Machine Learning Approaches for User Identity
Share This Topical Collection
Editors
 Dr. Kaushik Roy
Dr. Kaushik Roy
 Dr. Kaushik Roy
Dr. Kaushik Roy
E-Mail
Website
Collection Editor
1. Department of Computer Science, North Carolina A&T State University, Greensboro, NC 27411, USA
2. Center for Trustworthy AI, North Carolina A&T State University, Greensboro, NC 27411, USA
3. Center for Cyber Defense, North Carolina A&T State University, Greensboro, NC 27411, USA
4. Cyber Defense and AI Lab Lab, North Carolina A&T State University, Greensboro, NC 27411, USA
Interests: cyber Identity; cybersecurity; biometrics; data science; machine learning
 Dr. Mustafa Atay
Dr. Mustafa Atay
 Dr. Mustafa Atay
Dr. Mustafa Atay
E-Mail
Website
Collection Editor
Department of Computer Science, Winston-Salem State University, Winston-Salem, NC 27101, USA
Interests: data management; data security; data science; information analysis; information retrieval
 Dr. Ajita Rattani
Dr. Ajita Rattani
 Dr. Ajita Rattani
Dr. Ajita Rattani
E-Mail
Website
Collection Editor
Department of Electrical Engineering and Computer Science, Wichita State University, Wichita 67202, KS, USA
Interests: biometrics; computer vision; image processing; machine learning; deep learning; unmanned aerial vehicles; smart and connected health
Topical Collection Information
Dear Colleagues,
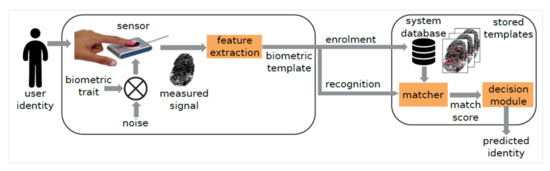
Identity theft intimidates the growth of e-commerce and online financial and government services, and a more comprehensive approach is required to protect personal information. User identity plays a critical role in building a secure, trustworthy and privacy-enhanced identity system. The state-of-the-art approaches used to manage identities cannot endure the increasing number of cyber-attacks from expert criminals. Further research is required on the secure control of identity, enhancing interoperability, and providing end users with more direct control over their digital identity. Recent advances in machine learning and artificial intelligence offer successful solutions in designing identity systems.
The Topical Collection invites original research papers on the applications of machine learning techniques in biometrics, cyber identity, and identity management. Relevant topics include, but are not limited to:
- Machine learning and deep learning techniques in biometrics and cyber identity;
- Machine learning, neural netwoks and artificial intelligence methods in identity management;
- Privacy, convenience and security of identity systems;
- Human behavior analysis and behavior modeling;
- Continous authentication and authorization;
- Identity ecosystem for the Internet of Things (IoT);
- Adversarial attacks on user authentication;
- Adversarial learning;
- Securing the identity claim using blockchain.
Dr. Kaushik Roy
Dr. Mustafa Atay
Dr. Ajita Rattani
Collection Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Future Internet is an international peer-reviewed open access monthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript.
The Article Processing Charge (APC) for publication in this open access journal is 1600 CHF (Swiss Francs).
Submitted papers should be well formatted and use good English. Authors may use MDPI's
English editing service prior to publication or during author revisions.
Keywords
- physiological and behavioral biometrics
- adversarial biometric recognition
- continuous authentication
- biometric data privacy
- social and mobile biometrics
- human behavior analysis and modeling
- identity management
- biometric
- face recognition
- deepfake
- iris recognition
- gait recognition
- fingerprint recognition
- spoofing attacks
- presentation attacks
Published Papers (12 papers)
Open AccessArticle
Personalized Federated Learning with Adaptive Feature Extraction and Category Prediction in Non-IID Datasets
by
Ying-Hsun Lai, Shin-Yeh Chen, Wen-Chi Chou, Hua-Yang Hsu and Han-Chieh Chao
Viewed by 891
Abstract
Federated learning trains a neural network model using the client’s data to maintain the benefits of centralized model training while maintaining their privacy. However, if the client data are not independently and identically distributed (non-IID) because of different environments, the accuracy of the
[...] Read more.
Federated learning trains a neural network model using the client’s data to maintain the benefits of centralized model training while maintaining their privacy. However, if the client data are not independently and identically distributed (non-IID) because of different environments, the accuracy of the model may suffer from client drift during training owing to discrepancies in each client’s data. This study proposes a personalized federated learning algorithm based on the concept of multitask learning to divide each client model into two layers: a feature extraction layer and a category prediction layer. The feature extraction layer maps the input data to a low-dimensional feature vector space. Furthermore, the parameters of the neural network are aggregated with those of other clients using an adaptive method. The category prediction layer maps low-dimensional feature vectors to the label sample space, with its parameters remaining unaffected by other clients to maintain client uniqueness. The proposed personalized federated learning method produces faster learning model convergence rates and higher accuracy rates for the non-IID datasets in our experiments.
Full article
►▼
Show Figures
Open AccessReview
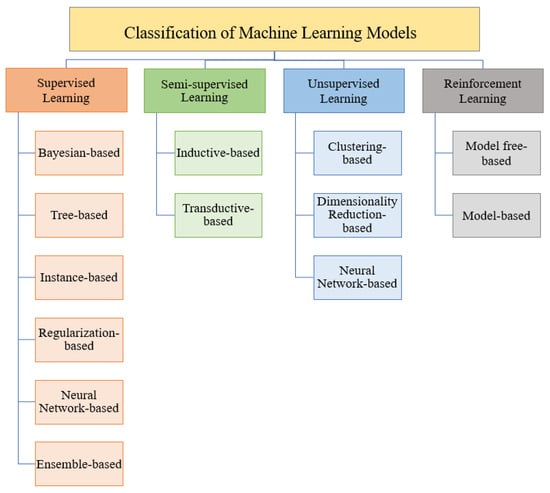
Machine Learning: Models, Challenges, and Research Directions
by
Tala Talaei Khoei and Naima Kaabouch
Cited by 1 | Viewed by 3129
Abstract
Machine learning techniques have emerged as a transformative force, revolutionizing various application domains, particularly cybersecurity. The development of optimal machine learning applications requires the integration of multiple processes, such as data pre-processing, model selection, and parameter optimization. While existing surveys have shed light
[...] Read more.
Machine learning techniques have emerged as a transformative force, revolutionizing various application domains, particularly cybersecurity. The development of optimal machine learning applications requires the integration of multiple processes, such as data pre-processing, model selection, and parameter optimization. While existing surveys have shed light on these techniques, they have mainly focused on specific application domains. A notable gap that exists in current studies is the lack of a comprehensive overview of machine learning architecture and its essential phases in the cybersecurity field. To address this gap, this survey provides a holistic review of current studies in machine learning, covering techniques applicable to any domain. Models are classified into four categories: supervised, semi-supervised, unsupervised, and reinforcement learning. Each of these categories and their models are described. In addition, the survey discusses the current progress related to data pre-processing and hyperparameter tuning techniques. Moreover, this survey identifies and reviews the research gaps and key challenges that the cybersecurity field faces. By analyzing these gaps, we propose some promising research directions for the future. Ultimately, this survey aims to serve as a valuable resource for researchers interested in learning about machine learning, providing them with insights to foster innovation and progress across diverse application domains.
Full article
►▼
Show Figures
Open AccessArticle
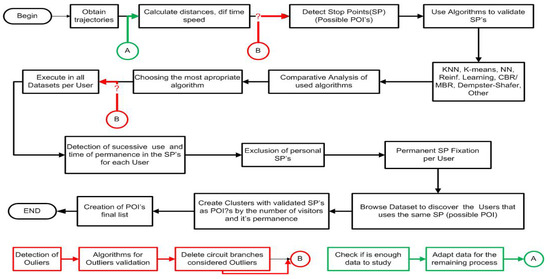
An Analysis of ML-Based Outlier Detection from Mobile Phone Trajectories
by
Francisco Melo Pereira and Rute C. Sofia
Cited by 1 | Viewed by 1381
Abstract
This paper provides an analysis of two machine learning algorithms, density-based spatial clustering of applications with noise (DBSCAN) and the local outlier factor (LOF), applied in the detection of outliers in the context of a continuous framework for the detection of
points of
[...] Read more.
This paper provides an analysis of two machine learning algorithms, density-based spatial clustering of applications with noise (DBSCAN) and the local outlier factor (LOF), applied in the detection of outliers in the context of a continuous framework for the detection of
points of interest (PoI). This framework has as input mobile trajectories of users that are continuously fed to the framework in close to real time. Such frameworks are today still in their infancy and highly required in large-scale sensing deployments, e.g., Smart City planning deployments, where individual anonymous trajectories of mobile users can be useful to better develop urban planning. The paper’s contributions are twofold. Firstly, the paper provides the functional design for the overall PoI detection framework. Secondly, the paper analyses the performance of DBSCAN and LOF for outlier detection considering two different datasets, a dense and large dataset with over 170 mobile phone-based trajectories and a smaller and sparser dataset, involving 3 users and 36 trajectories. Results achieved show that LOF exhibits the best performance across the different datasets, thus showing better suitability for outlier detection in the context of frameworks that perform PoI detection in close to real time.
Full article
►▼
Show Figures
Open AccessArticle
Examining Gender Bias of Convolutional Neural Networks via Facial Recognition
by
Tony Gwyn and Kaushik Roy
Cited by 2 | Viewed by 1694
Abstract
Image recognition technology systems have existed in the realm of computer security since nearly the inception of electronics, and have seen vast improvements in recent years. Currently implemented facial detection systems regularly achieve accuracy rates close to 100 percent. This includes even challenging
[...] Read more.
Image recognition technology systems have existed in the realm of computer security since nearly the inception of electronics, and have seen vast improvements in recent years. Currently implemented facial detection systems regularly achieve accuracy rates close to 100 percent. This includes even challenging environments, such as with low light or skewed images. Despite this near perfect performance, the problem of gender bias with respect to accuracy is still inherent in many current facial recognition algorithms. This bias needs to be addressed to make facial recognition a more complete and useful system. In particular, current image recognition system tend to have poor accuracy concerning underrepresented groups, including minorities and female individuals. The goal of this research is to increase the awareness of this bias issue, as well as to create a new model for image recognition that is gender independent. To achieve this goal, a variety of Convolutional Neural Networks (CNNs) will be tested for accuracy as it pertains to gender bias. In the future, the most accurate CNNs will then be implemented into a new network with the goal of creating a program which is better able to distinguish individuals with a high accuracy, but without gender bias. At present, our research has identified two specific CNNs, VGG-16 and ResNet50, which we believe will be ideal for the creation of this new CNN algorithm.
Full article
►▼
Show Figures
Open AccessArticle
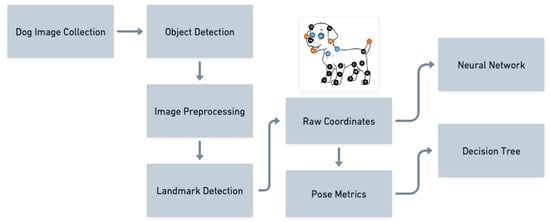
Predicting Dog Emotions Based on Posture Analysis Using DeepLabCut
by
Kim Ferres, Timo Schloesser and Peter A. Gloor
Cited by 16 | Viewed by 10763
Abstract
This paper describes an emotion recognition system for dogs automatically identifying the emotions anger, fear, happiness, and relaxation. It is based on a previously trained machine learning model, which uses automatic pose estimation to differentiate emotional states of canines. Towards that goal, we
[...] Read more.
This paper describes an emotion recognition system for dogs automatically identifying the emotions anger, fear, happiness, and relaxation. It is based on a previously trained machine learning model, which uses automatic pose estimation to differentiate emotional states of canines. Towards that goal, we have compiled a picture library with full body dog pictures featuring 400 images with 100 samples each for the states “Anger”, “Fear”, “Happiness” and “Relaxation”. A new dog keypoint detection model was built using the framework DeepLabCut for animal keypoint detector training. The newly trained detector learned from a total of 13,809 annotated dog images and possesses the capability to estimate the coordinates of 24 different dog body part keypoints. Our application is able to determine a dog’s emotional state visually with an accuracy between 60% and 70%, exceeding human capability to recognize dog emotions.
Full article
►▼
Show Figures
Open AccessArticle
Your Face Mirrors Your Deepest Beliefs—Predicting Personality and Morals through Facial Emotion Recognition
by
Peter A. Gloor, Andrea Fronzetti Colladon, Erkin Altuntas, Cengiz Cetinkaya, Maximilian F. Kaiser, Lukas Ripperger and Tim Schaefer
Cited by 7 | Viewed by 4862
Abstract
Can we really “read the mind in the eyes”? Moreover, can AI assist us in this task? This paper answers these two questions by introducing a machine learning system that predicts personality characteristics of individuals on the basis of their face. It does
[...] Read more.
Can we really “read the mind in the eyes”? Moreover, can AI assist us in this task? This paper answers these two questions by introducing a machine learning system that predicts personality characteristics of individuals on the basis of their face. It does so by tracking the emotional response of the individual’s face through facial emotion recognition (FER) while watching a series of 15 short videos of different genres. To calibrate the system, we invited 85 people to watch the videos, while their emotional responses were analyzed through their facial expression. At the same time, these individuals also took four well-validated surveys of personality characteristics and moral values: the revised NEO FFI personality inventory, the Haidt moral foundations test, the Schwartz personal value system, and the domain-specific risk-taking scale (DOSPERT). We found that personality characteristics and moral values of an individual can be predicted through their emotional response to the videos as shown in their face, with an accuracy of up to 86% using gradient-boosted trees. We also found that different personality characteristics are better predicted by different videos, in other words, there is no single video that will provide accurate predictions for all personality characteristics, but it is the response to the mix of different videos that allows for accurate prediction.
Full article
►▼
Show Figures
Open AccessArticle
A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications
by
Guma Ali, Mussa Ally Dida and Anael Elikana Sam
Cited by 12 | Viewed by 6666
Abstract
With the expansion of smartphone and financial technologies (FinTech), mobile money emerged to improve financial inclusion in many developing nations. The majority of the mobile money schemes used in these nations implement two-factor authentication (2FA) as the only means of verifying mobile money
[...] Read more.
With the expansion of smartphone and financial technologies (FinTech), mobile money emerged to improve financial inclusion in many developing nations. The majority of the mobile money schemes used in these nations implement two-factor authentication (2FA) as the only means of verifying mobile money users. These 2FA schemes are vulnerable to numerous security attacks because they only use a personal identification number (PIN) and subscriber identity module (SIM). This study aims to develop a secure and efficient multi-factor authentication algorithm for mobile money applications. It uses a novel approach combining PIN, a one-time password (OTP), and a biometric fingerprint to enforce extra security during mobile money authentication. It also uses a biometric fingerprint and quick response (QR) code to confirm mobile money withdrawal. The security of the PIN and OTP is enforced by using secure hashing algorithm-256 (SHA-256), a biometric fingerprint by Fast IDentity Online (FIDO) that uses a standard public key cryptography technique (RSA), and Fernet encryption to secure a QR code and the records in the databases. The evolutionary prototyping model was adopted when developing the native mobile money application prototypes to prove that the algorithm is feasible and provides a higher degree of security. The developed applications were tested, and a detailed security analysis was conducted. The results show that the proposed algorithm is secure, efficient, and highly effective against the various threat models. It also offers secure and efficient authentication and ensures data confidentiality, integrity, non-repudiation, user anonymity, and privacy. The performance analysis indicates that it achieves better overall performance compared with the existing mobile money systems.
Full article
►▼
Show Figures
Open AccessArticle
MFCNet: Mining Features Context Network for RGB–IR Person Re-Identification
by
Jing Mei, Huahu Xu, Yang Li, Minjie Bian and Yuzhe Huang
Cited by 1 | Viewed by 3221
Abstract
RGB–IR cross modality person re-identification (RGB–IR Re-ID) is an important task for video surveillance in poorly illuminated or dark environments. In addition to the common challenge of Re-ID, the large cross-modality variations between RGB and IR images must be considered. The existing RGB–IR
[...] Read more.
RGB–IR cross modality person re-identification (RGB–IR Re-ID) is an important task for video surveillance in poorly illuminated or dark environments. In addition to the common challenge of Re-ID, the large cross-modality variations between RGB and IR images must be considered. The existing RGB–IR Re-ID methods use different network structures to learn the global shared features associated with multi-modalities. However, most global shared feature learning methods are sensitive to background clutter, and contextual feature relationships are not considered among the mined features. To solve these problems, this paper proposes a dual-path attention network architecture MFCNet. SGA (Spatial-Global Attention) module embedded in MFCNet includes spatial attention and global attention branches to mine discriminative features. First, the SGA module proposed in this paper focuses on the key parts of the input image to obtain robust features. Next, the module mines the contextual relationships among features to obtain discriminative features and improve network performance. Finally, extensive experiments demonstrate that the performance of the network architecture proposed in this paper is better than that of state-of-the-art methods under various settings. In the all-search mode of the SYSU and RegDB data sets, the rank-1 accuracy reaches 51.64% and 69.76%, respectively.
Full article
►▼
Show Figures
Open AccessArticle
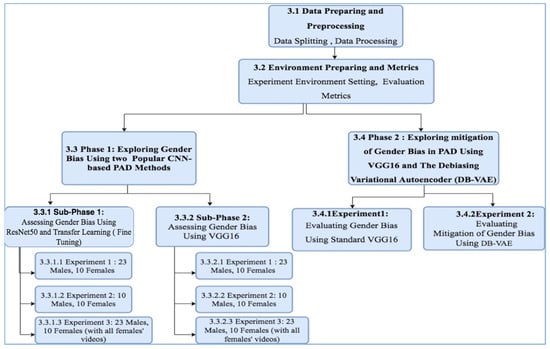
A Study of Gender Bias in Face Presentation Attack and Its Mitigation
by
Norah Alshareef, Xiaohong Yuan, Kaushik Roy and Mustafa Atay
Cited by 4 | Viewed by 3149
Abstract
In biometric systems, the process of identifying or verifying people using facial data must be highly accurate to ensure a high level of security and credibility. Many researchers investigated the fairness of face recognition systems and reported demographic bias. However, there was not
[...] Read more.
In biometric systems, the process of identifying or verifying people using facial data must be highly accurate to ensure a high level of security and credibility. Many researchers investigated the fairness of face recognition systems and reported demographic bias. However, there was not much study on face presentation attack detection technology (PAD) in terms of bias. This research sheds light on bias in face spoofing detection by implementing two phases. First, two CNN (convolutional neural network)-based presentation attack detection models, ResNet50 and VGG16 were used to evaluate the fairness of detecting imposer attacks on the basis of gender. In addition, different sizes of Spoof in the Wild (SiW) testing and training data were used in the first phase to study the effect of gender distribution on the models’ performance. Second, the debiasing variational autoencoder (DB-VAE) (Amini, A., et al., Uncovering and Mitigating Algorithmic Bias through Learned Latent Structure) was applied in combination with VGG16 to assess its ability to mitigate bias in presentation attack detection. Our experiments exposed minor gender bias in CNN-based presentation attack detection methods. In addition, it was proven that imbalance in training and testing data does not necessarily lead to gender bias in the model’s performance. Results proved that the DB-VAE approach (Amini, A., et al., Uncovering and Mitigating Algorithmic Bias through Learned Latent Structure) succeeded in mitigating bias in detecting spoof faces.
Full article
►▼
Show Figures
Open AccessArticle
Movement Analysis for Neurological and Musculoskeletal Disorders Using Graph Convolutional Neural Network
by
Ibsa K. Jalata, Thanh-Dat Truong, Jessica L. Allen, Han-Seok Seo and Khoa Luu
Cited by 9 | Viewed by 2991
Abstract
Using optical motion capture and wearable sensors is a common way to analyze impaired movement in individuals with neurological and musculoskeletal disorders. However, using optical motion sensors and wearable sensors is expensive and often requires highly trained professionals to identify specific impairments. In
[...] Read more.
Using optical motion capture and wearable sensors is a common way to analyze impaired movement in individuals with neurological and musculoskeletal disorders. However, using optical motion sensors and wearable sensors is expensive and often requires highly trained professionals to identify specific impairments. In this work, we proposed a graph convolutional neural network that mimics the intuition of physical therapists to identify patient-specific impairments based on video of a patient. In addition, two modeling approaches are compared: a graph convolutional network applied solely on skeleton input data and a graph convolutional network accompanied with a 1-dimensional convolutional neural network (1D-CNN). Experiments on the dataset showed that the proposed method not only improves the correlation of the predicted gait measure with the ground truth value (speed = 0.791, gait deviation index (GDI) = 0.792) but also enables faster training with fewer parameters. In conclusion, the proposed method shows that the possibility of using video-based data to treat neurological and musculoskeletal disorders with acceptable accuracy instead of depending on the expensive and labor-intensive optical motion capture systems.
Full article
►▼
Show Figures
Open AccessArticle
Fast Flow Reconstruction via Robust Invertible n × n Convolution
by
Thanh-Dat Truong, Chi Nhan Duong, Minh-Triet Tran, Ngan Le and Khoa Luu
Cited by 4 | Viewed by 2117
Abstract
Flow-based generative models have recently become one of the most efficient approaches to model data generation. Indeed, they are constructed with a sequence of invertible and tractable transformations. Glow first introduced a simple type of generative flow using an invertible
[...] Read more.
Flow-based generative models have recently become one of the most efficient approaches to model data generation. Indeed, they are constructed with a sequence of invertible and tractable transformations. Glow first introduced a simple type of generative flow using an invertible
convolution. However, the
convolution suffers from limited flexibility compared to the standard convolutions. In this paper, we propose a novel invertible
convolution approach that overcomes the limitations of the invertible
convolution. In addition, our proposed network is not only tractable and invertible but also uses fewer parameters than standard convolutions. The experiments on CIFAR-10, ImageNet and Celeb-HQ datasets, have shown that our invertible
convolution helps to improve the performance of generative models significantly.
Full article
►▼
Show Figures
Open AccessArticle
Face Recognition Using Popular Deep Net Architectures: A Brief Comparative Study
by
Tony Gwyn, Kaushik Roy and Mustafa Atay
Cited by 26 | Viewed by 3227
Abstract
In the realm of computer security, the username/password standard is becoming increasingly antiquated. Usage of the same username and password across various accounts can leave a user open to potential vulnerabilities. Authentication methods of the future need to maintain the ability to provide
[...] Read more.
In the realm of computer security, the username/password standard is becoming increasingly antiquated. Usage of the same username and password across various accounts can leave a user open to potential vulnerabilities. Authentication methods of the future need to maintain the ability to provide secure access without a reduction in speed. Facial recognition technologies are quickly becoming integral parts of user security, allowing for a secondary level of user authentication. Augmenting traditional username and password security with facial biometrics has already seen impressive results; however, studying these techniques is necessary to determine how effective these methods are within various parameters. A Convolutional Neural Network (CNN) is a powerful classification approach which is often used for image identification and verification. Quite recently, CNNs have shown great promise in the area of facial image recognition. The comparative study proposed in this paper offers an in-depth analysis of several state-of-the-art deep learning based-facial recognition technologies, to determine via accuracy and other metrics which of those are most effective. In our study, VGG-16 and VGG-19 showed the highest levels of image recognition accuracy, as well as F1-Score. The most favorable configurations of CNN should be documented as an effective way to potentially augment the current username/password standard by increasing the current method’s security with additional facial biometrics.
Full article
►▼
Show Figures
Planned Papers
The below list represents only planned manuscripts. Some of these
manuscripts have not been received by the Editorial Office yet. Papers
submitted to MDPI journals are subject to peer-review.
Title: Silently and Continuos Authentication in Mobile Environment
Abstract: Human activity recognition is attracting interest from researchers and developers in recent years due to its immense applications in wide area of human endeavors. The main issue in human behaviour modeling is represented by the diverse nature of human activities and the nature in which they are performed by the individual makes them challenging to recognize. In this paper we propose a method aimed to recognize human activities and detect users using features gathered from accelerometer sensors widespread in wearable and mobile devices. We exploit machine learning aimed to build models with the ability to discriminate between a set of user activities: sitting, sitting down, standing, standing up and walking. Furthermore, we demonstrate that the proposed method is able to distinguish between different users and to identify the user genre. Real-world experiment shows the effectiveness of the proposed solution.