Predictors of Employees’ Mobile Security Practice: An Analysis of Personal and Work-Related Variables
Abstract
:1. Introduction
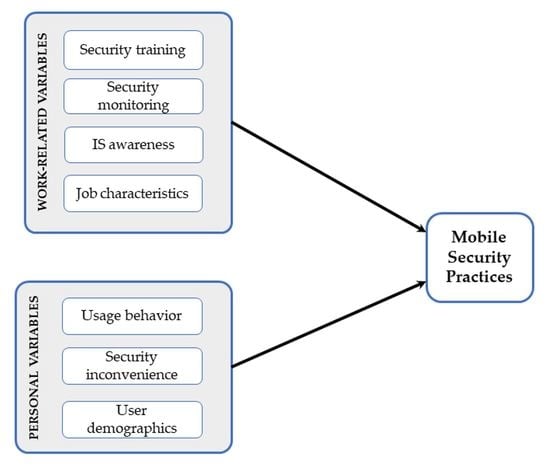
2. Literature Review and Hypotheses Formulation
2.1. Cost–Benefit Consideration
2.2. Personal Variables
2.3. Organizational Variables
3. Research Methods
3.1. Sample
3.2. Measurements
- Mobile security practice: Four items that gauged respondents’ frequency of performing behaviors related to the use of public Wi-Fi, webmail, and the protection of mobile devices (1, never, to 6, very frequent).
- Expected outcome: Respondents were requested to assess the possible outcome of each type of mobile security behavior (1, very negative, to 6, very positive).
- Security inconvenience: Respondents were requested to gauge the functional impact of the selected mobile security behavior on their work (1, very easy, to 10, very troublesome).
- Usage behavior: Three items related to the frequency (1, never, to 6, very frequent), expected benefits (1, very negative, to 6, very positive), and perceived utility of using mobile devices to store confidential information (1, very easy, to 10, very troublesome).
- Job characteristic: Respondents were asked about the confidentiality level of data, information, and documents handled at work (1, not confidential at all, to 6, very confidential).
- Security awareness: Four statements related to knowledge about information security, including actions to be taken, persons to contact, and relevant standards (1, strongly disagree, to 6, strongly agree).
- Security monitoring: Four items related to the actions taken by the employing companies to oversee the use of information resources (1, never, to 6, very frequent).
- Security training: Organization’s emphasis on information security via training programs. Four statements were used (1, never, to 6, very frequent).
- Security incident: Respondents were asked whether they had experienced security incidents before (yes, no, not sure).
- Perceived risk: Respondents were to rate the likelihood of security incidents occurring within their department (1, very unlikely, to 6, very likely).
3.3. Descriptive Statistics
3.4. Factor Analysis
3.5. Analysis 1: Path Modeling
3.6. Analysis 2: Ordinal Regression Analysis
4. Discussion and Conclusions
5. Limitations and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Mobile security practice: How frequent do you perform the following? 1, never, to 6, very frequent | |
| SP1 | Use unofficial webmail to perform office duties such as sending sensitive information/documents (e.g., @yahoo.com; @hotmail.com). |
| SP2 | Protect mobile devices such as hand phones, tablets and laptops either with passwords, PINs, patterns, or other access control methods. |
| SP3 | Access work-related emails via public networks such as Wi-Fi provided by a restaurant. |
| SP4 | Change your mobile devices’ passwords, PINs, patterns, or other access control methods as regular intervals. |
| Expected outcome: If the following tasks were performed in your organization, what is the possible outcome? 1, highly negative to 6 highly positive | |
| OE1 | Use unofficial webmail to perform office duties such as sending sensitive information/documents (e.g., @yahoo.com; @hotmail.com). |
| OE2 | Protect mobile devices such as hand phones, tablets and laptops either with passwords, PINs, patterns, or other access control methods. |
| OE3 | Access work-related emails via public networks such as Wi-Fi provided by a restaurant. |
| OE4 | Change your mobile devices’ passwords, PINs, patterns, or other access control methods as regular intervals. |
| Security inconvenience: By performing these tasks, your work will become: 1, very easy to 10, very troublesome | |
| PE1 | Use unofficial webmail to perform office duties such as sending sensitive information/documents (e.g., @yahoo.com; @hotmail.com). |
| PE2 | Protect mobile devices such as hand phones, tablets and laptops either with passwords, PINs, patterns, or other access control methods. |
| PE3 | Access work-related emails via public networks such as Wi-Fi provided by a restaurant. |
| PE4 | Change your mobile devices’ passwords, PINs, patterns, or other access control methods as regular intervals. |
| Usage behavior: | |
| UB1 | How frequent do you store confidential information in personal mobile devices such as hand phones, tablets and laptops. 1, never, to 6, very frequent |
| UB2 | By storing confidential information in personal mobile devices such as hand phones, tablets and laptops the possible outcome is 1, highly negative to 6 highly positive |
| UB3 | By storing confidential information in personal mobile devices such as hand phones, tablets and laptops, your work will become 1, very easy to 10, very troublesome |
| Job characteristic: 1, Not sensitive at all to 6, Highly sensitive | |
| JC1 | You usually handle documents that are … |
| JC2 | You usually handle information that are … |
| JC3 | You usually handle data that are … |
| Security awareness: Rate your agreement to the following statements. 1, Strongly disagree to 6, Strongly agree | |
| SA1 | You know who to contact in the event of information security breach. |
| SA2 | You know what to do in the event of information security breach. |
| SA3 | You know the standard operating procedures in handling private and confidential information. |
| SA4 | You know who the security officers in your organization are. |
| Security monitoring: How frequent does your organization conduct the following activities? 1, Never to 6, Very frequent | |
| SM1 | Conducts audit to detect the use of authorised software on its computers. |
| SM2 | Reviews logs of employee computing activities. |
| SM3 | Monitors employee computing activities. |
| SM4 | Monitors the content of employees’ e-mail messages. |
| Security training: How frequent does your organization conduct the following activities? 1, Never to 6, Very frequent | |
| ST1 | Briefs employees on the consequences of modifying computerised data in an unauthorised way. |
| ST2 | Communicates the importance of confidentially and privacy of data. |
| ST3 | Provides employees with education on computer software copyright laws. |
| ST4 | Educates employees on their computer security responsibilities. |
References
- Cisco BYOD Insights 2013 (2013, March). Available online: http://www.ciscomcon.com/sw/swchannel/registration/internet/registration.cfm?SWAPPID=91&RegPageID=350200&SWTHEMEID=12949 (accessed on 15 February 2019).
- Morrow, B. BYOD security challenges: Control and protect your most sensitive data. Netw. Secur. 2012, 2012, 5–8. [Google Scholar] [CrossRef]
- Jones, B.H.; Heinrichs, L.R. Do business students practice smartphone security? J. Comput. Inf. Syst. 2012, 53, 22–30. [Google Scholar]
- Mobile Devices Still Unsecured in the Workplace. Available online: https://www.eweek.com/mobile/mobile-devices-still-unsecured-in-the-workplace/ (accessed on 15 February 2019).
- Hayes, D.; Cappa, F.; Le-Khac, N.A. An effective approach to mobile device management: Security and privacy issues associated with mobile applications. Digit. Bus. 2020, 1, 100001. [Google Scholar] [CrossRef]
- Imgraben, J.; Engelbrecht, A.; Choo, K.R. Always connected, but are smart mobile users getting more security savvy? A survey of smart mobile device users. Behav. Inf. Technol. 2014, 33, 1347–1360. [Google Scholar] [CrossRef]
- McGill, T.; Thompson, N. Old risks, new challenges: Exploring differences in security between home computer and mobile device use. Behav. Inf. Technol. 2017, 36, 1111–1124. [Google Scholar] [CrossRef]
- Stanciu, V.; Gheorghe, M. Facing the mobile revolution: A Romanian insight. Account. Manag. Inf. Syst. 2019, 18, 101–118. [Google Scholar] [CrossRef]
- Clarke, N.; Symes, J.; Saevanee, H.; Furnell, S. Awareness of Mobile Device Security: A Survey of User’s Attitudes. Int. J. Mob. Comput. Multimedia Commun. 2016, 7, 15–31. [Google Scholar]
- Breitinger, F.; Tully-Doyle, R.; Hassenfeldt, C. A survey on smartphone user’s security choices, awareness and education. Comput. Secur. 2020, 88, 101647. [Google Scholar] [CrossRef]
- Mylonas, A.; Kastania, A.; Gritzalis, D. Delegate the smartphone user? Security awareness in smartphone plat-forms. Comput. Secur. 2013, 34, 47–66. [Google Scholar] [CrossRef] [Green Version]
- Yamin, M.M.; Katt, B. Mobile device management (MDM) technologies, issues and challenges. ICCSP’19. In Proceedings of the 3rd International Conference on Cryptography, Security and Privacy, Kuala Lumpur, Malaysia, 19–21 January 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 143–147. [Google Scholar]
- Garba, A.B.; Armarego, J.; Murray, D.; Kenworthy, W. Review of the information security and privacy challenges in Bring Your Own Device (BYOD) environments. Int. J. Inf. Secur. Priv. 2015, 11, 38–54. [Google Scholar] [CrossRef]
- Barthwal, D. Mobile Device Management (MDM) in Organizations. 2016. Available online: https://www.researchgate.net/publication/305380830_Mobile_Device_Management_MDM_in_Organizations (accessed on 15 February 2019).
- Doargajudhur, M.S.; Dell, P. Impact of BYOD on organizational commitment: An empirical investigation. Inf. Technol. People 2018, 32, 246–268. [Google Scholar] [CrossRef] [Green Version]
- Lima, A.; Borges, P.; Sousa, B.; Simões, P.; Cruz, T. An Introduction to Mobile Device Security. In Mobile Apps Engineering: Design, Development, Security, and Testing; Mostefaoui, G.K., Tariq, F., Eds.; CPC Press, Taylor & Francis Group: Boca Raton, FL, USA, 2019. [Google Scholar]
- Lima, A.; Rosa, L.; Cruz, T.; Simões, P. A Security Monitoring Framework for Mobile Devices. Electronics 2020, 9, 1197. [Google Scholar] [CrossRef]
- Jeong-Yeon, L.; Younghwa, L.; Wadhwa, P. Conference Paper Sharing Among Academicians: Calculative and Normative Aspects of Rational Choice. Acad. Manag. Learn. Educ. 2010, 9, 204–224. [Google Scholar] [CrossRef]
- Moscati, I.; Tubaro, P. Becker random behavior and the as-if defense of rational choice theory in demand analysis. J. Econ. Methodol. 2011, 18, 107–128. [Google Scholar] [CrossRef]
- Paternoster, R.; Simpson, S. Sanction threats and appeals to morality: Testing a rational choice model of corporate crime. Law Soc. Rev. 1996, 30, 549–584. [Google Scholar] [CrossRef]
- Bulgurcu, B.; Cavusoglu, H.; Benbasat, I. Information security policy compliance: An empirical student of rationality-based beliefs and information security awareness. MIS Q. 2010, 34, 523–548. [Google Scholar] [CrossRef] [Green Version]
- Li, H.; Zhang, J.; Sarathy, R. Understanding compliance with internet use policy from the perspective of rational choice theory. Decis. Support Syst. 2010, 48, 635–645. [Google Scholar] [CrossRef]
- Montesdioca, G.Z.; Maçada, A.G. Measuring user satisfaction with information security practices. Comput. Secur. 2015, 48, 267–280. [Google Scholar] [CrossRef]
- Bandura, A. Self-Efficacy: The Exercise of Control; W.H. Freeman: New York, NY, USA, 1997. [Google Scholar]
- Rhee, H.; Kim, C.; Ryu, Y.U. Self-efficacy in information security: Its influence on end users’ information security practice behavior. Comput. Secur. 2009, 28, 816–826. [Google Scholar] [CrossRef]
- Furnell, S.; Rajendran, A. Understanding the influences on information security behavior. Comput. Fraud. Secur. 2012, 2012, 12–15. [Google Scholar]
- Tu, Z.; Turel, O.; Yuan, Y.; Archer, N. Learning to cope with information security risks regarding mobile device loss or theft: An empirical examination. Inf. Manag. 2015, 52, 506–517. [Google Scholar] [CrossRef]
- McAlister, A.L.; Perry, C.L.; Parcel, G.S. How individuals, environments, and health behaviors interact: Social cognitive theory. In Health Behavior and Health Education: Theory, Research, and Practice, 4th ed.; Glanz, K., Rimmer, B.K., Viswanath, K., Eds.; Jossey-Bass: San Francisco, CA, USA, 2008; pp. 169–188. [Google Scholar]
- Ng, B.Y.; Kankanhalli, A.; Xu, Y. Studying users’ computer security behavior: A health belief perspective. Decis. Support Syst. 2009, 46, 815–825. [Google Scholar] [CrossRef]
- Jose, S.; Babu, D. A study on the role of performance and image outcome expectations on innovative behavior in the workplace. In Proceedings of the ISPIM Conferences, Manchester, UK, 17–20 June 2012; pp. 1–33. [Google Scholar]
- Williams, C.K.; Wynn, D.; Madupalli, R.; Karahanna, E.; Duncan, B.K. Explaining Users’ Security Behaviors with the Security Belief Model. J. Organ. End User Comput. 2014, 26, 23–46. [Google Scholar] [CrossRef]
- Seyeon, C.; Goo Hyeok, C.; Jing, D. Employees’ Attributions to Innovation and Implementation Behaviors; Academy of Management: Briarcliff Manor, NY, USA, 2015; p. 1. [Google Scholar]
- Albrechtsen, E. A qualitative study of users’ view on information security. Comput. Secur. 2007, 26, 276–289. [Google Scholar] [CrossRef]
- Hovav, A.; Putri, F.F. This is my device! Why should I follow your rules? Employees’ compliance with BYOD security policy. Pervasive Mob. Comput. 2016, 32, 35–49. [Google Scholar] [CrossRef]
- Posey, C.; Roberts, T.L.; Lowry, P.B.; Hightower, R.T. Bridging the divide: A qualitative comparison of information security thought patterns between information security professionals and ordinary organizational insiders. Inf. Manag. 2014, 51, 551–567. [Google Scholar] [CrossRef]
- Beautement, A.; Sasse, A. The economics of user effort in information security. Comput. Fraud. Secur. 2009, 2009, 8–12. [Google Scholar] [CrossRef]
- Rajamma, R.K.; Paswan, A.K.; Hossain, M.M. Why do shoppers abandon shopping cart? Perceived waiting time, risk, and transaction inconvenience. J. Prod. Brand. Manag. 2009, 18, 188–197. [Google Scholar] [CrossRef]
- Cheng, Y.; Liu, K. Evaluating bicycle-transit users’ perceptions of intermodal inconvenience. Transp. Res. Part A Policy Pract. 2012, 46, 1690–1706. [Google Scholar] [CrossRef]
- Liang, D.; Ma, Z.; Qi, L. Service quality and customer switching behavior in China’s mobile phone service sector. J. Bus. Res. 2013, 66, 1161–1167. [Google Scholar] [CrossRef]
- Barbarossa, C.; Pelsmacker, P. Positive and negative antecedents of purchasing eco-friendly products: A comparison between green and non-green consumers. J. Bus. Ethics 2016, 134, 229–247. [Google Scholar] [CrossRef]
- Stiakakis, E.; Georgiadis, C.; Andronoudi, A. Users’ perceptions about mobile security breaches. Inf. Syst. e-Bus. Manag. 2016, 14, 857–882. [Google Scholar] [CrossRef]
- Shaw, R.S.; Chen, C.C.; Harris, A.L.; Huang, H. The Impact of Information Richness on Information Security Awareness Training Effectiveness. Comput. Educ. 2009, 52, 92–100. [Google Scholar] [CrossRef]
- Safa, N.S.; Sookhak, M.; Von Solms, R.; Furnell, S.; Ghani, N.A.; Herawan, T. Information security conscious care behavior formation in organizations. Comput. Secur. 2015, 53, 65–78. [Google Scholar] [CrossRef] [Green Version]
- Hanus, B.; Wu, Y. Impact of users’ security awareness on desktop security behavior: A protection motivation theory perspective. Inf. Syst. Manag. 2016, 33, 2–16. [Google Scholar] [CrossRef]
- Edwards, K. Examining the Security Awareness, Information Privacy, and the Security Behaviors of Home Computer Users. Ph.D. Thesis, Nova Southeastern University, Fort Lauderdale-Davie, FL, USA, December 2015. [Google Scholar]
- Öğütçü, G.; Testik, Ö.M.; Chouseinoglou, O. Analysis of personal information security behavior and awareness. Comput. Secur. 2016, 56, 83–93. [Google Scholar] [CrossRef]
- Hoffman, W.M.; Hartman, L.P.; Rowe, M. You’ve got mail and the boss knows: A survey by the center for business ethics of companies’ email and internet monitoring. Bus. Soc. Rev. 2003, 108, 285–307. [Google Scholar] [CrossRef]
- Samaranayake, V.; Gamage, C. Employee perception towards electronic monitoring at work place and its impact on job satisfaction of software professionals in Sri Lanka. Telemat. Inform. 2012, 29, 233–244. [Google Scholar] [CrossRef]
- D’Arcy, J.; Hovav, A.; Galletta, D. User Awareness of Security Countermeasures and Its Impact on Information Systems Misuse: A Deterrence Approach. Inf. Syst. Res. 2009, 20, 79–98. [Google Scholar] [CrossRef] [Green Version]
- Trinkle, B.S.; Crossler, R.E.; Warkentin, M. I’m game, are you? Reducing real-world security threats by managing employee activity in online social networks. J. Inf. Syst. 2014, 28, 307–327. [Google Scholar] [CrossRef]
- Zoghbi-Manrique-de-Lara, P. Predicting nonlinear effects of monitoring and punishment on employee deviance: The role of procedural justice. Eur. Manag. J. 2011, 29, 272–282. [Google Scholar] [CrossRef]
- Yan, C.; Ramamurthy, K.; Kuang-Wei, W. Impacts of comprehensive information security programs on information security culture. J. Comput. Inf. Syst. 2015, 55, 11–19. [Google Scholar]
- Rahim, A.R.A.; Shabudin, A.; Nasurdin, A.M. Effects of Job Characteristics on Counterproductive Work Behavior Among Production Employees: Malaysian Experience. Int. J. Bus. Dev. Stud. 2012, 4, 123–145. [Google Scholar]
- Hackman, J.R.; Oldham, G.R. Motivation through the design of work: Test of a theory. Organ. Behav. Hum. Perform. 1976, 16, 250–279. [Google Scholar] [CrossRef]
- Shamir, B.; Salomon, I. Work-at-home and the quality of working life. Acad. Manag. Rev. 1985, 10, 455–464. [Google Scholar] [CrossRef]
- Grant, A.M. The significance of task significance: Job performance effects, relational mechanisms, and boundary conditions. J. Appl. Psychol. 2008, 93, 108–124. [Google Scholar] [CrossRef] [Green Version]
- Mete Eminağaoğlu, M.; Uçar, E.; Eren, Ş. The positive outcomes of information security awareness training in companies: A case study. Inf. Secur. Tech. Rep. 2009, 14, 223–229. [Google Scholar] [CrossRef]
- McCrohan, K.F.; Engel, K.; Harvey, J.W. Influence of Awareness and Training on Cyber Security. J. Internet Commer. 2010, 9, 23–41. [Google Scholar] [CrossRef]
- Da Veiga, A.; Martins, N. Information Security Culture: A Comparative Analysis of Four Assessments. Proc. Eur. Conf. Inf. Manag. Eval. 2014, 8, 49–57. [Google Scholar]
- Bentler, P.M. Comparative Fit Indexes in Structural Models. Psychol. Bull 1990, 107, 238–246. [Google Scholar] [CrossRef]
- Hooper, D.; Coughlan, J.; Mullen, M.R. Structural equation modeling: Guidelines for determining model fit. Electron. J. Bus. Res. Methods 2008, 6, 53–60. [Google Scholar]
- Steiger, J.H. Understanding the limitations of global fit in structural equation modelling. Pers. Individ. Differ. 2007, 42, 893–898. [Google Scholar] [CrossRef]
- Armando, A.; Costa, G.; Merlo, A.; Verderame, L. Formal modeling and automatic enforcement of Bring Your Own Device policies. Int. J. Inf. Secur. 2015, 14, 123–140. [Google Scholar] [CrossRef]
- De las Cuevas, P.; Mora, A.M.; Merelo, J.J.; Castillo, P.A.; García-Sánchez, P.; Fernández-Ares, A. Corporate security solutions for BYOD: A novel user-centric and self-adaptive system. Comput. Commun. 2015, 68, 83–95. [Google Scholar] [CrossRef]
- Dong, Y.; Mao, J.; Guan, H.; Li, J.; Chen, Y. A Virtualization Solution for BYOD With Dynamic Platform Context Switching. IEEE Micro 2015, 35, 34–43. [Google Scholar] [CrossRef]
- Cho, V.; Ip, W.H. A Study of BYOD adoption from the lens of threat and coping appraisal of its security policy. Enterp. Inf. Syst. 2018, 12, 659–673. [Google Scholar] [CrossRef]
- Veljkovic, I.; Budree, A. Development of Bring-Your-Own-Device Risk Management Model: A Case Study from a South African Organization. Electron. J. Inf. Syst. Eval. 2019, 22, 1–14. [Google Scholar]
- Crossler, R.E.; Long, J.H.; Loraas, T.M.; Trinkle, B.S. The Impact of Moral Intensity and Ethical Tone Consistency on Policy Compliance. J. Inf. Syst. 2017, 31, 49–64. [Google Scholar] [CrossRef]
- Zahadat, N.; Blessner, P.; Blackburn, T.; Olson, B.A. BYOD security engineering: A framework and its analysis. Comput. Secur. 2015, 55, 81–99. [Google Scholar] [CrossRef]
- Lee, J.; Warkentin, M.; Crossler, R.E.; Otondo, R.F. Implications of Monitoring Mechanisms on Bring Your Own Device Adoption. J. Comput. Inf. Syst. 2017, 57, 309–318. [Google Scholar] [CrossRef]
- Crossler, R.E.; Long, J.H.; Loraas, T.M.; Trinkle, B.S. Understanding Compliance with Bring Your Own Device Policies Utilizing Protection Motivation Theory: Bridging the Intention-Behavior Gap. J. Inf. Syst. 2014, 28, 209–226. [Google Scholar] [CrossRef]


| N * | Percentage | ||
|---|---|---|---|
| Age (in years): | age1: Below 30 | 138 | 22.8 |
| age2: 31–40 | 261 | 43.1 | |
| age3: 41–50 | 143 | 23.6 | |
| age4: 51–60 | 63 | 10.4 | |
| Gender: | gender0: Male | 298 | 49.7 |
| gender1: Female | 302 | 50.3 | |
| Academic qualification: | education1: Secondary school/certificate | 8 | 1.3 |
| education2: Diploma | 25 | 4.1 | |
| education3: Bachelor’s degree | 467 | 77.4 | |
| education4: Post-graduate | 103 | 17.1 | |
| Job function: | jobfunction1: Sales and marketing | 120 | 19.8 |
| jobfunction2: Accounting and finance | 65 | 10.7 | |
| jobfunction3: Operations, production, and project management | 187 | 30.9 | |
| jobfunction4: Information systems and technology | 149 | 24.6 | |
| jobfunction5: Facilities | 15 | 2.5 | |
| jobfunction6: Human resources and corporate communication | 62 | 10.2 | |
| jobfunction7: Security and risk management | 8 | 1.3 |
| Items | Mean | Low | Moderate | High |
|---|---|---|---|---|
| Mobile security practices * | ||||
| Use unofficial webmail to perform office duties such as sending sensitive information/documents (e.g., @yahoo.com; @hotmail.com). | 1.762 | 82.8% | 12.1% | 5.1% |
| Access work-related emails via public networks such as Wi-Fi provided by a restaurant. | 2.625 | 51.4% | 37.3% | 11.3% |
| Protect mobile devices such as handphones, tablets, and laptops with passwords, PINs, patterns, or other access control methods. | 4.501 | 13.2% | 27.7% | 59.1% |
| Change your mobile devices’ passwords, PINs, patterns, or other access control methods at regular intervals. | 3.374 | 28.6% | 48.9% | 22.7% |
| Security Monitoring * | ||||
| Conducts audit to detect the use of authorized software on its computers. | 3.1 | 35.0% | 45.7% | 19.3% |
| Reviews logs of employee computing activities. | 3.2 | 34.8% | 46.4% | 18.8% |
| Monitors employee computing activities. | 3.4 | 27.1% | 50.0% | 22.9% |
| Monitors the content of employees’ email messages. | 3.0 | 41.3% | 39.8% | 19.0% |
| Factor Loading | Cronbach’s Alpha | Mean | Std. Dev. | |
|---|---|---|---|---|
| Factor 1: Security monitoring | 0.927 | 3.168 | 1.280 | |
| ST1 | 0.885 | |||
| ST2 | 0.862 | |||
| ST3 | 0.824 | |||
| ST4 | 0.814 | |||
| Factor 2: Security training | 0.909 | 3.515 | 1.251 | |
| SM1 | 0.870 | |||
| SM2 | 0.815 | |||
| SM3 | 0.808 | |||
| SM4 | 0.769 | |||
| Factor 3: Security awareness | 0.875 | 4.166 | 0.992 | |
| SA1 | 0.885 | |||
| SA2 | 0.852 | |||
| SA3 | 0.800 | |||
| SA4 | 0.783 | |||
| Factor 4: Job characteristic | 0.941 | 4.406 | 1.015 | |
| JC1 | 0.945 | |||
| JC2 | 0.930 | |||
| JC3 | 0.928 | |||
| Factor 5: Usage behavior | 0.631 | 4.407 | 1.423 | |
| UB1 | 0.783 | |||
| UB2 | 0.757 | |||
| UB3 | 0.737 | |||
| Hypothesized Paths | β | S.E. | C.R. | Std. β | ||
|---|---|---|---|---|---|---|
| H1: | Expected outcome ➔ Mobile security practices | 0.229 | 0.036 | 6.425 | * | 0.246 |
| H2: | Security inconvenience ➔ Mobile security practices | −0.173 | 0.018 | −9.567 | * | −0.366 |
| H3: | Security inconvenience ➔ Expected outcome | −0.198 | 0.019 | −10.276 | * | −0.392 |
| H4: | Usage behavior ➔ Expected outcome | 0.090 | 0.027 | 3.336 | * | 0.122 |
| H5: | Usage behavior ➔ Security inconvenience | −0.239 | 0.057 | −4.148 | * | −0.164 |
| H6: | Security awareness ➔ Expected outcome | 0.306 | 0.141 | 3.730 | * | 0.096 |
| H7: | Security awareness ➔ Security inconvenience | −1.199 | 0.298 | −4.720 | * | −0.190 |
| H8: | Security monitoring ➔ Expected outcome | −0.278 | 0.097 | −3.242 | * | −0.112 |
| H9: | Security monitoring ➔ Security inconvenience | −0.444 | 0.207 | −2.515 | * | −0.091 |
| H10: | Job characteristic ➔ Usage behavior | 0.403 | 0.171 | 2.362 | * | 0.096 |
| H11: | Job characteristic ➔ Security awareness | 0.144 | 0.032 | 4.042 | * | 0.147 |
| H12: | Job characteristic ➔ Expected outcome | 0.295 | 0.116 | 2.297 | * | 0.085 |
| H13: | Job characteristic ➔ Security inconvenience | 0.250 | 0.249 | 1.163 | 0.041 | |
| H14: | Security training ➔ Security awareness | 0.307 | 0.029 | 10.368 | * | 0.348 |
| N | Percentage | ||
|---|---|---|---|
| Mobile security practice: | Never | 158 | 26.1 |
| Seldom | 64 | 10.6 | |
| Sometimes | 85 | 14.0 | |
| Quite frequent | 144 | 23.8 | |
| Frequent | 52 | 8.6 | |
| Very frequent | 102 | 16.9 |
| N | Percentage | ||
|---|---|---|---|
| Past security experience: | incident0: No known past security incident | 400 | 66.1 |
| incident1: Has prior security incident | 205 | 33.9 | |
| Perceived risk: | risk1: Very unlikely | 60 | 9.9 |
| risk2: Unlikely | 117 | 19.3 | |
| risk3: Quite unlikely | 170 | 28.1 | |
| risk4: Quite likely | 157 | 26.0 | |
| risk5: Likely | 76 | 12.6 | |
| risk6: Very likely | 25 | 4.1 |
| Predictors | χ2 | df | p |
|---|---|---|---|
| Gender | 10.31 | 1 | 0.001 |
| Age | 2.33 | 3 | 0.507 |
| Education | 2.13 | 3 | 0.546 |
| Job function | 13.17 | 6 | 0.040 |
| Past security experience | 6.71 | 1 | 0.010 |
| Perceived risk | 24.07 | 5 | <0.001 |
| 95% Confidence Interval | |||||||
|---|---|---|---|---|---|---|---|
| Predictor | Estimate | SE | Z | p | Odds Ratio | Lower | Upper |
| Gender: | |||||||
| gender1–gender0 | −0.4846 | 0.151 | −3.2013 | 0.001 | 0.616 | 0.457 | 0.828 |
| Age: | |||||||
| age2–age1 | 0.1340 | 0.192 | 0.6991 | 0.485 | 1.143 | 0.785 | 1.666 |
| age3–age1 | 0.3229 | 0.218 | 1.4789 | 0.139 | 1.381 | 0.901 | 2.121 |
| age4–age1 | 0.2371 | 0.283 | 0.8379 | 0.402 | 1.268 | 0.727 | 2.209 |
| Education: | |||||||
| education2–education1 | 0.7973 | 0.751 | 1.0612 | 0.289 | 2.220 | 0.500 | 9.801 |
| education3–education1 | 0.3422 | 0.672 | 0.5091 | 0.611 | 1.408 | 0.367 | 5.339 |
| education4–education1 | 0.2820 | 0.692 | 0.4078 | 0.683 | 1.326 | 0.334 | 5.217 |
| Job function: | |||||||
| jobfunction2–jobfunction1 | −0.3450 | 0.281 | −1.2278 | 0.220 | 0.708 | 0.407 | 1.227 |
| jobfunction3–jobfunction1 | −0.0553 | 0.213 | −0.2594 | 0.795 | 0.946 | 0.623 | 1.437 |
| jobfunction4–jobfunction1 | 0.3679 | 0.221 | 1.6617 | 0.097 | 1.445 | 0.936 | 2.232 |
| jobfunction5–jobfunction1 | 0.0401 | 0.478 | 0.0839 | 0.933 | 1.041 | 0.404 | 2.667 |
| jobfunction6–jobfunction1 | 0.0671 | 0.292 | 0.2296 | 0.818 | 1.069 | 0.602 | 1.896 |
| jobfunction7–jobfunction1 | 1.4460 | 0.638 | 2.2679 | 0.023 | 4.246 | 1.195 | 15.193 |
| Past security experience: | |||||||
| incident1–incident0 | −0.4082 | 0.158 | −2.5867 | 0.010 | 0.665 | 0.488 | 0.905 |
| Perceived risk: | |||||||
| risk2–risk1 | 0.2918 | 0.289 | 1.0109 | 0.312 | 1.339 | 0.761 | 2.362 |
| risk3–risk1 | −0.2100 | 0.274 | −0.7667 | 0.443 | 0.811 | 0.474 | 1.388 |
| risk4–risk1 | −0.7391 | 0.279 | −2.6494 | 0.008 | 0.478 | 0.276 | 0.825 |
| risk5–risk1 | −0.5012 | 0.318 | −1.5778 | 0.115 | 0.606 | 0.325 | 1.129 |
| risk6–risk1 | −0.1187 | 0.454 | −0.2615 | 0.794 | 0.888 | 0.363 | 2.163 |
| Model | −2 Log Likelihood | Chi-Square | df | Sig. |
|---|---|---|---|---|
| Null hypothesis | 1639.435 | |||
| General | 1571.328 b | 68.107 c | 76 | 0.729 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmad, Z.; Ong, T.S.; Gan, Y.W.; Liew, T.H.; Norhashim, M. Predictors of Employees’ Mobile Security Practice: An Analysis of Personal and Work-Related Variables. Appl. Sci. 2022, 12, 4198. https://0-doi-org.brum.beds.ac.uk/10.3390/app12094198
Ahmad Z, Ong TS, Gan YW, Liew TH, Norhashim M. Predictors of Employees’ Mobile Security Practice: An Analysis of Personal and Work-Related Variables. Applied Sciences. 2022; 12(9):4198. https://0-doi-org.brum.beds.ac.uk/10.3390/app12094198
Chicago/Turabian StyleAhmad, Zauwiyah, Thian Song Ong, Yen Wen Gan, Tze Hui Liew, and Mariati Norhashim. 2022. "Predictors of Employees’ Mobile Security Practice: An Analysis of Personal and Work-Related Variables" Applied Sciences 12, no. 9: 4198. https://0-doi-org.brum.beds.ac.uk/10.3390/app12094198