Realizing the Role of Permissioned Blockchains in a Systems Engineering Lifecycle
Abstract
:1. Introduction
- (i)
- data access and control;
- (ii)
- managing vast volumes of information and data, and;
- (iii)
- using information and data effectively in an SE development process.
2. Current Uses of Blockchain Technology
2.1. Financial Applications
2.2. Data Management
2.3. Internet of Things (IoT)
2.4. Governance
2.5. Integrity Verification
2.6. Supply Chain Management
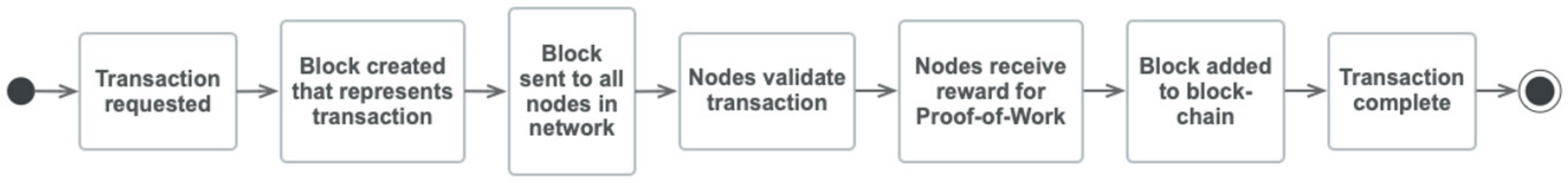
3. Blockchain Technology and Permissioned Blockchains
- Node—user or computer within the blockchain (each has an independent copy of the entire blockchain ledger stored on personal computer).
- Transaction—these are the building blocks of the blockchain and are data records, information, etc.).
- Block—a data structure used for keeping a set of transactions, which is distributed to all nodes in the network.
- Chain—a sequence of blocks in a specific order according to the time of transaction.
- Miners—specific nodes, which perform the block verification process before adding anything to the blockchain structure.
- Consensus (consensus protocol)—a set of rules and arrangements to carry out blockchain operations.
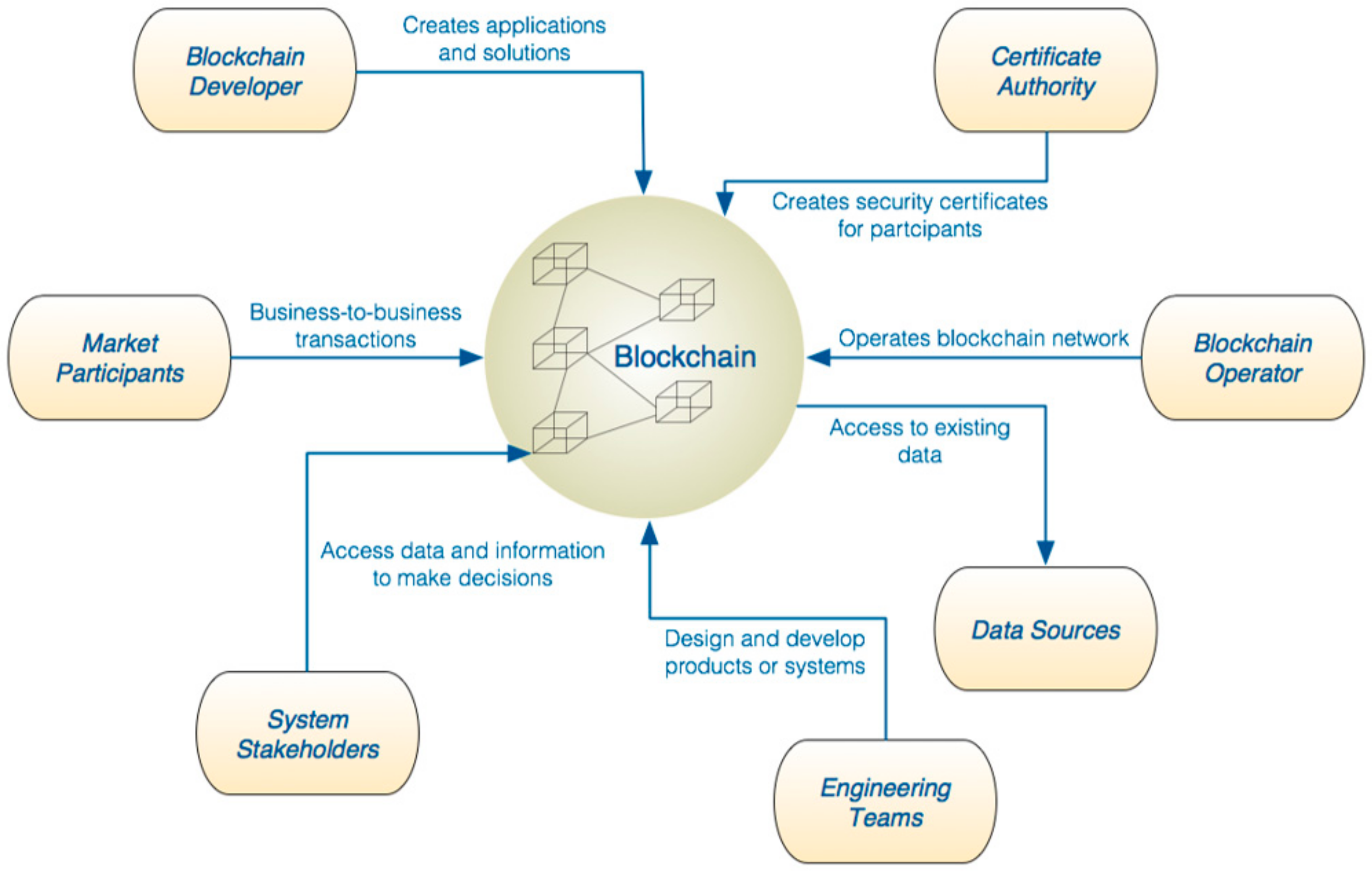
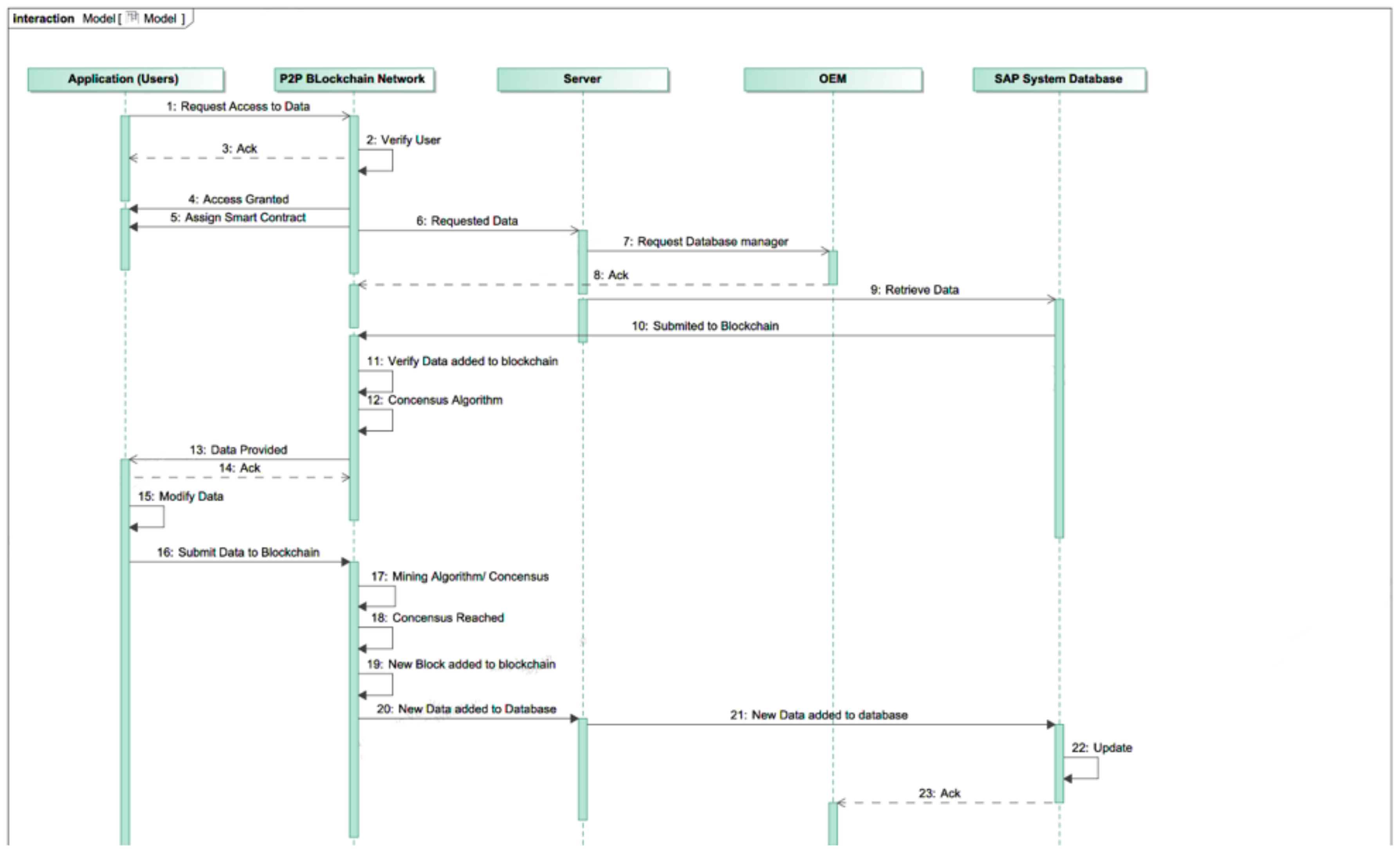
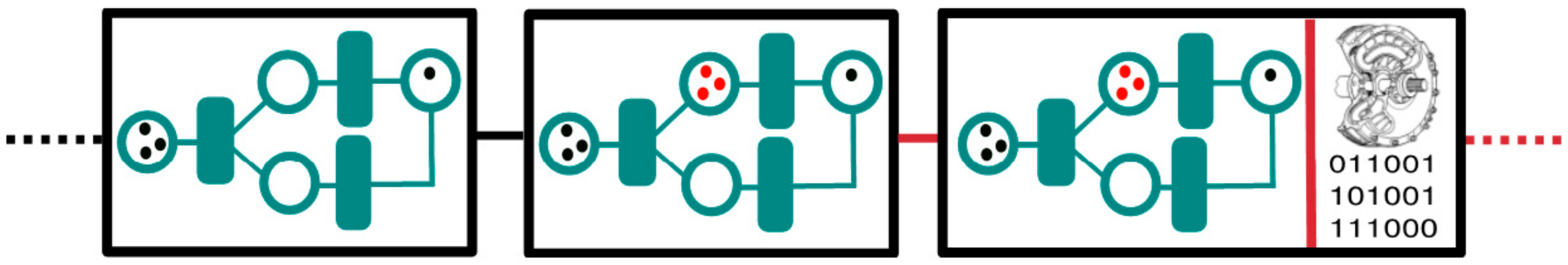
4. The Role of Permissioned Blockchains in the Systems Engineering Lifecycle
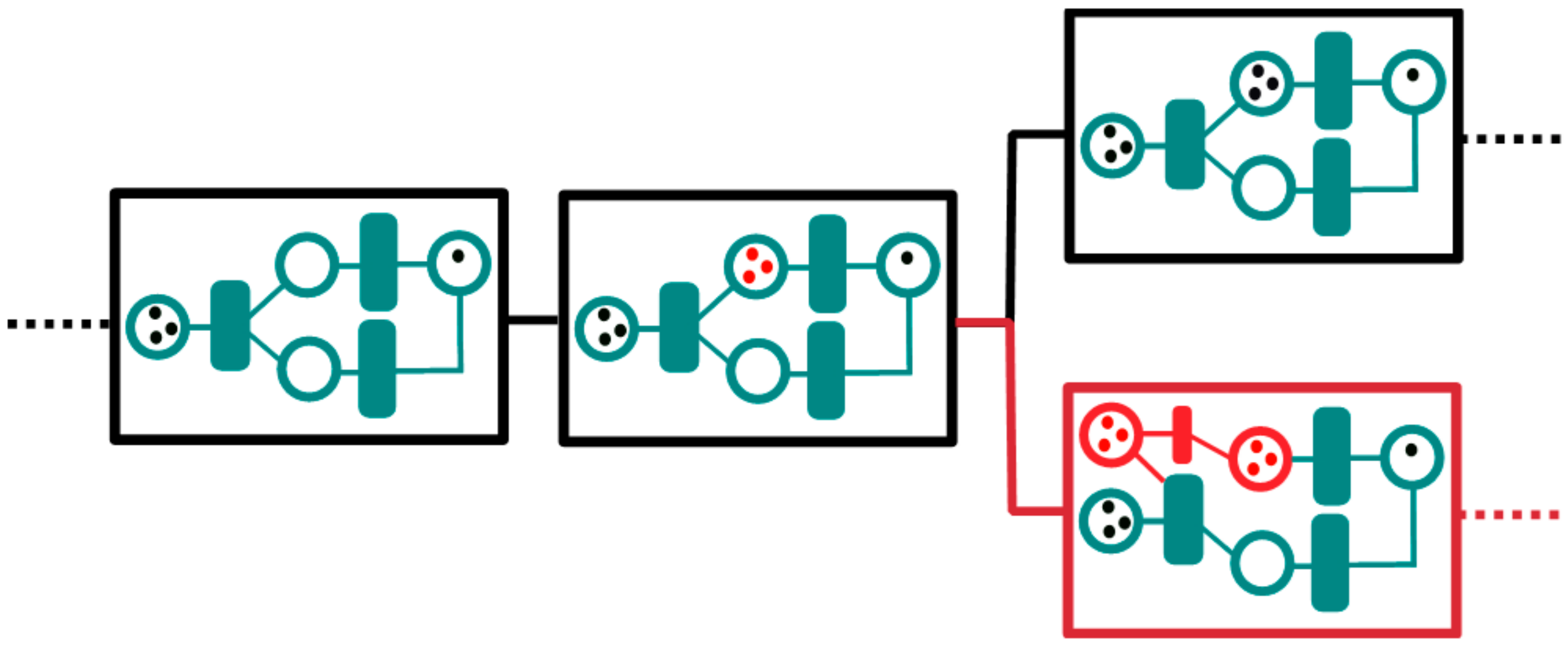
5. Architecture Patterns for Permissioned Blockchain Integration
Example Architecture: Blockchain Forking
6. Discussion on Implementation Challenges of Permissioned Blockchains in SE Lifecycle
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Raz, A.K.; Kenley, C.R.; DeLaurentis, D.A. System architecting and design space characterization. Syst. Eng. 2018, 21, 227–242. [Google Scholar] [CrossRef]
- Maier, M.W. Architecting Principles for Systems-of-Systems. Syst. Eng. 1998, 1, 267–284. [Google Scholar] [CrossRef]
- Dahmann, J.; Rebovich, G.; Lane, J.; Lowry, R.; Baldwin, K. An implementers’ view of systems engineering for systems of systems. In Proceedings of the 2011 IEEE International Systems Conference, Montreal, QC, Canada, 4–7 April 2011; IEEE: Washington, DC, USA, 2011; pp. 212–217. [Google Scholar] [CrossRef]
- Jin, T.; Zhang, X.; Liu, Y.; Lei, K. BlockNDN: A bitcoin blockchain decentralized system over named data networking. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; IEEE: Washington, DC, USA, 2017; pp. 75–80. [Google Scholar] [CrossRef]
- Hause, M. The Unified Profile for DoDAF/MODAF (UPDM) enabling systems of systems on many levels. In Proceedings of the 2010 IEEE International Systems Conference, San Diego, CA, USA, 5–8 April 2010; Institute of Electrical and Electronics Engineers (IEEE): Washington, DC, USA, 2010; pp. 426–431. [Google Scholar]
- Madni, A.M.; Purohit, S. Economic Analysis of Model-Based Systems Engineering. Systems 2019, 7, 12. [Google Scholar] [CrossRef] [Green Version]
- Holt, J.; Perry, S.; Payne, R.; Bryans, J.; Hallerstede, S.; Hansen, F.O. A Model-Based Approach for Requirements Engineering for Systems of Systems. IEEE Syst. J. 2015, 9, 252–262. [Google Scholar] [CrossRef] [Green Version]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 29 February 2019).
- Li, Z.; Barenji, A.V.; Huang, G.Q. Toward a blockchain cloud manufacturing system as a peer to peer distributed network platform. Robot. Comput. Manuf. 2018, 54, 133–144. [Google Scholar] [CrossRef]
- Muzammal, M.; Qu, Q.; Nasrulin, B. Renovating blockchain with distributed databases: An open source system. Future Gener. Comput. Syst. 2019, 90, 105–117. [Google Scholar] [CrossRef]
- Wang, Y.; Cai, S.; Lin, C.; Chen, Z. Study of Blockchains’s Consensus Mechanism Based on Credit. IEEE Access 2019, 7, 10224–10231. [Google Scholar] [CrossRef]
- Baena, F.; Guarin, A.; Mora, J.; Sauza, J.; Retat, S. Learning Factory: The Path to Industry 4.0. Procedia Manuf. 2017, 9, 73–80. [Google Scholar] [CrossRef]
- Qin, J.; Liu, Y.; Grosvenor, R. A Categorical Framework of Manufacturing for Industry 4.0 and Beyond. Procedia CIRP 2016, 52, 173–178. [Google Scholar] [CrossRef] [Green Version]
- Ahuett-Garza, H.; Kurfess, T. A brief discussion on the trends of habilitating technologies for Industry 4.0 and Smart manufacturing. Manuf. Lett. 2018, 15, 60–63. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain Challenges and Opportunities: A Survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Lewis, A. The Basics of Bitcoins and Blockchains: An Introduction to Cryptocurrencies and the Technology that Powers Them; Mango Media: London, UK, 2018; pp. 1–27. [Google Scholar]
- Crosby, M.; Nachiappan; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain Technology: Beyond Bitcoin. Appl. Innov. Rev. 2016, 20, 16. [Google Scholar]
- Zhao, J.L.; Fan, S.; Yan, J. Overview of business innovations and research opportunities in blockchain and introduction to the special issue. Financ. Innov. 2016, 2, 28. [Google Scholar] [CrossRef] [Green Version]
- CoinMarketCap. 2019. Available online: https://coinmarketcap.com/ (accessed on 21 February 2019).
- Nguyen, Q.K. Blockchain—A Financial Technology for Future Sustainable Development. In Proceedings of the 3rd International Conference on Green Technology and Sustainable Development (GTSD), Kaohsiung, Taiwan, 24–25 November 2016; pp. 51–54. [Google Scholar] [CrossRef]
- Fanning, K.; Centers, D.P. Blockchain and Its Coming Impact on Financial Services. J. Corp. Account. Financ. 2016, 27, 53–57. [Google Scholar] [CrossRef]
- Yamada, Y.; Nakajima, T.; Sakamoto, M. Blockchain-LI: A Study on Implementing Activity-Based Micro-Pricing using Cryptocurrency Technologies. In Proceedings of the 14th International Conference on Advances in Mobile Computing and Multi Media, Singapore, 28–30 November 2017; pp. 203–207. [Google Scholar]
- Beck, R.; Czepluch, J.S.; Lollike, N.; Malone, S. Blockchain—The Gateway to Trust-Free Cryptographic Transactions. In Proceedings of the 24th European Conference on Information Systems (ECIS), Istanbul, Turkey, 12–15 June 2016. [Google Scholar]
- Wu, T.; Liang, X. Exploration and practice of inter-bank application based on blockchain. In Proceedings of the 12th International Conference on Computer Science and Education (ICCSE), Houston, TX, USA, 22–25 August 2017; pp. 219–224. [Google Scholar] [CrossRef]
- Cocco, L.; Pinna, A.; Marchesi, M. Banking on Blockchain: Costs Savings Thanks to the Blockchain Technology. Future Internet 2017, 9, 25. [Google Scholar] [CrossRef] [Green Version]
- Gazali, H.M.; Hassan, R.; Nor, R.M.; Rahman, H.M. Re-inventing PTPTN study loan with blockchain and smart contracts. In Proceedings of the 8th International Conference on Information Technology (ICIT), Lintong Qu, China, 25–27 December 2017; pp. 751–754. [Google Scholar] [CrossRef]
- Hwang, G.-H.; Chen, P.-H.; Lu, C.-H.; Chiu, C.; Lin, H.-C.; Jheng, A.-J. InfiniteChain: A Multi-Chain Architecture with Distributed Auditing of Sidechains for Public Blockchains; Springer Science and Business Media LLC: Cham, Switzerland, 2018; pp. 47–60. [Google Scholar]
- Ma, Z.; Huang, W.; Bi, W.; Gao, H.; Wang, Z. A master-slave blockchain paradigm and application in digital rights management. China Commun. 2018, 15, 174–188. [Google Scholar] [CrossRef]
- Wang, B.; Chen, S.; Yao, L.; Liu, B.; Xu, X.; Zhu, L. A Simulation Approach for Studying Behavior and Quality of Blockchain Networks. Lect. Notes Comput. Sci. 2018, 10974 LNCS, 18–31. [Google Scholar]
- Zhu, L.; Wu, Y.; Gai, K.; Choo, K.-K.R. Controllable and trustworthy blockchain-based cloud data management. Future Gener. Comput. Syst. 2019, 91, 527–535. [Google Scholar] [CrossRef]
- Neisse, R.; Steri, G.; Nai-Fovino, I. A Blockchain-based Approach for Data Accountability and Provenance Tracking. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017. [Google Scholar]
- Wang, J.; Li, M.; He, Y.; Li, H.; Xiao, K.; Wang, C. A Blockchain Based Privacy-Preserving Incentive Mechanism in Crowdsensing Applications. IEEE Access 2018, 6, 17545–17556. [Google Scholar] [CrossRef]
- Do, H.G.; Ng, W.K. Blockchain-Based System for Secure Data Storage with Private Keyword Search. In Proceedings of the 2017 IEEE 13th World Congress on Services (SERVICES), Honolulu, HI, USA, 25–30 June 2017; pp. 90–93. [Google Scholar]
- Jiang, P.; Guo, F.; Liang, K.; Lai, J.; Wen, Q. Searchain: Blockchain-based private keyword search in decentralized storage. Future Gener. Comput. Syst. 2020, 107, 781–792. [Google Scholar] [CrossRef]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Jo, B.W.; Khan, R.M.A.; Lee, Y.-S. Hybrid Blockchain and Internet-of-Things Network for Underground Structure Health Monitoring. Sensors 2018, 18, 4268. [Google Scholar] [CrossRef] [Green Version]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Abbas, H.; Ni, W. Blockchain’s adoption in IoT: The challenges, and a way forward. J. Netw. Comput. Appl. 2018, 125, 251–279. [Google Scholar] [CrossRef]
- Kshetri, N. Can Blockchain Strengthen the IoT? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef] [Green Version]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A Decentralized Privacy-Preserving Healthcare Blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fabiano, N. The Internet of Things ecosystem: The blockchain and privacy issues. The challenge for a global privacy standard. In Proceedings of 2017 International Conference on Internet of Things for the Global Community (IoTGC), Funchal, Portugal, 10–13 July 2017; IEEE: Washington, DC, USA, 2017; Volume 2060, pp. 1–7. [Google Scholar]
- Patel, D.; Shah, K.; Shanbhag, S.; Mistry, V. Towards Legally Enforceable Smart Contracts. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2018; Volume 10974, pp. 153–165. [Google Scholar]
- Gatteschi, V.; Lamberti, F.; DeMartini, C.; Pranteda, C.; Santamaria, V. To Blockchain or Not to Blockchain: That Is the Question. IT Prof. 2018, 20, 62–74. [Google Scholar] [CrossRef]
- Boudguiga, A.; Bouzerna, N.; Granboulan, L.; Olivereau, A.; Quesnel, F.; Roger, A.; Sirdey, R. Towards Better Availability and Accountability for IoT Updates by Means of a Blockchain; IEEE: Paris, France, 2017. [Google Scholar]
- Ølnes, S.; Ubacht, J.; Janssen, M. Blockchain in government: Benefits and implications of distributed ledger technology for information sharing. Gov. Inf. Q. 2017, 34, 355–364. [Google Scholar] [CrossRef] [Green Version]
- Dutch Government Blockchain Pilot Projects. Available online: https://www.blockchainpilots.nl/results. (accessed on 27 February 2019).
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Dupont, Q. Blockchain Identities: Notational Technologies for Control and Management of Abstracted Entities. Metaphilosophy 2017, 48, 634–653. [Google Scholar] [CrossRef]
- Jamthagen, C.; Hell, M. Blockchain-Based Publishing Layer for the Keyless Signing Infrastructure. In Proceedings of the 2016 Intl IEEE Conferences on Ubiquitous Intelligence & Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People, and Smart World Congress (UIC/ATC/ScalCom/CBDCom/IoP/SmartWorld), Toulouse, France, 18–21 July 2016; IEEE: Washington, DC, USA, 2016; pp. 374–381. [Google Scholar]
- Xu, R.; Zhang, L.; Zhao, H.; Peng, Y. Design of Network Media’s Digital Rights Management Scheme Based on Blockchain Technology. In Proceedings of the 2017 IEEE 13th International Symposium on Autonomous Decentralized System (ISADS), Bangkok, Thailand, 22–24 March 2017; IEEE: Washington, DC, USA, 2017; pp. 128–133. [Google Scholar]
- Zikratov, I.; Kuzmin, A.; Akimenko, V.; Niculichev, V.; Yalansky, L. Ensuring data integrity using blockchain technology. In Proceedings of the 20th Conference of Open Innovations Association (FRUCT), St. Petersburg, Russia, 3–7 April 2017. [Google Scholar]
- Bhowmik, D.; Feng, T. The multimedia blockchain: A distributed and tamper-proof media transaction framework. Int. Conf. Digit. Signal Process. DSP 2017, 1–5. [Google Scholar] [CrossRef]
- Fujimura, S.; Watanabe, H.; Nakadaira, A.; Yamada, T.; Akutsu, A.; Kishigami, J.J. BRIGHT: A concept for a decentralized rights management system based on blockchain. In Proceedings of the 2015 IEEE 5th International Conference on Consumer Electronics—Berlin (ICCE-Berlin), Berlin, Germany, 6–9 September 2015; IEEE: Washington, DC, USA, 2015; pp. 345–346. [Google Scholar]
- Kishigami, J.; Fujimura, S.; Watanabe, H.; Nakadaira, A.; Akutsu, A. The Blockchain-Based Digital Content Distribution System. In Proceedings of the 2015 IEEE Fifth International Conference on Big Data and Cloud Computing, Dalian, China, 26–28 August 2015; IEEE: Washington, DC, USA, 2015; pp. 187–190. [Google Scholar]
- Kshetri, N. 1 Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inf. Manag. 2018, 39, 80–89. [Google Scholar] [CrossRef] [Green Version]
- Min, H. Blockchain technology for enhancing supply chain resilience. Bus. Horiz. 2019, 62, 35–45. [Google Scholar] [CrossRef]
- Ahram, T.; Sargolzaei, A.; Daniels, J.; Amaba, B. Blockchain technology innovations. In Proceedings of the 2017 IEEE Technology & Engineering Management Conference (TEMSCON), Santa Clara, CA, USA, 8–10 June 2017; pp. 137–141. [Google Scholar]
- Casado-Vara, R.; Prieto, J.; De La Prieta, F.; Corchado, J.M. How blockchain improves the supply chain: Case study alimentary supply chain. Procedia Comput. Sci. 2018, 134, 393–398. [Google Scholar] [CrossRef]
- Leng, K.; Bi, Y.; Jing, L.; Fu, H.-C.; Van Nieuwenhuyse, I. Research on agricultural supply chain system with double chain architecture based on blockchain technology. Futur. Gener. Comput. Syst. 2018, 86, 641–649. [Google Scholar] [CrossRef]
- IBM. IBM-Zero to Blockchain. Available online: http://www.redbooks.ibm.com/abstracts/crse0401.html?Open&mhq=blockchain&mhsrc=ibmsearch_a (accessed on 1 March 2019).
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Towards an Optimized BlockChain for IoT. In Proceedings of the Second International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–21 April 2017; Association for Computing Machinery (ACM): New York, NY, USA, 2017; pp. 173–178. [Google Scholar]
- Polim, R.; Hu, Q.; Kumara, S. Blockchain in megacity logistics. In Proceedings of the 67th Annual Conference and Expo of the Institute of Industrial Engineers 2017, Pittsburgh, PA, USA, 20–23 May 2017; pp. 1589–1594. [Google Scholar]
- O’Leary, D.E.M. Configuring Blockchain Architectures for Transaction Information in Blockchain Consortiums: The Case of Accounting and Supply Chain Systems. Intell. Syst. Account. Financ. Manag. 2017, 24, 138–147. [Google Scholar] [CrossRef]
- Tsai, W.-T.; Feng, L.; Zhang, H.; You, Y.; Wang, L.; Zhong, Y. Intellectual-Property Blockchain-Based Protection Model for Microfilms. In Proceedings of the 2017 IEEE Symposium on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 6–9 April 2017; IEEE: Washington, DC, USA, 2017; pp. 174–178. [Google Scholar]
- Madhwal, Y.; Panfilov, P.B.; Katalinic, B. Blockchain And Supply Chain Management: Aircrafts’ Parts’ Business Case. In Proceedings of the 29th International DAAAM Symposium 2017, Vienna, Austria, 11 November 2017; DAAAM International: Vienna, Austria, 2017; pp. 1051–1056. [Google Scholar]
- Decentralized Manufacturing. CIRP Encyclopedia of Production Engineering; Springer: Berlin/Heidelberg, Germany, 2014; 363p. [Google Scholar]
- Vukolić, M. Rethinking Permissioned Blockchains. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts—BCC ’17, Abu Dhabi, UAE, 2 April 2017; Association for Computing Machinery (ACM): New York, NY, USA, 2017; pp. 3–7. [Google Scholar]
- Hardjono, T.; Pentland, A.S. Verifiable Anonymous Identities and Access Control in Permissioned Blockchains. arXiv 2016, arXiv:1903.04584. [Google Scholar]
- Wüst, K.; Gervais, A. Do you need a Blockchain? IACR Cryptol. 2017, 1–7. [Google Scholar] [CrossRef]
- Tang, H.; Shi, Y.; Dong, P. Public blockchain evaluation using entropy and TOPSIS. Expert Syst. Appl. 2019, 117, 204–210. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in internet of things: Challenges and Solutions. arXiv 2016, arXiv:1608.05187. [Google Scholar]
- Duan, J.; Patel, M. Blockchain in Global Trade. Lect. Notes Comp. Sci. 2018, 10974 LNCS, 293–296. [Google Scholar]
- Hawlitschek, F.; Notheisen, B.; Teubner, T. The limits of trust-free systems: A literature review on blockchain technology and trust in the sharing economy. Electron. Commer. Res. Appl. 2018, 29, 50–63. [Google Scholar] [CrossRef]
- Ross, M.; Hastings, D.E. The tradespace exploration paradigm. INCOSE Int. Symp. 2005, 2005, 13. [Google Scholar]
- Ganne, E. Can Blockchain Revolutionize International Trade? World Trade Organization (WTO): Geneva, Switzerland, 2018. [Google Scholar]
- BlockchainHub. Blockchains & Distributed Ledger Technologies. 2015. Available online: https://blockchainhub.net/blockchains-and-distributed-ledger-technologies-in-general/ (accessed on 22 February 2019).
- Polge, J.; Robert, J.; Le Traon, Y. Permissioned blockchain frameworks in the industry: A comparison. ICT Express 2020. [Google Scholar] [CrossRef]
- Singh, V.; Willcox, K.E. Engineering Design with Digital Thread. AIAA J. 2018, 56, 4515–4528. [Google Scholar] [CrossRef]
- Elmessiry, M.; Elmessiry, A. Blockchain Framework for Textile Supply Chain Management. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2018; Volume 10974, pp. 213–227. [Google Scholar]
- Nguyen, G.-T.; Kim, K. A Survey about Consensus Algorithms Used in Blockchain. J. Inf. Process. Syst. 2018, 14, 101–128. [Google Scholar] [CrossRef]
- Bach, L.M.; Mihaljevic, B.; Zagar, M. Comparative analysis of blockchain consensus algorithms. In Proceedings of the 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; IEEE: Washington, DC, USA, 2018; pp. 1545–1550. [Google Scholar]
- Isaja, M.; Soldatos, J. Distributed ledger technology for decentralization of manufacturing processes. In Proceedings of the 2018 IEEE Industrial Cyber-Physical Systems (ICPS), St. Petersburg, Russia, 15–18 May 2018; IEEE: Washington, DC, USA, 2018; pp. 696–701. [Google Scholar]
- Wang, Y.; Han, J.H.; Beynon-Davies, P. Understanding blockchain technology for future supply chains: A systematic literature review and research agenda. Supply Chain Manag. Int. J. 2019, 24, 62–84. [Google Scholar] [CrossRef]
- Bumblauskas, D.; Mann, A.; Dugan, B.; Rittmer, J. A blockchain use case in food distribution: Do you know where your food has been? Int. J. Inf. Manag. 2020, 52, 102008. [Google Scholar] [CrossRef]
- Kamath, R. Food Traceability on Blockchain: Walmart’s Pork and Mango Pilots with IBM. J. Br. Blockchain Assoc. 2018, 1, 3712. [Google Scholar] [CrossRef]
- IBM. Now Arriving: IBM Blockchain for Supply Chain. Available online: https://www.ibm.com/blockchain/industries/supply-chain (accessed on 5 August 2019).
- Kalawsky, R.S.; Joannou, D.; Tian, Y.; Fayoumi, A. Using Architecture Patterns to Architect and Analyze Systems of Systems. Procedia Comput. Sci. 2013, 16, 283–292. [Google Scholar] [CrossRef] [Green Version]
- Unified Modeling LanguageTM (UML®) Resource Page. 2015. Available online: http://www.uml.org/ (accessed on 1 November 2020).
- Friedenthal, S.; Moore, A.; Steiner, R. OMG SysML TM Specification Specification Status; Object Management Group: Needham, MA, USA, 2008. [Google Scholar]
- Lane, J.A.; Bohn, T. Using SysML modeling to understand and evolve systems of systems. Syst. Eng. 2012, 16, 87–98. [Google Scholar] [CrossRef]
- Vujicic, D.; Jagodic, D.; Randic, S. Blockchain technology, bitcoin, and Ethereum: A brief overview. In Proceedings of the 2018 17th International Symposium INFOTEH-JAHORINA (INFOTEH), Sarajevo, Bosnia-Herzegovina, 21–23 March 2018; IEEE: Washington, DC, USA, 2018; Volume 2018, pp. 1–6. [Google Scholar]
- Barad, M.; Sipper, D. Flexibility in manufacturing systems: Definitions and Petri net modelling. Int. J. Prod. Res. 1988, 26, 237–248. [Google Scholar] [CrossRef]
- Howard, J.P.; Vachino, M.E. Blockchain Compliance with Federal Cryptographic Information-Processing Standards. IEEE Secur. Priv. Mag. 2020, 18, 65–70. [Google Scholar] [CrossRef]
- Greenspan, G. Avoiding the Pointless Blockchain Project. 2015. Available online: https://www.multichain.com/blog/2015/11/avoiding-pointless-blockchain-project/ (accessed on 5 March 2019).




| Access | Permissioned | Permissionless | Permissioned | Permissionless | Permissioned |
|---|---|---|---|---|---|
| Centralized Management | Public | Consortium | Private | ||
| Access Permissions | Open read/permissioned validation of transactions | Open read/open validation of transactions | Permissioned OR open read/permissioned validation of transactions | Open read/open validation of transactions | Permissioned read/validation of transactions |
| Participants | Unknown | Unknown | Known | Known (usually) | Known |
| Privacy | None | None | Tailored to requirements of platform | Tailored to requirements of platform | Tailored to requirements of platform |
| Validation Based on Consensus | Open to every participant in the network, subject to certain conditions | Open to every participant in the network | By preapproved entities | Depending on the consensus protocol chosen | By preapproved entities (within the single entity) |
| Validation Speed | Quick | Slow | Quick | Quick | Quick |
| Computing Energy Consumption | High (depending on consensus mechanism) | Very high | Low | Low | Low |
| Strengths | Weaknesses |
|
|
| Opportunities | Threats |
|
|
| Challenge | Blockchain Limitations | SE Considerations | Solutions |
|---|---|---|---|
| Requirement for Large Data Storage Capacity |
|
|
|
| Access Control |
|
|
|
| Trust Management |
|
|
|
| Connecting heterogeneous databases |
|
|
|
| Conflicting Consensus |
|
|
|
| Integrated blockchains |
|
|
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Joannou, D.; Kalawsky, R.; Martínez-García, M.; Fowler, C.; Fowler, K. Realizing the Role of Permissioned Blockchains in a Systems Engineering Lifecycle. Systems 2020, 8, 41. https://0-doi-org.brum.beds.ac.uk/10.3390/systems8040041
Joannou D, Kalawsky R, Martínez-García M, Fowler C, Fowler K. Realizing the Role of Permissioned Blockchains in a Systems Engineering Lifecycle. Systems. 2020; 8(4):41. https://0-doi-org.brum.beds.ac.uk/10.3390/systems8040041
Chicago/Turabian StyleJoannou, Demetrios, Roy Kalawsky, Miguel Martínez-García, Chris Fowler, and Kevin Fowler. 2020. "Realizing the Role of Permissioned Blockchains in a Systems Engineering Lifecycle" Systems 8, no. 4: 41. https://0-doi-org.brum.beds.ac.uk/10.3390/systems8040041





