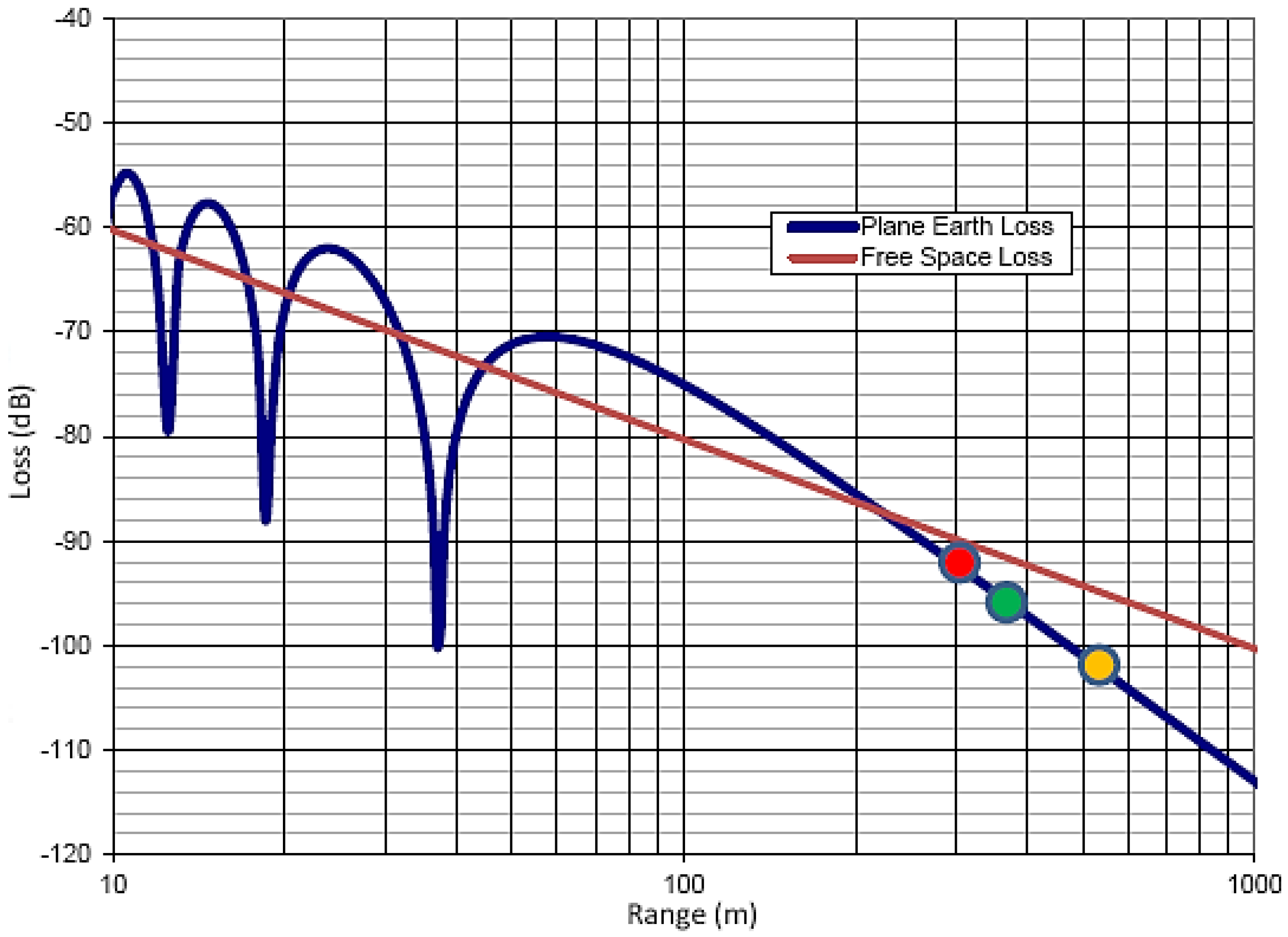
3.7. Range Calculation
- Persons/obstacles moving close to the antenna. This is due to multipath propagation and will have an impact even if the person is not in the line of sight between the two radios.
- Any obstacles within the radio path.
- Transmitting antenna gain and height.
- The mechanical design of the end product.
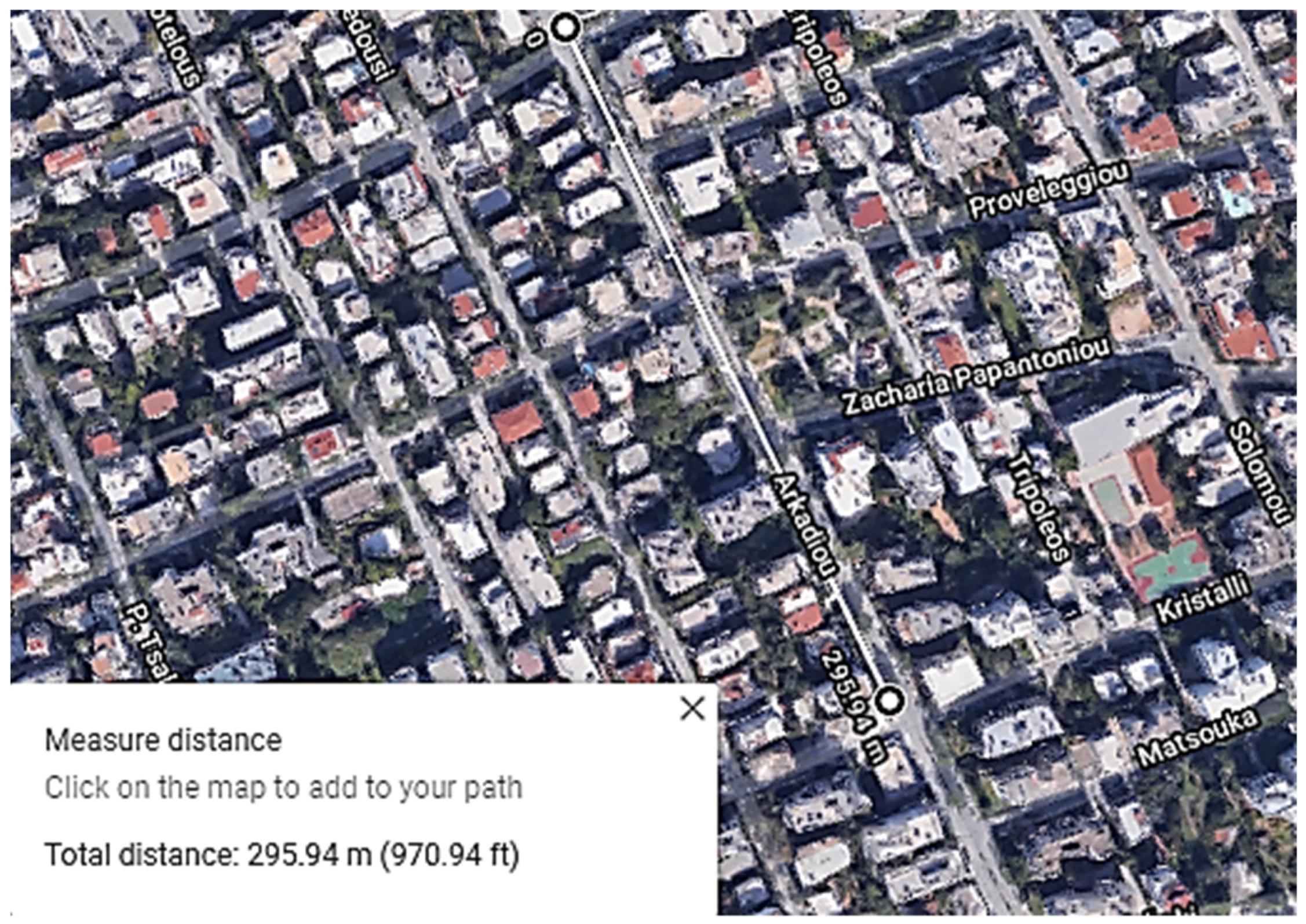
3.8. BLE Range Test Definition and Use Case Scenarios
- iBLio BLE/USB G03 unit with either 2 dBi or 9 dBi antenna connected to laptop USB port.
- RedBear nano-BLE tag with CRC2032 battery.
- Android Mobile phone to test and validate signal level.
- High/low antenna gain connection to BLE module.
- Configuration of BLE Tx power level and custom device name.
- Confirmation that custom device name is properly transmitted.
- Activation of BLE tag device and arrangement of it to be in observer mode. This ensures that data can be received by the test device.
- Separation of the two devices until BLE nanomode can be marginally modified.
- Recording of the previous mentioned location.
- Use of geographical information software (in this case Google Earth), to measure the range of the connection.
- Repetition of the experiment by using different antenna heights.
4. Performance Evaluation and Discussion
- Receiving theft incident reports along with the stolen device unique identifier (UID).
- Notifying the Mobile apps and the Gateways to initiate the activation process of the stolen device, and also providing them with the stolen device UID. This is the most innovative feature of the entire solution. The user can set the BLE sensor to remain at receiver only mode so as to prevent BLE transmission which could trigger the potential theft to remove or destroy the sensor if the thief’s mobile phone is notified by the sensor beacon signal.
- Receiving an activation report from either the mobile app or the gateway that activated the stolen device.
- Letting the gateway capture the signal and inform the Authorities once the sensor switches from receiver to beacon mode.
- Notifying both the gateways and the mobile apps to start scanning once the stolen device is activated.
- Triggering, nearby Gateways to start scanning the sensor which is in beacon mode
- Notifying the mobile apps to switch to inactive mode and stop scanning when the stolen device has been retrieved.
5. Future Work
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mealey, L. The sociobiology of sociopathy: An integrated evolutionary model. Behav. Brain Sci. 1995, 18, 523–541. [Google Scholar] [CrossRef] [Green Version]
- Insurance Information Institute. Available online: https://www.iii.org/fact-statistic/facts-statistics-auto-theft#Motor%20Vehicle%20Theft,%202010-2019 (accessed on 30 March 2021).
- Van Dijk, J.J.M.; Van Kesteren, J.N.; Smit, P. Criminal Victimization in International Perspective, Key Findings from the 2004–2005 ICVS and EU ICS; Boom Legal Publishers: Den Haag, The Netherlands, 2008; pp. 257–258. [Google Scholar]
- Hom, E.J. Mobile Device Security: Startling Statistics on Data Loss and Data Breaches. 2017. Available online: http://www.channelpronetwork.com/article/mobile-device-security-startling-statistics-data-loss-anddata-breaches (accessed on 7 March 2021).
- Zhang, L.; Messner, S.F.; Liu, J. Bicycle-Theft Victimization in Contemporary Urban China, A Multilevel Assessment of Risk and Protective Factors. J. Res. Crime Delinq. 2007, 44, 406–426. [Google Scholar] [CrossRef]
- Goonetilleke, A.; Yigitcanlar, T.; Ayoko, G.; Egodawatta, P. Sustainable Urban Water Environment: Climate, Pollution and Adaptation; Edward Elgar: Cheltenham, UK, 2014. [Google Scholar]
- Lara, A.; Costa, E.; Furlani, T.; Yigitcanlar, T. Smartness that matters: Comprehensive and human-centred characterisation of smart cities. J. Open Innov. Technol. Mark. Complex. 2016, 2, 1–13. [Google Scholar] [CrossRef] [Green Version]
- Yigitcanlar, T.; Hoon, M.; Kamruzzaman, M.; Ioppolo, G.; Sabatini-Marques, J. The making of smart cities: Are Songdo, Masdar, Amsterdam, San Francisco and Brisbane the best we could build? Land Use Policy 2019, 88, 104187. [Google Scholar] [CrossRef]
- Trindade, E.P.; Hinnig, M.P.F.; Da Costa, E.M.; Marques, J.S.; Bastos, R.C.; Yigitcanlar, T. Sustainable development of smart cities: A systematic review of the literature. J. Open Innov. Technol. Mark. Complex. 2017, 3, 11–14. [Google Scholar] [CrossRef] [Green Version]
- Zawieska, J.; Pieriegud, J. Smart city as a tool for sustainable mobility and transport decarbonisation. Transp. Policy 2018, 63, 39–50. [Google Scholar] [CrossRef]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of Wireless Sensor Networks: An Up-to-Date Survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef] [Green Version]
- Zantalis, F.; Koulouras, G.; Karabetsos, S.; Kandris, D. A Review of Machine Learning and IoT in Smart Transportation. Future Internet 2019, 11, 94. [Google Scholar] [CrossRef] [Green Version]
- Ejaz, W.; Anpalagan, A. Internet of Things for Smart Cities: Overview and Key Challenges. In Internet of Things for Smart Cities: Technologies, Big Data and Security; Springer International Publishing: Cham, Switzerland, 2019; pp. 1–15. [Google Scholar]
- Memos, V.A.; Psannis, K.E.; Ishibashi, Y.; Kim, B.G.; Gupta, B. An Efficient Algorithm for Media-based Surveillance System (EAMSuS) in IoT Smart City Framework. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Alazab, M.; Lakshmanna, K.; Reddy, T.; Pham, Q.V.; Maddikunta, P.K.R. Multi-objective cluster head selection using fitness averaged rider optimization algorithm for IoT networks in smart cities. Sustain. Energy Technol. Assess. 2021, 43, 100973. [Google Scholar]
- Kandris, D.; Alexandridis, A.; Dagiuklas, T.; Panaousis, E.; Vergados, D.D. Multiobjective Optimization Algorithms for Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2020, 1, 1–5. [Google Scholar] [CrossRef]
- Mahesh, R.P.; Imdad, R. IoT Based Embedded System for Vehicle Security and Driver Surveillance. In Proceedings of the 2nd International Conference on Inventive Communication and Computational Technologies (ICICCT 2018), Coimbatore, India, 20–21 April 2018; pp. 466–470. [Google Scholar]
- Raj, C.; Rajkumar, S.M. Design of a Low Cost GSM Based Embedded System for Preventing Vehicle Theft Using AVR Microcontroller. J. Sib. Fed. Univ. Eng. Technol. 2020, 13, 63–68. [Google Scholar]
- Vivek, K.S.; Soumitra, M.; Harshit, M. Car Security using Internet of Things. In Proceedings of the 1st IEEE International Conference on Power Electronics Intelligent Control and Energy Systems (ICPEICES-2016), Delhi, India, 4–6 July 2016; pp. 1–5. [Google Scholar]
- Ramadan, M.; Al-Khedher, M.; Al-Kheder, S. Intelligent anti-theft and tracking system for automobiles. Int. J. Mach. Learn. Comput. 2012, 2, 83. [Google Scholar] [CrossRef]
- Al-Hindawi, A.M.J.; Talib, I. Experimentally Evaluation of GPS/GSM Based System Design. J. Electron. Syst. 2012, 2, 67. [Google Scholar]
- Guorui, Z.; Dai, S. Design of auto guard against theft system based on GPRS and GPS. Microcontroll. Embed. Syst. 2007, 8, 39–41. [Google Scholar]
- Fasiuddin, S.; Omer, S.; Sohelrana, K.; Tamkeen, A.; Rasheed, M.A. Real Time Application of Vehicle Anti Theft Detection and Protection with Shock Using Facial Recognition and IoT Notification. In Proceedings of the 2020 Fourth International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 11–13 March 2020; pp. 1039–1044. [Google Scholar]
- Das, D.; Banerjee, S.; Ghosh, U.; Biswas, U.; Bashir, A.K. A decentralized vehicle anti-theft system using Blockchain and smart contracts. Peer-to-Peer Netw. Appl. 2021, 1–14. [Google Scholar] [CrossRef]
- Guo-Cheng, L.; Hong-Yang, Y. Design and implementation of a Bluetooth 4.0-based heart rate monitor system on iOS platform. In Proceedings of the 2013 International Conference on Communications, Circuits and Systems (ICCCAS), Chengdu, China, 15–17 November 2013; pp. 112–115. [Google Scholar]
- Arvanitopoulos, A.; Gialelis, J.; Koubias, S. Energy efficient indoor localization utilizing BT 4.0 strapdown inertial navigation system. In Proceedings of the 2014 IEEE Emerging Technology and Factory Automation (ETFA), Barcelona, Spain, 16–19 September 2014; pp. 1–5. [Google Scholar]
- Liu, J.; Chen, C.; Ma, Y.; Xu, Y. Energy Analysis of Device Discovery for Bluetooth Low Energy. In Proceedings of the 2013 IEEE 78th Vehicular Technology Conference (VTC Fall), Las Vegas, NV, USA, 2–5 September 2013; pp. 1–5. [Google Scholar]
- Siekkinen, M.; Hiienkari, M.; Nurminen, J.K.; Nieminen, J. How low energy is bluetooth low energy? Comparative measurements with ZigBee/802.15.4. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Paris, France, 1 April 2012; pp. 232–237. [Google Scholar]
- Koodtalang, W.; Sangsuwan, T. Improving motorcycle anti-theft system with the use of Bluetooth Low Energy 4.0. In Proceedings of the 2016 International Symposium on Intelligent Signal Processing and Communication Systems (ISPACS), Phuket, Thailand, 24–27 October 2016; pp. 1–5. [Google Scholar]
- City.Risks Project Overview, Objectives. Available online: http://project.cityrisks.eu/project-overview/ (accessed on 17 March 2021).
- Bluetooth Low Energy. Available online: https://www.bluetooth.com/learn-about-bluetooth/radio-versions/ (accessed on 29 March 2021).
- Townsend, K.; Cufí, C.; Davidson, R. Getting Started with Bluetooth Low Energy: Tools and Techniques for Low-Power Networking, 1st ed.; O’Reilly Media Inc.: Sebastopol, CA, USA, 2014; pp. 1–4. [Google Scholar]
- Du, J.; Chao, S. A study of information security for M2M of IOT. In Proceedings of the 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010; p. V3-576. [Google Scholar]
- Wu, G.; Talwar, S.; Johnsson, K.; Himayat, N.; Johnson, K.D. M2M: From mobile to embedded internet. IEEE Commun. Mag. 2011, 49, 36–43. [Google Scholar]
- City.Risks Deliverable D2.4 Use Case Requirements and Key Performance Indicators. Available online: http://project.cityrisks.eu/wp-content/uploads/deliverables/CityRisks_D2.4-Use%20Cases,-Requirements-and-Key-Performance-Indicators.pdf (accessed on 17 March 2021).
- Starsinic, M. System architecture challenges in the home M2M network. In Proceedings of the 2010 IEEE Long Island Systems, Applications and Technology Conference, Farmingdale, NY, USA, 7 May 2010; pp. 1–7. [Google Scholar]
- Lee, C.T.; Chang, C.M.; Kao, C.Y.; Tseng, H.M.; Hsu, H.; Nien, C.C.; Chen, L.H.; Lai, L.Y.; Chiu, T.C.; Chou, P.H. Smart Insulating Container with Anti-theft Features by M2M Tracking. In Proceedings of the 2014 IEEE International Conference on Internet of Things (iThings), and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom), Taipei, Taiwan, 1–3 September 2014; pp. 140–147. [Google Scholar]
- Rao, M.; Newe, T.; Grout, I. Secure Hash Algorithm-3(SHA-3) implementation on Xilinx FPGAs, Suitable for loT Applications. In Proceedings of the 8th International Conference on Sensing Technology, Liverpool, UK, 2–4 September 2014; Volume 7. [Google Scholar]
- Pinto, A.; Costa, R. Hash-Chain-Based Authentication for Iot. Adv. Distrib. Comput. Artif. Intell. J. 2015, 3, 1–16. [Google Scholar] [CrossRef] [Green Version]
- RedBearLabBLE Nano. Available online: https://os.mbed.com/platforms/RedBearLab-BLE-Nano/ (accessed on 17 March 2021).
- nRF51822 Bluetooth Smart Beacon Kit. Available online: https://www.nordicsemi.com/Software-and-tools/Reference-Designs/nRF51822-Beacon-Kit/GetStarted (accessed on 17 March 2021).
- Laird Bluetooth Modules. Available online: https://www.lairdtech.com/product-categories/connectivity-solutions/bluetooth-modules (accessed on 17 March 2021).
- Cypress Technologies PSoC 4 Bluetooth Low Energy Compliant Pioneer Kit. Available online: http://www.cypress.com/documentation/development-kitsboards/cy8ckit-042-ble-bluetooth-low-energy-ble-pioneer-kit (accessed on 17 March 2021).
- Jin, M.; He, Y.; Fang, D.; Chen, X.; Meng, X.; Xing, T. iGuard: A Real-Time Anti-Theft System for Smartphones. IEEE Trans. Mob. Comput. 2018, 17, 2307–2320. [Google Scholar] [CrossRef]
- Pezoa, F.; Reutter, J.; Suarez, F.; Ugarte, M.; Vrgoč, D. Foundations of JSON Schema. In Proceedings of the 25th International Conference on World Wide Web, Montreal, QC, Canada, 11–15 April 2016; pp. 263–273. [Google Scholar]
- Silicon Labs. BLE112. Available online: https://www.silabs.com/documents/public/data-sheets/BLE112-DK-DataSheet.pdf/ (accessed on 17 March 2021).
- Silicon Labs. BLE112, BLE113 and BLE121LR Range Analysis. Available online: https://www.silabs.com/documents/public/application-notes/AN985.pdf (accessed on 17 March 2021).
- Silabs AN983: Bluetooth® 4.0 Heart Rate Sensor Application Note. Available online: https://www.silabs.com/documents/public/application-notes/AN983-Bluetooth-4.0-Heart-Rate-Sensor.pdf (accessed on 27 March 2021).
- Bluetooth Smart Module Configuration Guide, Version 31. Available online: https://www.scribd.com/document/269277579/Bluetooth-Smart-Configuration-Guide-v31 (accessed on 27 March 2021).
- Lower Power Mode Nordic nRF51822. Available online: https://developer.mbed.org/questions/4693/Lower-power-Mode-Nordic-nRF51822/ (accessed on 27 March 2021).
- Major Cities of Europe IT Users Group. Available online: https://www.majorcities.eu/misc/eu-projects/city-risks/ (accessed on 15 May 2021).
- Wang, X.; Büsze, B.; Vandecasteele, M.; Liu, Y.H.; Bachmann, C.; Philips, K. The design challenges of IoT: From system technologies to ultra-low power circuits. IEICE Trans. Electron. 2017, 100, 515–522. [Google Scholar] [CrossRef] [Green Version]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low Power Wide Area Networks: An Overview. IEEE Commun. Surv. Tutor. 2017, 19, 855–873. [Google Scholar] [CrossRef] [Green Version]
- Yigitcanlar, T.; Kamruzzaman, M.; Foth, M.; Sabatini-Marques, J.; da Costa, E.; Ioppolo, G. Can cities become smart without being sustainable? A systematic review of the literature. Sustain. Cities Soc. 2019, 45, 348–365. [Google Scholar] [CrossRef]













| Setup | Practical Line of Sight Range Tested |
|---|---|
| BLE121LR vs. iPod | 250 m–300 m |
| BLE121LR vs. Nexus7 | ~430 m |
| BLE113 vs. iPod | 60 m–80 m |
| Direction | Antenna Attenuation (dB) | Link Budget (dB) | Range Calculated (m) | Range Tested (m) |
|---|---|---|---|---|
| Front | −3 | 100 | 470 | 450 |
| Back | −7 | 92 | 300 | 300 |
| Side | −5 | 96 | 370 | 340 |
| Antenna Type | Transmit Power (dBm) | Antenna Height (m) | Distance Reached (m) |
|---|---|---|---|
| 2.5 dBi | 3 | 1.5 | 295 |
| 5 | 310 | ||
| 9 dBi | 3 | 1.5 | 350 |
| 5 | 377 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Papadakis, N.; Koukoulas, N.; Christakis, I.; Stavrakas, I.; Kandris, D. An IoT-Based Participatory Antitheft System for Public Safety Enhancement in Smart Cities. Smart Cities 2021, 4, 919-937. https://0-doi-org.brum.beds.ac.uk/10.3390/smartcities4020047
Papadakis N, Koukoulas N, Christakis I, Stavrakas I, Kandris D. An IoT-Based Participatory Antitheft System for Public Safety Enhancement in Smart Cities. Smart Cities. 2021; 4(2):919-937. https://0-doi-org.brum.beds.ac.uk/10.3390/smartcities4020047
Chicago/Turabian StylePapadakis, Nikos, Nikos Koukoulas, Ioannis Christakis, Ilias Stavrakas, and Dionisis Kandris. 2021. "An IoT-Based Participatory Antitheft System for Public Safety Enhancement in Smart Cities" Smart Cities 4, no. 2: 919-937. https://0-doi-org.brum.beds.ac.uk/10.3390/smartcities4020047






