Integrity Authentication Based on Blockchain and Perceptual Hash for Remote-Sensing Imagery
Abstract
:1. Introduction
- A Perceptual Hash Secure Storage and Transmission Framework (PH-SSTF) is designed to realize the secure storage and transmission of the original perceptual hash values by innovatively combining the private IPFS network and Hyperledger Fabric. This framework fills the gap in the existing research for the secure protection of remote-sensing image authentication information.
- A prototype system was implemented using PH-SSTF, and its practicality and scaling value were verified through rigorous testing. The proposed framework enables a higher level of data security and privacy protection, faster data storage and retrieval, and elastic storage and capacity scaling. These results demonstrate the effectiveness and potential of the proposed approach.
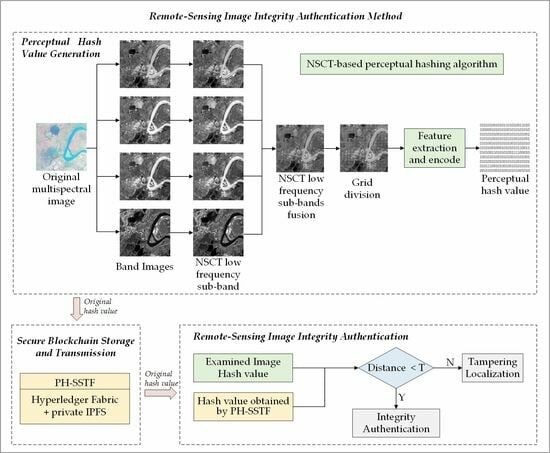
- A remote-sensing image perception hashing algorithm with wider applicability is proposed. The algorithm takes into account the unique multi-band features of remote-sensing images, uses the Non-Subsampled Contourlet Transform (NSCT) to achieve multi-band feature fusion and feature extraction, generates an encrypted perceptual hash, and improves the efficiency of hash generation.
2. Basic Idea and Preliminaries
2.1. Basic Idea
2.2. NSCT-Based Remote-Sensing Image Perceptual Hash Feature Extraction
2.2.1. Spatial Feature Extraction of Remote-Sensing Images Based on NSCT
2.2.2. NSCT Sub-Band Fusion of Multispectral Remote-Sensing Images
2.3. Hyperledger Fabric
2.3.1. Feasibility of Hyperledger Fabric Applied to Perceptual Hash Secure Transmission
- Member Licensing Mechanism for Authentication
- 2.
- Channel Mechanism for Secure Data Transmission
- 3.
- Modular Architecture for Efficient System Construction
2.3.2. Necessity of Combining Hyperledger Fabric with IPFS
3. Methods
3.1. Remote-Sensing Image Perceptual Hash Generation Algorithm
3.1.1. Preprocessing Stage
- The image k bands are each subjected to an NSCT decomposition of scale 1 to obtain k low-frequency sub-band coefficients .
- The is divided into W × H invisible grid cells of equal size and without overlapping. The divided grid cells are denoted as , where w and h identify the corresponding positions of the grid.
- The regional energy (RE) values of all bands at the position are calculated by Formula (1), where represents the RE value of the i-th band. The RE of all bands will be recorded in the blockchain simultaneously with the perceptual hash for use in the preprocessing stage of tampering localization. Furthermore, the weight of the sub-band coefficients of the i-th band can be calculated, and its expression is given in Formula (2).
- The weighted average of the low-frequency sub-band coefficients at each band position, , is regarded as the sub-band fusion result. The specific calculation method is shown in Formula (3).
3.1.2. Perceptual Hash Value Generation Stage
- The fused low-frequency sub-band coefficients of the grid cells are denoted as , and each grid cell is further divided into M × N sub-blocks of equal size. Calculate the standard deviation of each sub-block, and calculate the mean and standard deviation by Formulas (4) and (5):In the formula, M and N are, respectively, the total number of rows and columns of the sub-block; represents the low-frequency coefficient matrix of the -th sub-block; represents the standard deviation of the low-frequency coefficient of the -th sub-block with scale 1, . After the above processing, the characteristic sequence of the grid cell consisting of the standard deviation of the first-order low-frequency sub-bands of each sub-block NSCT transform is obtained as = ().
- The mean value of the feature sequence is calculated and quantized according to Formula (6) to obtain the perceptual hash value of the grid cell.
- Logistic mapping, as a typical chaotic system, can be expressed as a nonlinear iterative equation, as shown in Formula (7).The logistic mapping is chaotic when . Chaotic sequences can be generated by logistic mapping. The obtained chaotic sequence is very sensitive to the initial value and is non-periodic and non-convergent. The obtained chaotic sequence can be converted into binary numbers in the encryption process. Let each bit of it be an inner product with each bit of the original sequence of quantized perceptual hash, respectively, to obtain the final encrypted perceptual hash value . In this process, the initial value in chaotic encryption is used as the key K, which is shared between the sender and receiver and can improve the algorithm’s security.
3.2. Perceptual Hash Secure Storage and Transmission
3.2.1. Transmission and Storage Procedure Design
3.2.2. Hash Registration Chaincode Design
3.2.3. Prototype System Implementation
3.3. Remote-Sensing Image Authentication and Tampering Localization
3.3.1. Preprocessing Stage
- After receiving the data, the data recipient (DR) calls the CID and perceptual hash key K obtained by chaincode query through TxID. DR then, using the swarm.key file, joins the private IPFS network created by the DS. By utilizing the obtained CID, DR retrieves the original perceptual hash (including RE) from the IPFS network.
- The regional energy (RE) values for all bands of the received image are calculated by Formula (1), whererepresents the RE value of the i-th band. Furthermore, by comparing with the regional energy values for each band of the original image, a new weight of the sub-band coefficients of the i-th band can be assigned, and its expression is given in Formula (8).
- The low-frequency sub-band coefficients of each band are multiplied by the new weights to obtain the sub-band fusion result . The specific calculation method is shown in Formula (9).
3.3.2. Integrity Authentication Stage
- Original PH acquisition phase: DR decrypts the original hash value obtained by the IPFS network through perceptual hash key K Get , .
- Authentication phase: extract the quantized perceptual hash value , from the sub-band fusion result of the pending authentication image according to the hash value generation step in Section 3.1.2. The distance between the perceptual hash value and corresponding to the same location grid cell is calculated using the normalized Hamming distance. The specific formula is as follows.In the formula: , are two hash values of length ; denotes each bit in the hash value.
- The calculated normalized Hamming distance is compared to a predefined threshold T. If is found to be greater than T, it is concluded that the corresponding grid cell of the received image has been tampered with and marked as such. This process is repeated for all the grids. If the mean distance of all grid cells of the received image is less than the threshold T, it can be concluded that the received image is either the original image or a trusted image that has undergone content-preserving operations. Regarding the setting of the threshold T, a dedicated experiment will be carried out in Section 4.1.1 of this paper, as it concerns the balance between the robustness and sensitivity of the algorithm.
- If tampering with a grid is detected, it is considered that the integrity of the transmitted image has been compromised. Additionally, the location of the tampered area can be determined using the grid that was marked during the authentication phase.
4. Experiments and Results
4.1. Perceptual Hash Algorithm Validity Experiment
4.1.1. Threshold Determination Experiment
4.1.2. Algorithm Robustness and Sensitivity Experiment
4.2. Tampering Localization Experiments
4.2.1. Tampering Localization Ability Test
4.2.2. Comparative Experiments of Different Algorithms for Tampering Detection
4.3. Perceptual Hash Storage and Query Performance Experiments
4.3.1. Perceptual Hash Storage Efficiency Experiment
4.3.2. Perceptual Hash Query Efficiency Experiment
5. Discussion
5.1. Tamper Sensitivity Analysis
5.1.1. Sensitivity Analysis for Grid Cell Size
5.1.2. Sensitivity Analysis for Different Levels of Tampering
5.1.3. Sensitivity Analysis of High-Frequency Sub-Band Tampering
5.2. Original Perceptual Hash File Storage Reliability Analysis
5.3. Comparison with Existing Method
5.3.1. Comparison of Integrity Authentication Algorithms
5.3.2. Comparison of Waveband Fusion Methods
5.3.3. Comparison of Previous Schemes and the Proposed Scheme
- Stronger Data Security and Privacy Protection
- 2.
- Higher Speed Data Storage and Retrieval
- 3.
- Support Elastic Storage and Capacity Expansion
- 4.
- Support Offline Data Storage and Offline Transactions
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
References
- Avtar, R.; Kouser, A.; Kumar, A.; Singh, D.; Misra, P.; Gupta, A.; Yunus, A.P.; Kumar, P.; Johnson, B.A.; Dasgupta, R.; et al. Remote Sensing for International Peace and Security: Its Role and Implications. Remote Sens. 2021, 13, 439. [Google Scholar] [CrossRef]
- Chen, W.; Han, B.; Yang, Z.; Gao, X. MSSDet: Multi-Scale Ship-Detection Framework in Optical Remote-Sensing Images and New Benchmark. Remote Sens. 2022, 14, 5460. [Google Scholar] [CrossRef]
- Dempster, A. GNSS Data as Court Evidence: Lessons from Remote Sensing. In Proceedings of the 31st International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2018), Miami, FL, USA, 28 September 2018; pp. 1427–1433. [Google Scholar] [CrossRef]
- Nurhaida, I.; Ramayanti, D.; Riesaputra, R. Digital Signature & Encryption Implementation for Increasing Authentication, Integrity, Security and Data Non-Repudiation. Int. Res. J. Comput. Sci. 2017, 4, 4–14. [Google Scholar]
- Hou, X.; Yang, H.; Min, L. An Efficient Semi-Fragile Watermarking Scheme for Tamper Localization and Recovery. IOP Conf. Ser. Mater. Sci. Eng. 2018, 322, 052055. [Google Scholar] [CrossRef]
- Serra-Ruiz, J.; Megías, D. Watermarking Scheme for Tampering Detection in Remote Sensing Images Using Variable Size Tiling and DWT. In Satellite Data Compression, Communications, and Processing VI; SPIE: San Diego, CA, USA, 2010; Volume 7810, pp. 72–82. [Google Scholar] [CrossRef]
- Serra-Ruiz, J.; Megías, D. A Novel Semi-Fragile Forensic Watermarking Scheme for Remote Sensing Images. Int. J. Remote Sens. 2011, 32, 5583–5606. [Google Scholar] [CrossRef]
- Serra-Ruiz, J.; Qureshi, A.; Megías, D. Entropy-Based Semi-Fragile Watermarking of Remote Sensing Images in the Wavelet Domain. Entropy 2019, 21, 847. [Google Scholar] [CrossRef]
- Ding, K.; Meng, F.; Liu, Y.; Xu, N.; Chen, W. Perceptual Hashing Based Forensics Scheme for the Integrity Authentication of High Resolution Remote Sensing Image. Information 2018, 9, 229. [Google Scholar] [CrossRef]
- Weng, L.; Preneel, B. A Secure Perceptual Hash Algorithm for Image Content Authentication. In Communications and Multimedia Security; De Decker, B., Lapon, J., Naessens, V., Uhl, A., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; pp. 108–121. [Google Scholar] [CrossRef]
- Zhang, X.; Yan, H.; Zhang, L.; Wang, H. High-Resolution Remote Sensing Image Integrity Authentication Method Considering Both Global and Local Features. ISPRS Int. J. Geo-Inf. 2020, 9, 254. [Google Scholar] [CrossRef]
- Ding, K.; Chen, S.; Meng, F. A Novel Perceptual Hash Algorithm for Multispectral Image Authentication. Algorithms 2018, 11, 6. [Google Scholar] [CrossRef]
- Ding, K.; Chen, S.; Wang, Y.; Liu, Y.; Zeng, Y.; Tian, J. AAU-Net: Attention-Based Asymmetric U-Net for Subject-Sensitive Hashing of Remote Sensing Images. Remote Sens. 2021, 13, 5109. [Google Scholar] [CrossRef]
- Ding, K.; Yang, Z.; Wang, Y.; Liu, Y. An Improved Perceptual Hash Algorithm Based on U-Net for the Authentication of High-Resolution Remote Sensing Image. Appl. Sci. 2019, 9, 2972. [Google Scholar] [CrossRef]
- Ding, K.; Liu, Y.; Xu, Q.; Lu, F. A Subject-Sensitive Perceptual Hash Based on MUM-Net for the Integrity Authentication of High Resolution Remote Sensing Images. ISPRS Int. J. Geo-Inf. 2020, 9, 485. [Google Scholar] [CrossRef]
- Ding, K.; Zeng, Y.; Wang, Y.; Lv, D.; Yan, X. AGIM-Net Based Subject-Sensitive Hashing Algorithm for Integrity Authentication of HRRS Images. Geocarto Int. 2023, 38, 2168071. [Google Scholar] [CrossRef]
- Ding, K.; Chen, S.; Zeng, Y.; Wang, Y.; Yan, X. Transformer-Based Subject-Sensitive Hashing for Integrity Authentication of High-Resolution Remote Sensing (HRRS) Images. Appl. Sci. 2023, 13, 1815. [Google Scholar] [CrossRef]
- Lee, S.; Seok, H.-W.; Lee, K.; In, H.P. B-GPS: Blockchain-Based Global Positioning System for Improved Data Integrity and Reliability. ISPRS Int. J. Geo-Inf. 2022, 11, 186. [Google Scholar] [CrossRef]
- Krichen, M.; Ammi, M.; Mihoub, A.; Almutiq, M. Blockchain for Modern Applications: A Survey. Sensors 2022, 22, 5274. [Google Scholar] [CrossRef] [PubMed]
- Qingqing, H.; Yuan, J.; Jian, Y. Improved Fusion Method for Infrared and Visible Remote Sensing Imagery Using NSCT. In Proceedings of the 2011 6th IEEE Conference on Industrial Electronics and Applications, Beijing, China, 21–23 June 2011; pp. 1012–1015. [Google Scholar] [CrossRef]
- Chen, P.; Zhang, Y.; Jia, Z.; Yang, J.; Kasabov, N. Remote Sensing Image Change Detection Based on NSCT-HMT Model and Its Application. Sensors 2017, 17, 1295. [Google Scholar] [CrossRef] [PubMed]
- Da Cunha, A.L.; Zhou, J.; Do, M.N. The Nonsubsampled Contourlet Transform: Theory, Design, and Applications. IEEE Trans. Image Process. 2006, 15, 3089–3101. [Google Scholar] [CrossRef]
- Du, C.; Gao, S. Remote Sensing Image Fusion Based on Nonlinear IHS and Fast Nonsubsampled Contourlet Transform. J. Indian Soc. Remote Sens. 2018, 46, 2023–2032. [Google Scholar] [CrossRef]
- Wang, S.; Shen, Y. Multi-Modal Image Fusion Based on Saliency Guided in NSCT Domain. IET Image Process. 2020, 14, 3188–3201. [Google Scholar] [CrossRef]
- Dai, W.; Tan, L.; Yang, A. Fusion Algorithm of Infrared and Visible Images Based on Local Energy Using NSCT. In Proceedings of the 10th World Congress on Intelligent Control and Automation, Beijing, China, 6–8 July 2012; pp. 4579–4582. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain Challenges and Opportunities: A Survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Yang, R.; Wakefield, R.; Lyu, S.; Jayasuriya, S.; Han, F.; Yi, X.; Yang, X.; Amarasinghe, G.; Chen, S. Public and Private Blockchain in Construction Business Process and Information Integration. Autom. Constr. 2020, 118, 103276. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the Thirteenth EuroSys Conference, EuroSys’18, Porto, Portugal, 23–26 April 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1–15. [Google Scholar] [CrossRef]
- Ma, C.; Kong, X.; Lan, Q.; Zhou, Z. The Privacy Protection Mechanism of Hyperledger Fabric and Its Application in Supply Chain Finance. Cybersecurity 2019, 2, 5. [Google Scholar] [CrossRef]
- Benet, J. IPFS—Content Addressed, Versioned, P2P File System. arXiv 2014, arXiv:1407.3561. [Google Scholar] [CrossRef]
- Mukne, H.; Pai, P.; Raut, S.; Ambawade, D. Land Record Management Using Hyperledger Fabric and IPFS. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; pp. 1–8. [Google Scholar] [CrossRef]
- Nyaletey, E.; Parizi, R.M.; Zhang, Q.; Choo, K.-K.R. BlockIPFS—Blockchain-Enabled Interplanetary File System for Forensic and Trusted Data Traceability. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 18–25. [Google Scholar] [CrossRef]
- Li, L.; Yue, Z.; Wu, G. Electronic Medical Record Sharing System Based on Hyperledger Fabric and InterPlanetary File System. In Proceedings of the 2021 5th International Conference on Compute and Data Analysis; ICCDA 2021, Sanya, China, 2–4 February 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 149–154. [Google Scholar] [CrossRef]
- Mani, V.; Manickam, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. Hyperledger Healthchain: Patient-Centric IPFS-Based Storage of Health Records. Electronics 2021, 10, 3003. [Google Scholar] [CrossRef]
- Xia, G.-S.; Bai, X.; Ding, J.; Zhu, Z.; Belongie, S.; Luo, J.; Datcu, M.; Pelillo, M.; Zhang, L. DOTA: A Large-Scale Dataset for Object Detection in Aerial Images. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Salt Lake City, UT, USA, 18–22 June 2018; pp. 3974–3983. [Google Scholar]
- Tong, X.-Y.; Xia, G.-S.; Lu, Q.; Shen, H.; Li, S.; You, S.; Zhang, L. Land-Cover Classification with High-Resolution Remote Sensing Images Using Transferable Deep Models. Remote Sens. Environ. 2020, 237, 111322. [Google Scholar] [CrossRef]
- Fawcett, T. An Introduction to ROC Analysis. Pattern Recognit. Lett. 2006, 27, 861–874. [Google Scholar] [CrossRef]
- Liu, M.; Gao, H.; Xia, X.; Gui, S.; Gao, T. Perceptual Image Hashing Based on Canny Operator and Tensor for Copy-Move Forgery Detection. Comput. J. 2022, bxac186. [Google Scholar] [CrossRef]
- Yu, B.; Li, X.; Zhao, H. Virtual Block Group: A Scalable Blockchain Model with Partial Node Storage and Distributed Hash Table. Comput. J. 2020, 63, 1524–1536. [Google Scholar] [CrossRef]
- Wahid, M.; Ahmad, N.; Zafar, M.H.; Khan, S. On Combining MD5 for Image Authentication Using LSB Substitution in Selected Pixels. In Proceedings of the 2018 International Conference on Engineering and Emerging Technologies (ICEET), Lahore, Pakistan, 22–23 February 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Guo, M.; Liu, H.; Xu, Y.; Huang, Y. Building Extraction Based on U-Net with an Attention Block and Multiple Losses. Remote Sens. 2020, 12, 1400. [Google Scholar] [CrossRef]
- Ding, K.; Chen, S.; Yu, J.; Liu, Y.; Zhu, J. A New Subject-Sensitive Hashing Algorithm Based on MultiRes-RCF for Blockchains of HRRS Images. Algorithms 2022, 15, 213. [Google Scholar] [CrossRef]












| Categories | Advantages | Disadvantages | Use Cases | Delegates |
|---|---|---|---|---|
| Public | +Independence +Transparency +Trust | −Performance −Scalability −Privacy Security | Cryptocurrency Document validation | BTC ETH Solana |
| Private | +Access control +Performance | −Trust −Auditability | Supply chain Asset ownership | Multichain |
| Consortium | +Access control +Scalability +Privacy Security | −Transparency | Banking Research Supply chain | Hyperledger Fabric Corda Quorum |
| Abbreviation | Description |
|---|---|
| DS | Data Sender is an organization that has Remote-sensing images |
| DR | Data Recipients will perform data integrity certification |
| PH | Initial perceptual hash value |
| RE | The regional energy values of all bands |
| hashregistercc | perceptual hash register chaincode |
| TxID | Hyperledger Fabric transactions number |
| CID | Location of files in IPFS |
| swarm.key | Shared keys for private IPFS network |
| K | Perceptual hash secret key |
| RESULT | Results returned by the chaincode |
| Steps | Description |
|---|---|
| 1. | DS starts the Hyperledger Fabric network and establishes a blockchain node peer of Organization 1 (Org1). |
| 2. | Blockchain node peer of Org1 representing DS joins Channel A and deploys the chaincode in Channel A. |
| 3. | DR sends a data transmission request to DS. |
| 4. | DR is identified and establishes the blockchain node of Org2 in the Hyperledger Fabric network. |
| 5. | Blockchain node peer of Org2 representing DR joins Channel A. |
| 6. | DS will need to transmit remote-sensing image data to obtain PH through Section 3.1 Perceptual Hash Algorithm. |
| 7. | DS uploads PH to the private IPFS network to obtain CID. |
| 8. | Execute the chaincode and bind CID and perceptual hash key K and data transmission information to the blockchain for storage. |
| 9. | The chaincode is executed successfully and returns RESULT and TxID. |
| 10. | DS sends the TxID, the swarm.key file of the private IPFS network and the original file to the DR. |
| 11. | After receiving the data and related information, the DR initiates a query by TxID. |
| 12. | DR obtains the data corresponding to the CID of PH and the perceptual hash key K. |
| 13. | DR joins the private IPFS network created by DS through the swarm.key file and obtains the original PH through CID. |
| 14. | DR compares the obtained original PH with the PH obtained by the perceptual hash algorithm and performs integrity authentication. |
| Properties | Types | Description |
|---|---|---|
| Imagedata | String | Transmitting image information |
| Sender | String | Sender’s information |
| Receiver | String | Receiver’s information |
| Imagingtime | Int64 | Image production time |
| Transmissiontime | Int64 | Image transmission time |
| PHaddress | String | Perceptual Hash IPFS addresses |
| Method Name | Types | Input | Output | Description |
|---|---|---|---|---|
| init | String | N/A | Boolean | Initializes the chaincode and returns a Boolean value. |
| invoke | String | N/A | Boolean | Forwarding parameters to the corresponding method. |
| regist | String | Registration | TxID | Register the hash and return the transaction ID. |
| query | Int64 | TxID | Registration | Query hash and transmission information. |
| Parameters | Google Earth | Gaofen-2 (GF2) | Sentinel-2B | ||
|---|---|---|---|---|---|
| Spectral Number | 3 | 4 | 13 | ||
| Spectral Central wavelength (nm) | B-Blue 490 B-Green 560 B-Red 665 | B01-485 B02-555 B03-655 B04-830 | B01-443 B02-490 B03-560 B04-665 | B05-705 B06-740 B07-783 B08-842 B08A-865 | B09-940 B10-1375 B11-1610 B12-2190 |
| Content-Preserving Operation | Variable Parameters | Parameters Setting |
|---|---|---|
| JPEG compression | Quality factor | 50, 90 |
| Gaussian filtering (4 × 4) | Standard deviation | 0.5, 5 |
| Motion blurring | Motion length | 5, 10 |
| Salt and pepper noise | Noise density | 30%, 50% |
| Gaussian noise | Standard deviation | 5, 50 |
| Unsharp masking | Gain factor | 1, 10 |
| LSB watermark embedding | Bit-planes number | 1 |
| Format conversion to BMP | Selected bands | Gaofen-2: B03, B02, B01; Sentinel-2B: B04, B03, B02 |
| Format conversion to PNG | Selected bands | Gaofen-2: B03, B02, B01; Sentinel-2B: B04, B03, B02 |
| Processing Operations | Similar | Tampered | ||||
|---|---|---|---|---|---|---|
| Max. | Min. | Mean | Max. | Min. | Mean | |
| JPEG compression | 0.0495 | 0.0005 | 0.0045 | 0.5547 | 0.0623 | 0.3243 |
| Gaussian filtering (4 × 4) | 0.0237 | 0.0014 | 0.0027 | 0.5124 | 0.1134 | 0.2894 |
| Motion blurring | 0.0517 | 0.0018 | 0.0124 | 0.5435 | 0.1044 | 0.3827 |
| Salt and pepper noise | 0.0356 | 0.0015 | 0.0138 | 0.4989 | 0.0384 | 0.2845 |
| Gaussian noise | 0.0371 | 0.0027 | 0.0110 | 0.4872 | 0.0738 | 0.3143 |
| Unsharp masking | 0.0428 | 0.0016 | 0.0107 | 0.6483 | 0.1845 | 0.2976 |
| LSB watermark embedding | 0.0469 | 0.0020 | 0.0265 | 0.5743 | 0.0937 | 0.3285 |
| Format conversion to BMP | 0.0124 | 0.0000 | 0.0026 | 0.6463 | 0.1173 | 0.4866 |
| Format conversion to PNG | 0.0112 | 0.0000 | 0.0012 | 0.6271 | 0.1321 | 0.4824 |
| Tampering Type | Band Tampering Case | Band Fusion Results | Grid Localization | Average Hamming Distance |
|---|---|---|---|---|
| Erasure |  |  |  | Untampered area: 0.0032 Tampered area: 0.5456 |
| Copy-move |  |  |  | Untampered area: 0.0034 Tampered area: 0.3856 |
| Modify |  |  |  | Untampered area: 0.0012 Tampered area: 0.4712 |
| Algorithm | Farmland | Desert | Towns | Mountains | River | Marine |
|---|---|---|---|---|---|---|
| [9] | 96.67% | 82.87% | 96.70% | 96.72% | 96.19% | 87.02% |
| [11] | 97.22% | 88.39% | 98.35% | 95.62% | 95.10% | 85.94% |
| [12] | 97.78% | 90.61% | 96.15% | 96.17% | 95.65% | 86.48% |
| [38] | 98.89% | 93.92% | 97.80% | 97.26% | 96.73% | 91.89% |
| This paper | 98.89% | 94.47% | 97.80% | 97.81% | 97.28% | 94.59% |
| Grid Size | Sample of Original Images | Sample Tampered Images | Single-Grid Calculation Time (s) | Hamming Distance between Similar Grids |
|---|---|---|---|---|
| 512 × 512 |  |  | 30.29 | 0.0411 |
| 256 × 256 |  |  | 8.45 | 0.1491 |
| 128 × 128 |  |  | 2.66 | 0.3492 |
| 64 × 64 |  |  | 1.12 | 0.4349 |
| 32 × 32 |  |  | 0.56 | 0.3667 |
| Level of Tampering | Sample of Original Images | Sample of Tampered Images | Hamming Distance |
|---|---|---|---|
| 10% |  |  | 0.0364 |
| 20% |  |  | 0.0567 |
| 30% |  |  | 0.1150 |
| 40% |  |  | 0.1664 |
| 50% |  |  | 0.2445 |
| 60% |  |  | 0.3457 |
| 70% |  |  | 0.3862 |
| 80% |  |  | 0.4547 |
| 90% |  |  | 0.5349 |
| Tampering Methods | Sample of Original Images | Sample Tampered Images | Grid Localization | Average Hamming Distance |
|---|---|---|---|---|
| Erasure |  |  | none | 0.0237 |
| Modify |  |  | none | 0.0145 |
| Swap |  |  |  | 0.3678 |
| Swap |  |  |  | 0.4147 |
| 5 | 9.53 × 10−7 |
| 10 | 2.00 × 10−5 |
| 15 | 2.01 × 10−4 |
| 20 | 1.29 × 10−3 |
| 25 | 5.90 × 10−3 |
| 30 | 2.06 × 10−2 |
| Algorithm | Digital Signature [40] | Watermarking [5] | Watermarking [8] | FAST Based [11] | Canny Based [38] | Proposed Algorithm |
|---|---|---|---|---|---|---|
| Non-destructive to the original data | No | No | No | Yes | Yes | Yes |
| Robust to Content-preserving operations | No | Yes | Yes | Yes | Yes | Yes |
| Consider multi-band characteristics | No | No | Yes | No | No | Yes |
| Tamper Localization | No | Yes | Yes | Yes | Yes | Yes |
| Methods | Tampering Sample | Fusion Results | Fusion Time (s) | PSNR (dB) |
|---|---|---|---|---|
| PCA |  |  | 0.53452 | 11.35 |
| HSV conversion |  |  | 0.83972 | 33.20 |
| Wavelet Transform |  |  | 0.92643 | 29.85 |
| Ours |  |  | 0.32347 | 51.62 |
| Authors | Objective | 1 | 2 | 3 | 4 |
|---|---|---|---|---|---|
| Mukne et al. [31] | Land acquisition and ownership record management | Yes | Yes | No | No |
| Nyaletey et al. [32] | Proposed a BlockIPFS to create a clear audit trail | Yes | Yes | No | No |
| Li et al. [33] | Safe storage and sharing of medical record data | Yes | Yes | No | No |
| Mani et al. [34] | Patient-centric healthcare data management | Yes | Yes | No | No |
| PH-SSTF | Secure transmission and storage of perceptual hash | Better | Better | Yes | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, D.; Ren, N.; Zhu, C. Integrity Authentication Based on Blockchain and Perceptual Hash for Remote-Sensing Imagery. Remote Sens. 2023, 15, 4860. https://0-doi-org.brum.beds.ac.uk/10.3390/rs15194860
Xu D, Ren N, Zhu C. Integrity Authentication Based on Blockchain and Perceptual Hash for Remote-Sensing Imagery. Remote Sensing. 2023; 15(19):4860. https://0-doi-org.brum.beds.ac.uk/10.3390/rs15194860
Chicago/Turabian StyleXu, Dingjie, Na Ren, and Changqing Zhu. 2023. "Integrity Authentication Based on Blockchain and Perceptual Hash for Remote-Sensing Imagery" Remote Sensing 15, no. 19: 4860. https://0-doi-org.brum.beds.ac.uk/10.3390/rs15194860