A Study on the Evolution of Ransomware Detection Using Machine Learning and Deep Learning Techniques
Abstract
:1. Introduction
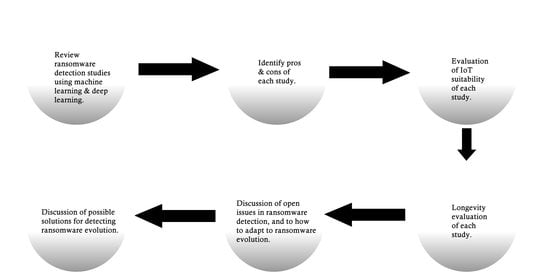
1.1. Contribution
- Review of Research: Review available machine learning and deep learning approaches to detecting ransomware; this is done in Section 3 and Section 4. We assess each research paper on their algorithmic approach, feature engineering process, results, and experiments. We also evaluate the weaknesses of each approach and how improvements can be made in the future.
- Evaluate Research: We evaluate each study’s strengths, weaknesses, and how they can be improved; this is included in Section 3, Section 4 and Section 5. The individual algorithms and papers reviewed are listed and broken down in Table 1. Summaries of the research papers can be found in Table 2 and Table 3. Table 2 presents a summary of each paper, and Table 3 shows the statistical achievements of each research study.
- Longevity Evaluation Experiments: We evaluate the longevity of these approaches by running our experiments on current generation and older generation ransomware. The results of our independent experiments are shown in Section 7. Section 7 focuses on testing for the existence of concept drift in ransomware over four years. Our experiments introduce concept drift to the approaches we reviewed and observe their accuracy under concept drift.
1.2. Paper Organisation
2. Preliminaries
2.1. Processes and Tools of Ransomware Detection
2.1.1. Cuckoo Sandbox
2.1.2. Machine Learning Platforms
2.1.3. Ransomware Detection Process For Learning Algorithms
2.2. Ransomware Infection Vectors
2.3. Command and Control (C&C)
2.4. Encryption and Extortion
2.5. Ransomware Detection Challenges
2.6. Ransomware in IoT
3. Machine Learning Detection Studies
3.1. Study Summary Table
| Research Study | Summary | Ransomware Used | Features Used | Dataset |
|---|---|---|---|---|
| EldeRan [10]: 2016 |
| Critoni, Cryptolocker, CryptoWall, Kollah, Kovter, Locker, MARSNU, PGPCoder, Reventon, TeslaCrypt, Trojan-Ransom. |
|
|
| RansomWall [11]: 2018 |
| CryptoWall, TeslaCrypt, Cerber, CTB-Locker, Jigsaw, TorrentLocker, Locky, CryptoLocker, CryptoDefense, Hidden Tear, CryptoFortress, CrypVault. |
|
|
| RansHunt [12]: 2017 |
| GPCoder, Winlock, Reveton, DirtyCrypt, CryptoLocker, CryptoWall, CryptoWallv3, Critoni, TeslaCrypt, CryptoWallv4, Locky, CBT Locker, TorrentLocker, Cerber3, Samas, CryptXXX. |
|
|
| Deep Learning [26]: 2016 |
| CryptoWall, TeslaCrypt, CryptXXX, Locky, CrypMIC, Cerber. |
|
|
| Long Short Term Memory (LSTM) [27]: 2017 |
| N/A. |
|
|
| Behavioural-Based [13]: 2018 |
| Cerber, Cryptowall, Crysis, Jaff, Jigsaw, Locky, Petya, Sage, Torrent Locker, Wannacry. |
|
|
| Support Vector Machines [14]: 2018 |
| WannaCry, Cerber, Petya, CryptoLocker. |
|
|
| SDN [15]: 2018 |
| Cerber. |
|
|
| NetConverse [16]: 2018 |
| Cerber, CryptoWall, CryptoLocker, CTB Locker, Locky, PadCrypt, PayCrypt, TeslaCrypt, Torrentlocker. |
|
|
| Shallow and Deep networks [28]: 2017 |
| Cerber, Cryptolocker, CryptoWall, Maktub, Sage, Torrentlocker. |
|
|
| Bayesian networks [17]: 2019 |
| Locky. |
|
|
| Analysis Framework [18]: 2016 |
| Locky, Teslacrypt, FileLocker, FileCryptor, Troldesh, CryptoWall, TorrentLocker, CryptoLocker, ZeroLocker, CryptoTorLocker, CTBLocker, Xorist, WannaCrypt. |
|
|
| Feature Selection-Based Detection [19]: 2018 |
| Locky, Cerber. |
|
|
| Machine Learning-Based File Entropy Analysis [20]: 2019 |
| PC BYBORG, Reveton, CryZip, May Archieve, FAVEAC, FastBsod, CyrptoLocker, GPCoder, Simple-Locker, TeslaCrypt, CryptorBit, KeRangerm CryptoWall. |
|
|
| Digital DNA Sequencing [21]: 2020 |
| Critoni, Cryptolocker, CryptoWall, Kollah, Kovter, Locker, MARSNU, PGPCoder, Reventon, TeslaCrypt, Trojan-Ransom. |
|
|
| Resilient Machine Learning [22]: 2019 |
| N/A. |
|
|
| API Sequence-Based Detection [23]: 2019 |
| N/A. |
|
|
| Two-stage Detection [24]: 2020 |
| N/A. |
|
|
| Multi-Tier Streaming Analytics Model [25]: 2020 |
| AiDS, GpCode, Archiveus, WinLock, Reveton, CryptoLocker, CryptoWall, RaaS, Cerber, Locky, Crysis, WannaCry, Sopra, Zeus. |
|
|
3.2. EldeRan
3.2.1. Feature Mapping
3.2.2. Regularised Logistic Regression
3.2.3. Experiments
3.2.4. Discussion
3.3. RansomWall
3.3.1. Feature Mapping
3.3.2. Gradient Tree Boosting
3.3.3. Experiments
3.3.4. Discussion
3.4. RansHunt
3.4.1. Feature Mapping
3.4.2. Support Vector Machines
3.4.3. Experiments
3.4.4. Discussion
3.5. Behavioural-Based
3.5.1. Feature Mapping
3.5.2. J48 Decision Tree
3.5.3. Experiments
3.5.4. Discussion
3.6. SVM
3.6.1. Feature Mapping
3.6.2. Experiments
3.6.3. Discussion
3.7. SDN(Software-Defined Network)
3.7.1. Feature Mapping
3.7.2. Random Forests
3.7.3. Discussion
3.8. NetConverse
3.8.1. Feature Mapping
3.8.2. Experiments
3.8.3. Discussion
3.9. Bayesian Networks
3.9.1. Feature Mapping
3.9.2. Bayesian Networks
3.9.3. Experiments
3.9.4. Discussion
3.10. Analysis Framework
3.10.1. Feature Mapping
3.10.2. AdaBoost
3.10.3. Experiments
3.10.4. Discussion
3.11. Feature Selection-Based Detection
3.11.1. Feature Mapping
3.11.2. Experiments
3.11.3. Discussion
3.12. Machine Learning-Based File Entropy Analysis
3.12.1. Feature Mapping
3.12.2. Entropy
3.12.3. Experiments
3.12.4. Discussion
3.13. Digital DNA Sequencing
3.13.1. Feature Mapping
3.13.2. Digital DNA Sequencing
3.13.3. Experiments
- Query strategies based on uncertainties, where instances with the lowest prediction confidence are queried.
- Query strategies based on disagreement which queries the instances on which the hypothesis space has the most disagreement degree on their predictions.
- Minimise the expected variances and error by labelling the instances on the pool of unlabelled instances.
- Exploiting the structure information among the instances.
3.13.4. Discussion
3.14. Resilient Machine Learning
3.14.1. Feature Mapping
3.14.2. GAN
3.14.3. Experiments
3.14.4. Discussion
3.15. API Sequence-Based Detection
3.15.1. Feature Mapping
3.15.2. CF-NCF (Class Frequency-Non-Class Frequency)
3.15.3. Experiments
3.15.4. Discussion
3.16. Two Stage Ransomware Detection
3.16.1. Feature Mapping
3.16.2. Markov Chains
3.16.3. Experiments
3.16.4. Discussion
3.17. Multi-Tier Streaming Analytics Model
3.17.1. Feature Mapping
3.17.2. HML Learner
3.17.3. Experiments
3.17.4. Discussion
4. Deep Learning Detection Studies
4.1. Deep Neural Networks
4.1.1. Feature Mapping
4.1.2. DNP
4.1.3. Experiments
4.1.4. Discussion
4.2. Long Short Term Memory (LSTM)
4.2.1. Feature Mapping
4.2.2. LSTMs
4.2.3. Experiments
4.2.4. Discussion
4.3. Shallow and Deep Networks
4.3.1. Feature Mapping
4.3.2. ANN
4.3.3. Experiments
4.3.4. Discussion
5. Experimental Observations & Open Issues
- Effective ML and DL: Machine learning models can be effectively trained to detect ransomware, albeit with some issues which can be addressed.
- Effective Feature Types: The research reviewed points towards the idea that the use of behavioural, network, and static features can all prove effective, despite none of the research papers combining the use of all three types of features.
- Evolution: There is a lack of emphasis on the evolution of ransomware and how the models created would become obsolete over time.
| Research Studies | Detection Rate | Recall | FPR | FNR | Precision | F1 Score |
|---|---|---|---|---|---|---|
| EldeRan [10]: 2016 | 96.34% | 96.33% | 0.16 % | 3.66% | 0.9983 | 0.9805 |
| RansomWall [11]: 2018 | 98.25% | 97.28% | 0.056% | 2.75% | 0.9994 | 0.9884 |
| RansHunt [12]: 2017 | 97.1% | 97.04% | 2.1% | 2.9% | 0.9788 | 0.9749 |
| Deep-Learning [26]: 2016 | 93.92% | 88.76% | 38% | 7.08% | 0.7119 | 0.8099 |
| Long Short Term Memory (LSTM) [27]: 2017 | 96.67% | N/A | N/A | 3.33% | N/A | N/A |
| Behavioural-Based [13]: 2018 | 78% Ransomware family classification rate. | N/A | N/A | N/A | N/A | N/A |
| Support-Vector Machines [14]: 2018 | 97.18% | 97.13% | 1.64% | 2.82% | 0.9834 | 0.9772 |
| SDN [15]: 2018 | 87% | 85.14% | 12.5% | 2.9% | 0.8744 | 0.872 |
| NetConverse [16]: 2018 | 97.1% | 97.05% | 1.6% | 2.9% | 0.9838 | 0.9774 |
| Shallow and Deep Networks [28]: 2017 | 100% 98% Ransomware family classification rate. | 98.01% | 1% | 2% | 0.99 | 0.9950 |
| Bayesian Networks [17]: 2019 | 99.83% | 97.1 % | 2.09% | 0.17% | 0.979 | 0.971 |
| Analysis Framework [18]: 2018 | N/A | N/A | N/A | N/A | 0.9062 | N/A |
| Feature Selection-Based Detection [19]: 2018 | 97.95% | N/A | N/A | 2.05% | N/A | N/A |
| Machine Learning-Based File Entropy Analysis [20]: 2019 | 100% | N/A | N/A | 0% | N/A | N/A |
| Digital DNA-Sequencing [21]: 2020 | 87.9% | 87.9% | 10% | 12.1% | 0.897 | 0.888 |
| Resilient ML [22]: 2019 | 98.90% | 99.89% | 3% | 1.1% | 0.995 | 0.979 |
| API-Sequence-Based Detection [23]: 2019 | 99.53% | 99.35% | N/A | 0.47% | 0.994 | 0.997 |
| Two-Stage Detection [24]: 2020 | 98.8% | 96.65% | 6.93% | 1.2% | N/A | 0.974 |
| Multi-Tier Streaming [25]: 2020 | N/A | N/A | N/A | N/A | N/A | N/A |
| Metric | Calculation | Value |
|---|---|---|
| Detection Rate | TP/(TP+FN) | Correct classification of Ransomware. |
| False Positive Rate (FPR) | FP/(FP+TN) | Benign software classed as Ransomware. |
| False Negative Rate (FNR) | 100-Detection Rate | Ransomware classed as benign. |
Open Issues
6. New Directions/Ransomware Evolution
7. Our Experiments and Results
- Data Entry: WEKA can take dataset inputs in the form of WEKA’s Attribute-Relation File Format(ARFF) format or Comma-Separated-Value (CSV) files.
- Data Mining: The data mining phase includes pre-processing, classification, clustering, association rules, and regression [31].
- Data Evaluation: Data Evaluation assesses the models of the results of the algorithm used.
- Visualisation: WEKA is capable of providing visual representations of the data and the results obtained by the algorithm.
- Storage: Once results are obtained, the data can be stored to be viewed.
8. Concluding Remarks & Future Work
Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| ANN | Artificial Neural Network |
| API | Application Programme Interface |
| AUC | Area Under the Curve |
| AV | Anti Virus |
| BCS | Binary Cuckoo Search |
| BN | Bayesian Network |
| C&C | Command and Control |
| CF-NCF | Class Frequency-Non-Class Frequency |
| CNN | Convolutional Neural Network |
| CS | Cuckoo Search |
| DLL | Dynamic Link Library |
| DNA | Deoxyribonucleic Acid |
| DNS | Domain Name System |
| DT | Decision Trees |
| ECU | Electronic Control Unit |
| FFN | Feed Forward Network |
| FIN | Finished Flag |
| FN | False Negative |
| FP | False Positive |
| GAN | Generative Adversarial Network |
| GTB | Gradient Tree Boosting |
| GWO | Grey Wolf Optimiser |
| HML | Hybrid Machine Learner |
| HTTP | Hypertext Transfer Protocol |
| IDA | Interactive Disassembler |
| IoT | Internet of Things |
| IP | Internet Protocol |
| KNN | K-Nearest Neighbour |
| LDA | Linear Discriminant Analysis |
| LMT | Logistic Model Tree |
| LSTM | Long Short Term Memory |
| MBR | Master Boot Record |
| MLP | Multilayer Perceptron |
| MOGWO | Multi-Objective Grey Wolf Optimiser |
| NB | Naive Bayes |
| NBNS | NetBIOS Name Service |
| NIC | Network Interface Controller |
| OS | Operating System |
| PC | Personal Computer |
| PCAP | Packet Capture |
| PFE | Programmable Forward Engines |
| ReLU | Rectified Linear Units |
| RSA | Rivest–Shamir–Adleman |
| RST | Reset Flag |
| SDN | Software Defined Network |
| SVM | Support Vector Machine |
| TCP | Transmission Control Protocol |
| TN | True Negative |
| TP | True Positive |
| WEKA | Waikato Environment for Knowledge Analysis |
| XGB | XGBoost |
References
- De Groot, J. A History of Ransomware Attack: The Biggest and Worst Ransomware Attack of All Time. 2017. Available online: Https://digitalguardian.com/blog/history-ransomware-attacks-biggest-and-worst-ransomware-attacks-all-time (accessed on 22 November 2018).
- Baig, M.; Zavarsky, P.; Ruhl, R.; Lindskog, D. The study of evasion of packed PE from static detection. In Proceedings of the World Congress on Internet Security (WorldCIS), Guelph, Ontario, 10–12 June 2012; pp. 99–104. [Google Scholar]
- Zakaria, W.Z.A.; Mohd, M.F.A.O.; Ariffin, A.F.M. The Rise of Ransomware. In Proceedings of the 2017 International Conference on Software and e-Business, ICSEB 2017, Hong Kong, 28–30 December 2017; pp. 66–70. [Google Scholar]
- Rieck, K.; Trinius, P.; Willems, C.; Holz, T. Automatic Analysis of Malware Behavior Using Machine Learning. J. Comput. Secur. 2011, 4, 639–668. [Google Scholar] [CrossRef]
- Milosevic, N.; Dehghantanha, A.; Choo, K.K.R. Machine learning aided Android malware classification. Comput. Electr. Eng. 2016, 61, 266–274. [Google Scholar] [CrossRef] [Green Version]
- Anderson, B.; Quist, D.; Neil, J.; Storlie, C.; Lane, T. Graph-based malware detection using dynamic analysis. J. Comput. Virol. 2011, 7, 247–258. [Google Scholar] [CrossRef]
- Kolter, J.Z.; Maloof, M.A. Learning to detect and classify malicious executables in the wild. J. Mach. Learn. Res. 2006, 7, 2721–2744. [Google Scholar]
- Honda, T.; Mukaiyama, K.; Shirai, T.; Ohki, T.; Nishigaki, M. Ransomware Detection Considering User’s Document Editing. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 907–914. [Google Scholar]
- Olenick, D. AI Use in Ransomware Attacks and Sextortion Schemes Top Malwarebytes 2018 Report, Malwarebytes. Available online: Https://www.scmagazine.com/home/security-news/malware/ai-use-in-ransomware-attacks-and-sextortion-schemes-top-malwarebytes-2018-report/ (accessed on 1 October 2019).
- Sgandurra, D.; Munoz-Gonzalez, L.; Mohsen, R.; Lupu, E. Automated Dynamic Analysis of Ransomware: Benefits, Limitations and Use for Detection. Available online: https://arxiv.org/abs/1609.03020 (accessed on 14 December 2020).
- Shaukat, S.; Ribeiro, V. RansomWall: A Layered Defence System against Cryptographic Ransomware Attacks using Machine Learning. In Proceedings of the 10th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 3–7 January 2018; pp. 356–363. [Google Scholar]
- Hasan, M.; Rahman, M. RansHunt: A Support Vector Machines Based Ransomware Analysis Framework with Integrated Feature Set. In Proceedings of the 20th International Conference of Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 22–24 December 2017; pp. 1–7. [Google Scholar]
- Daku, H.; Zavarsky, P.; Malik, Y. Behavioural-Based Classification and Identification of Ransomware Variants Using Machine Learning. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security and Privacy, New York, NY, USA, 1–3 August 2018; pp. 1560–1564. [Google Scholar]
- Takeuchi, Y.; Sakai, K.; Fukumoto, S. Detecting Ransomware using Support Vector Machines. In Proceedings of the 47th International Conference on Parallel Processing Companion, ICPP ’18 Comp, Eugene, OR, USA, 13–16 August 2018; ACM: New York, NY, USA, 2018. [Google Scholar]
- Cusack, G.; Michel, O.; Keller, E. Machine Learning-Based Detection of Ransomware Using SDN. In Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, SDN-NFV Sec’18, Tempe, AZ, USA, 19–21 March; pp. 1–6.
- Alhawi, O.M.K.; Baldwin, J.; Dehghantanha, A. Leveraging Machine Learning Techniques for Windows Ransomware Network Traffic Detection. In Cyber Threat Intelligence. Advances in Information Security; Dehghantanha, A., Conti, M., Dargahi, T., Eds.; Springer: Cham, Germany, 2018; Volume 70. [Google Scholar]
- Almashhadani, A.O.; Kaiiali, M.; Sezer, S.; O’Kane, P. A Multi-Classifier Network-Based Crypto Ransomware Detection System: A Case Study of Locky Ransomware. IEEE Access 2019, 7, 47053–47067. [Google Scholar] [CrossRef]
- Poudel, S.; Subedi, P.; Dasgupta, D. A Framework for Analyzing Ransomware using Machine Learning. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bengaluru, India, 18–21 November 2018. [Google Scholar]
- Chang, J.-C.; Wan, Y.-L.; Chen, R.-J. Feature-Selection-Based Ransomware Detection with Machine Learning of Data Analysis. In Proceedings of the 2018 3rd International Conference on Computer and Communication Systems (ICCCS), Nagoya, Japan, 27–30 April 2018. [Google Scholar]
- Lee, K.; Lee, S.-Y.; Yim, K. Machine Learning Based File Entropy Analysis for Ransomware Detection in Backup Systems. IEEE Access 2019, 7, 110205–110215. [Google Scholar] [CrossRef]
- Khan, F.; McNube, C.; Lakshmana, R.; Kadry, S.; Nam, Y. A Digital DNA Sequencing Engine for Ransomware Detection Using Machine Learning. IEEE Access 2020, 8, 119710–119719. [Google Scholar] [CrossRef]
- Chen, L.; Yang, C.-Y.; Paul, A.; Sahita, R. Towards resilient machine learning for ransomware detection. In Proceedings of the KDD 2019, Anchorage, AK, USA, 4–8 August 2019. [Google Scholar]
- Bae, S.I.; Lee, G.B.; Im, E.G. Ransomware detection using machine learning algorithms. In Concurrency and Computation: Practice and Experience; Wiley: Hoboken, NJ, USA, 2019; Volume 32. [Google Scholar]
- Hwang, J.; Kim, J.; Lee, S. Two-Stage Ransomware Detection Using Dynamic Analysis and Machine Learning Techniques. Wirel. Pers. Commun. 2020, 112, 2597–2609. [Google Scholar] [CrossRef]
- Zuhair, H.; Selamat, A.; Krejcar, O. A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning. Appl. Sci. 2020, 10, 3210. [Google Scholar] [CrossRef]
- Tseng, A.; Chen, Y.; Kao, Y.; Lin, T. Deep Learning for Ransomware Detection. Available online: https://www.semanticscholar.org/paper/Deep-Learning-for-Ransomware-Detection-Aragorn-Yun-chun/cc3a41b37230861cfe429632744e0d1db19256b7 (accessed on 14 December 2020).
- Maniath, S.; Ahok, A.; Poornach, R.P.; Sujadev, V.G.; Sankar, P.; Jan, S. Deep Learning LSTM based Ransomware Detection. In Proceedings of the Recent Developments in Control, Automation & Power Engineering (RDCAPE), Noida, India, 26–27 October 2017; pp. 442–446. [Google Scholar]
- VinayKumar, R.; Soman, K.P.; Senthil Velan, K.K.; Ganorkan, S. Evaluating Shallow and Deep Networks for Ransomware Detection and Classification. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Udupi, India, 13–16 September 2017. [Google Scholar]
- Guarnieri, C.; Tanasi, A.; Bremer, J.; Schloesser, M. Cuckoo Sandbox Book; Cuckoo Foundation: Berlin, Germany, 2018. [Google Scholar]
- Weka 3: Machine Learning Software in Java. 2018. Available online: https://www.cs.waikato.ac.nz/ml/weka/index.html (accessed on 21 November 2018).
- Yanguan, S.; Liu, J.; Shen, J. The Further Development of Weka Base on Positive and Negative Association Rules. In Proceedings of the 2010 International Conference on Intelligent Computation Technology and Automation, Changsha, China, 11–12 May 2010; pp. 811–814. [Google Scholar]
- Alernative.me. Who Uses Scikit-Learn, Scikit-Learn. Available online: https://scikit-learn.org/stable/testimonials/testimonials.html (accessed on 11 October 2019).
- Zimba, A. Malware-Free Intrusion: A Novel Approach to Ransomware Infection Vectors. Int. J. Comput. Sci. Inform. Secur. 2017, 15, 317–325. [Google Scholar]
- CyberPedia. What Is an Exploit Kit. 2018. Available online: Https://www.paloaltonetworks.com/cyberpedia/what-is-an-exploit-kit (accessed on 21 November 2018).
- Liska, A.; Gallo, T. Ransomware: Defending Against Digital Extortion, 1st ed.; O’Reilly, M., Ed.; O’Reilly Media: Sebastopol, CA, USA, 2017. [Google Scholar]
- Sophos Knowledge Base: Ransomware: How an Attack Works. 2016. Available online: Https://community.sophos.com/kb/en-us/124699 (accessed on 21 November 2018).
- Taile, J.P.; Patel, A.D. A Comprehensive Survey: Ransomware Attacks Prevention, Monitoring and Damage Control. Int. J. Res. Sci. Innov. 2017, 4, 2321–2705. [Google Scholar]
- Nassi, N.; Shamir, A.; Elovici, Y. emphOops!...I Think I Scanned a Malware. arXiv 2017, arXiv:1703.07751. [Google Scholar]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory, 2nd ed.; John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Wen, L.I.; Lingdi, P.; Wu, C.; Ming, J. Distributed Bayesian Network Trust Model in Virtual Network. In Proceedings of the 2010 Second International Conference on Networks Security, Wireless Communications and Trusted Computing, Wuhan, China, 24–25 April 2010; pp. 71–74. [Google Scholar]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Abadi, M.; Barham, P.; Chen, J.; Chen, Z.; Davis, A.; Dean, J.; Devin, M.; Ghemawat, S.; Irving, G.; Isard, M. Tensorflow: A system for large-scale machine learning in OSDI. In Proceedings of the 12th USENIX Symposium on Operating Systems Design and Implementation (OSDI ’16), Savannah, GA, USA, 2–4 November 2016; pp. 265–283. [Google Scholar]
- Hinton, G.E.; Srivastava, N.; Krizhevsky, A.; Sutskever, I.; Salakhutdinov, R.R. Improving neural networks by preventing co-adaptation of feature detectors. arXiv 2012, arXiv:1207.0580. [Google Scholar]
- Glorot, X.; Bordes, A.; Bengio, Y. Deep sparse rectifier neural networks. In Proceedings of the Fourteenth International Conference on Artificial Intelligence and Statistics, Fort Lauderdale, FL, USA, 11–13 April 2011; pp. 315–323. [Google Scholar]
- Meola, A. How 5G & IoT Technologies Are Driving the Connected Smart Vehicle Industry. 2020. Available online: Https://www.businessinsider.com/iot-connected-smart-cars?r=US&IR=T (accessed on 1 November 2020).
- Dickson, B. The IoT Ransomware Threat Is More Serious Than you Think. 2019. Available online: Https://www.iotsecurityfoundation.org/the-iot-ransomware-threat-is-more-serious-than-you-think/ (accessed on 1 November 2020).






| Study | Algorithm | Section |
|---|---|---|
| EldeRan [10]: 2016 | Logistic Regression | Section 3.2 |
| RansomWall [11]: 2018 | Gradient Tree Boosting | Section 3.3 |
| RansHunt [12]: 2017 | SVM | Section 3.4 |
| Behavioural-Based [13]: 2018 | J48 Decision Trees | Section 3.5 |
| Support Vector Machines [14]: 2018 | Support Vector Machines | Section 3.6 |
| SDN [15]: 2018 | Random Forests | Section 3.7 |
| NetConverse [16]: 2018 | J48 Decision Tree | Section 3.8 |
| Bayesian networks [17]: 2019 | Bayesian network | Section 3.9 |
| Analysis Framework [18]: 2018 | Random Forest | Section 3.10 |
| Feature Selection-Based Detection [19]: 2018 | J48 Decision Tree | Section 3.11 |
| Machine Learning-Based File Entropy Analysis [20]: 2019 | Entropy Analysis | Section 3.12 |
| Digital DNA Sequencing [21]: 2020 | Random Forests | Section 3.13 |
| Resilient Machine Learning [22]: 2019 | Adversarial Learning | Section 3.14 |
| API Sequence-Based Detection [23]: 2019 | CF-NCF-based Machine Learning | Section 3.15 |
| Two-stage Detection [24]: 2020 | Markov Chains | Section 3.16 |
| Multi-Tier Streaming [25]: 2020 | Hybrid Learner | Section 3.17 |
| Deep Learning [26]: 2016 | Deep Neural Network | Section 4.1 |
| Long Short Term Memory (LSTM) [27]: 2017 | LSTM Neural Network | Section 4.2 |
| Shallow and Deep networks [28]: 2017 | ANNs | Section 4.3 |
| Method | Parameters |
|---|---|
| GTB |
|
| Random Forest |
|
| SVM |
|
| Logistic Regression |
|
| J48 Decision Tree |
|
| Deep Neural Network (10 fold Cross Validation) |
|
| MLP (10 Hidden Layers) |
|
| MLP (20 Hidden Layers) |
|
| Bayesian networks |
|
| Detection | Detection | 13–15 | 16/17 | 13–15 | 16/17 | 13– | 16/ | |
|---|---|---|---|---|---|---|---|---|
| Method | Rate on | on 16/17 | False | False | False | False | 15 | 17 |
| Samples | Samples | Positive | Positive | Negative | Negative | Precision | Precision | |
| Regularised Logistic Regression | 88.6% | 62.3% | 13.6% | 32.1% | 11.4% | 37.3% | 86.4% | 92.8% |
| Gradient Tree Boosting | 94.6% | 77.4% | 5.5% | 19.2% | 5.4% | 22.6% | 95.5% | 96.6% |
| Random Forests | 94.0% | 79.2% | 5.6% | 17.6% | 6.0% | 20.8% | 94.5% | 96.9% |
| SVM | 33.1% | 17.0% | 36.1% | 70.4% | 76.9% | 83.0% | 74.9% | 84.0% |
| J48 Decision Tree | 89.8% | 79.2% | 8.0% | 17.9% | 10.2% | 20.8% | 92.2% | 94.6% |
| Deep Neural Network Using 10 (Fold Cross Validations) | 95.1% | 84.9% | 9.6% | 13.6% | 4.9% | 15.1% | 90.6% | 93.4% |
| Multi-Layer Perceptron (10 Hidden Layers) | 96.4% | 85.0% | 8.0% | 14.0% | 3.6% | 15.0% | 92.0% | 92.2% |
| Multi-Layer Perceptron (20 Hidden Layers) | 95.8% | 58.5% | 9.0% | 35.5% | 4.2% | 41.5% | 91.2% | 90.7% |
| Bayesian Networks | 93.4% | 83.0% | 13.3% | 17.4% | 6.4% | 17.0% | 87.1% | 88.1% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fernando, D.W.; Komninos, N.; Chen, T. A Study on the Evolution of Ransomware Detection Using Machine Learning and Deep Learning Techniques. IoT 2020, 1, 551-604. https://0-doi-org.brum.beds.ac.uk/10.3390/iot1020030
Fernando DW, Komninos N, Chen T. A Study on the Evolution of Ransomware Detection Using Machine Learning and Deep Learning Techniques. IoT. 2020; 1(2):551-604. https://0-doi-org.brum.beds.ac.uk/10.3390/iot1020030
Chicago/Turabian StyleFernando, Damien Warren, Nikos Komninos, and Thomas Chen. 2020. "A Study on the Evolution of Ransomware Detection Using Machine Learning and Deep Learning Techniques" IoT 1, no. 2: 551-604. https://0-doi-org.brum.beds.ac.uk/10.3390/iot1020030