The Relation of Shadow Systems and ERP Systems—Insights from a Multiple-Case Study
Abstract
:1. Introduction
2. The Challenge of Integrating Shadow Systems into ERP Systems
2.1. Literature on ERP Systems and Shadow Systems
2.2. The Dependency of IT Systems in Context of Integration
2.3. Problem Statement
3. Research Method
| Case A | Case B | Case C | |
|---|---|---|---|
| Industry | Insurance | Engineering | Electronics |
| No. of Employees | 1300 | 47,500 | 5500 |
| Analyzed Processes/Departments | Benefits Statements: Private and Corporate Clients | Order Management of a Manufacturing Unit (Sales to Shipment) | Corporate Marketing |
| Interview Partners in | |||
| Business | 2 | 5 | 3 |
| IT | 1 | 5 | 1 |
4. Findings
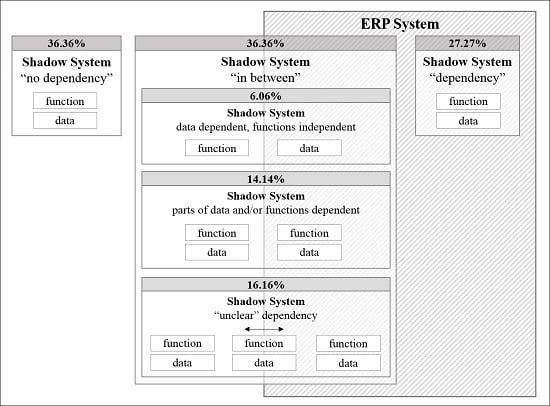
4.1. Dependency Stages of Shadow Systems and ERP Systems in the Case Studies
4.1.1. Dependency
- System A: In Case B, in the team of order processing of special products, we found a Microsoft Access application on an SQL (Structured Query Language) database to create offers for special products. It is associated with another shadow system for technical calculations and a database for orders. The creation of offers is a core functionality of the existing ERP system. Furthermore, the saved data is core data of the ERP system. Because the shadow system shares all its data with the ERP system and the ERP system can provide all the functionalities of the shadow system, we classify these systems as dependent.
- System B: In Case B, in the teams of quality management and spare part processing, the employees used an online portal for retrieving product information. The data are stored as pdf documents. Additionally, the system provides an authorization scheme to distinguish between different roles that have access to different documents. Product information, as well as authorization schemes, are core parts of the formal ERP system. Therefore, this shadow system belongs to this category.
- System C: In Case C, in the team of trade fairs and events, we found a small web based tool for inventory control that only one warehouseman uses. Inventory control is a core functionality of the ERP system as well as the storage of inventory data. Therefore, we classify the two systems as dependent.
4.1.2. No Dependency
- System D: Employees in Case C, in the team of corporate marketing, used a free content management framework for setting up websites about the company in the business unit. As this is not a functionality in an ERP system and the ERP system does not provide the data, we classify them as independent.
- System E: The team of corporate marketing in Case C used a collection of tools for editing graphics and videos. ERP systems provide neither the functionalities nor the data, which puts the shadow system into this category.
- System F: In Case C, the team of trade fairs and events applied software for the development of applications for a specific web application platform. The shadow system also accounts for independent, as the ERP system provides neither the functionality nor the data.
4.1.3. Grey Zone
- System G: In Case B, the team of construction uses an external software to stamp drawings from the ERP system. Therefore, the project from the ERP system is loaded into the software. Afterwards, the team puts the stamp on the drawing. The software shares the data with the ERP system, but the ERP system cannot provide the functionality. Therefore, data is dependent and already loosely integrated. Functionality, however, is not.
- System H: In Case C, the team of corporate design loads data from the ERP system into the database of an online shop. The team takes the data from the ERP system. The data is therefore dependent and integrated via a manual interface, whereas the ERP system cannot provide the functionality of the upload. The functionality therefore is independent, whereas the data is.
- System I: In Case A, the team of benefits for organizations uses benefit and case reports for insurances. The provided summary of benefits in the ERP system is not sufficient. Therefore, each employee uses a tool of end user computing. There, she accumulates data from the ERP system as well as from other information sources, depending on the circumstances.
- System J: In Case B, the team of order processing uses a web application. It uses data from the ERP system but also external order data. It has several functionalities, such as the granting of discounts, planning of dates and the display of milestones for the order. The ERP system can provide all of these functionalities. Hence, all of the functionalities are dependent but only parts of the data.
- System K: The team of corporate marketing in Case C uses a self-developed system, based on ASP (Active Server Pages) to archive documents in different languages. Although the ERP system can provide archiving, it is not its core competency. It shares part of its data with the ERP system, but also uses external sources. Due to the unclear functionality, we cannot make a clear proposition about its dependency on the ERP system.
- System L: The team of order processing of special products in Case B uses a shadow system to describe big projects in different languages. They use building text blocks to combine technical sales and distribution aspects. They use another system for pricing, but with some additional functionalities for customs and big orders. The pricing functionality and the data of distribution are parts of the ERP system. However, the functionality for combining building blocks is not a core competency of the ERP system and we can therefore not clearly define its dependency.

4.2. Discussion
5. Conclusions
Author Contributions
Conflicts of Interest
References
- Smyth, K.; Freeman, J. Blue Prism Rogue IT Survey 2007; Blue Prism Ltd.: London, UK, 2007. [Google Scholar]
- Chejfec, T. Shadow IT Survey v3. 2012. Available online: http://chejfec.com/2012/11/03/Shadow-it-infographic/Shadow-it-survey-v3/ (accessed on 12 October 2015).
- Zimmermann, S.; Rentrop, C. Schatten-IT. HMD Prax. Wirtsch. 2012, 49, 60–68. [Google Scholar] [CrossRef]
- Chua, C.; Storey, V.; Chen, L. Central IT or Shadow IT? Factors Shaping Users’ Decision to Go Rogue with IT. In Proceedings of the 35th International Conference on Information Systems, Auckland, New Zealand, 14–17 December 2014.
- Tambo, T.; Baekgaard, L. Dilemmas in enterprise architecture research and practice from a perspective of feral information systems. In Proceedings of the 17th IEEE Enterprise Distributed Object Computing Conference Workshops, Vancouver, BC, Canada, 9–13 September 2013; pp. 289–295.
- Houghton, L.; Kerr, D.V. A study into the creation of feral information systems as a response to an ERP implementation within the supply chain of a large government-owned corporation. Int. J. Internet Enterp. Manag. 2006, 4, 135–147. [Google Scholar] [CrossRef]
- Behrens, S.; Sedera, W. Why do shadow systems exist after an ERP implementation? Lessons from a case study: Paper 136. In Proceedings of the 8th Pacific Asia Conference on Information Systems, Shanghai, China, 8–11 July 2004; pp. 1712–1726.
- Silva, L.; Fulk, H.K. From disruptions to struggles: Theorizing power in ERP implementation projects. Inf. Organ. 2012, 22, 227–251. [Google Scholar] [CrossRef]
- Boudreau, M.C.; Robey, D. Enacting Integrated Information Technology: A Human Agency Perspective. Organ. Sci. 2005, 16, 3–18. [Google Scholar] [CrossRef]
- Lyytinen, K.; Newman, M. A tale of two coalitions—Marginalising the users while successfully implementing an enterprise resource planning system. Inf. Syst. J. 2015, 25, 71–101. [Google Scholar] [CrossRef]
- Davenport, T.H. Putting the enterprise into the enterprise system. Harv. Bus. Rev. 1998, 76, 121–131. [Google Scholar] [PubMed]
- Hochstein, A.; Zarnekow, R.; Brenner, W. ITIL as common practice reference model for IT service management: Formal assessment and implications for practice. In Proceedings of the International Conference on e-Technology, E-Commerce and E-Service, Hong Kong, China, 29 March–1 April 2005; pp. 704–710.
- Sammon, D.; Adam, F. Towards a model of organisational prerequisites for enterprise-wide systems integration: Examining ERP and data warehousing. J. Enterp. Inf. Manag. 2005, 18, 458–470. [Google Scholar]
- Thatte, S.; Grainger, N. Feral Systems: Why Users Write Them and How They Add Value. In Proceedings of the 5th Pre-ICIS Workshop on ES Research, St. Louis, MO, USA, 11 December 2010; pp. 1–16.
- Sabǎu, G.; Muntean, M.; Bologa, A.R.; Bologa, R. Analysis of Integrated Software Solutions Market for Romanian Higher Education. Econ. Comput. Econ. Cybern. Stud. Res. 2009, 43, 197–202. [Google Scholar]
- Zimmermann, S.; Rentrop, C. On the Emergence of Shadow IT—A Transaction Cost-Based Approach. In Proceedings of the 22nd European Conference on Information Systems, Tel Aviv, Israel, 9–11 June 2014; pp. 1–17.
- Fürstenau, D.; Rothe, H. Shadow IT systems: Discerning the good and the evil. In Proceedings of the 22nd European Conference on Information Systems, Tel Aviv, Israel, 9–11 June 2014.
- Ross, J.W.; Weill, P.; Robertson, D. Enterprise Architecture as Strategy: Creating a Foundation for Business Execution; Harvard Business Press: Cambridge, MA, USA, 2006. [Google Scholar]
- Hoogervorst, J.A.N. Enterprise Architecture: Enabling Integration, Ability and Change. Int. J. Coop. Inf. Syst. 2004, 13, 213–233. [Google Scholar] [CrossRef]
- Themistocleous, M.; Irani, Z.; O’Keefe, R.M.; Paul, R. ERP problems and application integration issues: An empirical survey. In Proceedings of the 34th Hawaii International Conference on System Sciences, Maui, HI, USA, 3–6 January 2001; pp. 1–10.
- Zimmermann, S.; Rentrop, C.; Felden, C. Managing Shadow IT Instances—A Method to Control Autonomous IT Solutions in the Business Departments. In Proceedings of the 20th American Conference on Information Systems, Savannah, Georgia, 7–9 August 2014; pp. 1–12.
- Kerr, D.; Houghton, L.; Burgess, K. Power Relationships that Lead to the Development of Feral Systems. Australas. J. Inf. Syst. 2007, 14, 141–152. [Google Scholar] [CrossRef]
- Wendt, T.; Brigl, B.; Winter, A. Assessing the integration of information system components. In Proceedings of the 1st International Workshop on Interoperability of Heterogeneous Information Systems, Bremen, Germany, 31 October–5 November 2005; ACM: New York, NY, USA, 2005; pp. 55–62. [Google Scholar]
- Ragowsky, A.; Licker, P.; Miller, J.; Gefen, D.; Stern, M. Do Not Call Me Chief Information Officer, But Chief Integration Officer. A Summary of the 2011 Detroit CIO Roundtable. Commun. Assoc. Inf. Syst. 2014, 34, 1333–1346. [Google Scholar]
- Chowanetz, M.; Legner, C.; Thiesse, F. Integration: An Omitted Variable in Information Systems Research: Paper 227. In Proceedings of the European Conference of Information Systems, Barcelona, Spain, 10–13 June 2012.
- Kähkönen, T.; Maglyas, A.; Smolander, K. The Life Cycle Challenge of ERP System Integration. In Proceedings of the Information Systems Development: Transforming Organisations and Society through Information Systems, Varaždin, Croatia, 2–4 September 2014.
- Modol, J. A methodological and conceptual review of inter organizational information systems integration. In Proceedings of the European Conference on Information Systems, Gothenburg, Sweden, 12–14 June 2006; pp. 402–413.
- Scott, S.V.; Wagner, E.L. Networks, negotiations, and new times: The implementation of enterprise resource planning into an academic administration. Inf. Organ. 2003, 13, 285–313. [Google Scholar] [CrossRef]
- Jones, D.; Behrens, S.; Jamieson, K.; Tansley, E. The rise and fall of a shadow system: Lessons for enterprise system implementation: Paper 96. In Proceedings of the 15th Australasian Conference on Information Systems, Hobart, Australia, 1–3 December 2004.
- Behrens, S. Shadow systems: The good, the bad and the ugly. Commun. ACM 2009, 52, 124–129. [Google Scholar] [CrossRef]
- Ignatiadis, I.; Nandhakumar, J. The effect of ERP system workarounds on organizational control: An interpretivist case study. Scand. J. Inf. Syst. 2009, 21, 1–34. [Google Scholar]
- Brehm, L.; Heinzl, A.; Markus, M.L. Tailoring ERP systems: A spectrum of choices and their implications. In Proceedings of the Hawaii International Conference on System Sciences, Maui, HI, USA, 3–6 January 2001; pp. 1–9.
- Kerr, D.; Houghton, L. The dark side of ERP implementations: Narratives of domination, confusion and disruptive ambiguity. Prometheus 2015, 1–15. [Google Scholar] [CrossRef]
- Webster, J.; Watson, R.T. Analyzing the past to prepare for the future: Writing a literature review. Manag. Inf. Syst. Q. 2002, 26, 8–13. [Google Scholar]
- Soh, C.; Kien, S.S.; Tay-Yap, J. Enterprise resource planning: Cultural fits and misfits: Is ERP a universal solution? Commun. ACM 2000, 43, 47–51. [Google Scholar] [CrossRef]
- Land, F. A historical analysis of implementing IS at J. Lyons; Oxford University Press: Oxford, UK, 1999. [Google Scholar]
- Olson, D.L.; Kesharwani, S. Enterprise Information Systems: Contemporary Trends and Issues; World Scientific: Singapore, 2010. [Google Scholar]
- Kien, S.; Lian, Y. Building Enterprise Integration Through Enterprise Resource Planning Systems: Paper 169. In Proceedings of the International Conference on Information Systems, Phoenix, AZ, USA, 14 December 2009.
- Hanseth, O.; Lyytinen, K. Theorizing about the design of information infrastructures: Design kernel theories and principles. Sprouts 2004, 4, 207–241. [Google Scholar]
- Lin, D. An information-theoretic definition of similarity. In Proceedings of the 15th International Conference on Machine Learning, Madison, WI, USA, 24–27 July 1998.
- Mertens, P. Integrierte Informationsverarbeitung 1-Operative Systeme in der Industrie 16. Überarbeitete Auflage; Gabler: Wiesbaden, Germany, 2007. [Google Scholar]
- Linß, H. Integrationsabhängige Nutzeffekte der Informationsverarbeitung: Vorgehensmodell und Empirische Ergebnisse; Dt. Univ.-Verlag: Wiesbaden, Germany, 1995. [Google Scholar]
- Rosemann, M. Gegenstand und Aufgaben des Integrationsmanagements. Integrationsmanagement 1999, 5, 5–18. [Google Scholar]
- Heilmann, H. Integration: Ein zentraler Begriff der Wirtschaftsinformatik im Wandel der Zeit. HMD 1989, 26, 46–58. [Google Scholar]
- Ruh, W.A.; Maginnis, F.X.; Brown, W.J. Enterprise Application Integration: A Wiley Tech Brief; Wiley: Hoboken, NJ, USA, 2002. [Google Scholar]
- Vernadat, F.B. Enterprise Modelling and Integration: From Fact Modelling to Enterprise Interoperability. In IFIP—The International Federation for Information Processing; Springer US: New York, NY, USA, 2003; pp. 25–33. [Google Scholar]
- Giachetti, R.E. A framework to review the information integration of the enterprise. Int. J. Prod. Res. 2004, 42, 1147–1166. [Google Scholar] [CrossRef]
- Frank, U. Integration—Reflections on a Pivotal Concept for Designing and Evaluating Information Systems. In Lecture Notes in Business Information Processing; Springer: Berlin, Germany; Heidelberg, Germany, 2008; pp. 111–122. [Google Scholar]
- Kerr, D.V.; Houghton, L. Just in time or Just in case: A Case study on the impact of context in ERP implementations. Australa. J. Inf. Syst. 2010, 16. [Google Scholar] [CrossRef]
- Le Roux, D.B. Misfit and Reinvention in Information Systems: The Case of a South African Metropolitan Municipality. In Proceedings of the Southern African Institute for Computer Scientist and Information Technologists Annual Conference, Centurion, South Africa, 30 September–1 October 2014; pp. 217–228.
- Robey, D.; Ross, J.W.; Boudreau, M.C. Learning to implement enterprise systems: An exploratory study of the dialectics of change. J. Manag. Inf. Syst. 2002, 19, 17–46. [Google Scholar]
- Strong, D.M.; Volkoff, O. A roadmap for enterprise system implementation. Computer 2004, 37, 22–29. [Google Scholar] [CrossRef]
- Oliver, D.; Romm, C. Justifying enterprise resource planning adoption. J. Inf. Technol. 2002, 17, 199–213. [Google Scholar] [CrossRef]
- Kallinikos, J. Deconstructing information packages: Organizational and behavioural implications of ERP systems. Inf. Technol. People 2004, 17, 8–30. [Google Scholar] [CrossRef] [Green Version]
- Kulkarni, A.; Williams, E.; Grimaila, M.R. Mitigating Security Risks for End User Computing Application (EUCA) Data. In Proceedings of the IEEE 2nd International Conference on Social Computing (SocialCom), Minneapolis, MN, USA, 20–22 August 2010; pp. 1171–1176.
- Kerr, D.; Houghton, L. Feral Systems: The Likely Effects on Business Analytics Functions in an Enterprise Resource Planning System Environment. In Proceedings of the 19th Australasian Conference on Information Systems, Christchurch, New Zealand, 3–5 December 2008; pp. 484–491.
- Thatte, S.; Grainger, N.; McKay, J. Feral practices. In Proceedings of the 23rd Australasian Conference on Information Systems, Geelong, Victoria, Australia, 3–5 December 2012; pp. 1–10.
- Lee, A.S. Case studies as natural experiments. Hum. Relat. 1989, 42, 117–137. [Google Scholar] [CrossRef]
- Yin, R.K. Case Study Research: Design and Methods; Sage Publications: Thousand Oaks, CA, USA, 2013. [Google Scholar]
- Benbasat, I.; Goldstein, D.K.; Mead, M. The case research strategy in studies of information systems. MIS Q. 1987, 369–386. [Google Scholar] [CrossRef]
- Herriott, R.E.; Firestone, W.A. Multisite qualitative policy research: Optimizing description and generalizability. Educ. Res. 1983, 14–19. [Google Scholar] [CrossRef]
- Lee, A.S. A Scientific Methodology for MIS Case Studies. MIS Q. 1989, 13, 33–50. [Google Scholar] [CrossRef]
- Eisenhardt, K.M. Building Theories from Case Study Research. Acad. Manag. Rev. 1989, 14, 532–550. [Google Scholar]
- Myers, M.D.; Newman, M. The qualitative interview in IS research: Examining the craft. Inf. Organ. 2007, 17, 2–26. [Google Scholar] [CrossRef]
- Corbin, J.; Strauss, A. Basics of Qualitative Research: Techniques and Procedures for Developing Grounded Theory; Sage Publications: Thousand Oaks, CA, USA, 2014. [Google Scholar]
- Flick, U. An Introduction to Qualitative Research; Sage: Thousand Oaks, CA, USA, 2009. [Google Scholar]
- Giacomazzi, F.; Panella, C.; Pernici, B.; Sansoni, M. Information systems integration in mergers and acquisitions: A normative model. Inf. Manag. 1997, 32, 289–302. [Google Scholar] [CrossRef]
- Carton, F.; Adam, F. Towards a model for determining the scope of ICT integration in the enterprise: The case of Enterprise Resource Planning (ERP) systems. In Proceedings of the 3rd European Conference on Information Management and Evaluation, Gothenburg, Sweden, 17–18 September 2009.
- Wagner, E.L.; Newell, S.; Piccoli, G. Understanding Project Survival in an ES Environment: A Sociomaterial Practice Perspective. J. Assoc. Inf. Syst. 2010, 11, 276–297. [Google Scholar]
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huber, M.; Zimmermann, S.; Rentrop, C.; Felden, C. The Relation of Shadow Systems and ERP Systems—Insights from a Multiple-Case Study. Systems 2016, 4, 11. https://0-doi-org.brum.beds.ac.uk/10.3390/systems4010011
Huber M, Zimmermann S, Rentrop C, Felden C. The Relation of Shadow Systems and ERP Systems—Insights from a Multiple-Case Study. Systems. 2016; 4(1):11. https://0-doi-org.brum.beds.ac.uk/10.3390/systems4010011
Chicago/Turabian StyleHuber, Melanie, Stephan Zimmermann, Christopher Rentrop, and Carsten Felden. 2016. "The Relation of Shadow Systems and ERP Systems—Insights from a Multiple-Case Study" Systems 4, no. 1: 11. https://0-doi-org.brum.beds.ac.uk/10.3390/systems4010011