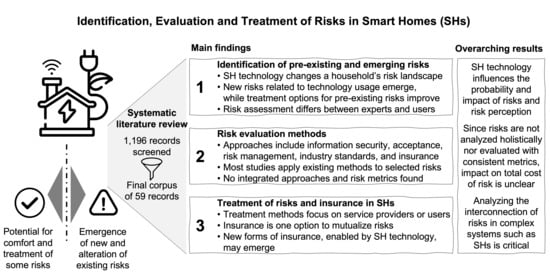
On the Identification, Evaluation and Treatment of Risks in Smart Homes: A Systematic Literature Review
Abstract
:1. Introduction
2. Methodology
2.1. Review Strategy and Data Collection
2.2. Descriptive Statistics
Frequency analysis of the screened records
Text mining on the final body of records
2.3. Data Synthesis
- Risk identification. The difficulty of identifying risks for SHs resides in having different terminologies due to the diversity of disciplinary origins. We present our findings on risk in SHs in Section 3 and attempt to keep a simple structure. For this reason, we adopt the risk management framework ISO 31000 (ISO, International Organization for Standardization 2018). That framework is generally applicable, simple to use and proven in the corporate context. We summarize the identified risks along their influence on impact and acceptance (see Table 1 in Section 3 and Table A3 in Appendix A).
- Risk evaluation. Methods to assess risks can be found in different research areas. In Section 4, we present the risk evaluation methods available from the literature and attribute them to the respective disciplines. Findings from academic literature are synthesized together with the methods found in practitioners’ studies (see Table 2 in Section 4).
- Risk treatment and insurance. Finally, selecting and implementing appropriate measures to address risks of SHs represents a nascent topic of SH risk research. However, the focus here is still entirely on cyber risks. Since we cannot fall back on any established concepts for structuring, the measures are divided into two categories. The first presents options that act as recommendations for SH providers. The second presents options for the users. The effect of SH on insurance, which represent a treatment option in their own right, is further discussed in depth.
3. Risk Identification
3.1. Emerging Risks
- Privacy. We find emerging cyber risks related to privacy and cyber security among the most relevant risks for SH (Loi et al. 2017). Privacy risks refer to the inappropriate handling of personal user data collected from SH (Gerber et al. 2019). As devices, like surveillance cameras or personal wearables, become part of the SH ecosystem, Jacobsson et al. (2016), among others, names privacy risks as the most undesirable consequence. Sovacool and Furszyfer Del Rio (2020), for example, attributes the highest probability of occurrence to privacy risks, while Park et al. (2019) attribute the highest severity to it. In addition, Tanczer et al. (2018) sees the status of privacy as the most fundamental risk under the dynamics of SH. The authors further warn that privacy risks are most likely to be accepted on an individual level, thus creating long-term risks for society as a whole.In research on the acceptance of SH technology and services, perceived privacy risks are extensively analyzed. Several studies state that privacy risks contribute the strongest to the users’ overall risk perception (Marikyan et al. 2019). Interestingly, all studies agree that while privacy risks have a strong influence on risk perception, overall risk perception does not influence acceptance (Kim et al. 2017; Klobas et al. 2019; Wang et al. 2020). Hubert et al. (2019) shares the opinion but argue that perceived privacy risks remain significant in the context of adoption, as they have an indirect influence on other acceptance variables. Studies from Alaiad and Zhou (2017) and Wilson et al. (2017) also conclude that perceived privacy risks are not the most relevant factor for the overall risk perception. Park et al. (2018) categorizes the surveyed sample into three groups: low, moderate and high overall risk perceivers. For the low risk perceivers, privacy risks do not influence the overall risk perception, whereas for the modest and high risk perceivers, they have the largest influence. Lastly, the work of Hong et al. (2020) show no direct influence of perceived privacy risks, and thereby does not investigate the overall risk perception.In our literature study, we found two unique approaches to perceived privacy risks. On the one hand, Lee (2020) analyzes how users perceive certain vulnerabilities. Vulnerabilities relating to user behavior are perceived as the most significant, technology vulnerabilities also result to be important, legal vulnerabilities are considered vaguely significant and provider vulnerabilities are not significant. On the other hand, Gerber et al. (2019) compares the significance of perceived privacy risk in the overall risk perception in SHs to the significance in social media and in smart health. Especially abstract risk scenarios, where consequences of privacy are rather vaguely defined without suggesting how users might be damaged (e.g., collection of usage patterns) are perceived the most likely, yet, in terms of severity, rated similarly significant throughout all domains.Overall, we conclude that privacy risks are well-researched. Within the field of information security, experts’ analyses of cyber risks consistently emphasize the importance of privacy risks. The literature points also to a large body of studies in the context of technology acceptance, although there is not yet conclusive agreement on the influence of privacy risks on acceptance.
- Cyber security. In contrast to the misuse of personal data associated with privacy risks, cyber security risks refer to vulnerabilities and threats in hardware, software, and data of SH devices and services (Klobas et al. 2019). Technical studies providing risk analysis in this context are numerous. Across all studies, statements can be assigned to one of the following three themes, namely asset, vulnerability, or threat. The interplay of these three aspects leads to the definition of a given cyber risk. For example, Ali et al. (2019) defines a cyber risk as the potential loss caused to the SH ecosystem by a threat exploiting certain vulnerabilities. Assets are typically defined at the beginning of the risk analysis, based on a given SH architecture (Alexandrov et al. 2019; Ali et al. 2019; Jacobsson et al. 2016). Such assets include sensors, gateways, servers, application programming interfaces, mobile devices, and the mobile device apps. Within these components of the SH architecture, certain categories, such as software, hardware, information, communication protocols, and human factors, are ubiquitous. Overall, the assets that are qualified as risky are mostly those that are used and whose properties are configured by the end user. Thus, cyber risks primarily arise from software and mobile devices and the related applications and services.Most reviewed studies proceed by identifying vulnerabilities of SHs based on the assets. In particular, the work by Jacobsson et al. (2016) is most comprehensive. In their study, 4 of 32 vulnerabilities result in high risks, 19 are classified as medium risks, 9 are low risks. The most relevant vulnerabilities are poor password selection, sloppy end user, gullible users and software security in applications. They all belong to the asset categories of human factors and software. Various studies emphasize the importance of human factors (e.g., Ali and Awad 2018; Li et al. 2018; Van Hoorde et al. 2018) and stress the relevance of software vulnerabilities (e.g., Ali et al. 2019).A threat can be defined as a potential action that results in a loss (Ali et al. 2019). New capabilities of smart homes enable new types of attacks while permitting traditional attacks with novel consequences (Denning et al. 2013). The literature emphasizes this trend and discusses threats in greater detail compared to assets or vulnerabilities. Most studies derive threats on the basis of previously identified vulnerabilities and the assets thereof. Jacobsson et al. (2016) identifies, in order of rank, circumvention of authentication mechanism, social engineering and unauthorized modification to a system as the top three threats to SHs. All are mainly caused by human-software combinations. The authors also note privacy and manipulation threats to hardware and communication protocols. Van Hoorde et al. (2018) emphasizes the fact that hardware-related manipulation should not be neglected, yet prioritize threats linked to privacy disclosure, inadequate access control and malware mitigation. Threats targeted toward smartphones, due to high risk exposure, are considered by Brauchli and Li (2015) the most relevant. Another prominent approach evaluates specific forms of attacks. Thereby, possible attacks from areas, such as information security, are summarized and then evaluated by assessing the vulnerabilities and assets (see Blythe and Johnson 2019 for an overview). There is a consensus that attacks with denial of service and eavesdropping are main threats (Ali et al. 2019; Nurse et al. 2016). Finally, some concepts take an in-depth look at the threats for a specific SH technology (e.g., RFID, Zigbee and Wi-Fi technologies in Krishnan et al. 2017; Zigbee technology in Wongvises et al. 2017).In risk analyses from technology acceptance research, the perceived importance of cyber security risks is minimal. Park et al. (2018) attributes minimal influence of cyber security to the overall risk perception, while Wang et al. (2020) attributes none at all. A possible reason for this could be the lack of understanding and the complexity of the topic, which prevents perception at all (Mani and Chouk 2017). Therefore, Klobas et al. (2019) analyzes cyber security risks separately from other risks.We conclude that cyber security is a major research subject in information security risk analyses. Human factors and software components are presented as critical sources of risks. Comparing these results to the technology acceptance literature illustrates how risk assessment depends on the perspective. Users rate the significance of cyber security risks as less important than information security experts.
- Performance. The loss in performance of a SH product or service is linked to an emerging performance risk (Hong et al. 2020). Typically, performance risks stem from considerations about topics of broader technological interest and, thus, have almost general applicability to all technologies (Sovacool and Furszyfer Del Rio 2020). Risks, such as technical reliability, warranties, or obsolescence, should be noted here. In studies from acceptance research, perceived performance risks are largely considered irrelevant (Hubert et al. 2019; Wang et al. 2020). Yet, the work of Park et al. (2018) highlights the perceived performance risks. They categorize the surveyed sample (1008 respondents) into three groups, depending on the resulting level of total risk perception. For the middle group, perceived performance risks resulted as the most significant. Hong et al. (2020) follows a similar approach, dividing the surveyed sample (553 respondents) into SH technology rejecters and postponers. For both, performance risk is perceived as relevant, even if only mediocre.
- Dependence. According to Sovacool and Furszyfer Del Rio (2020), there is a risk that SH technologies become a black box for average households, leading to isolation, vulnerability to fraud or lock-in effects. In the study by Wilson et al. (2017), other aspects, like mental aspects of a resulting dependence, are identified (e.g., SH as non-essential luxuries or driver of laziness). In acceptance research, the increase in dependence is studied as the effect of SHs on users’ control perception (Sovacool and Furszyfer Del Rio 2020). Initially, SHs were supposed to increase control. However, usage may also result in a loss of control (Wilson et al. 2017). Such risks potentially have negative effects on the users’ peace of mind. Hong et al. (2020) considers that dependence risks become increasingly important and have, for example, stronger influence on the overall risk perception than performance risks.
- Access to technology. On a societal level, new risks related to the access to SH technology emerge. From a risk perspective, this is a distinct but cross-cutting risk. The exposure to today’s pre-existing risks, such as water or fire, which we will address below, can largely be attributed to socio-economic factors (Banks and Bowman 2018). Today, it is still unclear whether SHs reinforces the significance of these factors or balance them out socially (Nilson and Bonander 2020).
- Social isolation.Marikyan et al. (2019) and Sovacool and Furszyfer Del Rio (2020) identify two types of social isolation. Besides the social divide in terms of technology access that may emerge, SH technology and services can lead to increasing technology-human interactions, and thereby displace human-human interactions. These considerations are closely related to human detachment concerns, which are a prominent topic in SH acceptance research. Users of SHs may feel disconnected from interpersonal contact and especially in SH studies with elderly users or with a clear health focus, such concerns are dominant (Alaiad and Zhou 2017).
- Legal. A study from the acceptance research area mentions that users perceive a certain risk associated with the lack of corporate accountability of SH vendors (Sovacool and Furszyfer Del Rio 2020). These considerations embody the user perspective and originate from unclear regulatory conditions or potentially limited longevity of vendors, as the latter are often start-ups.
- Time. Perceived time risk refers to the time wasted when using SH technologies (Wang et al. 2020). However, this risk has been found to be insignificant in other studies (Klobas et al. 2019; Wang et al. 2020).
3.2. Pre-Existing Risks
- Theft.Blythe and Johnson (2019) map specific attacks related to cyber security to pre-existing risks. On the one hand, they emphasize that exploiting insecure SH devices by eavesdropping offers criminals a wider variety of options to perform crimes, such as stalking or burglary. On the other hand, insurance experts (AXA 2019; Octotelematics 2019) see significant advantages of SH technologies concerning theft. They refer for example to a study of the Federal Bureau of Investigation (2016), where the probability of a burglary rose by 300% if no preventive measures were in place. Light and camera systems play a crucial role here. One may conclude that crime risk, mainly associated to burglary and theft, is changing, but a consensus is not yet found in the literature. In addition, studies on theft provide some initial indications of connections between SH risks.
- Waste of resources. SH is promoted as an important lever for new climate targets. Using the example of intelligent ventilation systems, Psomas et al. (2017) show how SHs can foster a more careful and targeted use of resources. However, other studies show how the increasing data consumption resulting from SH technologies greatly increases global electricity usage (Vidal 2017) or even daily household labor (Strengers and Nicholls 2017) and, thus, reinforce unsustainable energy consumption (Tirado Herrero et al. 2018).
- Financial. Unexpected additional expenses or loss of income are often the results of household damages (i.e., fire, water, burglary) (Tanczer et al. 2018). The SH context broadens the potential sources of financial consequences. According to a study by Hartford Steam Boiler (HSB) insurance company (Milewski 2017), 87% of the victims of cyber attacks in the U.S. suffered financial losses. Likewise, derived as a consequence of potentially increased dependence, there is a real risk that SH technologies leads to greater financial dependence (Sovacool and Furszyfer Del Rio 2020). Thus, emerging risks come with relevant new financial risks and many pre-existing risks ultimately have a financial impact on the household’s individual.In technology acceptance studies, perceived financial risks denote the possibility by which the product or service may not be worth its price (Hong et al. 2020). However, numerous studies find that the influence of perceived financial risks on overall risk perception is not significant (Alaiad and Zhou 2017; Hong et al. 2020; Kim et al. 2017; Sovacool and Furszyfer Del Rio 2020; Wang et al. 2020). The work of Park et al. (2018) is an exception as they point out that, in those that perceive financial risks as low, they have by far the greatest influence on the overall risk perception.
- Fire. Average fire-related insurance claims are the most expensive losses for non-SH households (Insurance Information Institute 2020). Several studies point to SHs’ potential in reducing the probability, as well as the severity of a fire incident (Feuerstein and Karmann 2017). Roost (Goldberg et al. 2019), an insurtech whose business model is built on the use of SH, reports a 15% reduction in claims frequency. BI Intelligence (Meola 2016) sees even greater potential in reducing the severity of the risk. Banks and Bowman (2018) confirm the potential mitigation of fire risk by SHs. Likewise, in comparison to commercial buildings, the potential of SH technologies for private households becomes especially obvious (Salhi et al. 2019). While the use of SH to prevent and treat fire risk is widely discussed, we found no indication of a change of the underlying risk.
- Water. The risk of water damage is assessed in insurance practitioners’ studies. Contrarywise to fire losses, the probability of water damage is high and the severity low (Insurance Information Institute 2020). ACE Group (2011) points out that 93% of all insurance costs from water damage could be prevented by SH technology. More recently, an empirical study from LexisNexis (Davis 2020b) confirm the finding by comparing households equipped with and without water sensors. One year after the installation of sensors, SHs saw a 96% decrease in paid water leakage claims and a 72% decrease in claims severity, while the control group recorded a 10% increase in frequency with unchanged severity levels. The risk of flooding has its own major field of research intensively discussing risk treatment measures. SH technology is listed by Azam et al. (2017) for reducing the severity of potential losses.
- Health. Many SH use cases seek to promote health and well-being (Alam et al. 2012; Ehrenhard et al. 2014). In contradiction to these benefits, it is unclear whether new health risks arise from SH use (Sovacool and Furszyfer Del Rio 2020; Tanczer et al. 2018). The literature related to technology acceptance is scarce (Sovacool and Furszyfer Del Rio 2020). We only found Park et al. (2018) discussing the polarizing issue of electromagnetic radiation. For high risk perceivers, such radiation becomes overwhelmingly salient, while, for moderate and low risk perceivers, radiation leaves a low impact, respectively, negatively affecting the overall risk perception.
- Other property damage. Finally, the reviewed literature mentions other pre-existing risks of non-SH households. The risks of property damage, excluding fire and water, that are discussed are for example wind and hail (Feuerstein and Karmann 2017). Early warning systems based on SH technology demonstrate their positive effect on pre-existing risks. In sum, while SH provides early warning or new risk treatment options, there is no indication of a change in the underlying risk.
4. Risk Evaluation
5. Risk Treatment
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
| Reference | Region | Type | Method | Key Contents and Main Results | RI | RE | RT |
|---|---|---|---|---|---|---|---|
| Alaiad and Zhou (2017) | U.S. | A | Interviews (); survey () | – Human detachment concerns as emerging risks for SH healthcare systems adoption – Other perceived features are privacy concerns, life-quality expectancy, and cost | √ | ||
| Alexandrov et al. (2019) | RU | A | Discussion (information security risk analysis) | – Different types of vulnerabilities lead to similar threats – Lack of backups and unprotected communication change integrity of information – Based on some protective measures identified, some risks are permissible | √ | √ | |
| Ali and Awad (2018) | SE | A | Discussion (information security risk analysis) | – Human factors as largest risk source because of different know-how of SH users – Risks related to cyber or information assets score high, e.g., user credentials and mobile personal data user applications stemming from inadequate authentication | √ | √ | √ |
| Ali et al. (2019) | SA | A | Discussion (systematic literature review) | – Risk defined as damage impacting system by a threat advanced from vulnerabilities – Various vulnerabilities identified and described, e.g., heterogeneous architecture – Various threats identified and described, e.g., DoS or eavesdropping | √ | √ | |
| Azam et al. (2017) | KR | A | Case study (floods in Mushim stream region) | – Frequency and impact of natural disasters native to hydrological events increase – In South Korea, floods cause the greatest damage among all natural disasters – SH as a potential risk treatment option | √ | ||
| Balakrishnan et al. (2018) | MY | P | Discussion (systematic literature review) | – Some factors prevent mass commercialization of SH systems, e.g., interoperability, relevance of extracted data, security and privacy, cost, or societal changes – Expectations, user involvement, and capability of the systems act as constraints | √ | ||
| Blythe and Johnson (2019) | UK | A | Discussion (systematic literature review) | – At least half of all crime now committed online, IoT represents substantial part – Different IoT ecosystems suffer from this trend; home is heavily exposed to it – New types of crimes include burglary, stalking, sex crimes, and political subjugation | √ | ||
| Bondarev and Prokhorov (2017) | RU | P | Discussion (information security risk analysis) | – Filtering of outward parameters proposed to treat internal SH threats – Internal threats are threats to sensor, servers and other hardware components – Sensor failures categorized in equipment, software, network, or human factor | √ | √ | |
| Brauchli and Li (2015) | U.S. | P | Case study (SH digitalSTROM environment) | – Attack vectors can be grouped into vulnerability categories – Categories are server, communication bus, control-device, and third party services – Control-device refers to the greatest risk | √ | ||
| Bugeja et al. (2017) | SE | P | Discussion (information security risk analysis) | – Threat agents are nations, terrorists, organized crime, hacktivists, thieves, hackers – Threat motivations are curiosity, personal gain, terrorism, and national interests – Combination of intruders, motivations, and capabilities lead to a new threat model | √ | ||
| Clark et al. (2015) | UK | A | Discussion (UK fire incidents statistics) | – Percentage of dwelling fires relatively to all fires tends to increase in the past decade – Fires are not equally distributed across socio-demographic or geographical domains – Social science should be included in fire risk analysis | √ | √ | |
| Dahmen et al. (2017) | U.S. | A | Case study (CASAS SH framework) | – Improving home security is a practical use case for SH – Monitoring activity-based anomalies supports detection and treatment of threats – Anomalies naturally exist; thus, not all represent security threats | √ | ||
| Gerber et al. (2019) | DE | A | Survey (, technology acceptance) | – Abstract risk scenarios are perceived as likely, but only moderately severe – Specific risk scenarios are perceived as moderately likely, but rather severe – Specific risk scenarios has great influence on users’ risk perception | √ | ||
| Hong et al. (2017) | KR | P | Survey (, technology acceptance) | – Perceived risks divided into performance, financial, privacy, and psychological risk – Only minor differences when surveyed sample divided into postponers and rejecters – Exception forms perceived privacy risks and perceived financial risks | √ | ||
| Hong et al. (2020) | KR | A | Survey (, technology acceptance) | – Perceived risks divided into performance, financial, privacy, and psychological risk – Only minor differences when surveyed sample divided into postponers and rejecters – Exception from perceived privacy and financial risks | √ | ||
| Hubert et al. (2019) | DE | A | Survey (, technology acceptance) | – Overall risk perception (ORP) is a valid inhibitor of use intention and acceptance – Perceived usefulness predictors are more significant to acceptance than ORP – Perceived security risk contributes strongest to ORP, followed by performance risk | √ | ||
| Jacobsson et al. (2014) | SE | P | Interviews () | – Most significant risks result from combination of software and human end-user – Security and privacy mechanisms to be included in design phase of SH – Enforcing privacy in IoT environments is main barrier to realize the vision SH | √ | √ | |
| Jacobsson and Davidsson (2015) | SE | P | Interviews () | – Most significant risks result from combination of software and human end-user – Security and privacy mechanisms to be included in design phase of SH – Enforcing privacy in IoT environments is main barrier to realize the vision SH | √ | √ | |
| Jacobsson et al. (2016) | SE | A | Interviews () | – Most significant risks result from combination of software and human end-user – Implementation of standard security features significantly reduces software risks – Human factors need careful consideration as they are inherently complex to handle | √ | √ | √ |
| James (2019) | U.S. | P | Discussion (authors’ expertise) | – Recently, there has been a great deal of SH device development – Risk model based on probability, impact, attractiveness as compromised platform – Human factors and security goals considered as main features to determine impact | √ | √ | |
| Kim et al. (2017) | KR | A | Survey (, value-based adoption model) | – Privacy risk and innovation resistance were found to limit perceived value – Yet, perceived benefits have a stronger influence on perceived value – SH acceptance affected more by positive factors than risks | √ | ||
| Kirkham et al. (2014) | UK | A | Case study (connected washing machine) | – Risk-based integrated management of devices improves utilization of home resources – Risk calculated as sum of legal risk, appliance failure risk, and resource security risk – Holistic view on risk includes trust, risk, eco-efficiency, cost, and their relationship | √ | √ | |
| Klobas et al. (2019) | AU | A | Survey (, technology acceptance) | – Perceived security risks have a significant indirect effect on SH adoption decisions – Indirect influence is equally important for acceptance – Guiding users to develop knowledge and skills needed for secure use is key | √ | ||
| Krishnan et al. (2017) | IN | P | Scenario-based analysis (authors’ expertise) | – RFID security threats are eavesdropping, physical attacks, DoS, and spoofing – For Zigbee, they are replay attack, eavesdropping, data manipulation – For WiFi, they are MITM attacks, eavesdropping, DoS, and packet re-routing | √ | ||
| Lee (2020) | KR | A | Survey (, resistance theory) | – Influence of users’ privacy concerns on resistance statistically confirmed for SH – Privacy vulnerabilities are categorized into technology, law, provider, and user – User vulnerabilities have the strongest impact on SH users privacy concerns | √ | ||
| Li et al. (2018) | CN | A | Discussion (information security risk analysis) | – Effective risk management for smart cities combines different evaluation techniques – Threats in natural, contrived, and physical aspects are most relevant for cyber risks – Policy measures should educate, improve public safety, and provide guidance | √ | ||
| Marikyan et al. (2019) | UK | A | Discussion (systematic literature review) | – SHs share three aspects: technology, services, and ability to satisfy users’ needs – Perceived risks act as significant barriers to adoption – Technological barriers are the most important factors to be addressed | √ | ||
| Nawir et al. (2016) | MY | P | Discussion (authors’ expertise) | – Clear outline of various attack types supports development of apt security measures – Resulting taxonomy divides attack types into device property, location, strategy, access level, protocol, information damage, host, and communication stack protocol | √ | ||
| Nilson and Bonander (2020) | SE | A | Survey (, household panel) | – Large risk reductions in fire-related deaths observed in most high-income countries – Reductions are disproportionate for different socio-demographic groups – Household fires remain a considerable societal problem | √ | ||
| Nurse et al. (2016) | UK | P | Discussion (authors’ expertise) | – Accessibility of security and risk management process promotes risk understanding – Risk frameworks include use case definition, assets & network analysis, threat & attack analysis, risk definition & prioritization, and control definition & alignment | √ | √ | |
| Park et al. (2018) | KR | A | Survey (, technology acceptance) | – Perceived risks include financial, performance, security, privacy, and health risk – Electromagnetic radiation (EMR) as one health risk with great influence on ORP – Experts emphasize cyber security risks, but users are more likely to perceive EMR | √ | ||
| Park et al. (2019) | KR | A | Scenario-based analysis (FAIR risk analysis) | – Risk = Threat × Vulnerability × Impact, where Threat × Vulnerability = Likelihood – Existing qualitative risk assessments update on risk indicators once determined – Risk distribution can change with each scenario, country, and time | √ | √ | |
| Pechon et al. (2021) | BE | A | Actuarial rate making (policies ) | – Dependence between home and motor insurance claims frequency – Multivariate credibility models allow to better identify the riskiest households | √ | √ | |
| Psomas et al. (2017) | DK | A | Case study (summer window ventilation) | – Trends towards nearly-zero energy houses increases overheating occurrences indoors – Use of automated roof window control system truly decreases overheating risk – Comes without any significant compromise of the indoor air quality | √ | ||
| Salhi et al. (2019) | JP | P | Case study (fire and gas leakage) | – Smoke and fire detection devices considered as first line of defense to leakage risk – Compared to industrial domains, detection systems in residential houses are basic – Detection systems work separately and are not embedded in home ecosystem | √ | ||
| Schiefer (2015) | DE | P | Discussion (authors’ expertise) | – Higher market penetration makes SH devices more attractive for offenders – Raw sensors are limited on memory and computing power – Lower risk to be target of an attack | √ | ||
| Sovacool and Furszyfer Del Rio (2020) | UK | A | Interviews (); retail visits | – Privacy and security risks rank highest, health risk lowest – Several other technical issues are seen as barriers to adoption, e.g., reliability – Ability to better manage energy services is the most prominent benefit | √ | ||
| Tanczer et al. (2018) | UK | P | Interviews (, IoT experts) | – Four emerging risk patterns are extracted for all IoT risk scenarios (incl. home) – Physical safety, crime and exploitation, loss of control, and social norms and structures are named | √ | √ | |
| Varghese and Hayajneh (2018) | U.S. | P | Case study ( popular SH devices) | – Frameworks for SH product purchase decision are available – Almost all products fail to effectively promote security awareness – Security awareness is particularly missed on product packaging or product website | √ | √ | |
| Wang et al. (2020) | AU | A | Survey (, technology acceptance) | – Individuals ignore potential risks and focus on potential benefits from SH usage – Perceived privacy, performance, and time risk significantly influence ORP – Perceived security and financial risk have no influence on ORP | √ | ||
| Wilson et al. (2017) | UK | A | Interviews (); survey () | – Ceding autonomy and independence are the main perceived risks – Policy-makers can play an important role in mitigating perceived risks – They support design and operating standards, guidelines on data privacy, and more | √ | ||
| Wongvises et al. (2017) | TH | P | Case study (Zigbee lighting system) | – In Fault Trees, top event is systems’ failure and basic events components’ failures – Events leading to failure are compromising sensors, vulnerable controlling device, infection attack, and DoS attack | √ | √ |
| Reference | Region | Type | Method | Key Contents and Main Results | RI | RE | RT |
|---|---|---|---|---|---|---|---|
| ACE Group (2011) | U.S. | R | Discussion (insurance claims, 2007–09) | – Water caused annually USD 9.1 billion property losses from 2007 to 2009 – Losses from water claims reflect 23% of all property losses – 93% could been minimized with automatic water leak detection and shut-off system | √ | √ | |
| Banks and Bowman (2018) | AU | R | Interviews () | – Low-income households live in areas rated high risk with the highest premiums – Improvements in detecting or preventing risks have impact on risk assessment – With access to SH, low-income households may benefit particularly | √ | √ | |
| Davis (2020a) | U.S. | R | Survey (, technology acceptance) | – SH devices meet needs, such as convenience, energy savings, or desire being modish – Adoption rates of specific devices indicate perception of certain needs – For example, 75% own a smoke detector, 2/3 a thermostat or security installation | √ | ||
| Davis (2020b) | U.S. | R | Experiment (water sensor claims) | – One year with sensor, SH homes saw a 96% decrease in paid water leak claims – Within the same period, control group’s claims (without sensor) increased by 10% – Severity decreased by 72% after one year (remained stable in the control group) | √ | √ | |
| Donlon (2015) | U.S. | I | Case study (wine storage) | – Top five claims for wine received by AIG from 2004 to 2014 are water damage (26%), power outage (25%), theft (21%), natural catastrophe (18%), breakage (10%) – SH may reduce severity of loss, especially for power failure or temperature drops | √ | √ | |
| Fasano et al. (2017) | CH | R | Discussion (authors’ expertise) | – Time is a key factor when dealing with domestic damages – Cost of damage increases at rate of USD 3000 per fire per minute of response time – Predictive modeling around behavior within the home will become a key domain | √ | √ | |
| Feuerstein and Karmann (2017) | CH | R | Discussion (authors’ expertise) | – At present, behavior is not taken into account beyond claims data – Studies suggest behavioral changes can significantly reduce risk exposure – Claims data for all insurance-related risks are assessed | √ | √ | |
| Fitzpatrick (2019) | U.S. | I | Discussion (author’s expertise) | – Worthwhile SH devices have low acquisition cost compared to premium counterparts – Fire alarms have the most attractive ratio | √ | ||
| InsuranceInformation Institute (2020) | U.S. | R | Discussion (insurance claims, 2014–18) | – Homeowner losses are ranked by claims severity and frequency – Fire losses are highest in severity, and wind & hail are highest in probability | √ | ||
| König et al. (2017) | AT | R | Survey (, IoT experts) | – Main risk in healthcare settings is that devices are used by inexperienced people – Another risk is that devices may compromise privacy – Devices may also introduce safety hazards | √ | √ | |
| Marsh Private Client Services (2020) | U.S. | R | Discussion (insurance claims, 2016) | – Cooking equipment is leading cause of home fires, igniting 46% of all home fires – In order of priority, candles, electrical causes, heating, and smoking follow | √ | ||
| Matera and Salvador (2018) | IT | R | Discussion (authors’ expertise) | – Proposed risk evaluation method builds on objective and quantitative analyses – Measures include maximum possible loss and normal loss expectancy – Novel approaches emphasize importance of risk prevention | √ | √ | |
| Milewski (2017) | U.S. | R | Survey | – 87% of cyber attack victims suffer from financial losses by paying money to attacker – Problem will likely worsen as the number of connected home devices increases – New cyber insurance coverage is one alternative of risk treatment | √ | √ | |
| Octotelematics (2019) | IT | R | Discussion (authors’ expertise) | – Traditionally, insurers use proxy data to identify the risk of loss for an asset – IoT gives access to real-time, individual, and observable data on risks – Data is directly actionable for risk pricing and treatment | √ | √ | √ |
| Sevillano (2018) | CH | R | Survey | – Water, theft, and fire are source of around 50% of insurance claims (2013) – Technology will play a vital role in reducing these risks | √ | √ | |
| Sheng et al. (2017) | CN | R | Discussion (authors’ expertise) | – Individual coverage concepts are complex and time consuming – Technology makes these concepts possible within retail and commercial space – Coverage to adapt automatically and real-time to changing life and risk situations | √ | ||
| Van Hoorde et al. (2018) | BE | B | Discussion (authors’ expertise) | – Threats mainly relate to privacy, inadequate access control and malware mitigation – Additional risks to hardware are theft, manipulation and sabotage – Overall, the end-user still represents one of the weakest links | √ |
| Risk | Source | Events | Consequences | Likelihood | References | |
|---|---|---|---|---|---|---|
| Emerging risks | ||||||
| Privacy | Bundle of highly sensitive information resulting from SH behavior (e.g., unaware usage or threats linked to privacy disclosure) | Specific cyber attacks directed towards data leakage or unauthorized retention of personal data | Inappropriate handling of personal user data collected from SH | High probability, as privacy experiences fundamental change within SH settings and risk often accepted by users | Gerber et al. (2019); Jacobsson et al. (2016); Klobas et al. (2019); Loi et al. (2017); Park et al. (2019); Sovacool and Furszyfer Del Rio (2020); Tanczer et al. (2018) | |
| Cyber security | Inadequate access control and malware mitigation directed to SHs’ user behavior or software (e.g., poor user credentials, identity credential theft, unauthorized modification to systems) | Specific attacks directed at the software-human interface (e.g., eavesdropping, DoS, DDoS) | Damage experienced personally as a user or societal damage building on hijacked personal SH system | High probability, as household-related crime shifts increasingly into the cyber space | Alexandrov et al. (2019); Ali and Awad (2018); Ali et al. (2019); Blythe and Johnson (2019); Brauchli and Li (2015); Denning et al. (2013); Jacobsson et al. (2016); Krishnan et al. (2017); Li et al. (2018); Nurse et al. (2016); Van Hoorde et al. (2018); Wongvises et al. (2017) | |
| Performance | Loss in performance of a SH product or service derived from topics of broader technological interest (e.g., reliability, obsolescence) | n.a. | Uncertainty or experienced loss in performance | n.a. | Hong et al. (2020); Hubert et al. (2019); Park et al. (2018); Wang et al. (2020) | |
| Dependence | Lack of technical understanding, users’ laziness or lack of alternatives to SH | n.a. | Technology dependency or greater laziness with greater levels of usage | n.a. | Alaiad and Zhou (2017); Hong et al. (2020); Sovacool and Furszyfer Del Rio (2020); Wilson et al. (2017) | |
| Access to technology | Technology access disparities related to socio-economic factors or willful non-access | n.a. | Individual isolation from certain SH benefits | n.a. | Nilson and Bonander (2020); Park et al. (2019); Sovacool and Furszyfer Del Rio (2020) | |
| Social isolation | High levels of dependency or non-access to technology | n.a. | Non-access to SH, technology-human interactions displacing human-human interaction or human detachment | n.a. | Alaiad and Zhou (2017); Hong et al. (2020); Park et al. (2019); Sovacool and Furszyfer Del Rio (2020); Wilson et al. (2017) | |
| Legal | Limited longevity of supplier (start-ups) or unclear regulatory conditions | n.a. | Lack of corporate accountability or legal clarity on safeguards in the event of a dispute | n.a. | Sovacool and Furszyfer Del Rio (2020) | |
| Time | n.a. | n.a. | Time wasted when using SH technologies | n.a. | Klobas et al. (2019); Wang et al. (2020) | |
| Pre-existing risks | ||||||
| Theft | Regional aspects, period, infrastructure, behavior or insecure SH systems | Break-in | Physical or psychological consequences | Low probability, compared to other pre-existing risks, such as water | AXA (2019); Blythe and Johnson (2019); Nurse et al. (2016); Octotelematics (2019); Tanczer et al. (2018); Van Hoorde et al. (2018) | |
| Waste of resources | Unenlightened use of technology and additional devices that are powered and connected to the internet | n.a. | Increase in global electricity usage or increase in daily household labor | n.a. | Hong et al. (2020); Jacobsson et al. (2016); Psomas et al. (2017); Strengers and Nicholls (2017); Tirado Herrero et al. (2018); Vidal (2017) | |
| Financial | Insecure SH systems or extend by which SHs may not be worth the financial price | n.a. | Financial losses (aggregated from all risks) | High probability, as emerging cyber risks entail new financial consequences and also pre-existing risks often result in financial loss | Alaiad and Zhou (2017); Hong et al. (2020); Kim et al. (2017); Milewski (2017); Park et al. (2019); Sovacool and Furszyfer Del Rio (2020); Wang et al. (2020) | |
| Fire | n.a. | n.a. | Health and financial consequences | Low probability, compared to other pre-existing risks, such as water or theft | Feuerstein and Karmann (2017); Goldberg et al. (2019); Meola (2016); Octotelematics (2019); Salhi et al. (2019) | |
| Water | n.a. | Pipes bursting, water overflow, roof leakage, or frost damage | Water waster (leaks waste more than one trillion gallons of water annually in the U.S.) | High probability, compared to other pre-existing risks, such as fire or theft | ACE Group (2011); Azam et al. (2017); Davis (2020b) | |
| Health | Health-related hazards arising from incorrect use of SH or potentially unknown effects of electromagnetic radiation | n.a. | n.a. | n.a. | Park et al. (2018); Sovacool and Furszyfer Del Rio (2020); Tanczer et al. (2018) | |
| Other property damage | Non-awareness of fragility at certain state | Power outages or long periods of inactivity | Breakage of the item | n.a. | Feuerstein and Karmann (2017) | |
References
- ACE Group. 2011. Device Could Reduce 93 Percent of Homeowner Water Damage Claims. San Diego: Wells Media Group. [Google Scholar]
- Alaiad, Ahmad, and Lina Zhou. 2017. Patients’ Adoption of WSN-Based Smart Home Healthcare Systems: An Integrated Model of Facilitators and Barriers. IEEE Transactions on Professional Communication 60: 4–23. [Google Scholar] [CrossRef]
- Alam, Muhammad Raisul, Mamun Bin Ibne Reaz, and Mohd Alauddin Mohd Ali. 2012. A Review of Smart Homes—Past, Present, and Future. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews) 42: 1190–203. [Google Scholar] [CrossRef]
- Aldrich, Frances K. 2006. Smart Homes: Past, Present and Future. In Inside the Smart Home. London: Springer, Chp. 2. pp. 17–39. [Google Scholar] [CrossRef]
- Alexandrov, Vladislav Andreevich, Vasily A. Desnitsky, and Dmitrii Yur’evich Chaly. 2019. Design and Security Analysis of a Fragment of Internet of Things Telecommunication System. Automatic Control and Computer Sciences 53: 851–56. [Google Scholar] [CrossRef] [Green Version]
- Ali, Bako, and Ali Awad. 2018. Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes. Sensors 18: 817. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ali, Waleed, Sharaf Malebary, Adel A. Ahmed Abdullah, Talal A. A. Abdullah, and Adel Ali Ahmed. 2019. A Review of Cyber Security Challenges, Attacks and Solutions for Internet of Things Based Smart Home. International Journal of Computer Science and Network Security 2019: 139–146, Seoul: IJCSNS. [Google Scholar]
- Amiribesheli, Mohsen, Asma Benmansour, and Abdelhamid Bouchachia. 2015. A review of smart homes in healthcare. Journal of Ambient Intelligence and Humanized Computing 6: 495–517. [Google Scholar] [CrossRef] [Green Version]
- AXA. 2019. Burglary: In Which Canton the Danger is Particularly High. Winterthur: AXA Insurance. [Google Scholar]
- Azam, Muhammad, Hyung San Kim, and Seung Jin Maeng. 2017. Development of flood alert application in Mushim stream watershed Korea. International Journal of Disaster Risk Reduction 21: 11–26. [Google Scholar] [CrossRef] [Green Version]
- Balakrishnan, Sumathi, Hemalata Vasudavan, and Raja Kumar Murugesan. 2018. Smart Home Technologies. Paper presented at 6th International Conference on Information Technology: IoT and Smart City—ICIT 2018, Hong Kong, China, December 29–31; pp. 120–27. [Google Scholar] [CrossRef]
- Banks, Marcus, and Dina Bowman. 2018. Juggling Risks Insurance in Households Struggling with Financial Insecurity. Technical Report. Fitzroy: The Brotherhood of St Laurence. [Google Scholar] [CrossRef]
- Blythe, John M., and Shane D. Johnson. 2019. A systematic review of crime facilitated by the consumer Internet of Things. Security Journal 2019: 1–29. [Google Scholar] [CrossRef]
- Bondarev, Sergey E., and Andrey S. Prokhorov. 2017. Analysis of internal threats of the system “smart home” and assessment of ways to prevent them. Paper presented at 2017 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow, Russia, February 1–3; pp. 788–90. [Google Scholar] [CrossRef]
- Brauchli, Andreas, and Depeng Li. 2015. A solution based analysis of attack vectors on smart home systems. Paper presented at 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC), Shanghai, China, August 5–7; pp. 1–6. [Google Scholar] [CrossRef]
- Braun, Virginia, and Victoria Clarke. 2006. Using thematic analysis in psychology. Qualitative Research in Psychology 3: 77–101. [Google Scholar] [CrossRef] [Green Version]
- Bugeja, Joseph, Andreas Jacobsson, and Paul Davidsson. 2017. An analysis of malicious threat agents for the smart connected home. Paper presented at 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, March 13–17; pp. 557–62. [Google Scholar] [CrossRef] [Green Version]
- Chan, Marie, Daniel Estève, Jean-Yves Fourniols, Christophe Escriba, and Eric Campo. 2012. Smart wearable systems: Current status and future challenges. Artificial Intelligence in Medicine 56: 137–56. [Google Scholar] [CrossRef]
- Clark, Andrew, Jessica Smith, and Carole Conroy. 2015. Domestic fire risk: A narrative review of social science literature and implications for further research. Journal of Risk Research 18: 1113–29. [Google Scholar] [CrossRef]
- Dahmen, Jessamyn, Brian Thomas, Diane Cook, and Xiaobo Wang. 2017. Activity Learning as a Foundation for Security Monitoring in Smart Homes. Sensors 17: 737. [Google Scholar] [CrossRef] [PubMed]
- Davis, Dan. 2020a. Insights and Strategies for Smart Home Insurance Programs. Technical Report. Alpharetta: LexisNexis Risk Solutions. [Google Scholar]
- Davis, Dan. 2020b. Preventing Water Claims: Understanding the Value of Smart Home Technology. Technical Report. Alpharetta: LexisNexis Risk Solutions. [Google Scholar]
- Denning, Tamara, Tadayoshi Kohno, and Henry M. Levy. 2013. Computer security and the modern home. Communications of the ACM 56: 94–103. [Google Scholar] [CrossRef]
- Donlon, Rosalie. 2015. Do You Collect Wine? Here Are Some Tips for Keeping Your Bottles Safe. New York: ALM Media. [Google Scholar]
- Ehrenhard, Michel, Bjorn Kijl, and Lambert Nieuwenhuis. 2014. Market adoption barriers of multi-stakeholder technology: Smart homes for the aging population. Technological Forecasting and Social Change 89: 306–15. [Google Scholar] [CrossRef]
- Fasano, Pierluigi, Cecilia Sevillano, James Stansberry, Leigh Carlton, Arthur Houannic, and Domenico Saravese. 2017. Risk Talk on Smart Homes. Technical Report. Ruschlikon: Swiss Re Centre for Global Dialogue. [Google Scholar]
- Federal Bureau of Investigation. 2016. Uniform Crime Report Crime in the Property Crime. Technical Report. Washington, DC: Federal Bureau of Investigation. [Google Scholar]
- Feuerstein, Daniel, and Maximilian Karmann. 2017. The Insurer’s Playbook on Smart Home Point of View. Technical Report. Zurich: Deloitte. [Google Scholar]
- Fitzpatrick, Marc. 2019. Are Smart Device Home Insurance Discounts Worth It? Charlotte: ValuePenguin. [Google Scholar]
- Gerber, Nina, Benjamin Reinheimer, and Melanie Volkamer. 2019. Investigating People’s Privacy Risk Perception. Proceedings on Privacy Enhancing Technologies 2019: 267–88. [Google Scholar] [CrossRef]
- Goldberg, Jeff, Roel Peeters, and Assaf Wand. 2019. The Present And Future Of Home Telematics. New York: SourceMedia. [Google Scholar]
- Hong, Areum, Changi Nam, and Seongcheol Kim. 2017. Analysis of the barriers that consumers encounter when smart home service is introduced in South Korea. In Mapping ICT into Transformation for the Next Information Society. Kyoto and Calgary: International Telecommunications Society (ITS). [Google Scholar]
- Hong, Areum, Changi Nam, and Seongcheol Kim. 2020. What will be the possible barriers to consumers’ adoption of smart home services? Telecommunications Policy 44: 101867. [Google Scholar] [CrossRef]
- Hosseini, Sayed Saeed, Kodjo Agbossou, Sousso Kelouwani, and Alben Cardenas. 2017. Non-intrusive load monitoring through home energy management systems: A comprehensive review. Renewable and Sustainable Energy Reviews 79: 1266–74. [Google Scholar] [CrossRef]
- Hubert, Marco, Markus Blut, Christian Brock, Ruby Wenjiao Zhang, Vincent Koch, and René Riedl. 2019. The influence of acceptance and adoption drivers on smart home usage. European Journal of Marketing 53: 1073–98. [Google Scholar] [CrossRef]
- Insurance Information Institute. 2020. Facts + Statistics: Homeowners and Renters Insurance. New York: Insurance Information Institute. [Google Scholar]
- International Organization for Standardization. 2018. Risk Management: ISO 31000. Geneva: International Organization for Standardization. [Google Scholar]
- Jacobsson, Andreas, Martin Boldt, and Bengt Carlsson. 2014. On the Risk Exposure of Smart Home Automation Systems. Paper presented at 2014 International Conference on Future Internet of Things and Cloud, Barcelona, Spain, August 27–29; pp. 183–90. [Google Scholar] [CrossRef]
- Jacobsson, Andreas, Martin Boldt, and Bengt Carlsson. 2016. A risk analysis of a smart home automation system. Future Generation Computer Systems 56: 719–33. [Google Scholar] [CrossRef] [Green Version]
- Jacobsson, Andreas, and Paul Davidsson. 2015. Towards a model of privacy and security for smart homes. Paper presented at 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, December 14–16; pp. 727–32. [Google Scholar] [CrossRef] [Green Version]
- James, Fathima. 2019. A Risk Management Framework and A Generalized Attack Automata for IoT based Smart Home Environment. Paper presented at 2019 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, October 23–25; pp. 86–90. [Google Scholar] [CrossRef]
- Kang, Yoolee, and Seongcheol Kim. 2009. Understanding User Resistance to Participation in Multihop Communications. Journal of Computer-Mediated Communication 14: 328–51. [Google Scholar] [CrossRef]
- Keller, Benno, Martin Eling, Hato Schmeiser, Markus Christen, and Michele Loi. 2018. Big Data and Insurance: Implications for Innovation, Competition and Privacy. Zurich: The Geneva Association. [Google Scholar]
- Kim, Yonghee, Youngju Park, and Jeongil Choi. 2017. A study on the adoption of IoT smart home service: Using Value-based Adoption Model. Total Quality Management & Business Excellence 28: 1149–65. [Google Scholar] [CrossRef]
- Kirkham, Tom, Django Armstrong, Karim Djemame, and Ming Jiang. 2014. Risk driven Smart Home resource management using cloud services. Future Generation Computer Systems 38: 13–22. [Google Scholar] [CrossRef] [Green Version]
- Klobas, Jane E., Tanya McGill, and Xuequn Wang. 2019. How perceived security risk affects intention to use smart home devices: A reasoned action explanation. Computers & Security 87: 101571. [Google Scholar] [CrossRef]
- König, Sandra, Stefan Schiebeck, Stefan Schauer, Martin Latzenhofer, Peter Mayer, Geraldine Fitzpatrick, and Iot Risks. 2017. Deliverable 3: Internet of Things Risk Analysis and Assessment. Technical Report. Vienna: The Austrian Research Promotion Agency. [Google Scholar]
- Krishnan, Silpa, MS Anjana, and Sethuraman N. Rao. 2017. Security Considerations for IoT in Smart Buildings. Paper presented at 2017 IEEE International Conference on Computational Intelligence and Computing Research (ICCIC), Tamil Nadu, India, December 14–16; pp. 1–4. [Google Scholar] [CrossRef]
- Lee, Hwansoo. 2020. Home IoT resistance: Extended privacy and vulnerability perspective. Telematics and Informatics 49: 101377. [Google Scholar] [CrossRef]
- Li, Xiaotong, Hua Li, Bingzhen Sun, and Fang Wang. 2018. Assessing information security risk for an evolving smart city based on fuzzy and grey FMEA. Journal of Intelligent & Fuzzy Systems 34: 2491–501. [Google Scholar] [CrossRef]
- Loi, Franco, Arunan Sivanathan, Hassan Habibi Gharakheili, Adam Radford, and Vijay Sivaraman. 2017. Systematically Evaluating Security and Privacy for Consumer IoT Devices. Paper presented at 2017 Workshop on Internet of Things Security and Privacy, Dallas, TX, USA, November 3; pp. 1–6. [Google Scholar] [CrossRef]
- Lutolf, Remo. 1992. Smart Home concept and the integration of energy meters into a home based system. Paper presented at Seventh International Conference on Metering Apparatus and Tariffs for Electricity Supply 1992, Glasgow, UK, November 17–19; pp. 77–78. [Google Scholar]
- Mani, Zied, and Inès Chouk. 2017. Drivers of consumers’ resistance to smart products. Journal of Marketing Management 33: 76–97. [Google Scholar] [CrossRef]
- Marikyan, Davit, Savvas Papagiannidis, and Eleftherios Alamanos. 2019. A systematic review of the smart home literature: A user perspective. Technological Forecasting and Social Change 138: 139–54. [Google Scholar] [CrossRef]
- Marsh Private Client Services. 2020. Fire Safety at Home: Prevention and Precautions. Edmonton: Marsh Private Client Services. [Google Scholar]
- Matera, Fabio, and Emanuele Salvador. 2018. An Innovative Approach to Measuring and Controlling Risk. Technical Report. Boston: Arthur D. Little. [Google Scholar]
- Mazri, Chabane. 2017. (Re) Defining Emerging Risks. Risk Analysis 37: 2053–65. [Google Scholar] [CrossRef]
- Meola, Andrew. 2016. IoT Insurance: Trends in Home, Life & Auto Insurance Industries. New York: Insider Inc. [Google Scholar]
- Mikkonen, Kristina, and Maria Kääriäinen. 2020. Content Analysis in Systematic Reviews. In The Application of Content Analysis in Nursing Science Research. Cham: Springer International Publishing, pp. 105–15. [Google Scholar] [CrossRef]
- Milewski, Dennis. 2017. HSB Cyber Survey Shows Increase in Smart Home Devices Adds New Hacking Risks. Hartford: The Hartford Steam Boiler Inspection and Insurance Company. [Google Scholar]
- Nawir, Mukrimah, Amiza Amir, Naimah Yaakob, and Ong Bi Lynn. 2016. Internet of Things (IoT): Taxonomy of security attacks. Paper presented at 2016 3rd International Conference on Electronic Design (ICED), Phuket, Thailand, August 11–12; pp. 321–26. [Google Scholar] [CrossRef]
- Nilson, Finn, and Carl Bonander. 2020. Household Fire Protection Practices in Relation to Socio-demographic Characteristics: Evidence from a Swedish National Survey. Fire Technology 56: 1077–98. [Google Scholar] [CrossRef] [Green Version]
- Nurse, Jason R. C., Ahmad Atamli, and Andrew Martin. 2016. Towards a Usable Framework for Modelling Security and Privacy Risks in the Smart Home. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics). Berlin: Springer, vol. 9750, pp. 255–67. [Google Scholar] [CrossRef] [Green Version]
- Octotelematics. 2019. The Power of Insurance IoT for Risk Management. Rome: Octotelematics. [Google Scholar]
- Page, Matthew James, David Moher, Patrick Bossuyt, Isabelle Boutron, Tammy Hoffmann, Cynthia Mulrow, Larissa Shamseer, Jennifer Tetzlaff, Elie Akl, Sue E. Brennan, and et al. 2020. PRISMA 2020 Explanation and Elaboration: Updated Guidance and Exemplars for Reporting Systematic Reviews. MetaArXiv Preprint. Charlottesville: Center for Open Science. [Google Scholar] [CrossRef]
- Park, Chankook, Yangsoo Kim, and Min Jeong. 2018. Influencing factors on risk perception of IoT-based home energy management services. Telematics and Informatics 35: 2355–65. [Google Scholar] [CrossRef]
- Park, Mookyu, Haengrok Oh, and Kyungho Lee. 2019. Security Risk Measurement for Information Leakage in IoT-Based Smart Homes from a Situational Awareness Perspective. Sensors 19: 2148. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Pechon, Florian, Michel Denuit, and Julien Trufin. 2021. Home and Motor insurance joined at a household level using multivariate credibility. Annals of Actuarial Science 15: 82–114. [Google Scholar] [CrossRef]
- Psomas, Theofanis, Per Heiselberg, Thøger Lyme, and Karsten Duer. 2017. Automated roof window control system to address overheating on renovated houses: Summertime assessment and intercomparison. Energy and Buildings 138: 35–46. [Google Scholar] [CrossRef]
- Radomirovic, Saša. 2010. Towards a Model for Security and Privacy in the Internet of Things. In Proceedings of the First International Conference on Security of Internet of Things. New York: Association for Computing Machinery. [Google Scholar]
- Reinisch, Christian, Mario J. Kofler, Félix Iglesias, and Wolfgang Kastner. 2011. ThinkHome Energy Efficiency in Future Smart Homes. EURASIP Journal on Embedded Systems 2011: 1–18. [Google Scholar] [CrossRef] [Green Version]
- Salhi, Lamine, Thomas Silverston, Taku Yamazaki, and Takumi Miyoshi. 2019. Early Detection System for Gas Leakage and Fire in Smart Home Using Machine Learning. Paper presented at 2019 IEEE International Conference on Consumer Electronics (ICCE), Berlin, Germany, September 8–11; pp. 1–6. [Google Scholar] [CrossRef]
- Schiefer, Michael. 2015. Smart Home Definition and Security Threats. Paper presented at 2015 Ninth International Conference on IT Security Incident Management & IT Forensics, Magdeburg, Germany, May 18–20; pp. 114–118. [Google Scholar] [CrossRef]
- Scott, Faye. 2007. Teaching Homes to be Green: Smart Homes and the Environment. London: Green Alliance. [Google Scholar]
- Sevillano, Cecilia. 2018. Smart Homes. Paper presented at EMEA Claims Conference, Rüschlikon, Switzerland, March 6–7. [Google Scholar]
- Sheng, Cliff, Dietmar Kottmann, Kang Liu, Kai Prestinari, Xing Jiang, Wei Chen, and Xuefeng Li. 2017. Technology-Driven Value Generation in Insurance. Technical Report. Hong Kong, China: Oliver Wyman. [Google Scholar]
- Sovacool, Benjamin K., and Dylan D. Furszyfer Del Rio. 2020. Smart home technologies in Europe: A critical review of concepts, benefits, risks and policies. Renewable and Sustainable Energy Reviews 120: 109663. [Google Scholar] [CrossRef]
- Strengers, Yolande, and Larissa Nicholls. 2017. Convenience and energy consumption in the smart home of the future: Industry visions from Australia and beyond. Energy Research & Social Science 32: 86–93. [Google Scholar] [CrossRef]
- Tanczer, Leonie Maria, Ine Steenmans, Miles Elsden, Jason Blackstock, and Madeline Carr. 2018. Emerging risks in the IoT ecosystem: Who’s afraid of the big bad smart fridge? Paper presented at Living in the Internet of Things: Cybersecurity of the IoT— 2018, London, UK, March 28–29; vol. 2018. [Google Scholar]
- Thomé, Antônio Márcio Tavares, Luiz Felipe Scavarda, and Annibal José Scavarda. 2016. Conducting systematic literature review in operations management. Production Planning & Control 27: 408–20. [Google Scholar] [CrossRef]
- Tirado Herrero, Sergio, Larissa Nicholls, and Yolande Strengers. 2018. Smart home technologies in everyday life: Do they address key energy challenges in households? Current Opinion in Environmental Sustainability 31: 65–70. [Google Scholar] [CrossRef]
- Tranfield, David, David Denyer, and Palminder Smart. 2003. Towards a Methodology for Developing Evidence-Informed Management Knowledge by Means of Systematic Review. British Journal of Management 14: 207–22. [Google Scholar] [CrossRef]
- Van Hoorde, Kim, Evelien De Pauw, Hans Vermeersch, and Wim Hardyns. 2018. The influence of technological innovations on theft prevention. In Socially Responsible Innovation in Security: Critical Reflections. Edited by J. Peter Burgess, Genserik Reniers, Koen Ponnet, Wim Hardyns and Wim Smit. London: Routledge, Chp. 3. [Google Scholar]
- Varghese, Joel, and Thaier Hayajneh. 2018. A Framework to Identify Security and Privacy Issues of Smart Home Devices. Paper presented at 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, November 8–10; pp. 135–43. [Google Scholar] [CrossRef]
- Vidal, John. 2017. ‘Tsunami of data’ could consume one fifth of global electricity by 2025. Broadstairs: Climate Home News. [Google Scholar]
- Von Gaudecker, Hans-Martin, Radost Holler, Lena Janys, Bettina Siflinger, and Christian Zimpelmann. 2020. Labour Supply in the Early Stages of the COVID-19 Pandemic: Empirical Evidence on Hours, Home Office, and Expectations. Technical Report. Bonn: Institute of Labor Economics (IZA). [Google Scholar]
- Wang, Xuequn, Tanya Jane McGill, and Jane E. Klobas. 2020. I Want It Anyway: Consumer Perceptions of Smart Home Devices. Journal of Computer Information Systems 60: 437–47. [Google Scholar] [CrossRef]
- Wilson, Charlie, Tom Hargreaves, and Richard Hauxwell-Baldwin. 2017. Benefits and risks of smart home technologies. Energy Policy 103: 72–83. [Google Scholar] [CrossRef] [Green Version]
- Wongvises, Chanoksuda, Assadarat Khurat, Doudou Fall, and Shigeru Kashihara. 2017. Fault tree analysis-based risk quantification of smart homes. Paper presented at 2017 2nd International Conference on Information Technology (INCIT), Salaya, Thailand, November 2–3; pp. 1–6. [Google Scholar] [CrossRef]



| Risk | Description | Impact | Acceptance |
|---|---|---|---|
| Emerging risks | |||
| Privacy | Inappropriate handling, disclosure, or use of data collected by SH system leading to interference to the right to keep personal matters private | H | H |
| Cyber security | Inadequate use of hardware or software by user, attacker or others, leading to damages, such as denial of service or mal-performance | H | L |
| Performance | Undesired performance variations resulting from usage of a young technology | – | H |
| Dependence | Degree of dependence that leads to undesired outcomes, such as loss of choice, lock-in, or anxiety | H | H |
| Access to technology | Disparities in access to technology due to, e.g., socio-economic factors, unwillingness to share data | – | L |
| Social isolation | Feeling of loneliness resulting from lacking technology access or increasing substitution of human-human interaction | L | H |
| Legal | Unclear regulatory conditions or supplier longevity leading to uncertainty regarding accountability | L | L |
| Time | Disappointing benefits or opportunity costs in relation to time invested | L | L |
| Pre-existing risks | |||
| Theft | Loss of physical or digital property and non-financial losses as a consequence of unauthorized access, use, and misappropriation | – | – |
| Waste of resources | Unnecessary or wrong use of money, substances, time, energy, or abilities resulting in waste of resources | L | – |
| Financial | Unexpected deterioration of the value of SH system or extra expenses or loss of income leading to financial loss | – | L |
| Fire | Bodily injury, death, property damages, and loss of income resulting from fire in and around the house | L | – |
| Water | Property damages resulting from water leakage in and around the house | L | – |
| Health | Impairments of physical and psychological health resulting from use of SH technology | L | H |
| Other property damage | Non-water or fire related property damage in and around the house | L | – |
| Method | Description | References |
|---|---|---|
| Information security | ||
| Information security risk analysis | Review of a system’s risk exposure based on its ability to fulfill the three basic goals of system security, i.e., confidentiality, integrity, and availability | Alexandrov et al. (2019); Ali and Awad (2018); Ali et al. (2019); Bondarev and Prokhorov (2017); Jacobsson et al. (2016); Tanczer et al. (2018) |
| Failure mode and effects analysis | Identification of potential failure modes (causes, effects, and areas) affecting a system’s safety, reliability, and maintainability; integration of the fuzzy set theory to evaluate failure modes and of the grey relational theory to calculate the degree of relation among failure modes | Li et al. (2018) |
| Fault tree analysis | Boolean logic expressed as tree or diagram, where the top event is the failure of a system, and the other events are components’ failures | Wongvises et al. (2017) |
| Factor analysis of information risk | Risk measurement based on likelihood and probability, consisting of loss event frequency and magnitude factors that represent threats and damage to assets | Park et al. (2019) |
| Acceptance | ||
| Technology acceptance models | Structural equation models where predetermined hypotheses of the risks’ influence on acceptance are assessed through, e.g., perceived risk or resistance theories | Hubert et al. (2019); Kim et al. (2017); Lee (2020); Park et al. (2018) |
| Scenario-based perception differences | Definition of different risk scenarios based on detail level of a resulting consequence (abstract vs. specific) or on the SH use case (health vs. comfort) | Gerber et al. (2019); Hong et al. (2020) |
| Risk management | ||
| ISO 31000 | International risk management standard aiming to develop a common understanding on risk management concepts | James (2019) |
| Individual enhancements | Frameworks based on ISO 31000 specifically adapted to SH settings | Nurse et al. (2016) |
| Industry standards | ||
| ISO 27000 | Best practice in information security management aiming to manage information risks by information security means | König et al. (2017) |
| NIST SP800 | Frameworks developed to address the security and privacy needs, e.g., systems security engineering (NIST SP800-160) and networks of things (NIST SP800-183) | König et al. (2017) |
| ISA/IEC-62443 | Design framework to improve cyber security robustness and resilience in industrial automation control systems | König et al. (2017) |
| Insurance | ||
| Actuarial rate making | Determination of the price charged by insurance companies for pre-existing household risks | Matera and Salvador (2018); Sheng et al. (2017) |
| Claims data analysis | Comparison of insurance claims data from households with and without specific SH products, e.g., water leakage or fire sensors | Davis (2020b) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Iten, R.; Wagner, J.; Zeier Röschmann, A. On the Identification, Evaluation and Treatment of Risks in Smart Homes: A Systematic Literature Review. Risks 2021, 9, 113. https://0-doi-org.brum.beds.ac.uk/10.3390/risks9060113
Iten R, Wagner J, Zeier Röschmann A. On the Identification, Evaluation and Treatment of Risks in Smart Homes: A Systematic Literature Review. Risks. 2021; 9(6):113. https://0-doi-org.brum.beds.ac.uk/10.3390/risks9060113
Chicago/Turabian StyleIten, Raphael, Joël Wagner, and Angela Zeier Röschmann. 2021. "On the Identification, Evaluation and Treatment of Risks in Smart Homes: A Systematic Literature Review" Risks 9, no. 6: 113. https://0-doi-org.brum.beds.ac.uk/10.3390/risks9060113